As the adoption of online banking within Brazil continues to grow, a corresponding rise in banking malware targeting this developing market is also being observed. The prolific Brazilian cybercrime group behind the banking malware “Banload” have implemented an interesting new driver component, internally called ‘FileDelete’, to remove software drivers and executables belonging to anti-malware and banking protection programs. The goal behind this driver is to enable fraud through credential theft and account-takeover operations on a victim’s machine. In this technical analysis, I dissect the novel FileDelete driver to reveal how it works.
Digital Signature Helps Defeat Legacy AV
The FileDelete driver is installed via the group Golang loader, leveraging PowerShell, to the local directory “C:G DATA Security Software.”
The driver is digitally signed with a certificate with the name “M2 AGRO DESENVOLVIMENTO DE SISTEMAS LTDA”. A digital certificate allows the malware to have a lower static detection among security solutions that implicitly trust code with a valid signature.
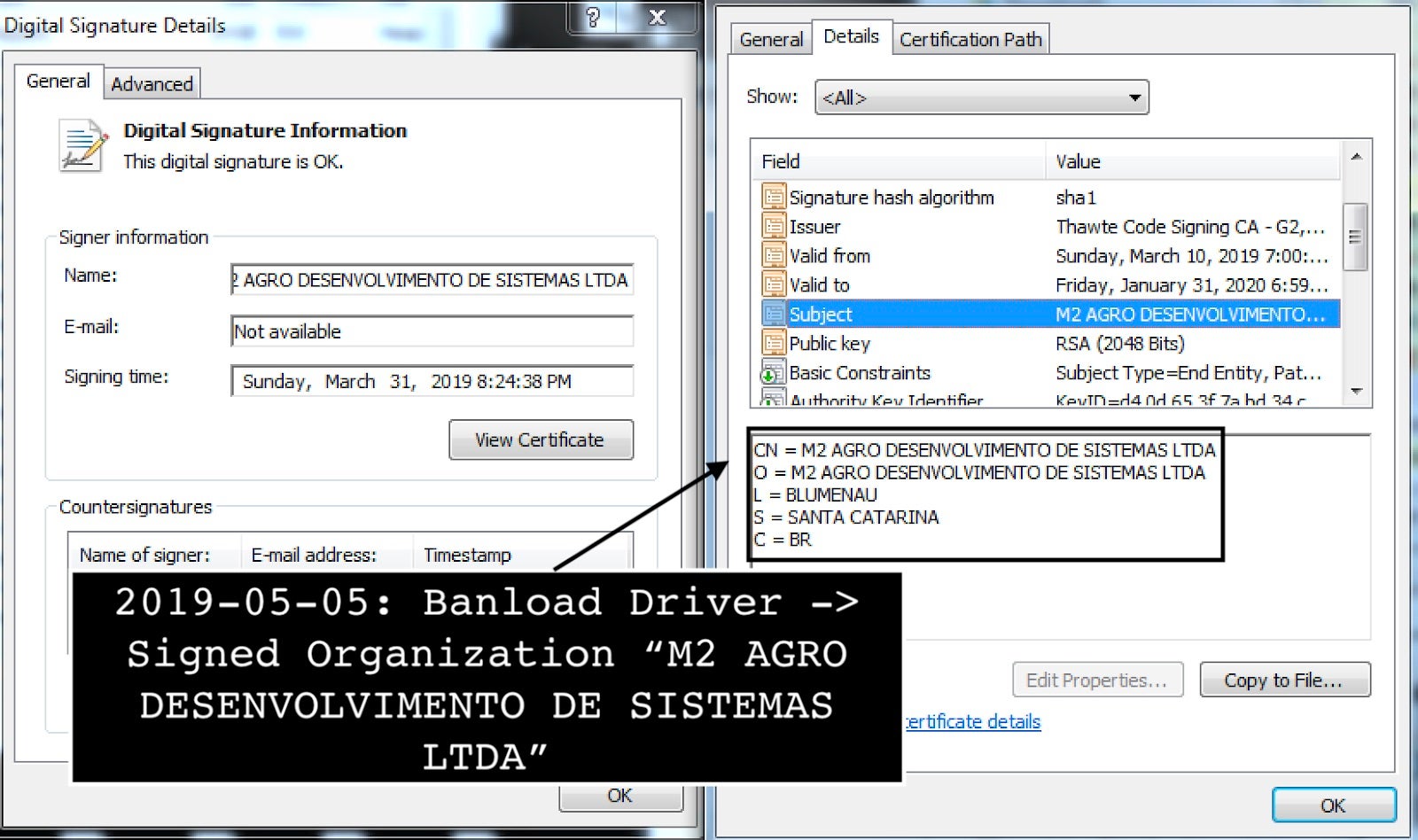
As the image above shows, the malware driver was signed on 31 March, 2019 with a Thawte Code Signing Certificate. These certificates are intended to assure users running the signed code that it is safe and trustworthy.
