Cyber threats do not ring a bell first before invading, instead, they attack when no one is on guard. One could easily argue that cyberattacks are reserved for Fortune 500 companies, while the truth is that all companies fall in the crosshairs.
Currently, projections for 2025 state that the annual cost of cybercrime would amount to $10.5 trillion. These are staggering numbers, so for those in charge of safeguarding IT assets, there’s no room for complacency, only improvement.
The core philosophy of a defensive approach to cybersecurity is to construct an integrated defense system that is robust enough to adapt to any form of attack.
From constant monitoring to educating employees about phishing, this strategy prepares your organization for the worst before it even happens, dampening the effect of an attack, increasing recovery time, or preventing the threat altogether.
This article comprehensively covers the principles of defensive cybersecurity, why we need it, and use cases of a defensive cybersecurity setup.

What is Defensive Cyber Security?
Defensive cybersecurity is an overarching term that implies preparedness to take proactive security measures and protocols to protect IT assets, systems, programs, and networks from potential threats.
It focuses solely on preventing and maintaining barriers that shield assets from unauthorized access and attacks. It does all this by actively monitoring, recognizing vulnerabilities, and reinforcing weak spots.
Defensive cybersecurity is a layered ecosystem. Setting up these defensive walls starts with a risk check, then adds layers like:
- Identity management and continuous monitoring
- Firewalls and Intrusion Detection Systems (IDS) work as the outer barrier, filtering traffic and detecting suspicious activity
- Encryption adds another layer, scrambling your data so attackers can’t read it
- Tools like Endpoint Detection and Response (EDR) help keep an eye on all connected devices
- Security Information and Event Management (SIEM) tools gather and analyze data to proactively detect and prevent potential attacks
Regardless of these defending elements, people are often the weakest link to a potentially compromised system.
This defensive approach covers this with regular training, simulations, and phishing tests to keep all stakeholders aware of social engineering tricks.
Why do we need Defensive Cyber Security?
The challenge is no longer if an organization will be attacked, but when. So, the real question should be, “How do we defend an increasingly digital world where every action, transaction, and connection could be a potential threat?”
We are not only protecting data but safeguarding hard-earned trust and operational integrity, which are the very fabric of today’s economy.
Therefore, the emphasis goes beyond the necessity of strong defenses to how robust, adaptive, and multi-layered those defenses must be to face threats that can emerge from anywhere.
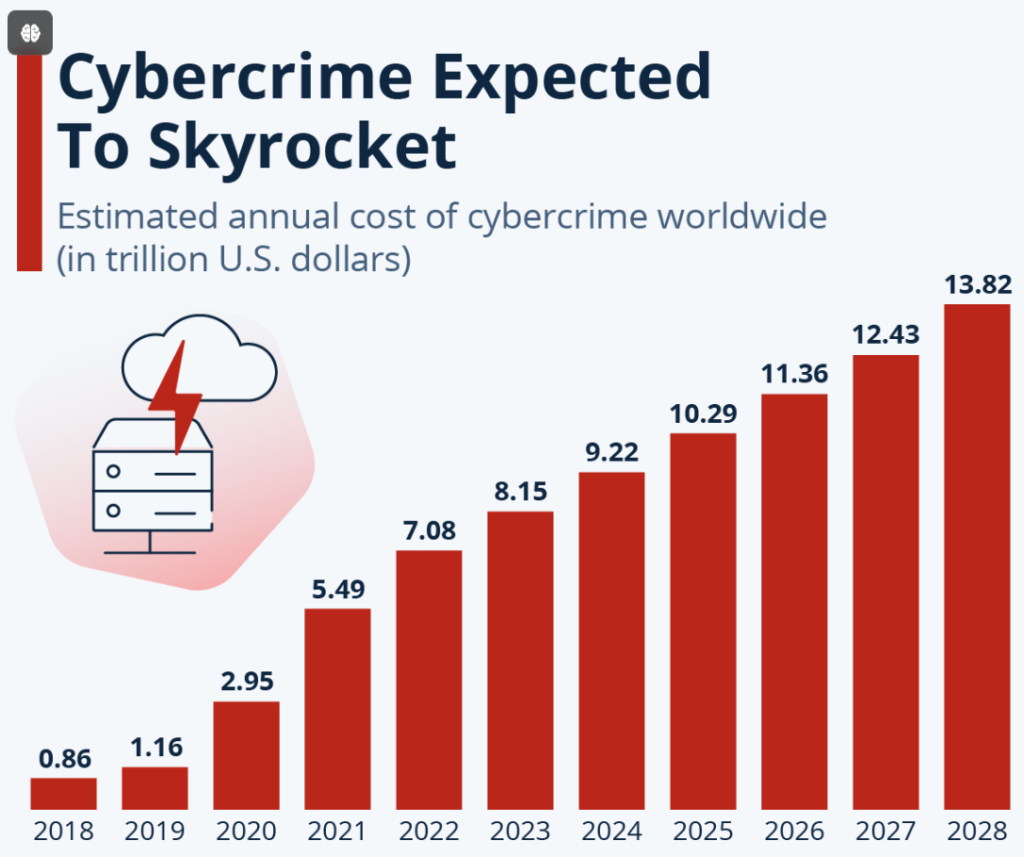
The global cost of cybercrime is expected to spike in the next couple of years, rising from $9.22 trillion in 2024 to $13.82 trillion by 2028. This summation includes the costs of tackling cybercrime, fallout, and consequences of unchecked and successful attacks.
