Threat hunting is a proactive approach to identifying and mitigating cyber threats before they cause harm. This guide explores the principles of threat hunting, its benefits, and the techniques used by security professionals.
Learn about the importance of threat intelligence and continuous monitoring ineffective threat hunting. Understanding threat hunting is essential for organizations looking to enhance their cybersecurity posture.
 What is Cyber Threat Hunting?
What is Cyber Threat Hunting?
Cyber threat hunting is proactively and systematically searching for signs of potential cyber threats within an organization’s network or systems. This can be done through manual and automated techniques, such as analyzing log data, conducting network scans, and using threat intelligence feeds. Cyber threat hunting aims to identify potential threats that may have evaded traditional security controls, such as firewalls or intrusion detection systems. By detecting and responding to these threats early, organizations can reduce their risk of being impacted by a cyber attack and maintain the security and availability of their systems and networks.
Threat hunting can be defined as a practice designed to help you find adversaries hiding in your network before they can execute an attack or fulfill their goals. Unlike most security strategies, threat hunting is a proactive technique that combines the data and capabilities of an advanced security solution with the strong analytical and technical skills of an individual or team of threat-hunting professionals.
Threat hunting is quite a different activity from either incident response or digital forensics. The purpose of DF/IR methodologies is to determine what happened after a data breach has already come to light. In contrast, when a threat-hunting team engages in threat hunting, the aim is to search for attacks that may have already slipped through your defensive layers.
Threat hunting also differs from penetration testing and vulnerability assessment, too. These attempts to simulate an attack from the outside, whereas threat hunters work from the premise that an attacker is already in the network and then try to look for indicators of compromise, lateral movement and other tell-tale artifacts that may provide evidence of attack behavior.
What Do You Need to Start Threat Hunting?
As we’ve seen, the cyber threat hunting process is all about aggressively seeking out hidden IOCs and covert behavior by assuming a breach has occurred and then searching for anomalous activity. To do that, security analysts must separate the unusual from the usual, filtering out the noise of everyday network traffic in search of as yet-unknown activity.
Doing that effectively begins with comprehensive visibility into your network and rich data from your endpoints. Device telemetry should include things like encrypted traffic, file hashes, system and event logs, data on user behavior, denied connections trapped by firewall controls and peripheral device activity. Ideally, you want tools such as SIEM (Security Information and Event Management) that allow a clear overview of all this data with powerful search capabilities that can contextualize what you see to minimize the amount of manual sifting through raw logs.
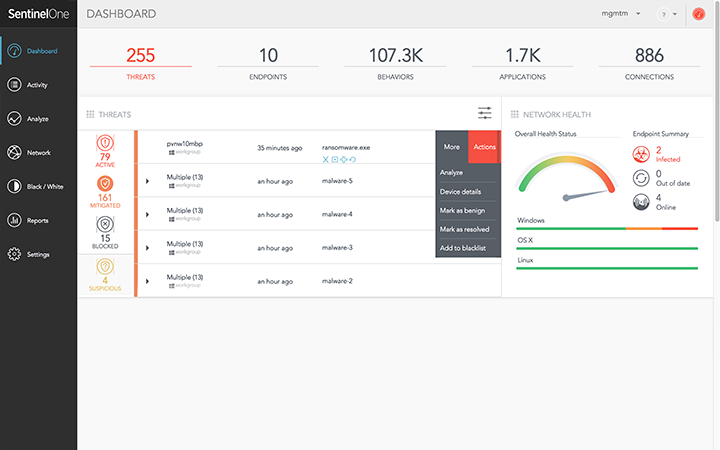
Features that can report unmanaged endpoints, IoT devices, and mobiles and discover running services on your network are a major boon, as are utilities that you can incorporate into your browser to speed up threat detection and research.
