The Good | DoJ Indicts WhisperGate Threat Actor
A malicious cyber actor thought to be behind the WhisperGate attacks on Ukraine in the days prior to Russia’s invasion, as well as attacks on NATO and U.S. computer networks has been indicted by the DoJ.
Amin Stigal, a 22-year old Russian national, is alleged to have managed infrastructure used by Russia’s GRU to stage malicious payloads used in WhisperGate malware campaigns, targeting the Ukrainian government and later U.S allies. U.S. Attorney General Merrick B. Garland said that Stigal conspired with Russian military intelligence to aid the Russian military, including in attacks on government systems and data with no military or defense-related roles.

WhisperGate is one of a number of wiper malware families used in intrusions against government and other institutions in Ukraine in early 2022. Designed to look like ransomware, wipers attempt to destroy the target computer and related data.
In conjunction with attacking systems with WhisperGate, Stigal allegedly helped the GRU to compromise other systems, exfiltrate sensitive data and deface websites. Some of the stolen data later appeared on public forums and included patient health records.
Stigal remains at large but if caught and convicted faces a penalty of five years in prison. Rewards for Justice is offering up to $10 million in bounty for information leading to his capture.
The Bad | Ransomware as a Tool for Spies
There’s been no shortage of bad news thanks to ransomware in our weekly cybersecurity news roundup over the years, but this week SentinelLabs put the spotlight on yet another evolution of this egregious threat. It appears that ransomware has become a tool of choice not just for financially-motivated threat actors but also for those engaged in cyberespionage.
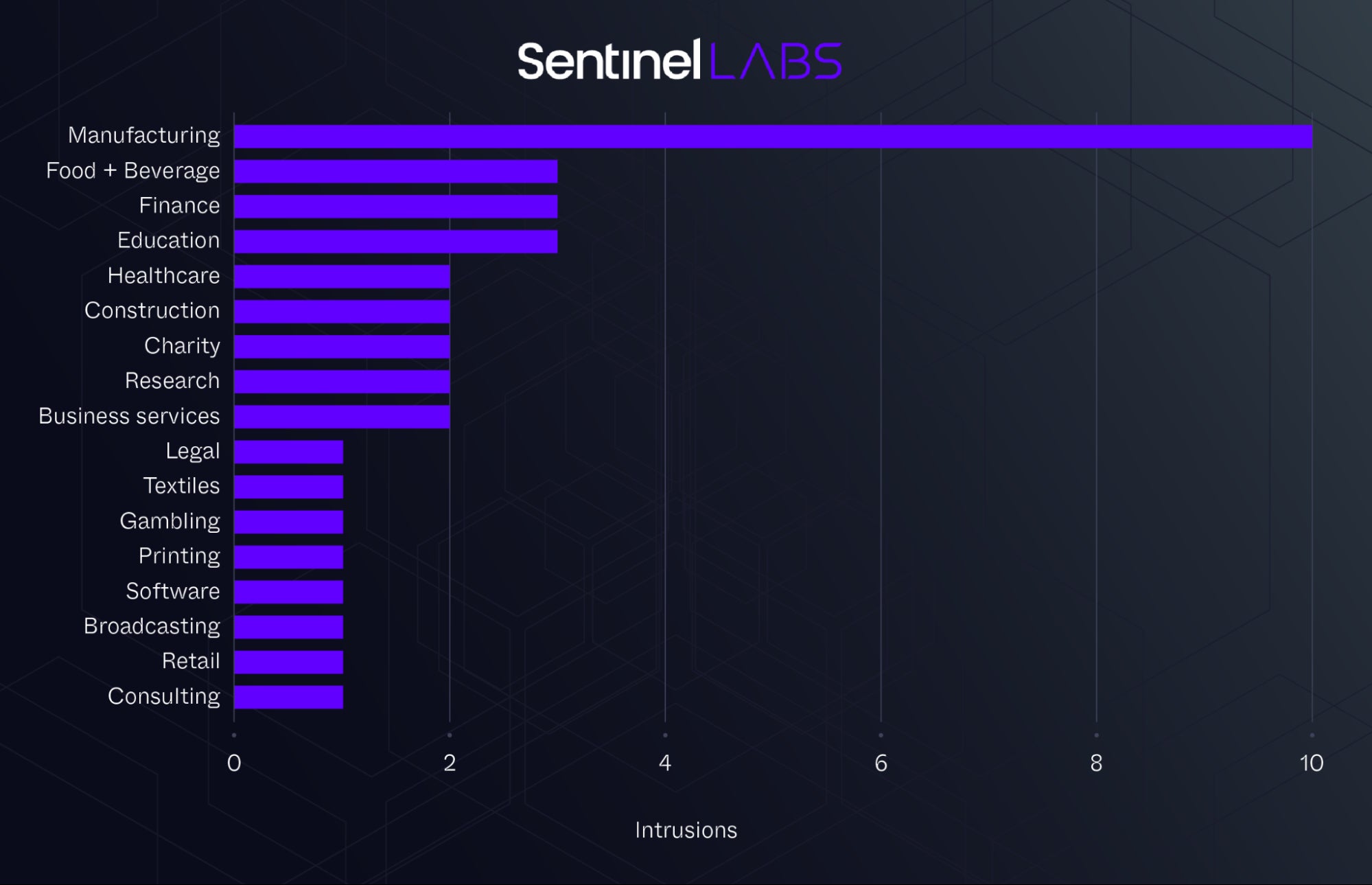
Suspected Chinese APT group ChamelGang targeted multiple organizations with CatB ransomware, including the Presidency of Brazil and India’s healthcare institution AIIMS. In addition, the group is believed to have targeted a government organization in East Asia and critical infrastructure sectors, including an aviation organization in the Indian subcontinent. In unrelated incidents, a separate cluster of intrusions involving off-the-shelf tools BestCrypt and BitLocker have been deployed by espionage actors in a variety of industries, primarily those involved in the U.S. manufacturing sector, across North America, South America and Europe.
What could spies, whose tradecraft typically relies on stealth, want with the noisiest of all malwares, one that literally announces to the user that they have been compromised by splashing a ransom note on the screen and locking files?