Kernel-mode Driver Targets AV Solutions
It is rare to observe kernel-mode driver implementations on the financially-motivated malware landscape. The FileDelete function removes the software products belonging to AVG, Trusteer Rapport, Avast, and Bradesco software “scpbrad.”
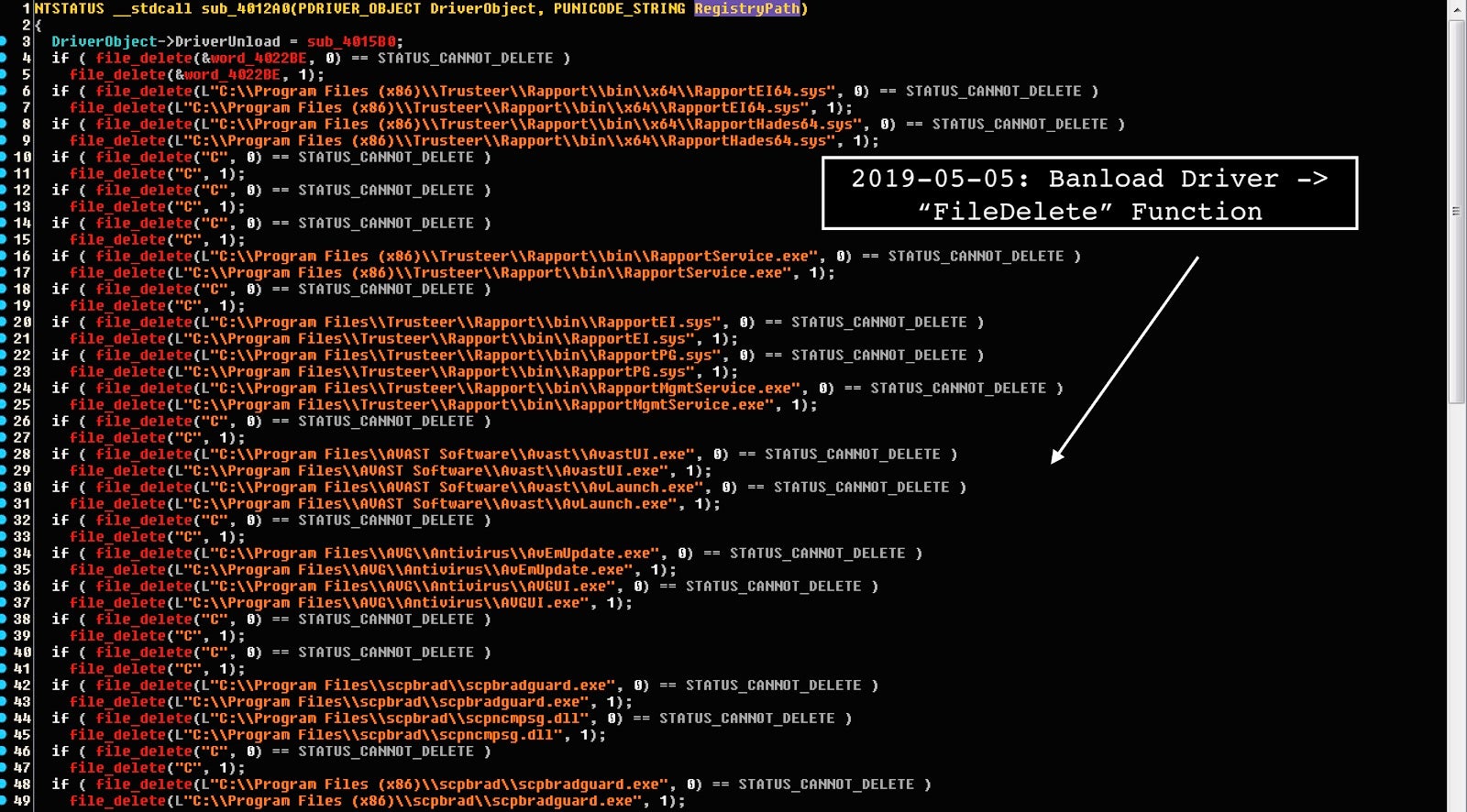
It does this via the internal driver called “FileDelete.sys” (as it was originally discovered by @MalwareHunterTeam), which leverages I/O request packet (IRP) structures.
