In cybersecurity, speed and accuracy are necessities. Every second counts, and every detection could be the difference between resilience and breach. That’s why SentinelOne takes immense pride in protecting our customers, monitoring trillions of signals annually across organizations from SMBs to Fortune 10 enterprises to top government entities and critical infrastructure. With visibility into the most sophisticated threats, we’ve detected and disrupted countless ransomware attacks, thwarted advanced eCrime and nation state adversaries, and ensured operations remain protected against evolving risks.
Key highlights:
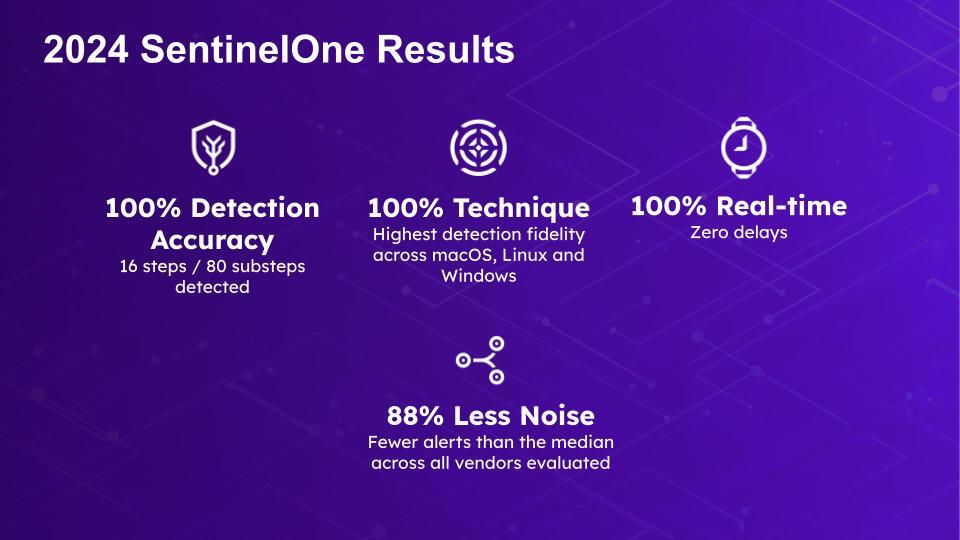
- 100% Detections – For the fifth consecutive year, the Singularity Platform delivered a flawless detection performance, achieving 100% detection at major step level
- Zero Delays – Singularity had zero detection delays across all simulated attack scenarios
- 100% Technique Detections Across ALL Operating Systems – Singularity scored perfect on detections for attack techniques simulated across Windows, MacOS and Linux systems
- 88% Less Noise – Compared to the median of participating vendors, Singularity produced 88% fewer alerts, demonstrating an outstanding signal-to-noise ratio. Security teams that can avoid alert fatigue stay ahead of adversaries, rapidly responding to legitimate threats while safeguarding their operations and customers.
Our commitment to relentless defense through advanced AI-powered cybersecurity was once again validated in the 2024 MITRE ATT&CK® Evaluations: Enterprise. SentinelOne continues to demonstrate how it outpaces the complexity of today’s cyber threats, giving organizations the tools they need to grow their business safely, and with confidence.

MITRE ATT&CK Evaluations | Understanding the Key Criteria & Insights
This year, MITRE focused on emulating sophisticated attacker techniques, simulating widespread ransomware targeting Windows and Linux, and malware linked to the Democratic People’s Republic of Korea’s (DPRK) targeting MacOS. By replicating the playbooks and tactics, techniques and procedures (TTPs) of well-known and prolific adversaries like the DPRK, this evaluation assesses how well security products detect and respond to real-world attack methods in a real-life production environment.
The evaluations serve to simulate these sophisticated yet common attack techniques, providing valuable insights into the strengths and weaknesses of various security products. For security professionals, understanding the background and methods of these evaluations is key to improving defense strategies.
SentinelOne’s Proven Excellence in Detection
The 2024 MITRE ATT&CK Evaluations: Enterprise simulated 16 attack steps and 80 substeps, covering a range of sophisticated tactics, techniques, and procedures (TTPs). The result: SentinelOne’s Singularity Platform successfully detected 100% of the attacks with no delays, providing real-time visibility and actionable insights across Windows, Linux, and MacOS environments.
