Executive Summary
- SentinelLABS has analyzed a data leak containing infrastructure details and work logs from employees of a state-affiliated private sector security firm in China.
- The leaked data contains references to web content monitoring services used to enforce censorship for public and private sector customers.
- Work logs reveal that the firm provided bespoke monitoring services to a state-owned enterprise when a corruption scandal impacted this organization, providing insights into how the state and CCP coordinate with some cybersecurity companies to manage fallout from corruption scandals.
Overview
SentinelLABS has analyzed a data leak from TopSec (北京天融), a Chinese cybersecurity firm offering services such as Endpoint Detection & Response (EDR) and vulnerability scanning, while offering boutique solutions to align with government initiatives and intelligence requirements.
The data leak includes a document with 7,000+ lines of work logs and code used to orchestrate infrastructure for the firm’s DevOps practices and downstream customers and includes scripts that connect to several Chinese government hostnames, academic institutions and news sites.
We identified work logs and system features that indicate TopSec is likely enabling content moderation for internet censorship purposes, a key strategy used by the Chinese Communist Party (CCP) to monitor and control public opinion on issues that the state deems contentious or antisocial.
Further, we found evidence indicating that TopSec provided bespoke services to a state-owned enterprise on the date that a corruption investigation was announced targeting the organization’s top official.
The Chinese cybersecurity market has long been a mystery for many researchers in the west. Unlike Europe and parts of the Middle East, which foster some degree of collaboration, the Chinese cybersecurity market is obscured behind the wall that divides China from the global internet. This finding reveals not only the types of technologies that are used by a prestigious Chinese tech firm, but how they are providing security services to private and public sector customers inside China.
TopSec
TopSec is a provider of monitoring and IT security solutions, as well as big data and cloud services. Established in 1995, TopSec prides itself on its long history and prioritizes national cyberspace security as a core element of its mission statement.
Company registration details reveal that TopSec holds over 1,000 patents, 87 software copyrights, and has 12 subsidiaries. The company is also a Tier 1 vulnerability supplier to China’s civilian intelligence ministry. According to TopSec’s 2024 annual corporate report for shareholders, the company has been offering cloud monitoring services–including IT security monitoring capabilities–since 2004. By 2020, these TopSec services were in use across all 31 of China’s administrative regions.


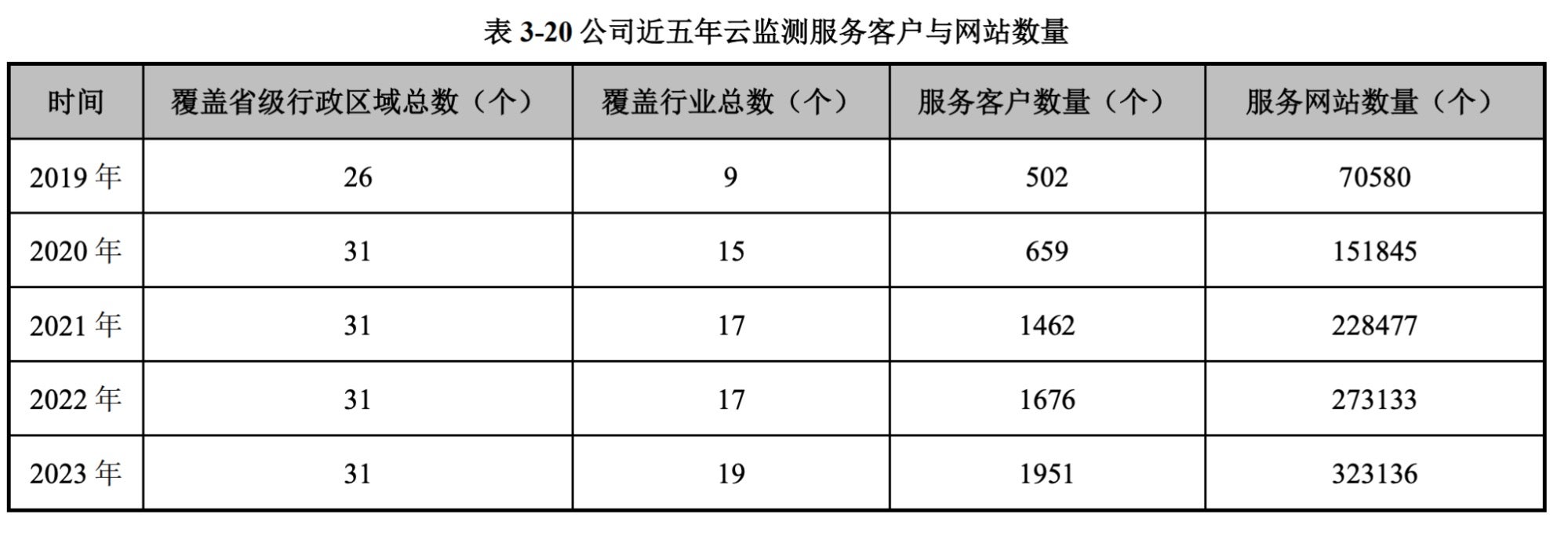
The leaked documents we analyzed reference multiple organizations in both the private and public sectors, likely customers or otherwise associated with TopSec, a selection of which is listed below. These references include probable deployment sites of monitoring probes and mentions in-work progress records.