The answer to that lies, in part, in the way that organizations respond to ransomware incidents. These are typically reported to local law enforcement agencies which may not share critical data and insights with intelligence agencies. In addition, as organizations across the world ride out a wave of ransomware attacks from an increasing number of unsophisticated-yet-effective cyber criminals buying cheap RaaS offerings, cyberespionage actors can disguise their operations and avoid attribution by dropping ransomware payloads after completing their other objectives.
For cyber spies, deploying ransomware as a final payload affords various opportunities to cause disruption, distraction, misattribution, and the removal of evidence as they conduct their more discrete operations. The researchers also point out that some APTs are not averse to funding their own operations with funds stolen from the organizations they spy on, either.
The Ugly | MOVEit CVE-2024-5806 – Exploit Attempts in Progress
Researchers are warning that a CVSS 9.1 rated vulnerability in Progress Software’s MOVEit Transfer is seeing in-the-wild attempts to exploit it, beginning within hours of the patch becoming available.
CVE-2024-5806 affects MOVEit Transfer version 2023.0.0 earlier than 2023.0.11, version 2023.1.0 earlier than 2023.1.6, and version 2024.0.0. The bug is described as being able to lead to an authentication bypass and can be exploited to allow an attacker to impersonate another user on the system.
Researchers from Rapid7 say they believe that prerequisites for the attack involve knowing an existing user’s name, targeting an account that can be authenticated remotely, and having an SFTP service open to the public internet. Censys research estimates that there are around 2,700 exposed instances of MOVEit Transfer on the internet, with the majority of those in the U.S.
Very shortly after vulnerability details were published today we started observing Progress MOVEit Transfer CVE-2024-5806 POST /guestaccess.aspx exploit attempts. If you run MOVEit & have not patched yet – please do so now: https://t.co/AenLgqg1wM
— The Shadowserver Foundation (@Shadowserver) June 25, 2024
A previous flaw in MOVEit Transfer was used in attacks by Cl0p ransomware around this time last year. In May and June 2023, CVE-2023-34362 was used to deliver webshells that allowed the attackers to exfiltrate files, including files hosted on Windows Azure if the MOVEit instance was configured to use Azure’s blob services storage. SentinelOne observed opportunistic attacks against more than 20 organizations during that time.
Progress says it strongly urges all MOVEit Transfer customers on versions 2023.0, 2023.1 and 2024.0 to upgrade to the latest patched version immediately, and also to apply the mitigation steps described here.