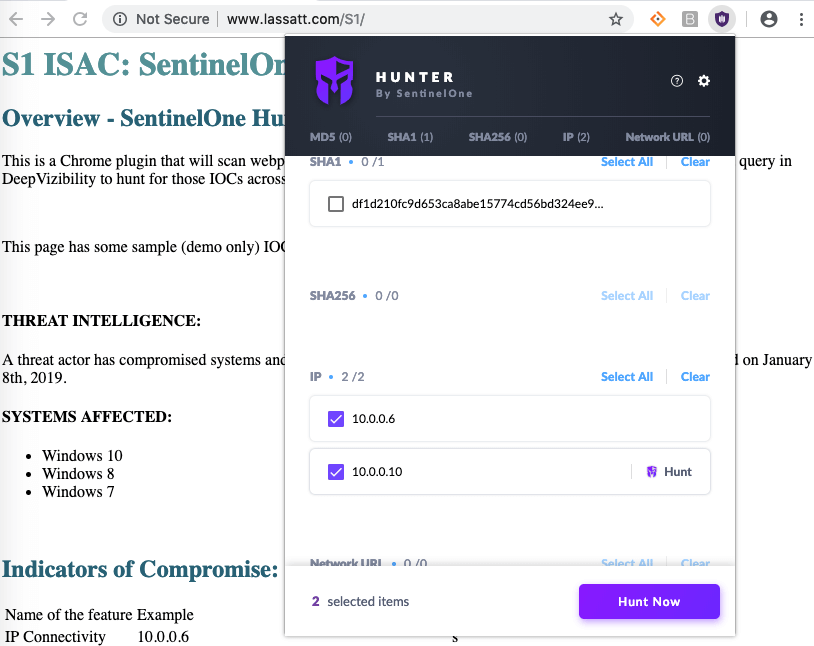
A threat-hunting program requires proper reporting tools to provide analysts with quality data, but it also presupposes that they have full confidence in the security solutions protecting their network. Threat hunting is time-consuming, and your SOC (Security Operations Center) analysts can’t afford to waste time manually catching threats that your EDR solution should have found for them autonomously. Detecting advanced threats is the most difficult challenge security teams face, particularly if the organization is limited by a cyber skills staff shortage or is stuck with an infosec (Information Security) solution that swamps them with masses of alerts or a high degree of false positives.
Another vital security tool for analysts is good threat intelligence. There are several public or OSINT (open source intelligence) feeds where hunters can keep up to date with the latest IOCs, such as malicious IP addresses, newly announced CVEs and sample hashes of the newest malware. For example, the SANS institute keeps a compiled list of suspicious domains. The MITRE ATT&CK framework is also a powerful tool to help cyber threat hunters learn about the tools, tactics and procedures (TTP) used by advanced threat actors. You can, for example, search the MITRE ATT&CK database for groups that are known to target your sector or industry and learn about the techniques they have used. Armed with this intel, you can start to threat hunt across your network for evidence of that group’s TTPs. For more information on the steps needed for Threat Hunting, read our white paper.
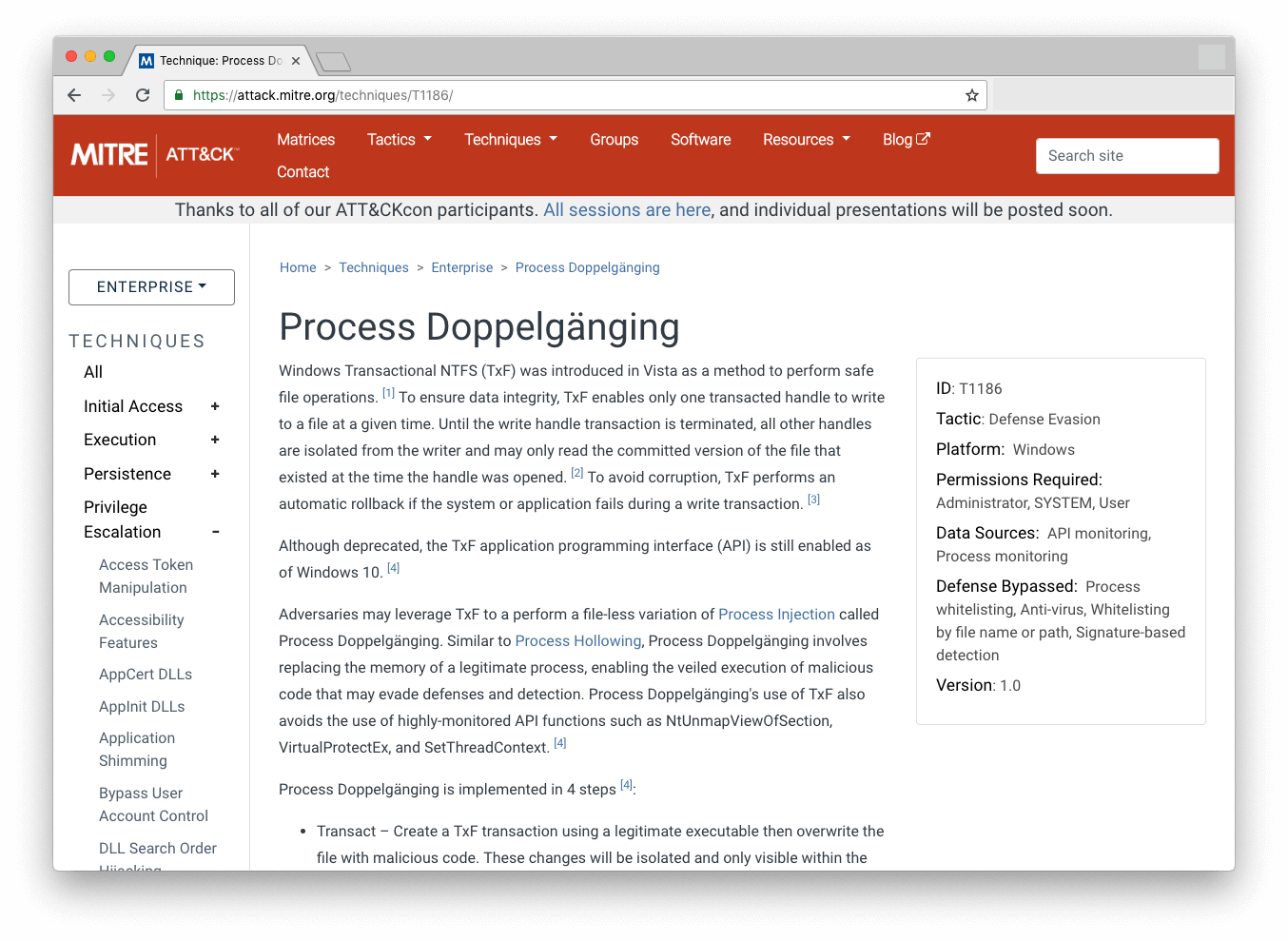
How Do You Know What to Look For?
Using OSINT tools and frameworks like MITRE ATT&CK only works effectively if you know what you’re looking for, and that brings us to one of the essential components of effective threat hunting: hypothesis formation and testing.