Public sector organizations referenced in the documents include entities integral to China’s political system, such as the Municipal Commissions for Discipline Inspection, which enforce party regulations and investigate corruption. Another example is the Illegal and Harmful Information Reporting Center, an entity dedicated to combating what the Chinese Communist Party (CCP) considers illegal and harmful behavior in the online space. TopSec customers referenced in these documents include:
- Dongwu Fund Management Co., Ltd
- Gucheng County Petition Bureau
- Illegal and Harmful Information Reporting Center
- Linhai Rural Commercial Bank
- Petkit
- Shanghai Diepai Automobile Technology Co
- Shanghai Fengyilong Electronic
- Shanghai Medical Packaging Materials Factory
- Shanghai Municipal Commission for Discipline Inspection
- Shanghai Municipal Supervisory Commission
- Tibet Autonomous Region
- Tibet Autonomous Region Committee of the Communist Party of China
- Wuhu Discipline Inspection and Supervision Network
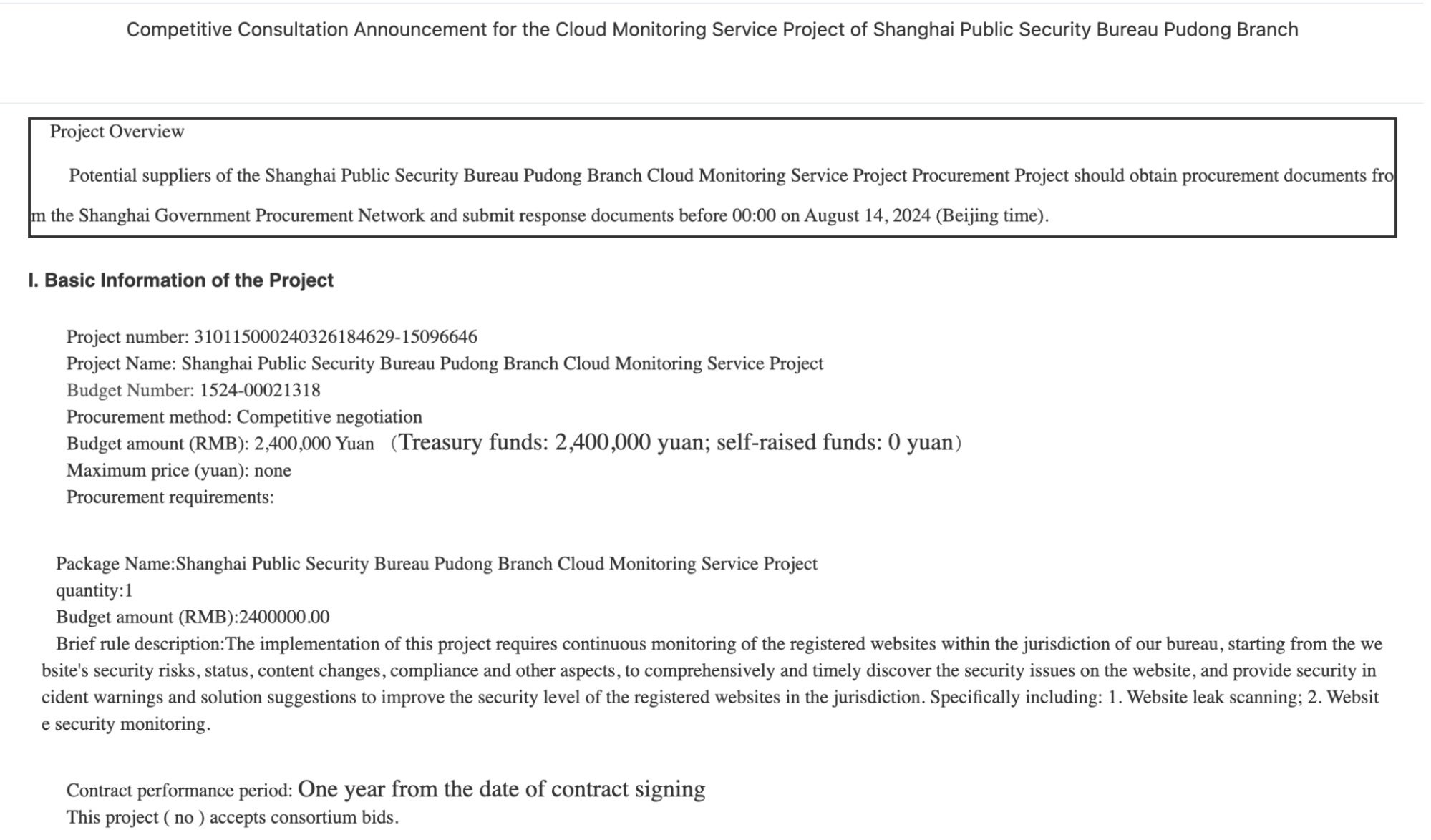
We observed references to three projects associated with Bureaus of the Ministry of Public Security in the northeastern city of Dandong, as well as the Songjiang and Pudong districts of Shanghai, with the latter project referred to as the “Cloud Monitoring Service Project”. The Ministry of Public Security is responsible for maintaining public order and overseeing law enforcement and surveillance activities to ensure compliance with national regulations.