Out of the 80 simulated attacks, Singularity generated 88% fewer alerts than the median of all vendors evaluated, significantly streamlining analysts’ workflows and improving response times. When security teams can dedicate their time on real threats rather than being overwhelmed by unnecessary alerts, they can maintain a sharp focus on acting decisively when it matters most. In today’s threat landscape, speed and accuracy equip teams with the clarity they need to protect their organizations from genuine attacks.
By detecting every attacker action across every operating system in real time, SentinelOne continues to redefine what’s possible in autonomous cybersecurity.
Continuous Evolution in Enterprise Evaluations | 3 Changes in MITRE’s 2024 Test
This year, MITRE challenged participating vendors by adding background noise and alert counts to test which would be able to strike the right balance between detection accuracy and managing noise and false positives, a critical factor in real-world security operations.
Our world is fast-paced with overwhelming amounts of noise slowing down even large-scale security teams. To keep ahead of irrelevant alerts and pinpoint critical leads amidst the clutter, security teams aim for a high signal-to-noise ratio rate. Increasing this rate translates to better decision making and more effective responses – teams can maintain a much more proactive strategy in defending their customers.
1 – Measuring False Positive Rates to Maximize Detection Accuracy
SentinelOne again showed a low number of alerts during the evaluation while maintaining 100% detection, demonstrating the effectiveness of the solution in alerting users to the most critical security issues in the network. False positive (FP) substeps were also woven in with attack steps during the emulation.
We support the decision to include noise and false positive measurements in the evaluation. This can reflect a more realistic simulation of the challenges faced by modern security teams and reinforce the importance of providing tools that enhance efficiency and effectiveness without compromising detection accuracy. We look forward to working with MITRE to refine how FPs are measured in future evaluations.
2 – Removing Telemetry to Shift from Visibility into Real Impact
Telemetry was removed as an explicit categorization in this round given that this type of data — raw visibility into telemetry data — is considered table stakes for modern security solutions like Singularity Platform. Therefore, this year’s evaluation measured the ability to raise actionable detections versus just provide visibility.
3 – Operating the Console | MITRE’s Hands-On Approach to Eliminate Bias
The emulation itself was different this year. MITRE analysts actually operated the console as a real SOC would rather than relying on the vendor. We support this change, given that it significantly reduced the chances of a vendor misleading MITRE about the performance of their product during the evaluation.
Meet the Adversaries | CL0P, LockBit, and the DPRK
MITRE utilized a relevant set of threat actors who frequently gain coverage in various media outlets.
Ransomware variants used in this round included CL0P, a group associated with the greater TA505 threat group who have continued to be active since January 2022, as well as LockBit whose Ransomware-as-a-Service (RaaS) operations were disrupted earlier this year as part of Operation Cronos.
Threat actors tying back to the DPRK have stepped up their targeting of macOS based systems as detailed in our blog post, making it ever so important for companies to prioritize protection for macOS now more than ever.
SentinelOne Leads the Way in AI-Driven Cybersecurity
MITRE ATT&CK Evaluations: Enterprise have become a trusted benchmark for assessing cybersecurity solutions’ ability to defend against advanced, real-world threats. Unlike traditional tests, these evaluations focus on the essence of “the how” – spotlighting the way platforms are designed to protect, detect, correlate, and contextualize adversary behaviors throughout the entire attack lifecycle.
SentinelOne’s consistent performance year-over-year underscores its commitment to delivering innovation in AI-driven security. For security leaders, this achievement speaks directly to operational impact and strategic advantages. The Singularity Platform’s ability to detect all attacks in real-time, without delays, ensures security teams are not only equipped to combat evolving threats, but doing so with unmatched efficiency, reducing downtime and preserving critical business operations.
Customers trust their cybersecurity vendors to protect them from the rippling fallout of ransomware attacks and data breaches – where every second of delay could mean terabytes of data encrypted – to insider threats and DDoS threats that could disrupt operations and break trust. With SentinelOne, threats are detected immediately, giving teams the upper hand in responding effectively before significant damage can occur. This level of precision and responsiveness empowers business leaders and security teams to focus on high-value innovative and strategic tasks rather than chasing false positives and delayed alerts.
Our Continued Commitment
As threat actors evolve their techniques, SentinelOne remains committed to innovation and delivering solutions to keep our customers safe. We are grateful for the opportunity to participate in the 2024 MITRE ATT&CK Evaluations: Enterprise. Our participation is not just a measure of our current capabilities, but a driving force behind the future advancements in our platform to come.
See how SentinelOne can revolutionize your security strategy. Visit s1.ai/mitre or schedule a demo today.