The driver forces deletion of the files with an irpStack walk via
IRP_MJ_SET_INFORMATION... -> FileDispositionInformation-> DeleteFile
The driver malware consists of 6 sections with 25 imports from ntoskrnl and 1 from HAL.dll. The driver malware is rather simple and consists of debugging elements with the program database (PDB) path as “F:SistemaDrivers-DenisFileDeleteFileDeletex64DebugB.sys.”
The malware sections are as follows with the “INIT” one used as “AddressOfEntryPoint” for Import Directory RVA. The rest are the usual sections with .pdata leveraged as Exception Directory RVA.
Essentially, the driver attempts to delete the list of the hardcoded software protections paths. The malware sets up the driver path as “DosDevicesA:” and attempts to obtain a file handle via the sequence of IoCreateFile and ObReferenceObjectByHandle API calls.
Next, the malware utilizes IRP to create a file via the sequence of
KeInitializeEvent -> IoAllocateIrp -> IoFileObjectType -> KeGetCurrThread -> ExAllocatePoolWithTag -> IoGetFileObjectGenericMapping -> SeCreateAccessState -> IoGetNextIrpStackLocation -> Driver Call Function
The malware then forces deletion of the file passing the object handle from the previous call. Then to IoGetBaseFileSystemDeviceObject and IoGetNextIrpStackLocation, adjusting both IrpSetFileAttributes and IrpFileDelete function.
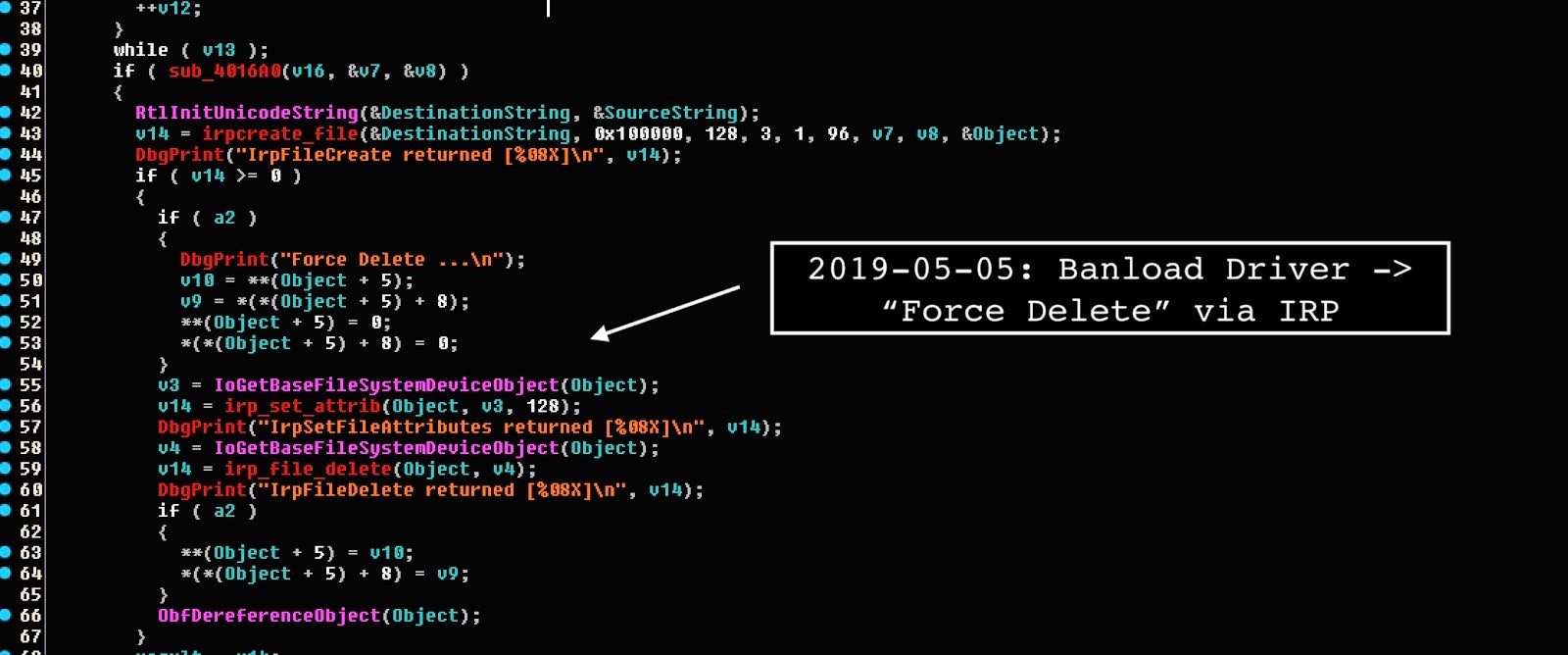
The developer left quite a few notable DbgPrint elements meant to debug the flow of the driver such as “Normal Call MJ[%d] %pn”, “Force Delete …n.”
