Organizational defenders today face unprecedented pressure to keep up with a relentless stream of new attacks. No sooner than the latest campaign is discovered, indicators shared, and defenses bolstered, and we are on to the next one. The details of these attacks are added to our collective historical record, but most defenders rarely have time or motivation to reconsider what further value they might offer.
However, mining historical data for insight into tomorrow’s attacks is, we would argue, an undervalued resource. From expanding our list of known indicators and developing better threat intelligence to improving our understanding of attribution and providing new discoveries, investigating historical data is an asset that cyber defenders can and should make more of.
In this post, we explore practical ways that revisiting past cyber incidents can empower defenders and help to anticipate future threats more effectively.
1. Exploring the Past to Expand Actionable Threat Intelligence
In September of 2023, SentinelLABS observed a new threat activity cluster by a previously unknown threat actor we dubbed Sandman. The threat actor deploys malware utilizing the LuaJIT platform, a development paradigm relatively rarely seen in the cyberespionage domain, but which has an historical association with suspected Western or Western-aligned advanced threat actors.
Early last year, SentinelLABS released a report on a new cyber threat actor we named ModifiedElephant. This research was the conclusion of an investigation into an unknown offensive threat actor responsible for targeted attacks on human rights activists, human rights defenders, academics, and lawyers across India with the objective of planting incriminating digital evidence. Our analysis identified that ModifiedElephant has been operating since at least 2012 and continued to operate as of the report.
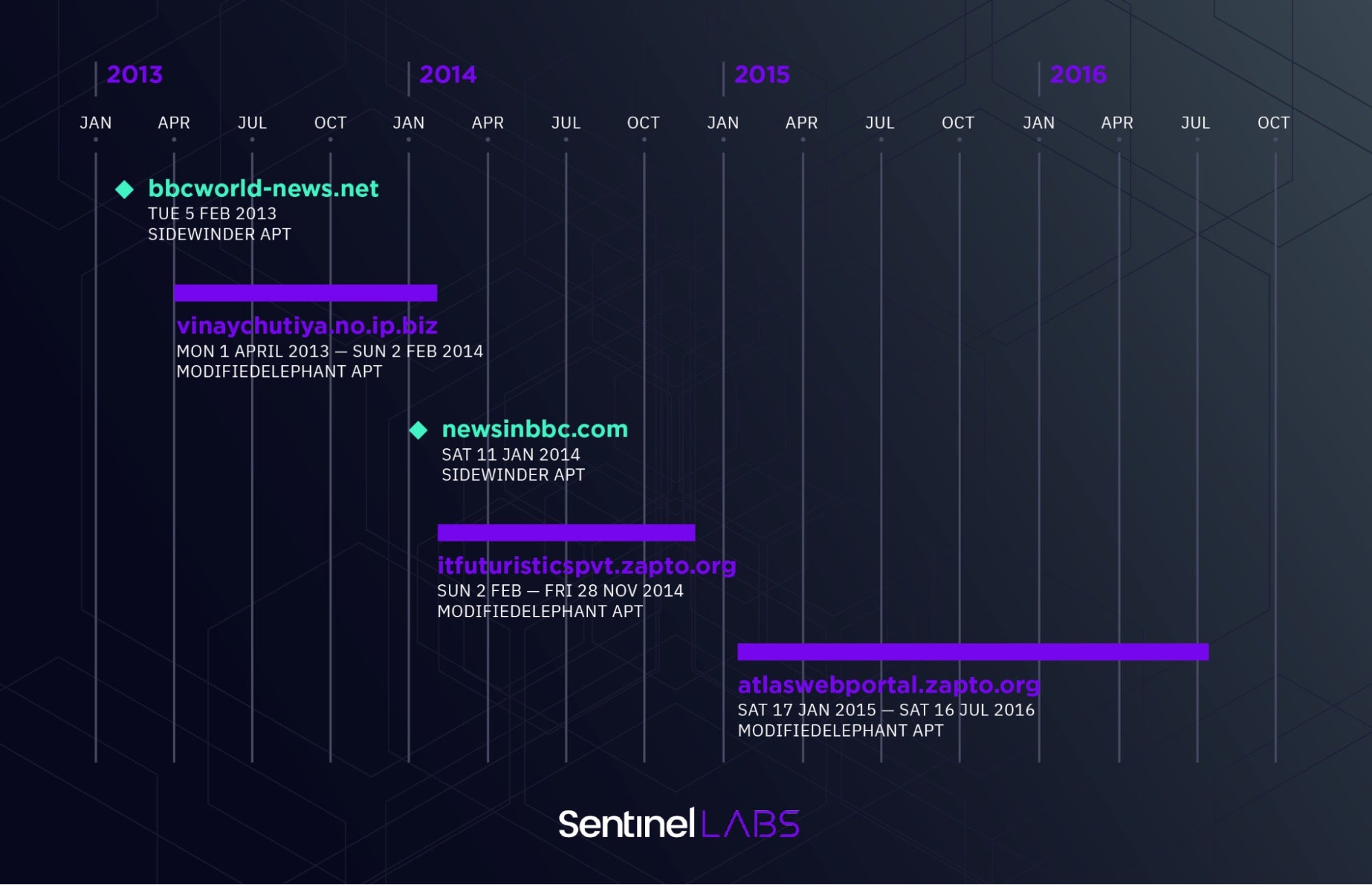
So why does this matter? Cyber paleontology allows us to take a small bit of knowledge of targeted intrusions, and expand it into hundreds of indicators of compromise, such as malware samples and unique infrastructure. In the case of ModifiedElephant, we tied the threat actor to hundreds of other intrusion attempts across the globe. This research found activity spread across nearly a decade, targeting individuals and organizations alike.
