Network security is a high priority for any business these days. With many organizations having a distributed workforce, multiple OS platforms to support, and an increasing number of IoT devices coming into play, managing the security of an organization’s network and the vital data it carries can be a complex task.
There are a multitude of tools, applications and utilities on offer to help secure your network, but just where do you start and how can you be sure that what you’ve implemented is really keeping you protected? In this post, we take a look at the fundamentals of modern network security to give you a head start.

What is Network Security?
What is Network Security? With so many terms bandied around in the world of cybersecurity it can be difficult to get a clear sense of the scope of such a broad term as ‘network security’. Let’s start by contrasting ‘network security’ with ‘endpoint security’. Whereas endpoint security concerns protecting a device from intrusion and misuse, network security is the same concerns applied to the entire network of interconnected devices in your organisation, and that includes the devices themselves and the data communicated between them, both in transit and at rest.
That definition means that endpoint security is part-and-parcel of your network security – a compromised device can serve as a pivot point into other devices on your network – but there’s much more to it than that. There’s also the question of how you control both users and devices within your network and how you detect and respond to anomalous behavior.
Network security also incorporates the policies and procedures you put in place to protect your assets such as password management, two-factor authentication and even three-factor authentication such as fingerprint identification and facial or retinal scans.
Importance of Network Security
Once upon a time, an organisation would put up a firewall and conduct all its activities behind that supposedly impenetrable wall. However, as organisations have changed their practices and attackers have changed their tools, tactics and procedures, simply relying on a firewall has become increasingly inadequate.
With many organisations now using or moving to cloud or hybrid cloud technology, mobile devices and remote workers, as well as communication across timezones, it’s simply not realistic to expect all your users to be sitting cosily side-by-side on a corporate network.