 Damage from a cybersecurity incident can be long-lasting and far-reaching, often surpassing the direct financial costs, including:
Damage from a cybersecurity incident can be long-lasting and far-reaching, often surpassing the direct financial costs, including:
1. Safety of Employees
Cyber-attacks don’t just compromise systems; they sometimes target employees’ private data, such as payroll information and personal identifiers, leaving them vulnerable to identity theft and fraud.
According to the 2022 Insider Threat Report, the metric of computer-related crimes showed that the cost of credential theft had increased by 65%, from $2.79 million in 2020 to $4.6 million as of 2022. Businesses have also reported that compromised business credentials caused 19% of data breaches.
This alarming increase begs the need for a continuous and proactive defense system.
2. Denying Unauthorized Access
Think of your systems as a vault. Would you leave it half-open, assuming no one would notice? Hackers like to exploit misconfigurations and poor access controls, sneaking through cracks like SQL injections or Cross-Site Scripting (XSS).
Did you know that many breaches start with a simple privilege escalation attack? Once inside, attackers can navigate your systems undetected.
Look at Flagstar Bank; their breach was not through brute force attacks but from exploiting a vulnerability in their cloud infrastructure, exposing about 1.5 million individual records.
3. Increase the Trust of all Stakeholders
It takes years to earn trust and mere seconds to lose it all. Trust is not earned with a security badge or a compliance certificate but built with consistent security practices.
Stakeholders, whether they are shareholders, partners, customers, or even employees, expect robust protection.
The incident on Britain’s TalkTalk Telecom group saw data stolen from 157,000 people and triggered a stream of bad publicity. The company lost 101,000 customers (about 3% of its subscriber base at the time) and cost over £60 million in damages.
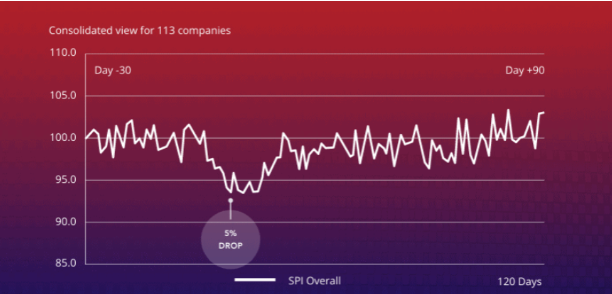
The Ponemon Institute, in collaboration with Centrify, conducted a survey on the impact of data breaches on reputation and share value. Although published in 2017, the research is still definitive on this subject.
It showed that a pool of 113 globally traded UK companies had a share price drop of -5% in the wake of a disclosure of a cyber incident.
Defensive cybersecurity thus becomes a tool for strengthening trust and ensuring business continuity.
4. Business Advancement
Cyber defenses should not just protect but also be a proponent for positive and expansive growth. The more you innovate, the more attractive you become to attackers.
By consistently and continuously protecting digital assets and intellectual property, companies are free to innovate without fear of theft or sabotage.
Businesses that invest in cybersecurity often outperform those that don’t. Taking a point from rapidly scaling retail corporation—Home Depot; an attack on the company set them back with damages that compromised 56 million cardholders and $10 billion in losses.