Threat hunters need a solid understanding of the organization’s profile, business activities that could attract threat actors (such as hiring new staff or acquiring new assets, companies, etc), and baseline usage.
Attackers will often want to blend in with ordinary users and try to acquire user credentials such as from a phishing or spear phishing campaign, so understanding users’ typical behavior is a useful baseline for investigating anomalous file access or log in events. Combining that with understanding what company data is of value to attackers and where it is located can lead to hypotheses such as “Is an attacker trying to steal data located at xyz?”. This in turn could prompt data collection that answers questions such as:
“Which users have accessed location XYZ for the first time in the last n days?”
Advanced threat-hunting techniques will try to automate as many tasks as possible using statistical analyses and machine learning. Monitoring user behavior and comparing that behavior against itself to search for anomalies, for example, is far more effective than running individual queries, though both techniques are likely to be required in practice. Both are made easier if you have tools like SentinelOne that have a rich set of native APIs enabling full integration across your security software stack.
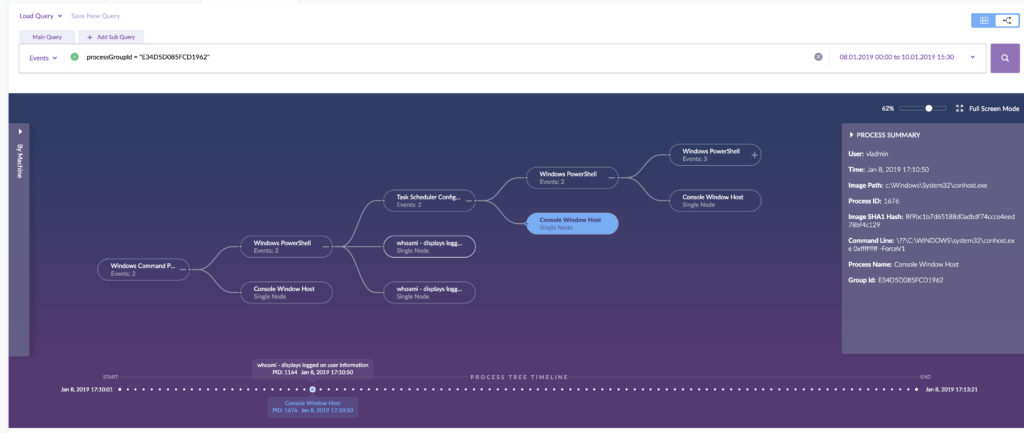
How Often Should You Threat Hunt?
Some businesses only hunt for new threats on an ad hoc basis. This might be triggered when a certain event (e.g., an access attempt on a particularly sensitive service or file location) or staff has free time from other duties. While ad hoc hunting allows organizations with restricted staff and budgets to still engage in this extra layer of defense, it has the drawback of only allowing minimal hunts for a limited set of behaviors and is the least effective way to employ the strategy.
