Leading Autonomous Protection
One intelligent platform. Unprecedented speed. Infinite scale. Security that moves faster, protects stronger, and costs less.
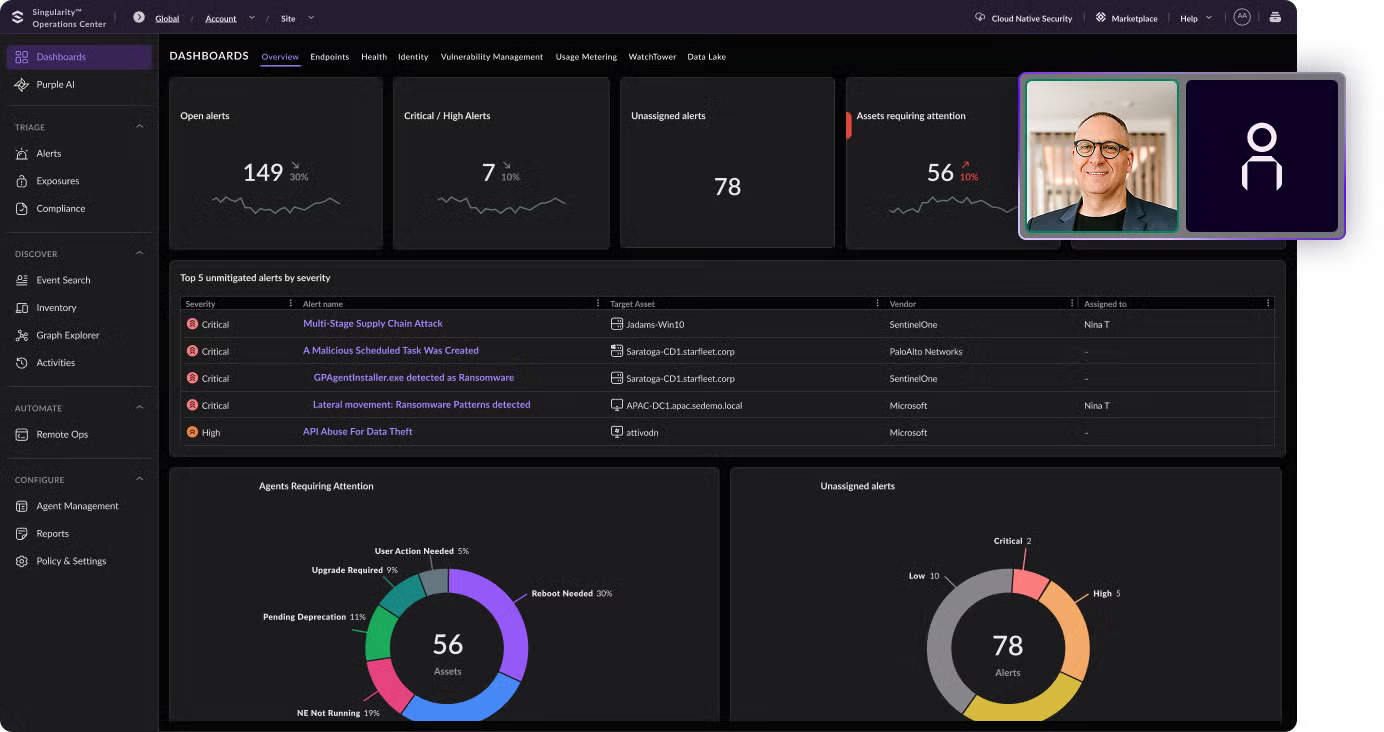
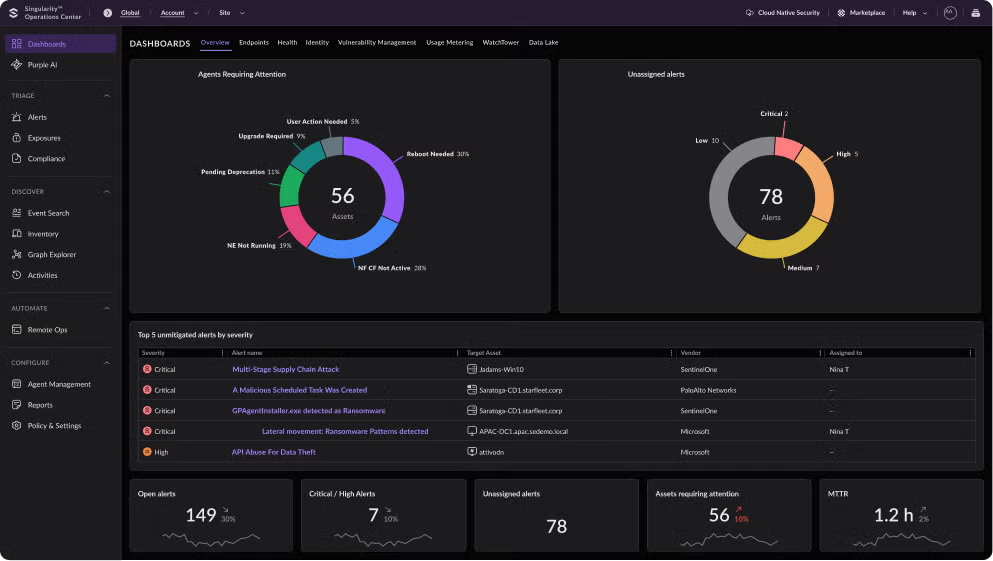
Stop threats before they start with the most advanced protection. Defend every edge of your enterprise with autonomous, AI-powered security.
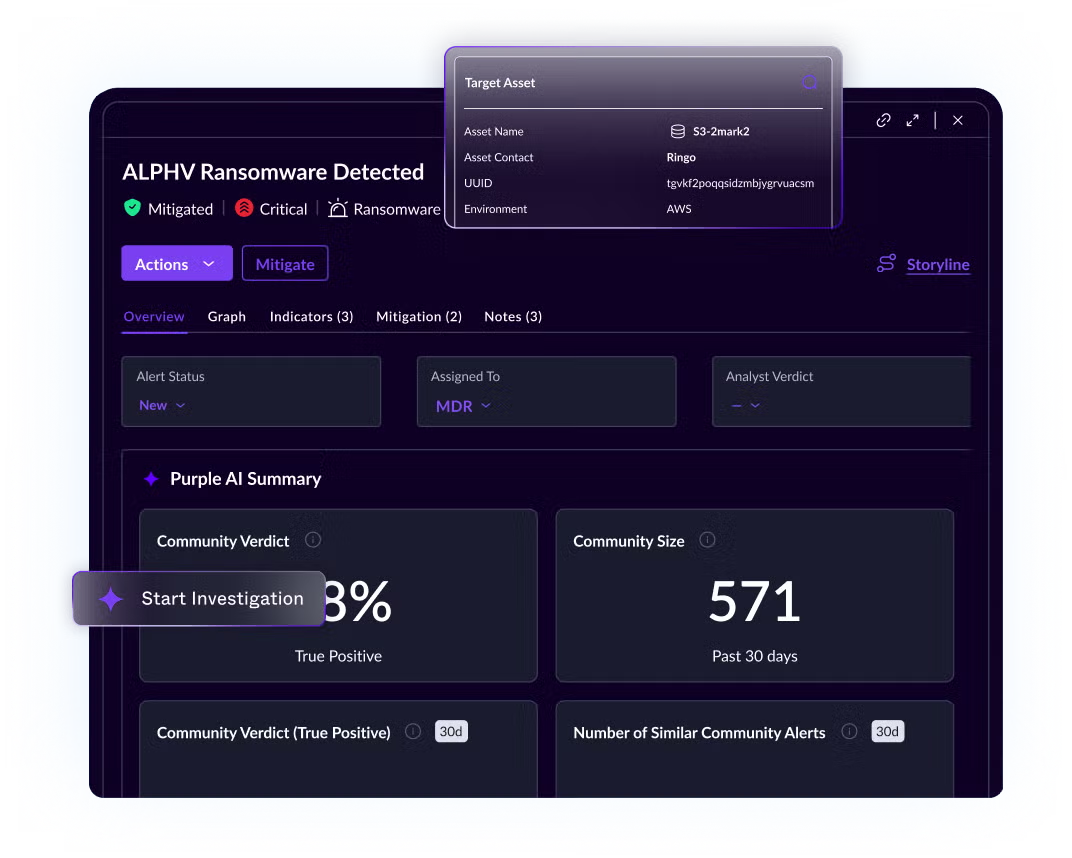
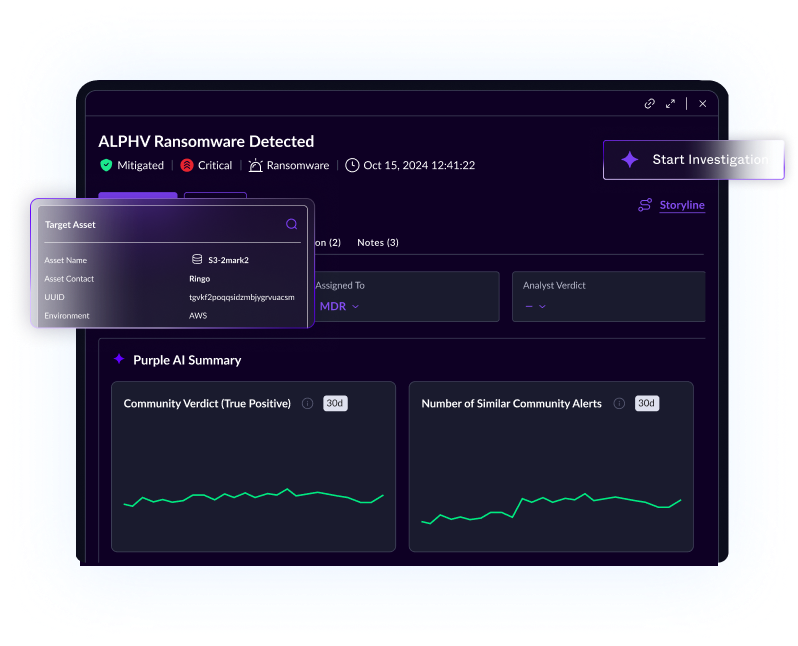
Supercharge your team with AI that accelerates investigations, boosts accuracy, and slashes response times—so analysts can focus on what matters.
Secure your cloud, endpoints, and identities with AI-powered protection, 24/7 threat hunting, and managed services — SentinelOne is redefining cybersecurity with the power of AI.