Conclusion
While the signed driver itself does not appear to be sophisticated, its custom implementation demonstrates that the group behind Banload continues to innovate and adopt newer tools meant for fraud operations while installed on the victim machines.
Indicators of Compromise (IOCs)
Golang Loader (MD5):
bd73f690fb9479ccfacad8cc3d36f002
64-bit Driver (MD5):
ef4048de1c678045520815c932e73f56 PDB: F:SistemaDrivers-DenisFileDeleteFileDeletex64DebugB.pdb
32-bit Driver (MD5):
f54c335c5024cfa43c4673f3c99209b2 PDB: F:SistemaDrivers-DenisFileDeleteFileDeleteDebugB.pdb
Targeted Software
#Sample 1
C:Program Files (x86)TrusteerRapportbinx64RapportAegle64.sys C:Program Files (x86)TrusteerRapportbinx64RapportEI64.sys C:Program Files (x86)TrusteerRapportbinx64RapportHades64.sys C:Program Files (x86)TrusteerRapportbinx64RapportKE64.sys C:Program Files (x86)TrusteerRapportbinx64RapportPG64.sys C:Program Files (x86)TrusteerRapportbinRapportMgmtService.exe C:Program Files (x86)TrusteerRapportbinRapportService.exe C:Program FilesTrusteerRapportbinRapportAegle.sys C:Program FilesTrusteerRapportbinRapportEI.sys C:Program FilesTrusteerRapportbinRapportPG.sys C:Program FilesTrusteerRapportbinRapportMgmtService.exe C:Program FilesTrusteerRapportbinRapportService.exe C:Program FilesAVAST SoftwareAvastAvastUI.exe C:Program FilesAVAST SoftwareAvastAvLaunch.exe C:Program FilesAVAST SoftwareAvastAvEmUpdate.exe C:Program FilesAVGAntivirusAvEmUpdate.exe C:Program FilesAVGAntivirusAVGUI.exe C:Program FilesAVGAntivirusAvLaunch.exe
#Sample 2
C:Program Files (x86)TrusteerRapportbinx64RapportAegle64.sys C:Program Files (x86)TrusteerRapportbinx64RapportEI64.sys C:Program Files (x86)TrusteerRapportbinx64RapportHades64.sys C:Program Files (x86)TrusteerRapportbinx64RapportKE64.sys C:Program Files (x86)TrusteerRapportbinx64RapportPG64.sys C:Program Files (x86)TrusteerRapportbinRapportMgmtService.exe C:Program Files (x86)TrusteerRapportbinRapportService.exe C:Program FilesTrusteerRapportbinRapportAegle.sys C:Program FilesTrusteerRapportbinRapportEI.sys C:Program FilesTrusteerRapportbinRapportPG.sys C:Program FilesTrusteerRapportbinRapportMgmtService.exe C:Program FilesTrusteerRapportbinRapportService.exe C:Program FilesAVAST SoftwareAvastAvastUI.exe C:Program FilesAVAST SoftwareAvastAvLaunch.exe C:Program FilesAVAST SoftwareAvastAvEmUpdate.exe C:Program FilesAVGAntivirusAvEmUpdate.exe C:Program FilesAVGAntivirusAVGUI.exe C:Program FilesAVGAntivirusAvLaunch.exe C:Program Filesscpbradscpbradserv.exe C:Program Filesscpbradscpbradguard.exe C:Program Filesscpbradscpncmpsg.dll C:Program Files (x86)scpbradscpbradserv.exe C:Program Files (x86)scpbradscpbradguard.exe C:Program Files (x86)scpbradscpncmpsg.dll
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- RobinHood Ransomware “CoolMaker” Functions Not So Cool
- Ursnif – A Polymorphic Delivery Mechanism Explained
- Asus ShadowHammer Episode – A Custom Made Supply Chain Attack
- 7 Reasons To Move Away From Legacy AV
- How Malware Can Easily Defeat Apple’s macOS Security
- What Is Windows PowerShell (And Could It Be Malicious)?