Scheduled threat hunting, where time is dedicated for staff to conduct hunts at regular intervals, is an improvement and can allow organizations to prioritize searches at different times and improve efficiency. However, scheduled threat hunting has the drawback of offering a certain dwell time for advanced attacks to try to operate in between those intervals, so the shorter the interval, the better.
Ideally, organizations with sufficient staff and budget should engage in continuous, real-time threat hunting in which the network and endpoints are proactively engaged to uncover attacks on the network as part of a sustained effort.
Who Should Conduct Your Threat Hunting?
It’s probably clear by now that threat hunting is a specialist task. It requires a security analyst who can use various tools, understand and analyze the risks your organization faces, and is versed in the methods and tools used by advanced attackers.
While hiring in-house threat hunters can be a great way to go, organizations need to have the budget for it and access to people with the relevant skills. For many enterprises, a more realistic approach can be to engage threat hunting services from MSSPs (Managed Security Service Providers) for some or all of their threat hunting work.
 Enhance Your Threat Intelligence
Enhance Your Threat Intelligence
See how the SentinelOne threat-hunting service WatchTower can surface greater insights and help you outpace attacks.
Learn MoreConclusion
Threat hunting allows you to get out in front of the latest threats by proactively hunting for malicious activity. Advanced solutions like behavioral AI will stop most cyberattacks in their tracks and are prerequisites to providing the visibility threat hunting requires, but malicious actors are always innovating and looking for ways around enterprise network security. Organizations need to be vigilant to prevent vectors such as insider threats and highly targeted attacks. Adding the expertise of human analysts can provide that extra layer of security for your organization.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- Zero Day Survival Guide | Everything You Need To Know Before Day One
- 7 Tips To Protect Against Your Growing Remote Workforce
- Bluetooth Attacks | Don’t Let Your Endpoints Down
- What is Network Security in Today’s Day and Age?
- How Hacker’s Use Social Media To Profile Targets
Threat Hunting FAQs
Threat hunting is the practice of actively searching for cyber threats hiding in your network. Instead of waiting for alerts to tell you there’s a problem, threat hunters assume attackers are already inside and look for signs of malicious activity. They dig deep into security data to find threats that automated tools might have missed.
It’s like having a security expert constantly patrol your network, looking for anything suspicious or out of place.
A threat hunter might notice unusual network traffic patterns that suggest data is being stolen. They could investigate why a user account is accessing files at 3 AM or why there are suspicious login attempts from different countries. Another example is looking for specific malware signatures based on new threat intelligence reports.
They might also search for indicators that match known attack methods, like checking if systems show signs of lateral movement by hackers.
Threat hunting is important because sophisticated attackers can slip past your automated security tools and hide in your network for months. The average time to detect a breach is 194 days, which gives attackers plenty of time to steal data. Threat hunting helps you find hidden threats faster, reducing the damage they can cause.
Threat hunters start by creating hypotheses about potential threats based on threat intelligence or unusual activity. They then search through network logs, endpoint data, and security alerts to find evidence that proves or disproves their theories.
If they find something suspicious, they investigate further to determine if it’s a real threat. The process is continuous and iterative, with hunters constantly refining their techniques based on what they discover.
The four main types of cybersecurity threats are malware, which includes viruses and ransomware that can damage your systems. Phishing attacks trick people into giving away passwords or clicking malicious links. Distributed denial-of-service attacks overwhelm your systems with traffic to make them unavailable.
Advanced persistent threats are sophisticated, long-term attacks where hackers hide in your network for extended periods. Each type requires different detection and response strategies.
Common threat hunting techniques include clustering, where you group similar data points to spot anomalies. Stacking involves organizing data into categories and looking for outliers that seem suspicious. Baselining means understanding what normal network activity looks like, then searching for deviations.
Analysis involves examining logs and security data to identify patterns that might indicate threats. Grouping combines multiple indicators to see if they appear together in suspicious ways.
Threat hunting is proactive and ongoing, while incident response is reactive and triggered by alerts. Threat hunters actively search for threats before they cause damage, but incident response teams react after an attack has been detected.
Threat hunting is like a continuous patrol, while incident response is like emergency services responding to a fire. Forensics happens after an incident to understand what happened, but threat hunting tries to prevent incidents from occurring.
The threat hunting process has three main steps: trigger, investigation, and resolution.
- In the trigger phase, hunters identify what they want to investigate based on threat intelligence, anomalies, or specific hypotheses.
- During investigation, they search through data to find evidence that supports or disproves their theory.
- In the resolution phase, they document their findings and either escalate real threats to incident response teams or update their knowledge for future hunts.