[2024-2025 Shanghai Public Security Bureau Pudong Branch Cloud Monitoring Service Project (Phase II)] The statistics of events that occurred today are as follows: Aggregated events: 883 Valid: 129 Invalid: 672 On-hand: 82 Single events: 5637 Valid: 187 Invalid: 2781 On-hand: 2669 In terms of event volume, it is basically the same as that of our competitors.
A public procurement announcement for the “Cloud Monitoring Service Project” suggests that it involves monitoring the security posture and content of websites under the Bureaus’ jurisdiction, with alerts issued in case of security breaches or policy violations. TopSec was likely involved in the bidding process alongside competitor companies. Public documents, however, show TopSec did not win the contract.

Infrastructure Features
We identified this leak as a submission to a multi-scanner platform that fired off a rule that looks for common abuse activities associated with Kubernetes. The main file we analyzed (SHA-1: 1bccef07ad0348e326248fe321259e2bd8f8cf8b) contains numerous work logs, which are a description of the work performed by a TopSec employee and the amount of time the task took, often accompanied by scripts, commands, or data related to the task.
In addition to work logs, the leak contains many commands and playbooks used to administrate TopSec’s services via multiple common DevOps and infrastructure technologies that are used worldwide, including Ansible, Docker, ElasticSearch, Gitlab, Kafka, Kibana, Kubernetes, and Redis. There are many artifacts showing JSON data for web APIs used by TopSec services. There are also network configurations, SSH and port mapping commands with hardcoded credentials, which present a huge security risk should anyone obtain access to the environment–and would likely provide access to TopSec’s downstream customers as well.
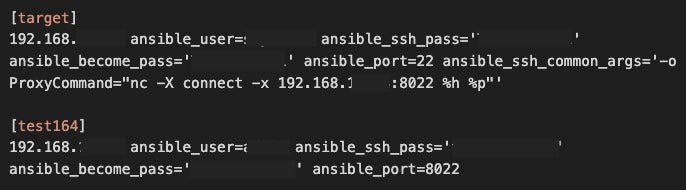
The leaked file is very large, disorganized, and the formatting is inconsistent, which complicates analysis. It is highly likely that we have not identified all capabilities outlined in the leak. Our analysis approach focused on translating the Chinese language content, identifying known technologies, and identifying interesting references in the commands and API JSON artifacts, particularly those where there were upticks in work logs performed around specific dates documented in the work logs or web API data.
The data leak includes a file that starts with infrastructure management code, including some which initializes several Docker images to enable security monitoring related features. These containers run probes, which are likely used for network monitoring. We are unable to fully assess the capabilities of these containers without access to them. However, the containers are run with several flags such as --privileged and --net host that suggest deep access to the monitored data. This may indicate the probes inspect network traffic or perform privileged tasks in the deployment environment.
Deeper in the file, there are work logs which contain dates indicating when certain tasks were performed and notes from the TopSec staff who worked on specific infrastructure projects. One project referenced repeatedly is called Sparta or Sparda, with the spelling changing regularly. Notes from the TopSec staff indicate that Sparta handles sensitive word processing, an indication of censorship keyword monitoring.
On a technical level, Sparta is a framework that uses GraphQL APIs to receive content from downstream web applications. Work logs indicate that TopSec migrated from a system called Apollo, which is plausibly a reference to Apollo-GraphQL, an open-source framework offered by a company based in San Francisco. The work logs also indicate that Sparta is equipped to process Chinese language characters. This suggests that TopSec likely developed Sparta as an in-house solution that is tailored to the localized needs of TopSec’s customers and does not rely on a US-based solution.
Additionally, we observed a note indicating that detection alerts considered severe are likely distributed to internal teams via WeChat for prioritized handling. WeChat is a widely-used messaging and social media platform in China, known for its broad range of features, including messaging, social networking, and payment services. Its integration into daily life makes it an essential tool for communication and business operations within the country.