IOCs have been greatly expanded on, which allow us to improve the defenses of those who were originally targeted, and others who may be targeted in the future. If we simply stopped researching the threat actor based on the initial, smaller, case of a handful of intrusions against individuals, our perception of this actor would remain to be interesting but irrelevant to most. However, visiting a decade back of activity allows us to understand and use actionable intelligence for direct network defense needs.
2. Developing Better Strategic Threat Intelligence
Pushing past directly actionable intelligence such as malware samples, IOCs, and threat detection rules, we can also gain new strategic intelligence on threat actors. Specifically, our perspective of known threat actors can alter greatly when we review past intrusions.
For example, in September we reported and presented at LABScon the topic of China’s soft power agenda throughout Africa. In this research, we shared how Chinese attributed APTs, such as “Backdoor Diplomacy”, have been linked to a previously-reported set of intrusions across South Africa, Kenya, Senegal, and Ethiopia in the past few years.
Revising previously reported infrastructure associated with the threat actor opened our eyes to a wider set of targets in these countries, and a set of targets we have not observed before, including financial organizations. Today, we can use this expanded understanding of the threat actor to apply strategic intelligence for financial organizations and the countries newly observed of interest to the attacker.
Taking a similar approach to others, it would be valuable to dive into high-interest threat actors to question our past assessments and intelligence, aimed at expanding defense capabilities and context today.
3. Enhancing Our Understanding of Attribution
An additional value which can come from a fresh review of historical threat activity concerns attribution – the process of identifying the true attacker behind an activity.
Past intrusions can become clearer based on understanding who the attacking entity actually was, or understanding which threat actor cluster some previously unknown activity may now fall under. For example, in August, we identified malware, with a long history of use by a variety of suspected Chinese clusters, and infrastructure targeting Southeast Asia’s gambling sector related to previous activities attributed to BRONZE STARLIGHT, a Chinese threat actor whose main goal appears to be espionage rather than financial gain.
In addition, we recently reported on the Appin hack-for-hire business in India and how unconfirmed and mysterious activity years back can finally be attributed to them. This includes Operation Hangover, the well known industrial espionage case, and targeting of human rights malware with custom Mac malware.
![C2 / Delivery Server bluecreams[.]com and Linked Malware Visualized](https://www.sentinelone.com/wp-content/uploads/2023/11/Appin_2.jpg)
4. Newer Techniques Offer Fresh Insights From Old Data
Using today’s technology to expand past context and knowledge of attackers is also increasingly valuable to modern defenders. The technology sector evolves at a blistering pace, and new research tools often arrive to provide new capabilities.
Although much recent focus has been on adopting and adapting LLMs and generative AI for various infosec tasks, we can also see examples of existing technologies that continue to develop and push the boundaries of what is possible.
One of the best examples of this is YARA— today’s go-to tool for malware description rules used to hunt for various types of files, such as malware or files of high interest. YARA continues to be developed in ways that can yield new discoveries from old datasets. New rule writing methods, combined with major malware repositories such as Stairwell and VirusTotal, can lead to the discovery of leaked attacker files, targeted malware family changes, and uploads of never before seen malware from past attacks.
Combining new discoveries with other tools for tracking infrastructure, like SilentPush, it is possible to make similar high interest discoveries centered around old attacker infrastructure.
Conclusion
As we move forward, it’s important not to lose sight of the past. As many of our research examples highlighted above show, retrospective analyses can wring new actionable intelligence from the raw data of past breaches and help to preempt future attacks.
We encourage other analysts to join us in connecting the dots between what was known, what was overlooked, and what can be learned, taking advantage of the insights that new technologies and methods afford us. Historical data isn’t just an academic record of what went before, but a resource we must mine to craft a more resilient and responsive cybersecurity posture.




