The Good
Cyber cops in the Ukraine assisted by US and UK law enforcement officers have this week bust a ransomware gang that is believed to have caused losses of around $1 million to more than 50 American and European businesses.
According to the Cyberpolice of Ukraine, a husband-and-wife team from Kyiv aided by three accomplices used malspam to breach companies and infect them with ransomware. The gang also offered IP anonymization services to other cyber criminals and stole banking credentials from UK consumers. These were subsequently used to purchase goods from online stores, which were later resold for cash.

The gang no doubt believed they were on to a good thing until the cops raided their homes and confiscated three cars along with multiple computers, phones, bank cards and flash drives. The five individuals will be charged with offenses related to computer misuse, the use, distribution or sale of malicious software or hardware, and money laundering. As the gang had contacts with other international cyber criminals, there is the potential for further arrests down the road, and police say the investigation is ongoing.
The Bad
While it’s great to see the police take down one ransomware gang, plenty of others are still running amok. This week has seen a number of other successful attacks impacting businesses.
Among those affected are Netherlands’ Game Mania, which was hit in the early hours of Monday morning with a ransomware attack and data breach. Attackers gained access to a server containing company data, including customer PII, as well as deploying an unnamed ransomware. While the company says its business activities remain unaffected, they are warning customers to be vigilant of phishing scams and unsolicited emails demanding money.

Wednesday saw another attack on US critical infrastructure. Last week it was an Albuquerque jail, this week it’s the education sector. Albuquerque Public Schools were forced to cancel classes in around 31 schools after teachers discovered the attack prevented them from accessing the APS student information system, which is used to record attendance, grades and other student information.
In a stark reminder of the true costs of ransomware, this week also saw Houston-based United Structures of America, Inc, which fabricates and designs steel structures for use in buildings and other applications, file for bankruptcy as a consequence of a ransomware attack back in 2019. The attackers erased the company’s financial records and technical software and demanded a ransom for return of the data. Although the company paid the ransom, the attackers did not fulfill their end of the bargain and the data was never returned. As a result, the company, which at one time had brought in revenue in excess of $100 million, was forced to start winding down its operations.
The Ugly
Software development and bugs go hand-in-hand, which is why many vendors offer bug bounty programs so that external researchers can help spot problems the developers may not have foreseen. And while despite that there are still some really bad bugs out there that remain unpatched, things really start to turn ugly when it turns out that a piece of security software has had a known but unpatched bypass for eight years.
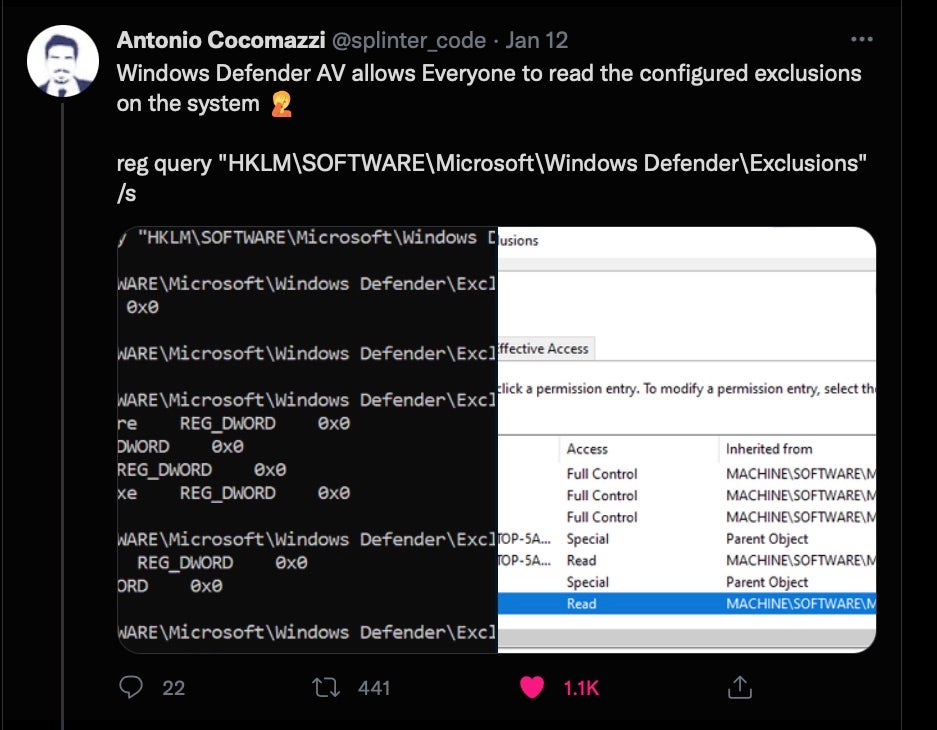
The bug? It turns out Microsoft Defender allows unprivileged users to look-up any locally excluded paths. Even if an admin hasn’t created any exclusions, certain software installations and server configurations can result in some paths being automatically excluded. If an attacker has local access, they can look up these excluded paths and drop their malware at paths that Defender will ignore. Researchers this week tested the theory with a sample of Conti ransomware, encrypting the device while Defender sat idly by.
For enterprises relying on Defender to protect their servers and other endpoints, this is a gaping security hole. While an attacker does need a foothold, they don’t need privileges, and with plenty of other RCEs available at the moment, it really is past time that enterprises started looking beyond OS vendors for effective defense of their endpoints and networks.