More importantly, relying solely on a firewall presents a single-point of failure. Aside from the denial of service attacks against your perimeter, modern networks are under increasing risk of being penetrated through supply-chain attacks, DNS hijacking, phishing and spear-phishing campaigns and fileless malware, to name just a few. The modern threatscape essentially means that security needs to be distributed throughout your endpoints, rather than concentrated around the edges with a few supposedly “iron boxes”. If not, your network becomes entirely vulnerable once that thin outer layer is penetrated.
Network security is also not just about external threats, but also the misuse or abuse of data and company assets by internal threats, too. For example, nearly a third of all data breaches in the healthcare industry have been attributed to insiders, either from wrongdoing or human error. In the financial sector, some 60% of cyber-attacks have been attributed to privileged users, third-party partners, or malicious employees.
How Does Modern Network Security Work?
Because of the need to protect at more than just the perimeter, modern network security takes a defense in depth approach. It all begins with visibility because you cannot protect against a threat that you cannot see. Therefore, modern network security requires that all endpoints have protection that offers admins the ability to see into their traffic, including encrypted traffic, as many threat actors have already moved to using SSL certificates and https connections.
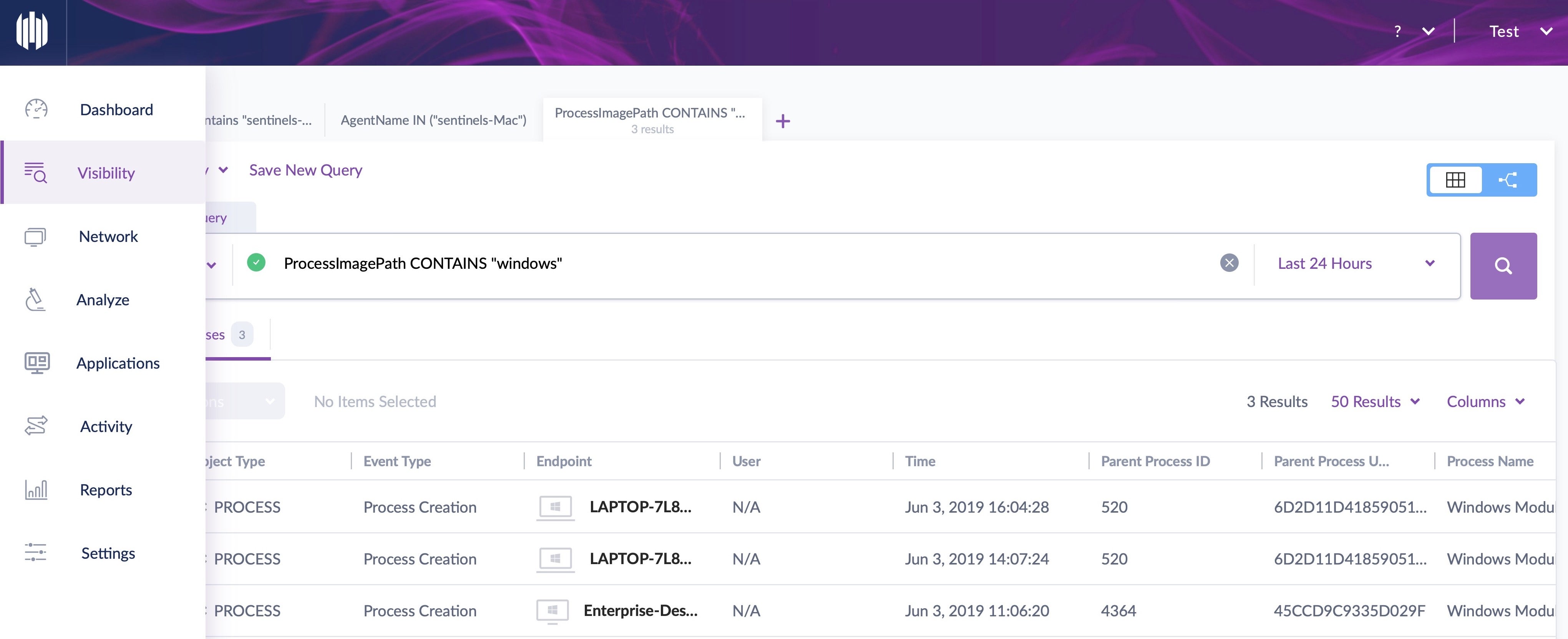
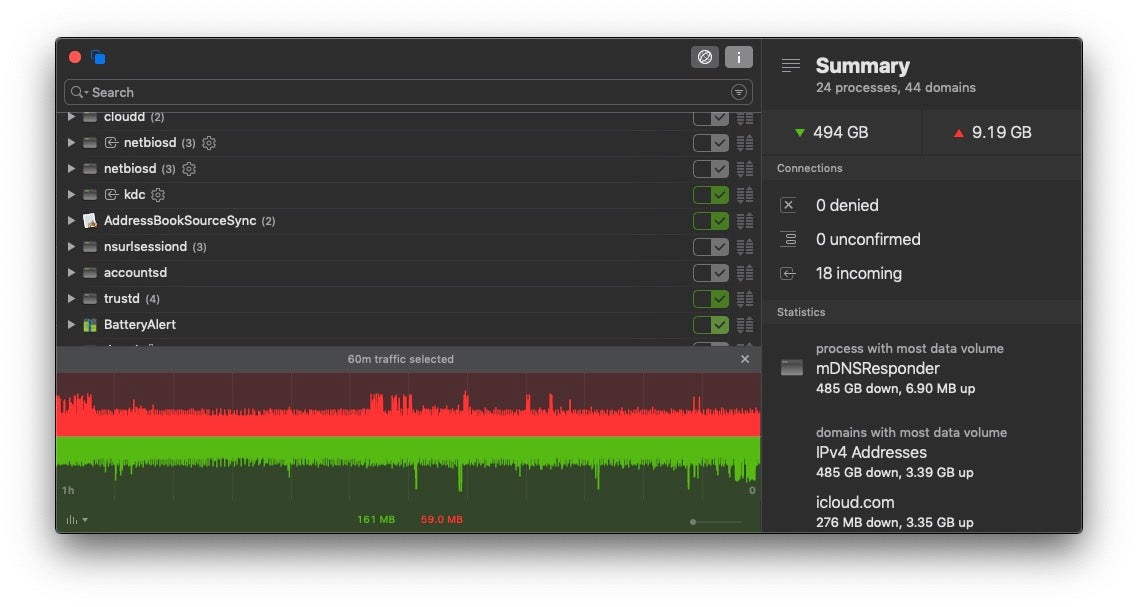
Once you have visibility, defense in depth can be applied by first thinking about prevention. Ensure that access control policies are in place that will block unauthorized use, and limit the access of authorized users to the assets that they need. If you have, for example, a network with a bunch of IoT devices connecting to it, there’s really no need for those devices to access large parts of your network that are unrelated to their intended functions.
Devices should also have security software that incorporates application Firewall controls. This allows the network admin to manage permitted traffic to and from every endpoint. On top of that, device control to prevent attacks from malicious USBs and other peripherals is also an essential part of protecting your network through securing ports that can be physically accessed on your endpoints.