They quickly turned around the disaster by setting up encryption defense systems. They reported a sharp rise in shareholder value to 25% (over $30 billion) in their end-of-year post-crisis report.
5. Customer Data Protection
One slip, one unsecured database, and you’ve not only lost data, but you’ve also lost relationships. Data breaches are commonplace, and customers need assurance that their information is secure.
Failure to secure customer data can lead to severe penalties and legal downturns for an organization, as well as loss of brand loyalty and long-term customer commitments.
Under the GDPR, fines for serious breaches can reach up to €20 million or 4% of global revenue, whichever is higher, while even lesser violations can result in penalties of up to €10 million.
Similarly, the CCPA imposes fines of up to $7,500 per intentional violation, with the added risk of customer legal action.
The Differences in Offensive and Defensive Cybersecurity
When we hear “offensive,” we usually think of hackers breaking into systems, but offensive and defensive security actually go hand in hand.
The difference is in how they approach threats: offensive security actively probes, finds, and fixes weak points before anyone can take advantage. In contrast, defensive security focuses on blocking and catching threats before they cause damage.
Key differences between them include:
| Aspect | Offensive Cybersecurity | Defensive Cybersecurity |
|---|---|---|
| Mindset | Adopts an attacker mindset, attempting to bypass or exploit defenses to test effectiveness. | Based on a protection-oriented mindset, maintaining security postures and remediating vulnerabilities post-incident. |
| Goal | Helps to identify exploitable weaknesses before malicious actors do. | Aims to maintain a solid, consistent, and continuous security to thwart attackers and reduce system exposure. |
| Techniques | Includes advanced penetration testing, red teaming, and exploiting cloud misconfigurations. | Uses firewalls, IDS/IPS (Intrusion Detection/Prevention Systems), machine learning, behavioral analytics, cloud security posture management (CSPM), SIEM (Security Information and Event Management), and vulnerability management strategies. |
| Activity type | Often reactive, simulating real-world attacks after vulnerabilities are identified. | Proactive, focused on building security systems to prevent attacks before they occur. |
| Legal and Ethical Boundaries | May involve legally grey areas if done without consent; heavily reliant on permissions. | Entirely ethical and legal, with a focus on preventing illegal activities. |
| Time Sensitivity | Offensive actions are often conducted within short, targeted windows for testing purposes. | Defensive measures are ongoing and require continuous monitoring and incident response. |
Defensive Cyber Security Measures
In 2023 alone, cybercrime cost around $8 trillion globally, reflecting more than stolen data. It includes everything from lost money and productivity to the hassle of cleaning up hacked systems, post-attack investigations, system restoration, and adverse business outcomes.
Some measures your organization can take to prevent losses include:
1. Threat Intelligence Integration
Cyber threat intelligence platforms collect information from sources like dark web monitoring and threat feeds to help you stay ahead of attackers. This intelligence can be used to preemptively update firewalls, IDS/IPS systems, and patch management protocols.
2. Zero Trust Architecture
Zero Trust Architecture will help you divide the network into segments, verify identities at every step, and enforce strict access rules. Key technologies include multi-factor authentication (MFA), micro-segmentation, and Identity and Access Management (IAM) systems to limit internal threats and unauthorized movement.
3. Deception Technology
Using decoys like honeypots or false user accounts, this strategy gathers information about how attackers operate without risking real assets. It helps refine security measures by mimicking real network environments and watching how attackers behave.
4. Cloud Security Posture Management (CSPM) Tools
These tools watch for misconfigurations, bad access controls, and vulnerabilities, like unsecured storage or permissive permissions. They help ensure that cloud systems remain secure by catching gaps before attackers can exploit them.
5. Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR)
EDR tools constantly track activity on endpoints, watching for any signs of threats. MDR services offer round-the-clock monitoring and expert-level threat hunting, giving companies security without having to maintain their own in-house teams.