Severe monitoring events are sent to corporate WeChat
Since WeChat operates under Chinese regulations, there are significant implications regarding data privacy and government access. Under Chinese laws, such as the Cybersecurity Law, companies like Tencent, which owns WeChat, are required to cooperate with government entities, allowing them to access data when requested.
Web Content Monitoring
Our analysis found that TopSec’s capabilities include web content monitoring, as indicated by references to a service called Website Monitoring Service and detection events with internal identifiers prefixed with Web, such as WebTamper, WebHiddenLink, WebAvailHttp, WebDns, WebTr, and WebSensitive.
This feature of the platform is likely part of what would have been proposed in response to the bid issued by the Shanghai Pudong Bureau for the “Cloud Monitoring Service Project”, offering the Bureau tools to monitor website security and content as part of their broader surveillance and compliance efforts.
Inspect website monitoring-related services [ . . . ] [2024-06-12T18:00:00 to 2024-06-12T22:00:00 Event volume: 553] 2024-06-12T18:00:00 to 2024-06-12T22:00:00 Event volume: 553 WebSensitive 56 WebTamper 149 WebHiddenLink 348
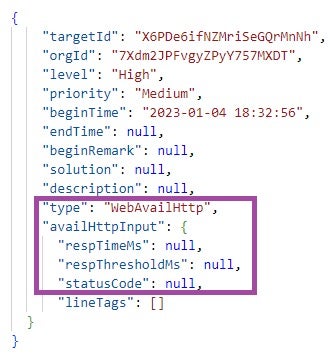
While the exact logic behind how the Web events are triggered remains unclear, the event names and metadata present in the documents provide insight into the purpose of some of these events. For instance, the WebAvailHttp event is likely triggered when a website is considered unavailable due to its response time (measured in milliseconds as respTimeMs in the figure below) exceeding a predefined threshold (respThresholdMs).
Further, the WebHiddenLink event is likely triggered when web content contains hidden links — links that obscure their destination or mislead users, posing a security risk. Examples include links concealed within small or transparent elements, deceptive anchor text, and styling tricks that make links appear as plain text.
Web Content Monitoring | Sensitive Words
The WebSensitive event is likely triggered when web content contains so-called sensitive words (敏感词 in Simplified Chinese). These words are related to political criticism, violence, or pornography, and are central to China’s domestic Internet censorship efforts aimed at ensuring compliance with government policies. Detecting the presence of such words in web content helps prevent the dissemination of information considered inappropriate or harmful by PRC authorities.
Assist the product to check for missed scans and manual analysis and marking errors of sensitive word events
TopSec’s ability to detect sensitive words demonstrates the impact that state policies related to the cyber domain have on the design and implementation of monitoring solutions developed by the private sector in China. These policies shape the strategies and technologies used to monitor, filter, and control online content, ensuring that IT systems comply with governmental regulations and censorship guidelines.
WebSensitive alerts may be used by private sector organizations to monitor user-generated content on their websites in order to trigger actions such as issuing warnings, deleting content, or restricting access when sensitive words are detected. Government entities may also consume these alerts to track the presence of sensitive words on their own websites or across broader online spaces to enforce compliance with national censorship regulations. For example, the latter may have been an objective of the previously mentioned “Cloud Monitoring Service Project” by the Shanghai Pudong Bureau of the Ministry of Public Security.
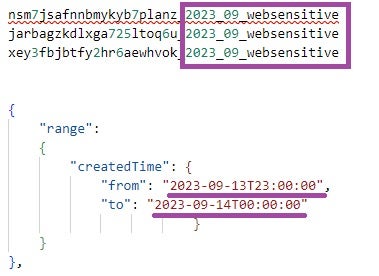
We observed a task list indicating a focused effort to ensure consistent monitoring for sensitive words between 7:00 AM and 8:00 AM on the 14th (converted from GMT to China Standard Time), with the month and year not specified. The preceding document content suggests that the reference is to September 2023. One item in the task list instructs verification of the availability and capacity of sensitive word detection capabilities during this period, while another item records the forwarding of ‘asset identifiers’ for collected ‘validated events’ to an individual named Zhao Nannan (赵楠楠). The task list issuing this instruction very likely includes a typo stating the validated events were from 7:00 AM to 10:00 PM on September 14.
1. Plan the probe deployment plan for the web split emergency milestone launch 3h 2. Check the number of agents for sensitive words between 23:00 on the 13th (GMT) and 14:00 at 00:00 (排查敏感词13日23点到14点0点之间的代办数量) 2h 3. Check cloud baseline 500 errors 1h 4. Collect asset identifiers of valid events on the 13th and provide them to Zhao Nannan 1h 5. Check the task execution failure of ipv6 probe 1h
The identification of an individual named Zhao Nannan as the likely recipient of this information, alongside the context of the monitoring effort, leads us to conclude with moderate confidence that this effort was in response to political events in Shanghai.