After prevention, the next layer of defense in depth is detection. That means looking for and recognising anomalous behavior. The best way to do this is through behavioral AI software, but beware that not all “Next-Gen” security solutions are created equal. Just how effective they are depends greatly on the datasets the AI has been trained on, rather than any particular algorithm.
A modern approach to network security means realising that breaches are sometimes going to happen. The attack surface is so vast that it would be naive to think that your prevention and detection is undefeatable by a determined attacker. Therefore, you need a response plan, aided and abetted by security solutions that can take autonomous action to remediate threats when they are detected.

In the longer term, think about how you can incorporate a DevOps or SecOps mindset into your organizational management. With these kinds of approaches, network security becomes an intrinsic consideration at every level of decision-making.
How Can Network Security Be Tested?
So how can you know if your defenses are good enough? This is where network security testing comes into play. Vulnerability assessment, also commonly known as “pentesting“, involves simulating attacks against your own network to see how your tools, people and procedures hold up against an attacker. “Stress testing” your defenses takes skill – and permission – and is best undertaken by qualified penetration testers with clear limits and objectives agreed beforehand.
Exactly what a penetration test will involve depends on the specific terms you agree with your tester, but there are typically three stages: a vulnerability scan, an in-depth penetration test and a risk analysis performed on any vulnerabilities discovered.
Preliminary scans are often undertaken with automated tools that look for known CVE vulnerabilities. While these are useful to cover the basics, they will not offer insight into unreported vulnerabilities nor test the strength of your defenses under active or persistent attack.
An in-depth penetration test, however, if conducted by a suitably qualified “white hat” or “ethical hacker” should do exactly that, but it’s important to work with your tester to agree the rules of engagement and the scope of the test. Commonly deployed tools include metasploit, burp, wireshark, nmap and include various ways to get domain admin access on your internal network. However, be sure your tester is doing more than just running “off-the-shelf” attacks and is actually capable of customising his attacks to the attack surface your environment presents.
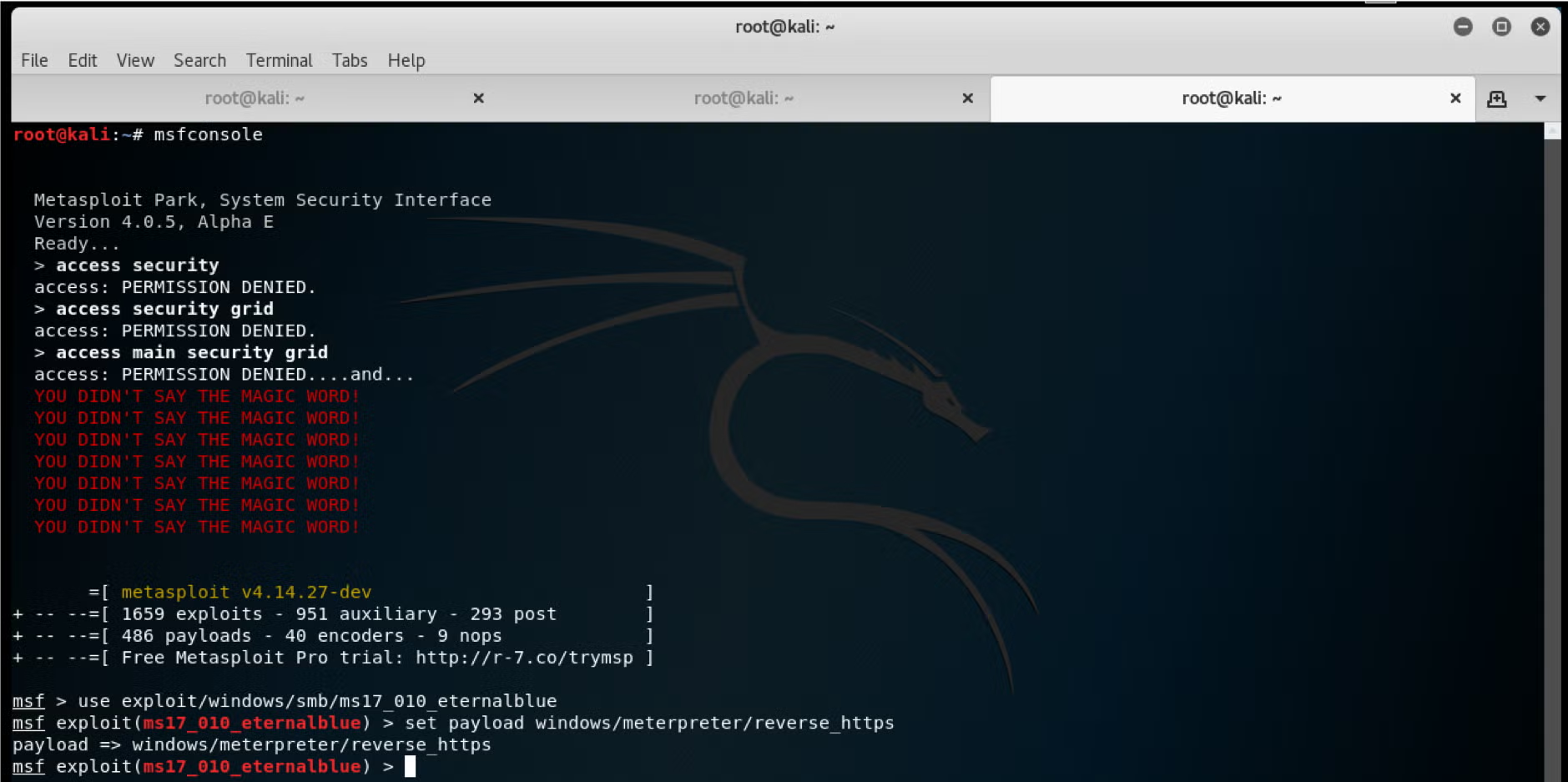
Regardless of whether your pen tester performs the risk analysis stage or not, the outcome of a good penetration test should be a clear, digestible and itemised report – not a hocus-pocus of high-level geek-speak – detailing any vulnerabilities. Expect and insist upon clear instructions that will enable you or your own IT staff to reproduce the issue. If it isn’t reproducible by your own team, you cannot confirm that it’s a real security vulnerability.
A good penetration tester should also provide recommendations on mitigation, although these always need to be taken in light of your organization’s other needs and priorities. Either the tester or another analyst should conduct a risk analysis of specific vulnerabilities. Does the vulnerability represent a financial risk, possible data loss or compliance failure? What is the likelihood of it being exploited and the potential impact on the company?
