The Good | Law Enforcement Set New IoT Device Protections, Charge Ex-NSA Spy, and Sentence REvil Affiliate to Prison
Global law enforcement agencies made significant strides this week, improving the minimum safety standards to protect tech consumers and officially sentencing two major cybersecurity criminals.
Tech manufacturers in the U.K. are now legally required to protect internet-connected devices against the risk of default passwords. The latest legislation prohibits weak passwords on smartphones, TVs, appliances, and more to ensure ongoing protection against credentials-based cyberattacks. Manufacturers must also provide a point of contact for reporting security issues and state when devices will receive important security updates. Those that fail to meet the provisions will now face recalls and penalty fees up to £10 million, or 4% of their global annual revenue – whichever is higher. The U.K. is the first country in the world to ban default credentials from IoT devices.
An ex-NSA employee caught trying to sell classified secrets to Russia has been formally sentenced to over 20 years in prison. The DoJ charged Jareh Sebastian Dalke, 32, for attempted espionage while he was employed as an information systems security designer for under two months. During his short tenure with the agency, Dalke met with what he thought was a Russian agent to exchange top-secret National Defense Information (NDI) documents for a sum of $85,000 and establish future opportunities to sell more documents.
Yaroslav Vasinskyi has been sentenced for deploying REvil ransomware over 2500 attacks, including the one on Kaseya in 2021. Demanding a combined $700 million from various U.S. victims, Vasinskyi and his co-conspirators often threatened to publish sensitive data to drive a higher rate of ransom. The Ukrainian national is charged with conspiracy to commit fraud and related activity in connection with computers, damage to protected computers, and conspiracy to commit money laundering.
DOJ’s Office of International Affairs worked with Polish authorities to secure the extradition of cybercriminal Yaroslav Vasinskyi who was sentenced to 13 years & seven months in prison & ordered to pay over $16M in restitution. https://t.co/lzvJO6rg0a
— U.S. Department of Justice – International (@USDOJ_Intl) May 1, 2024
The Bad | Attackers Plant Millions of Malicious Repositories in Docker Hub Loaded with Malware
Millions of malicious “imageless” containers planted within Docker Hub have been redirecting unsuspecting users to phishing and malware sites for years. This week, security researchers reported on three large-scale malware campaigns specifically targeting the container image registry popular with developers and open source contributors globally.
According to the report, the containers were published over a five-year period and the campaigns have been running since early 2021. They account for approximately 20% of the malicious content found across 15 million repositories hosted on Docker Hub. The imageless containers identified by researchers have no content, only documentation ranging from spam to malware and phishing websites.
