
The Good
After only a partially successful attempt to get security researchers hacking on voting machines at DEF CON 2019, several hundred US military and National Guard cyber security troops have this week been training for Election Day 2020 at AvengerCon. The two-day event, which is only open to US Cyber Command employees, aims to test both voting machines and the people responsible for protecting them in the event of an Election Day cyber attack. Participants at the con will get their hands on the actual voting machines scheduled to be used in next year’s election and will also run drills to test responses to attacks on the electric grid and other voting machine infrastructure. The organizers are also hoping to raise wider public awareness of the vulnerabilities in voting machine technology, which could be used to erase votes or prevent legitimate voters from participating by deleting their details from databases. To that end, they are also promoting the recently formed Election Integrity Foundation, which interested readers can follow on Twitter at @ElectionInteg.
The Bad
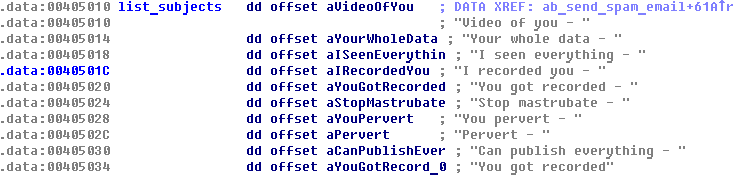
If you’ve been lucky enough not to have received one of the many sextortion spam emails that have been circulating in increasing numbers over the last few years, congratulate yourself on having a fine set of spam and junk mail filters. Fingers crossed that they keep up the good work, though, as the half a million-strong Phorpiex aka Trik botnet turns its attention away from ransomware like GandCrab and cryptomining to deliver millions more of the blackmail payment demands. According to researchers, the botnet is now using its network of infected devices to run sextortion campaigns at a massive scale. It’s estimated that a single Phorpiex spam bot can generate up to 30,000 spam emails per hour. The bot downloads one of over a thousand database files, each containing up to 20,000 email addresses, from its C2 server. The researchers suggest that a single campaign could potentially target 27 million individual email inboxes.
The Ugly
Who knew it could be so easy? Well, Samsung do now, along with the rest of the world. After a British couple accidentally discovered that the fingerprint reader in their Galaxy S10 would grant access to anyone if covered with a plastic screen protector, people all around the world were able to confirm that the fingerprint reader was easily defeated by nothing more than a thin film of plastic.
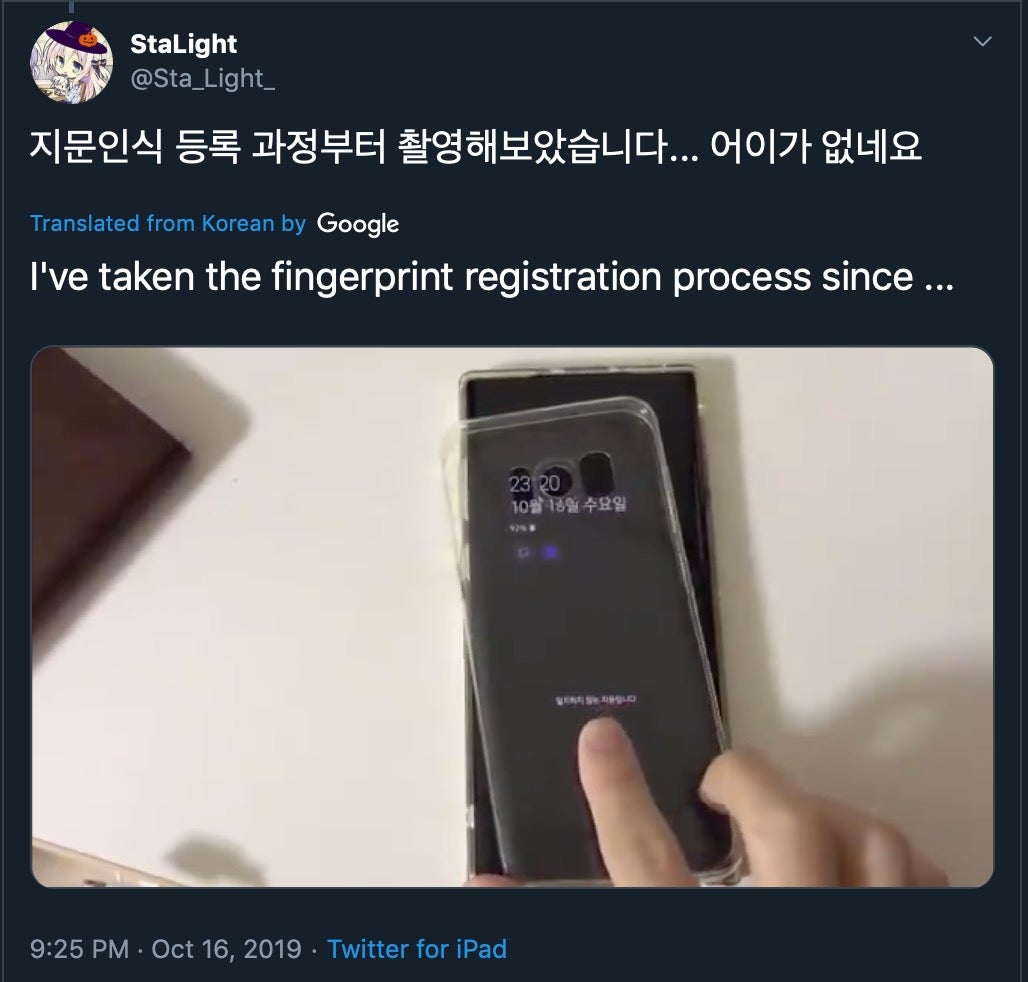
The issue appears to revolve around the fact that, unlike smartphones from almost all other manufacturers, the affected Samsung devices use an unconventional ultrasonic sensor rather than an optical reader. It seems common plastics disrupt the ultrasounds sent out by the sensor and the unexpected readings cause the underlying software to unlock the device.
The same bug also affects the Galaxy Note 10, and users are being advised to switch off the fingerprint-recognition option, particularly if using mobile banking or other apps that contain confidential data. Meanwhile, Samsung say they are aware of the “malfunctioning fingerprint recognition” and will issue a software patch soon.