We identified a woman named Zhao Nannan as having worked at the 3rd Bureau of the Ministry of Public Security in Shanghai, which is responsible for network security and technical investigations. Our observations presented earlier in this post suggest close ties between Shanghai-based Bureaus of the Ministry of Public Security and TopSec, one example being TopSec’s participation in a project bidding process launched by the Shanghai Pudong Bureau.
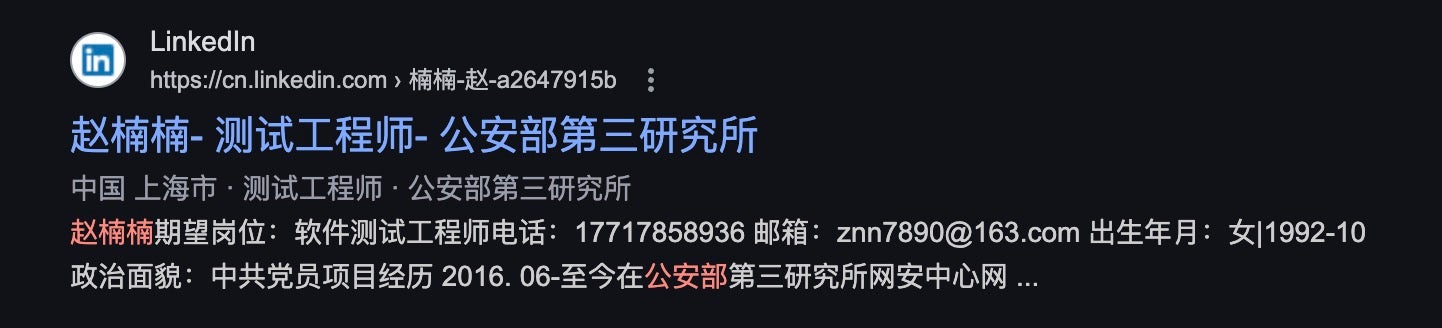
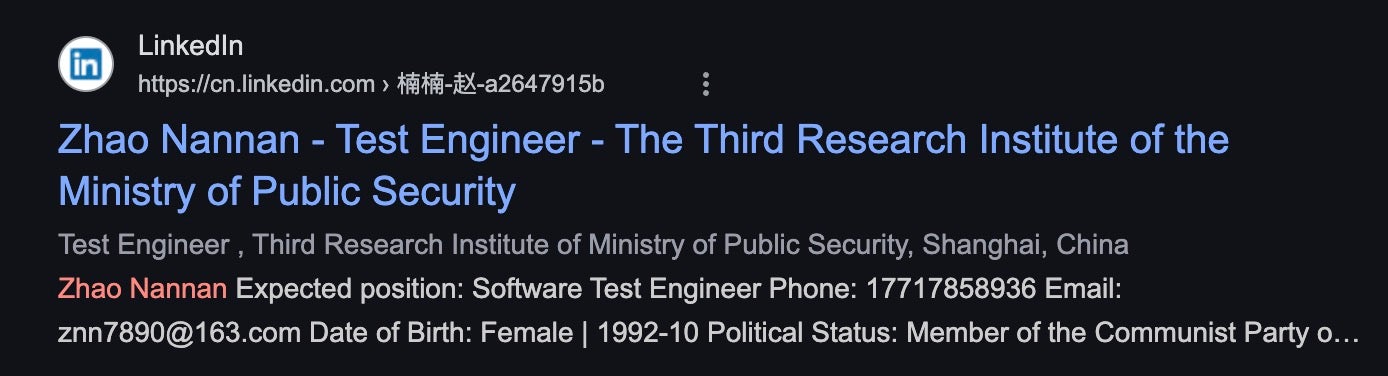
