Recent events have highlighted the fact that security researchers are high value targets for threat actors, and given that we deal with malware samples day in and day out, the possibility of either an accidental or intentional compromise is something we all have to take extra precautions to prevent.
Most security researchers will have some kind of AV installed such that downloading a malicious file should trigger a static detection when it is written to disk, but that raises two problems. If the researcher is actively investigating a sample and the AV throws a static detection, this can hamper the very work the researcher is employed to do. Second, it’s good practice not to put known malicious files on your PC: you just might execute them by mistake and/or make your machine “dirty” (in terms of IOCs found on your machine).
One solution to this problem would be to avoid writing samples to disk. As malware reverse engineers, we have to load malware, shellcode and assorted binaries into IDA on a daily basis. After a suggestion from our team member Kasif Dekel, we decided to tackle this problem by creating an IDA plugin that loads a binary into IDA without writing it to disk. We have made this plugin publicly available for other researchers to use. In this post, we’ll describe our Memory Loader plugin’s features, installation and usage.
Memory Loader Plugin
If you have not used IDA Pro plugins before, a plugin basically takes IDA Pro database functionality and extends it. For example, a plugin can take all function entry points and mark them in the graph in red, making it easier to spot them. The plugin feature runs after the IDA database is initialized, meaning there is already a binary loaded into the database. A loader loads a binary into the IDA database.
Our Memory Loader plugin offers several advanced features to the malware analyst. These include loading files from a memory buffer (any source), loading files from zip files (encrypted/unencrypted), and loading files from a URL. Let’s take a look at each in turn.
Loading Files From a Memory Buffer
This plugin offers a library called Memory Loader that anyone can use to extend further the loading capability of IDA Pro to load files from a memory buffer from any source.
MemoryLoader is the base memory loader, a DLL executable, where the memory loading capabilities are stored. Its main functionally is to take a buffer of bytes from a memory buffer and load it into IDA with the appropriate loading scheme.
You will then have an IDA database file and be able to reverse engineer the file just as if it were loaded from the disk but without the attendant risks that come with saving malware to your local drive.
After you’ve analyzed the binary, save your work and close IDA Pro. The temporary IDA db files will be deleted and you will be left with your IDA database file and no binary on the disk.
Loading Files From a Zip/Encrypted Zip
MemZipLoader is able to load both encrypted and plain ZIP files into memory without writing the file to the disk. The loader accepts specific zip format files (.zip). After accepting a zip file, it will display the zip files and allow you to choose the file you want to work with.
MemZipLoader will extract the file from the input ZIP into a memory buffer and load it into IDA without writing it to disk and storing the encrypted zip file on your drive.
Loading Files From a URL
UrlLoader makes loading a file from a URL very easy. The loader is always suggested for any file you open. After you select UrlLoader, you will be asked to enter a URL, and the file downloaded will be stored in a memory buffer.
You will be able to reverse engineer the file and make changes to the IDA database. After you close the IDA window, you will be left with only the database file.
Installation Guide (tested on IDA 7.5+)
- Download zip with binaries from here.
- Extract the zip files to a folder.
- Place the loaders in the loaders directory of IDA.
-
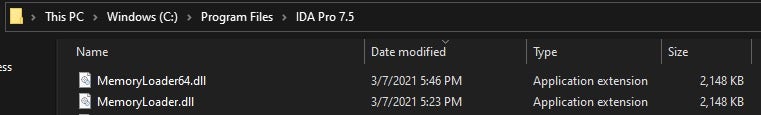
- MemoryLoader.dll -> (C:Program FilesIDA Pro 7.5)
- MemoryLoader64.dll -> (C:Program FilesIDA Pro 7.5)
-
- Place the memory loader DLL in the IDA directory folder.
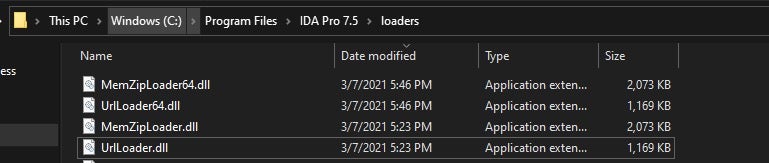
- MemZipLoader64.dll -> (C:Program FilesIDA Pro 7.5loaders)
- UrlLoader64.dll -> (C:Program FilesIDA Pro 7.5loaders)
- UrlLoader.dll -> (C:Program FilesIDA Pro 7.5loaders)
- MemZipLoader.dll -> (C:Program FilesIDA Pro 7.5loaders)
How to Use MemZipLoader & UrlLoader
You can load binaries with MemZipLoader and UrlLoader as follows:
MemZipLoader:
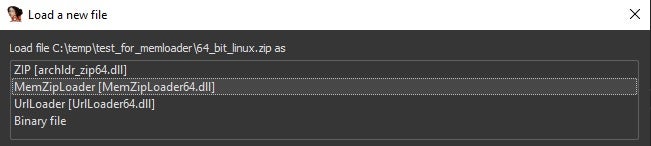
- Open IDA and choose zip file.
- IDA should automatically suggest the loader:
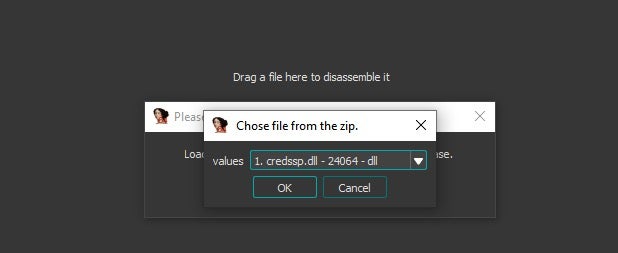
- Once selected, a list of the files from the zip will be displayed:
- IDA will then use the loader code and load it as if the binary was a local file on the system.