Each of the three campaigns employ different tactics to mislead users and distribute the malicious repositories. Using lures such as pirated content, video game cheats, educational e-books, and online diary-hosting services, the payloads ultimately contact a command and control (C2) server to transmit system metadata and obtain links to cracked software. Currently, researchers suspect the attacks are part of a larger operation that may involve monetization schemes via adware or third-party software distribution.
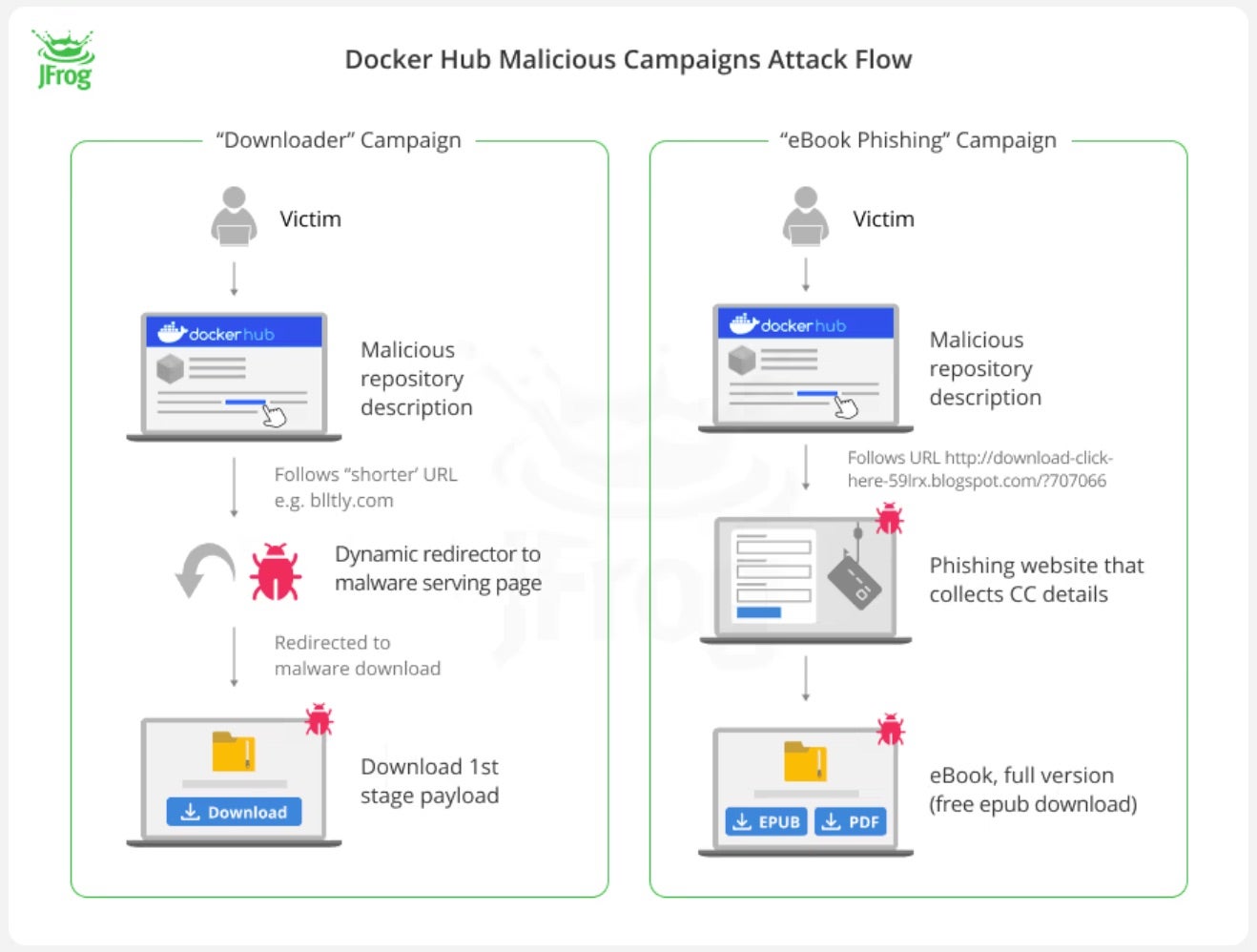
Security researchers note that these campaigns work by capitalizing on Docker Hub’s good name and credibility, which makes it all the more difficult to separate the legitimate containers from those triggering phishing and malware installation attempts. Continued misuse of Docker Hub by threat actors emphasizes the need for stricter moderation and better content screening mechanisms on such platforms.
As the trend of malware exploiting vulnerabilities in open-source ecosystems climbs, security experts warn users to exercise caution when downloading packages by reviewing the designated tags for trusted content.
The Ugly | CISA Warns Against Critical GitLab Account Takeover Flaw Under Active Exploit
Ongoing attacks are plaguing GitLab instances this week caused by a critical severity vulnerability tracked as CVE-2023-7028 (CVSS 10.0). Confirming the active exploits, CISA has issued a warning about the flaw, adding it to their KEV catalog and urging all federal civilian executive branch (FCEB) agencies to remediate the risks within three weeks.
CVE-2023-7028 was first disclosed by GitLab in January and allows attackers to seize control of accounts. The flaw stems from improper access control, which then enables remote, unauthenticated attackers to send password reset emails to accounts, all without user interaction. Attackers could also exploit this vulnerability to infiltrate Continuous Integration and Continuous Delivery (CI/CD) pipelines, potentially leading to supply chain attacks.
At time of writing, the GitLab has released fixes for versions 16.5.6, 16.6.4, and 16.7.2 with older versions being patched retroactively. While there have been no reports of ransomware attacks linked to the account takeover flaw, CISA’s warning underscores the severity of the risks it poses.
Given the nature of the platform, GitLab houses mass amounts of source code and API keys – all of which could be abused by attackers to breach organizations and carry out software supply chain attacks. According to Shadowserver, over 2100 servers are still exposed to the vulnerability. Organizations using GitLab are urged to prioritize patching, consult their incident response guide, and check for signs of breach immediately.