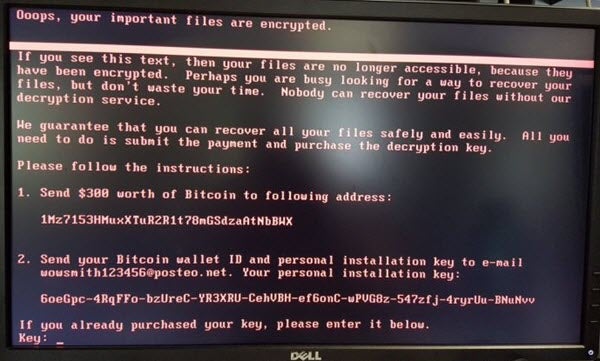
Several customers and industry analysts frequently ask us (and other vendors) about independent validation of our capabilities. We wanted to share information about a recent test conducted by MRG-Effitas to validate the effectiveness of various traditional and next-generation endpoint security suites against the EternalBlue and Doublepulsar exploits/backdoor. These threats were unearthed by “The Shadow Brokers” hacking group and are said to have been used by the NSA-linked Equation Group to launch cyber-attacks. The EternalBlue exploit received recent worldwide attention due to the WannaCry outbreak that used this exploit to infect over 230,000 machines in over 150 countries.
And unfortunately WannaCry does not seem to be the end of these threats. Attackers can use these same exploits to not only lock up data to demand ransom, but also to steal employee credentials to exfiltrate other sensitive information (think of this as two-for-one attack – advanced threat combined with ransomware). Worse yet, as seen in this particular case, attackers can bypass traditional and next-generation security measures, including hundreds of intelligence feeds. Further, security researchers who’ve tested security tools claim that these threats bypass 99% of security tools out there and we’re likely sitting with thousands more computers infected across several industries.
MRG-Effitas tested for these exploits against various traditional and next-generation endpoint security suites, including SentinelOne, Cylance, ESET, Symantec and others. The tests began in May 2017 – two months after Microsoft disclosed the MS17-010 vulnerability (EternalBlue exploit) and within weeks of the WannaCry outbreak.
The summary of the MRG-Effitas tests are as follows:
- We’re happy to see that SentinelOne passed this test with flying colors.
- In the words of MRG-Effitas: “SentinelOne 1.8.4.6202 was able to block every malicious payload DLL or shellcode introduced to the system via the Eternalblue exploit, by blocking it in a generic way. Both original Eternalblue with Doublepulsar and Metasploit port was tested. SentinelOne not only blocks the Meterpreter payload but the original Peddlecheap payload as well. As more and more tests were ongoing, we have seen that multiple (typically next-gen) products were able to block the Meterpreter payload loading in a generic way, but not the Peddlecheap one.”
- Other traditional endpoint security suites such as ESET and Kaspersky also stopped the backdoor from being installed.
- Symantec EPP seems to have failed with blue-screen-of-death when run within VMWare, but caught the attack on a physical endpoint.
- Cylance was the only vendor that failed this test.
- In the words of MRG-Effitas: “The interesting part of the video starts at 5:00. The Doublepulsar backdoor is already installed and this means the system is already compromised and it would appear that Cylance did not realise this.”
- The video referenced above is Cylance’s video on WannaCry protection
One of the other pieces explored by the blog is looking beyond the tactics used by WannaCry to other capabilities that may be exploited in the future. For instance, WannaCry is a strain of Windows ransomware that took advantage of the EternalBlue exploit along with a file-based payload. However, the EternalBlue exploit could easily be used with fileless (in-memory) malware that can completely work around the defenses of solutions that miss the exploit or focus on file-based detection. This methodology is discussed in the blog and was also used in the wild by another ransomware family dubbed UIWIX. In other words, customers without holistic protection will leave themselves exposed to another WannaCry-like attack in the future. So look at your security vendors carefully.
Interested in the versions of Windows impacted by MS17-010 – check out the Microsoft Security Bulletin. The most popular versions, such as Windows 7, Windows 8.1, Windows Server 2008 R2, Windows Server 2012 R2, Windows Server 2016 and Windows 10 all have this vulnerability. It’s obviously wise to get the patches and updates installed as soon as possible.
To learn more about how SentinelOne can help, check out our Endpoint Protection Platform online or our datasheet.