Suggested read: Building a Defense Posture | Top 5 Cybersecurity Tips For Small & Medium Businesses (SMBs)
Core Principles of Defensive Cybersecurity
The three major principles of defensive cybersecurity are:
- Confidentiality
- Integrity
- Availability
| Principle | Description | Key Measures |
|---|---|---|
| Confidentiality | Ensures sensitive data is only accessed by authorized individuals, protecting it from unauthorized disclosure. | – Strong authentication is used to verify user identities. – Encrypt data both when stored and during transmission. – Mask or anonymize data to prevent unauthorized visibility. |
| Integrity | Guarantees that data remains accurate, consistent, and unaltered during storage, transmission, or processing. | – Use checksums and hash functions to verify data integrity. – Apply digital signatures to ensure data authenticity. – Use version control to track data changes. – Employ redundant systems and regular backups for data availability and integrity. |
| Availability | Ensures data and systems are accessible to authorized users when needed, keeping operations running smoothly even during disruptions. | – Implement load balancing and failover systems to ensure continuous service. – Use cloud solutions for scalable and resilient infrastructures. – Protect against DDoS attacks with firewalls and traffic analysis tools. – Create a disaster recovery plan with backup and recovery strategies. |
Defensive Cybersecurity Use Cases and Examples
Cyber attacks are devastating, but they teach hard lessons to build resilience against any further potential attempts.
Here’s how an organization reacted to threats and did things differently:
Maersk and the NotPetya Recovery
A.P. Møller-Maersk, a global shipping company, was severely impacted by an attack. A power cut in Nigeria’s capital city salvaged Maersk’s network infrastructure during the NotPetya attack in 2017.
Maersk CISO Andy Powell said the malware wiped out almost all online backups of the company’s Active Directory – save, mercifully, for a piece held in its powered-down Lagos office.
The NotPetya exploit tool trashed nearly 50,000 company laptops, blocked access to 1,200 applications, and turned off the entire VoIP phone network.
Adam Banks, CTIO at Maersk, said this about the incident:
“When Maersk was hit by NotPetya, the company was “not unusually weak,” and this is really important because too often organizations feel immune to cyber-attacks because they do not consider themselves to have obvious security flaws.”
After the attack, Maersk restructured its cybersecurity protocols and established a backup system to restore operations quickly.
Maersk Line increased its investment budget to set up better defenses against cyber attacks, and its India M.D. Steve Felder had this to say:
“We have revised our system architecture to reduce some of the risks. If there is a future attack, we will be able to contain it locally.”
SentinelOne Safeguards Quantiphi with AI and Machine Learning
Quantiphi’s CISO, Amit Dhawan, talks about how the company keeps its data secure using SentinelOne.
With tools like smart policy management, asset tracking, forensic features, and AI-driven protection, they make sure both Quantiphi’s data and its customers are safe. The ability to roll back systems in case of an issue adds an extra layer of security, giving them confidence that any threats can be quickly handled.
Singularity™ Cloud Security is designed to provide real-time cloud security that spans public, private, and hybrid environments. Its core strength lies in the ability to secure workloads at every stage (from build time to runtime) using an AI-powered platform that detects, responds to, and remediates threats autonomously.
Singularity™ Cloud Security tackles several core cybersecurity issues organizations face when defending cloud environments.
Here’s how it solves them:
- Misconfigurations and Vulnerabilities
Cloud breaches are often caused by misconfigurations, which leave systems exposed. Singularity™ Cloud Security handles this by:
- Running real-time checks to spot and fix misconfigurations before they escalate into security risks.
- Using vulnerability management to continuously scan and automatically patch issues in containers, Kubernetes, and other environments, keeping everything secure.
- Compliance and Governance Challenges
Meeting regulatory compliance in complex cloud infrastructures can be overwhelming. Singularity™ addresses this by:
- Running automatic compliance checks to make sure you’re following the proper regulations.
- Providing insights to help you quickly fix any compliance gaps so you don’t have to do it manually.
- Threat Detection and Response
Quickly responding to cloud threats is crucial to prevent serious breaches. The platform:
- Using autonomous AI to detect and stop threats in real-time.
- Threats are prioritized through Verified Exploit Paths™ so security teams can focus on the most critical issues first, preventing serious breaches.
- Leakage of Secrets and Loss of Data
Maintaining the confidentiality of data, especially in the cloud, where containerized applications are increasingly used, has become increasingly difficult. Singularity helps by:
- It looks into the code repositories, CI/CD pipelines and cloud applications to prevent the leakage of sensitive information by looking for suspicious patterns.
- Providing measures to protect information that is both being sent and information that has been stored.
- Operating in Multi-Cloud, Hybrid Environments
On-premise combined with private and/or public clouds is what most organizations employ for their security posture. Singularity solves this challenge by:
- Applying a single, consistent set of security policies across public cloud, private cloud, hybrid, and multi-cloud infrastructures.