Tried and trusted by the industry's leading authorities, analysts, and associations.
A Leader.
Five Years Running.
A Leader. Five Years Running.
At SentinelOne, customers are #1. Global industry leaders across every vertical choose SentinelOne as their trusted cybersecurity partner.
“
SentinelOne is our defense so that we can focus on our offense.”
Brian Fulmer
Senior Director of IT | Golden State Warriors
“
SentinelOne was really like a self-driving car. It aided the team to do bigger and better things.”
Steve O'Connor
Director of IT | Aston Martin Lagonda LTD
“
SentinelOne has changed the way we do cybersecurity.”
Tony Tufte
IT Support Specialist | Norwegian Airlines

“
We chose SentinelOne because of the protection. We believe out of the independent testing that SentinelOne is doing the best job in the market.”
Friedrich Wetschnig
CISO & VP Enterprise IT | Flex
“
Innovation is king and we have to move fast. SentinelOne gives us the confidence to move quickly, knowing that it has our back.”
Lou Senko
Chief Availability Officer | Q2
The only CNAPP product to earn a 4.9 out of 5 rating. Over
240 awards—and counting.
Gartner Peer Insights recognized SentinelOne as a Customer’s Choice
for Endpoint Extended Detection and Response.

CNAPP customers rank SentinelOne highly in satisfaction,
innovation, and performance.
Unify Your Defense
Outpace Threats
Enhance Your Teams
See how the world’s most intelligent, autonomous cybersecurity platform can protect your organization today and into the future.