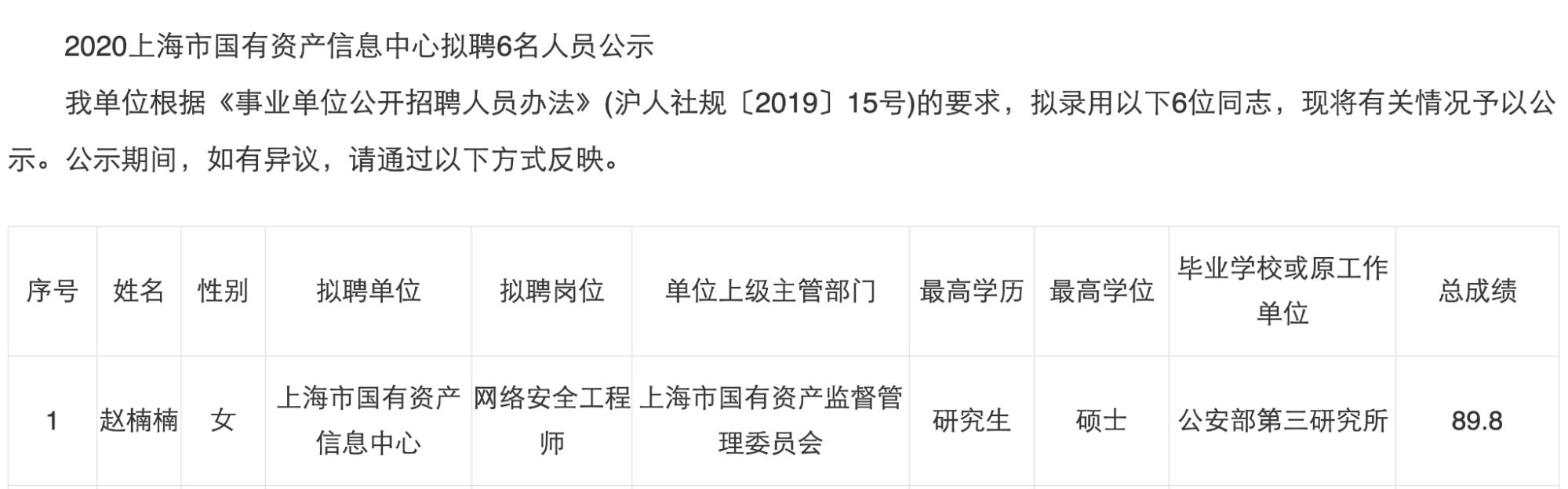
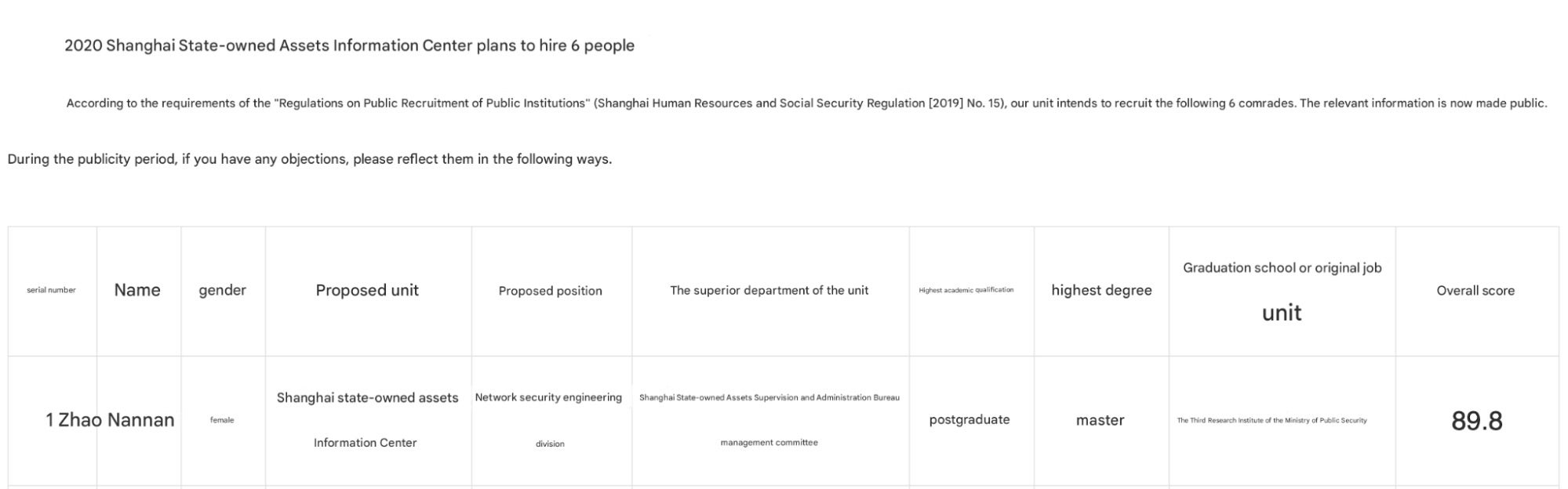
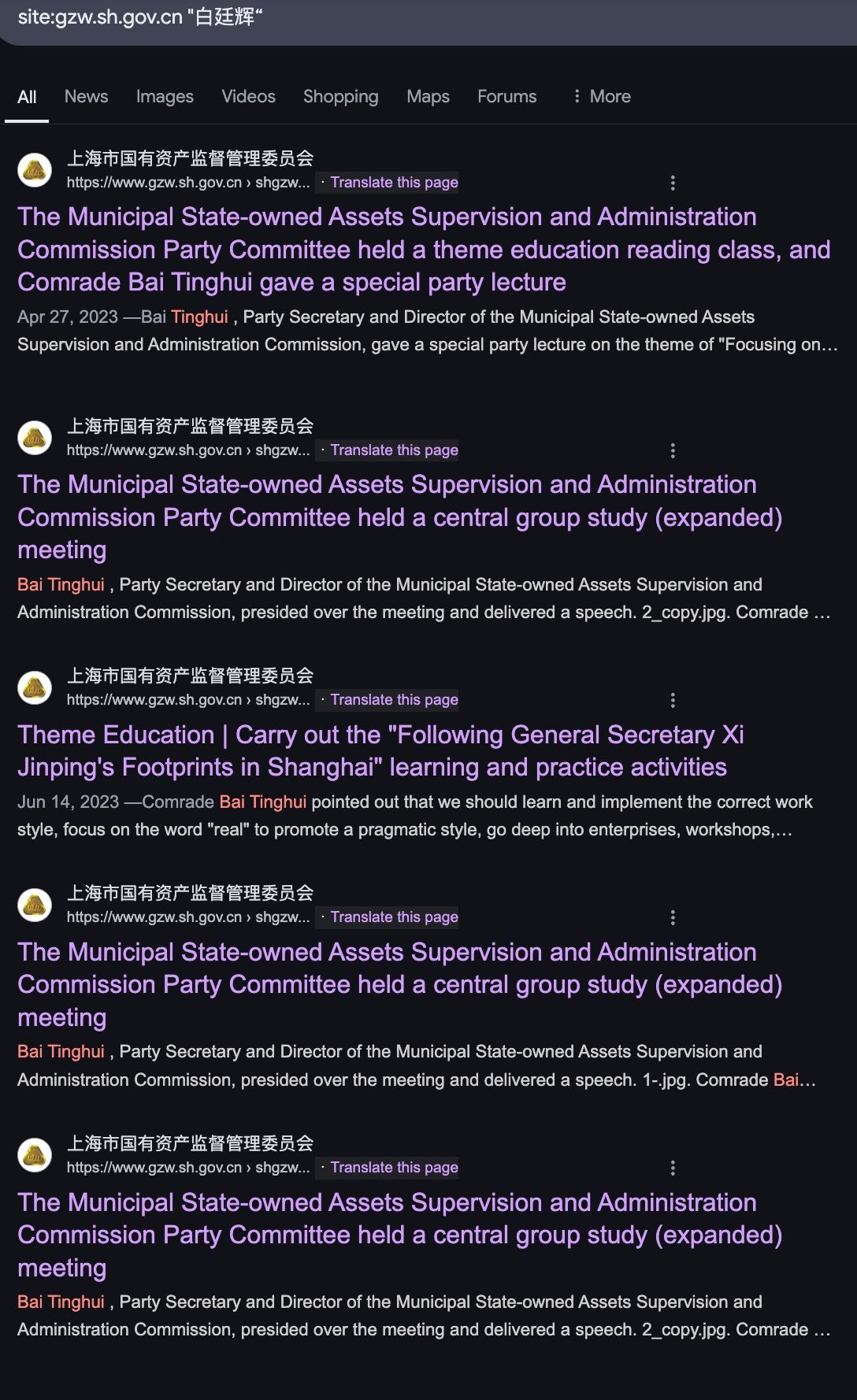
However, Zhao Nannan no longer works for the MPS 3rd Bureau in Shanghai. According to an online announcement from the Shanghai State-owned Assets Supervision and Administration Commission (SASAC), Zhao Nannan was one of six successful applicants to SASAC for a network security role. The announcement even references her past role at the MPS 3rd Bureau. Congratulations are due to her, as she scored the highest among the applicants for the role–恭喜!
On the morning of September 14th, when Zhao Nannan received alerts for sensitive content, her new employer announced on its WeChat account that the head of the Shanghai SASAC, Bai Tinghui, was under investigation for corruption. The news was quickly picked up by the South China Morning Post, Caixing, and other news-reposting blogs in China. The Shanghai government itself confirmed the investigation into Bai Tinghui and his subsequent dismissal one month later.