UrlLoader:
- Open any file on your computer in a directory you have write privileges to.
- The UrlLoader will suggest a file to open.
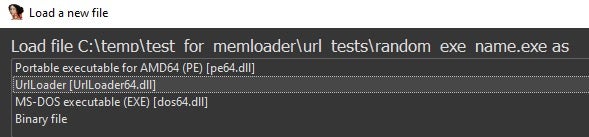
- After you chose UrlLoader, you will be asked enter a URL:
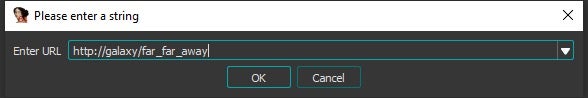
- The loader will browse to the network location you entered. Then IDA Pro will use the loader code and load the binary as if it was a local file.
Setting Up Visual Studio Development
In order to set up the plugin for Visual Studio development, follow these steps.
-
- Open a DLL project in Visual Studio
- An IDA loader has three key parts: the accept function, the load function and the loader definition block. Your dllmain file is the file where the loader definition will be.
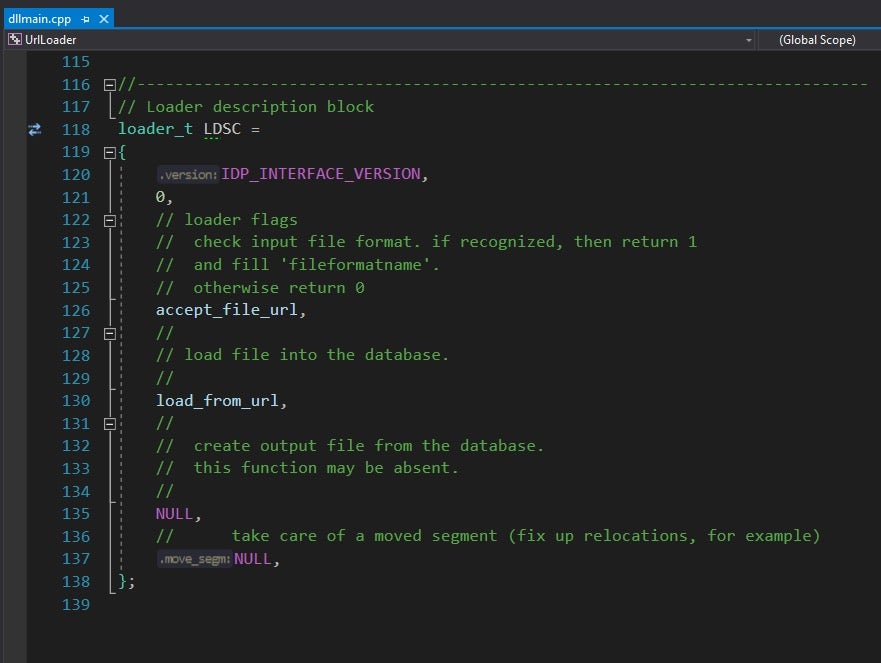
- accept_file – this function returns a boolean if the loader is relevant to the current binary that is being loaded into IDA. For example, if you are loading a PE, the
build_loaders_listshould returnPE.dllas one of the loading options.
- Open a DLL project in Visual Studio
load_file – this function is responsible for loading a file into the database. For each loader this function acts differently, so there is not much to say here. Documentation on loaders can be found here.
- The project can be compiled into two versions x64 for IDA with x64 addresses, and x64 for IDA x64 with 32 bit addresses. From this point forward we will mark them:
- X64 | X64 – 64 bit IDA with 64 BIT addresses
- X32 | X64 – 64 bit IDA with 32 BIT addresses
- Target file name (Configuration Properties -> Target Name)
- X64 | X64 – $(ProjectName)64
- X32 | X64 – $(ProjectName)
- Include header files: (Similar in: (X64 | x64) and( X64 | X32)
- Configuration Properties -> C/C++ -> Additional Include Directories – should point to the location of your IDA PRO SDK.
- Set Runtime Library -> Multi-threaded Debug (/MTd)
- Include lib files:
- X64 | X64
- idasdk75libx64_win_vc_64
- X64 | X64
- X64 | X32
- idasdk75libx64_win_vc_32
- idasdk75libx64_win_vc_64
- Preprocessor Definitions (Configuration Properties -> C/C++ -> Preprocessor Definitions):
- X64 | X64 add: __EA64__
- X32 | X64 add: __X64__, __NT__
- Preprocessor Definitions (Configuration Properties -> C/C++ -> Undefined Preprocessor Definitions):
- X32 | X64: __EA64__
-
Conclusion
When downloading malware to analyze from repositories like VirusTotal, the sample is usually zipped so that the endpoint security doesn’t detect it as malicious. Using our Memory Loader plugin will enable you to reverse engineer malicious binaries without writing them to the disk.
Using the Memory Loader plugin also saves you time analyzing binaries. When working with malicious content in IDA Pro often a different environment is created for it, usually in a virtual machine. Copying the binary and setting up the machine for research every time you want to open IDA is time-expensive. The Memory Loader plugin will allow you to work from your machine in a safer and more productive way.
Please note that a IDA professional license is needed to use and develop extensions for IDA Pro.
The SentinelOne IDA Pro Memory Loader Plugin is available on Github.