Conclusion
It is important for your organization to deliver services customers and employees demand, but to do so you need to protect your network. Good network security not only helps protect your IP and customer data, it also protects your reputation. By combining multiple layers of defense throughout your network – not just at the perimeter – with appropriate policies, controls and a Next-Gen endpoint security solution, you can give authorized users access to the network resources they need while blocking those trying to carry out attacks.
If you’d like to see how the SentinelOne solution can help you in this fight, listen to our customers explain why they chose SentinelOne or better still, give it a try for yourself with a free demo.
AI-Powered Cybersecurity
Elevate your security posture with real-time detection, machine-speed response, and total visibility of your entire digital environment.
Get a DemoNetwork Security FAQs
Network security is the practice of protecting data and resources as they travel across or connect to networks. It uses firewalls, intrusion detection systems, antivirus software, and encryption to block unauthorized access. By monitoring traffic, controlling access points, and enforcing policies, network security keeps attackers from intercepting data, planting malware, or using your systems as a launchpad for further attacks.
Without network security, sensitive data—like customer records, financial details, or proprietary plans—can be stolen or altered. Attacks can disrupt services, harm reputation, and lead to legal fines. Good network security makes sure employees can work safely, partners can connect securely, and customers can trust your systems. It also helps you spot and stop threats before they spread and cause major downtime.
Key parts include firewalls that filter incoming and outgoing traffic; intrusion detection and prevention systems that flag suspicious behavior; virtual private networks (VPNs) for secure remote access; and endpoint protection on devices. Encryption scrambles data in transit, while security information and event management (SIEM) tools collect logs and alerts. Together, these layers form a defense-in-depth strategy.
Network segmentation splits a large network into smaller zones or subnets, each with its own access controls. If attackers breach one segment, they can’t easily move to others. Segmentation limits the spread of malware, lets you apply different security rules to sensitive zones, and helps contain incidents.
You can group devices by function—like servers, workstations, or guest Wi-Fi—to tailor protections for each.
Authentication checks who you are—usually via passwords, certificates, or tokens. Authorization decides what you can do once you’re in, like which servers you can reach. Accounting logs your actions, recording access times and resources used.
Together, AAA ensures only valid users connect, they only do permitted tasks, and you can trace their activities for audits or incident response.
Attackers often use Denial of Service (DoS) or Distributed DoS to flood systems, making them unavailable. Man-in-the-Middle attacks intercept and alter data in transit. Phishing and social engineering target users to steal credentials. Malware campaigns drop viruses, worms, or ransomware onto devices. Port scanning and vulnerability exploits probe for weak spots in software or open services.