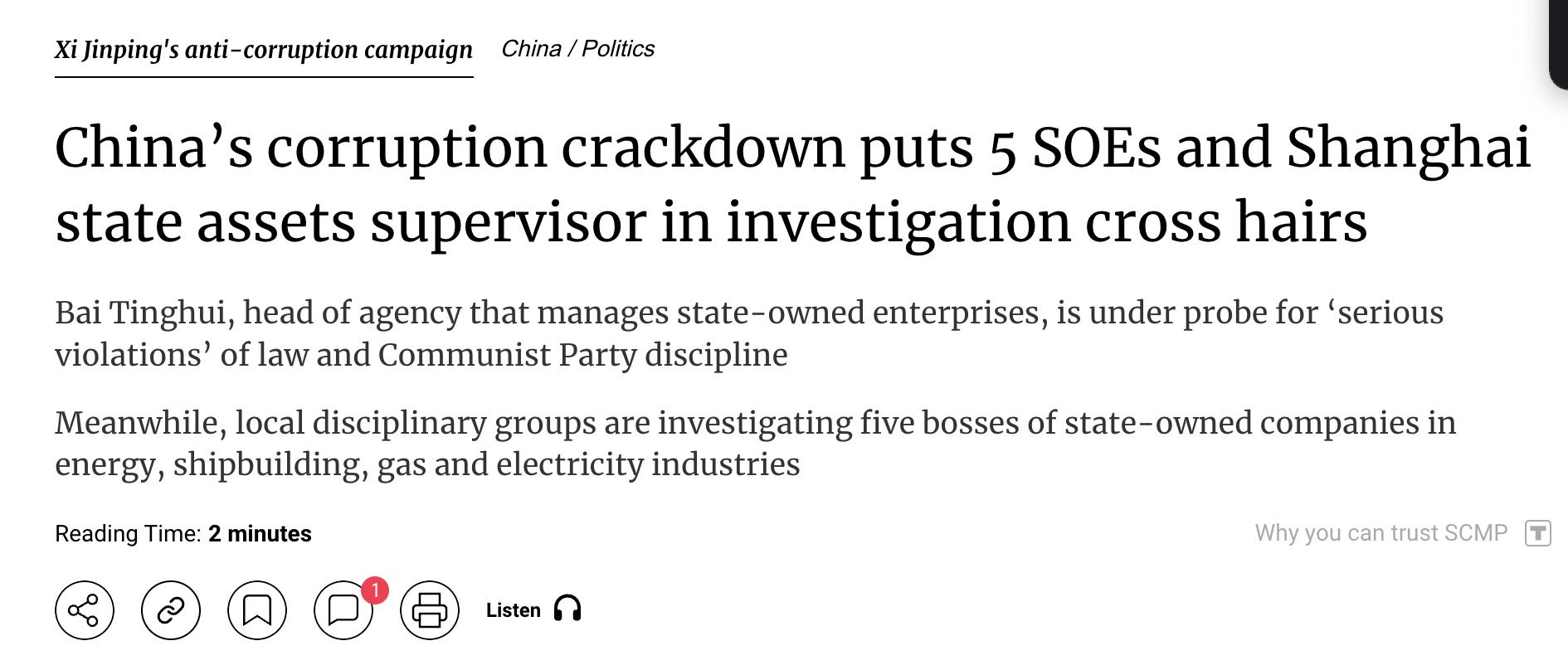

Because the Shanghai SASAC posted the news on WeChat, we know that the investigation itself was not subject to censorship. The lack of complete censorship regarding the investigation raises questions about what “validated events” would have been reported to Zhao Nannan following the announcement.
Currently, only five webpages of the Shanghai SASAC still mention Bai Tinghui. All five pages also mention Bai leading a Party study session of Xi Jinping Thought. It’s unclear why only these pages of Bai Tinghui remain–perhaps his tarnished reputation is outshown by Xi Jinping: it may be hard to delete a website with Xi Jinping’s name on it, even if it is accompanied by a corrupt local official.
Intriguingly, the organization that is responsible for investigating the fallen Bai Tinghui, the Shanghai Municipal Commission for Discipline Inspection, is listed among TopSec’s customers in the tooling.
The downfall of Bai Tinghui and the resulting use of Beijing TopSec’s tooling for coordinated monitoring of politically sensitive content shines a light on the important role cybersecurity companies can play in Chinese politics. The CCP has long-acknowledged that “If our party cannot traverse the hurdle represented by the Internet, it cannot traverse the hurdle of remaining in power for the long term.” This episode provides a compelling example of how corruption investigations expand to rely on the institutions of those being investigated and the cybersecurity companies that service them.
Conclusion
These leaks yield insight into the complex ecosystem of relationships between government entities and China’s private sector cybersecurity companies. While many countries have significant overlap between government requirements and private sector cybersecurity firms, the ties between these entities in China are much deeper and represent the state’s grasp on managing public opinion through online enforcement.
The September 2023 situation in Shanghai provides insight into how local and national government interests are enforced through private sector partnerships. The CCP’s strategy of controlling information is multifaceted and requires significant investment in resources that enable the monitoring and alteration of content that citizens engage with. While there are still many unknown factors regarding how such censorship is applied, these findings yield insights into how collaboration occurs between the government and other entities in China.
The nature of how this data was leaked remains unclear, but the materials show that TopSec engineers were documenting their work in a highly granular way that included entire commands used to perform the outlined tasks. Considering the types of information in this leak, organizations should evaluate how their systems and infrastructure engineers are logging work. Proper credential management is essential to securing sensitive environments. Infrastructure engineers should rely on a secrets manager that integrates with the CI/CD pipeline rather than running commands from playbooks that include hardcoded credentials. This results in only variable names being stored in commands instead of sensitive credentials and lowers the likelihood that an unexpected disclosure could result in further compromise.