- Incorporating protection for various types of workloads, such as Kubernetes, containers, and virtual machines, so that all infrastructure can be fully secured.
Key Features
Singularity™ Cloud Security brings together multiple cloud security tools into one easy-to-manage platform, offering flexible, real-time protection for today’s cloud environments.
It can also speed up incident investigation and resolution using Storyline. It keeps track of context even across multiple processes and system reboots.
Storylines allow organizations to quickly track and resolve security breaches by linking related events, helping teams test their theories efficiently and perform rapid Root Cause Analysis (RCA).
| Features | Benefits |
|---|---|
| AI-Powered Threat Detection | Automatically detects and responds to cloud threats with AI, reducing the need for manual work and mistakes. |
| Zero Kernel Dependencies | It protects your systems without slowing them down or requiring deep-level integrations. |
| Full Cloud Coverage | Covers everything from virtual machines and containers to serverless setups, so nothing is left unprotected. |
| Hyper-Automation | Uses low-code/no-code workflows for faster response and easy automation of threat handling. |
| Forensic Telemetry | Provides deep insights into cloud incidents, ensuring a faster and more comprehensive post-incident analysis. |
Singularity™ Platform
Elevate your security posture with real-time detection, machine-speed response, and total visibility of your entire digital environment.
Get a DemoConclusion
Staying ahead of threats means setting up a multi-layered defense system that anticipates, detects, and responds to potential threats in real-time.
From protecting sensitive data to managing complex multi-cloud environments, businesses must take a proactive approach and set up defense systems to ensure the safety and integrity of their IT assets.
The next steps for any organization involve assessing its current security posture and identifying gaps in protection, especially as cloud infrastructures continue to grow.
FAQs
Defensive cybersecurity is exactly what the phrase connotes: It is a barricade set up to maintain and safeguard systems from potential threats and attacks. In detail, it builds three proactive lines of defense to effectively combat cyberattacks:
- First line of defense – Deals with/is responsible for risk ownership and management across the board.
- Second line of defense – This level focuses on risk oversight and compliance with relevant regulations.
- Third line of defense – It acts as an independent assurance function that provides objective evaluations of the effectiveness of risk management processes and controls.
It simply protects and keeps sensitive and confidential data away from unauthorized individuals. “Network Security” is a popular overarching term that houses comprehensive strategies, tools (hardware and software), protocols, and configurations to protect networked systems against threats.
Organizations must seek to protect data through a multi-layered technique that includes stepwise measures like:
- Securing the physical assets (hardware/endpoint devices)
- Restricting access according to defined roles
- Educating employees on how to recognize security threats
There must also be a scheduled data backup in place while also being able to encrypt some sensitive information from breaches.
It is also necessary to use or install network monitoring mechanisms and make sure to secure cloud amenities so as to be able to identify and act against any threats in real-time.
Even using new tools like AI and ML can boost the detection and prediction of threats —all of which work well to encourage security proactiveness rather than reactive remediation after the fact.
These can position an organization to better counter threats posed by its hired nuances and even those that may be external.
An incident response plan is important in cybersecurity because it helps you quickly detect, contain, and bounce back from attacks. Creating the plan factors in the technical, operational, and strategic responses to an organization’s compromised system, with each focusing on specific aspects like containment, system recovery, or long-term prevention.
A solid plan not only reduces the damage but also keeps the business running smoothly, helps you stay compliant, and lowers the chances of another attack.
Emerging technologies like AI are changing how we defend against cyber threats by making it easier to spot and react to attacks quickly.
Although, according to cybersecurity specialist Dr Haji Amirudin Abdul Wahab of the Ministry of Communications and Multimedia Malaysia (KKMM):
“AI presents a dual-edge opportunity – while it can enhance threat intelligence and automate detection and response, it can also be exploited by attackers.”
Projections for the next two years from the World Economic Forum’s 2024 Cybersecurity Outlook show that about 56% of AI’s benefits currently favor attackers.
Quantum computing is also being explored for its potential to revolutionize encryption methods, offering new, unbreakable codes that can protect sensitive data from even the most advanced threats.
Getting ahead with firsthand use of how these technologies work to secure your assets and how it can be reverse-engineered as an attacker’s tool can place your organization at both current and anticipatory advantages.


