There’s a seductive allure to the story that hacking can be a force for good, a way to tip the scales in favor of an underdog equipped with little more than a terminal, elite skills, and good intentions. In previous decades, what passed for hacktivism was little more than pointed website defacements and distributed denial of service attacks. Basically, politically motivated nuisances. They made their presence known, but their long-term impact was negligible. A post-Wikileaks era emphasized the power of hack-and-leak operations as a suitable lever for real-world impact of the sort hacktivists had sought for a long time. And it inevitably became the de facto standard for the greyhat vigilante.
The idea of hacktivists out there looking to settle the score against oppressive regimes is alluring in the same way that a grassroots revolution, a cohesive outcry of an oppressed people against their oppressors, is alluring. But the two aren’t equivalent.
A politically motivated hacking operation is not representative of a societal quorum. Technological skills and means are an amplifier that can give a handful of individuals an outsized voice and while that may be used to advance a moral cause, it’s also a great cover for action for established state-sponsored actors to influence sentiment and outcomes all over the world.
All of which begs the questions, are there still real hacktivists out there or are they all a cover for state-sponsored operations? Have we learned enough from previous run-ins to improve our analysis processes when approaching these potential deception operations?
Focus on this topic was motivated by our discovery of MeteorExpress and the rise of the Belarusian Cyber Partisans as a force opposing the Lukashenko regime. Both are widely different cases of hacktivism, with the former exhibiting inauthentic traits while the latter makes for a more convincing example of a grassroots endeavor.
The results of our analysis were first codified in the form of a CyberWarcon 2021 talk. In light of recent events, like the Partisans’ alleged use of ransomware to hinder Russian troop movements and a recent FBI report revisiting aspects of the Yemen Cyber Army, we felt it appropriate to spell out some insights and open mysteries.
State-Sponsored Knockoffs
In our 2016 paper, Brian Bartholomeow and I documented multiple instances of state-sponsored groups abusing hacktivist covers for their operations, focusing on two particular actors, Lazarus and Sofacy (APT28, STRONTIUM, FancyBear, etc.). Let’s briefly recap both.
The former resorted to this tactic early and often but did so poorly. Around 2015, it was easier to consider Lazarus a single grand threat cluster unified by a nexus of North Korean interest. Their operations against South Korean targets in 2012-2014 employed the cover of ‘hacktivist’ groups like ‘IsOne’, the ‘New Romantic Cyber Army’, and ‘WhoIs Team’.
Their more infamous cover, ‘Guardians of Peace’, became well-known for its involvement in the Sony Entertainment Pictures hack. Ultimately, all these hacktivist groups proved a thin and unconvincing disguise. They lacked any established pedigree and would lack any further operational continuity. They were abandoned just as quickly as the operations were carried out.
On the other hand, Sofacy would prove far more dogged and successful in their use of hacktivism groups as cover. In some cases, they succeeded in fooling media outlets, victims, and researchers into thinking that they were dealing with hacktivist jihadis (CyberCaliphate) or pro-Russian Ukrainian security services (CyberBerkut).
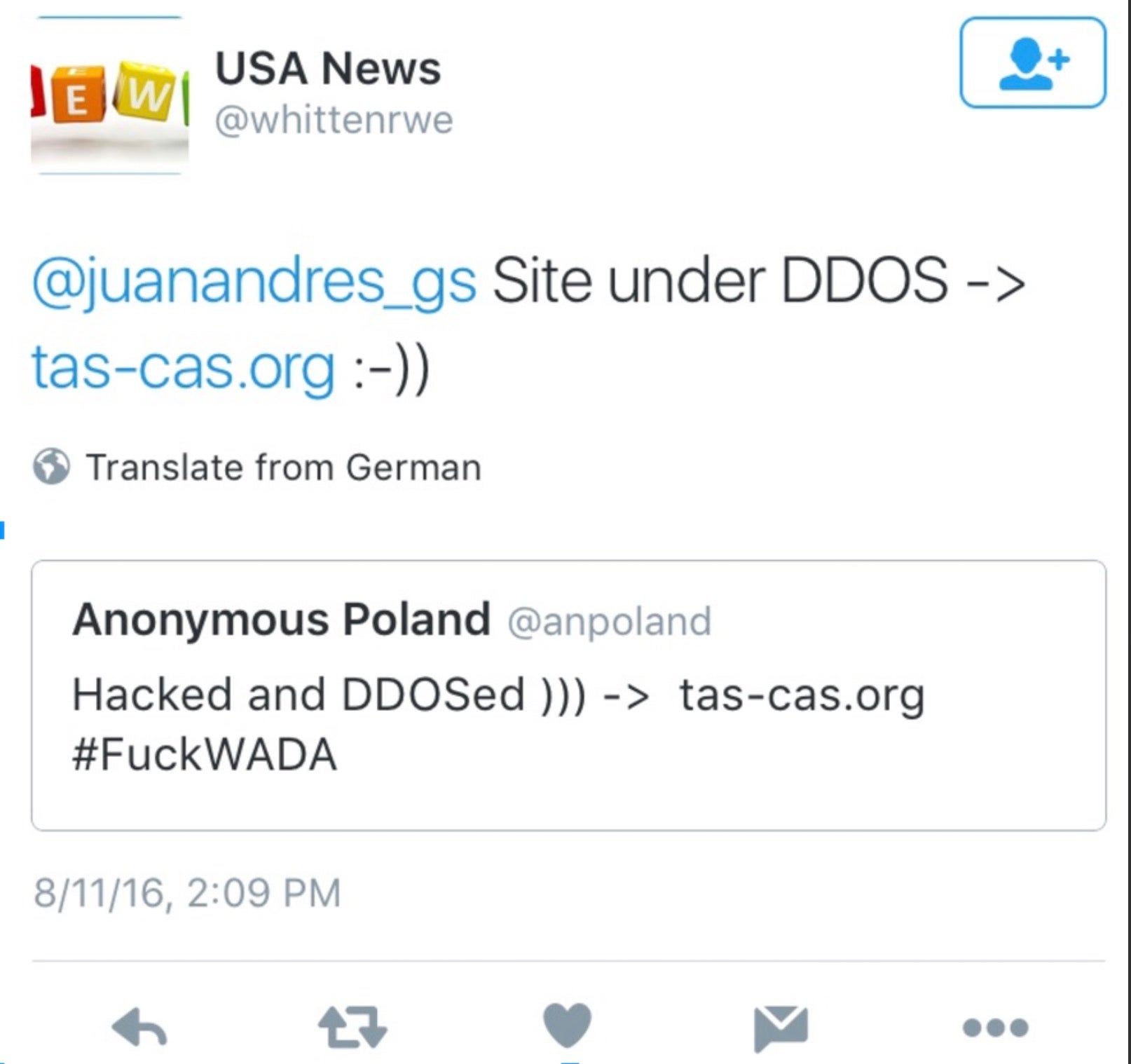
While these outfits lacked much pedigree, they were nurtured over time and focused on objectives across different regions. Their efforts became sloppier during the summer of election hacks in 2016, employing outfits like the now infamous Guccifer 2.0, the lesser known @AnPoland, and even ultimately embracing one of their threat intelligence cryptonyms outright as the ‘FancyBears Hack Team’.
Beyond soft indicators like pedigree and continuity, threat intelligence researchers avidly tracking state-sponsored operations were in a position to correlate the leak phase of these operations with their respective earlier intrusion phases. For example, the attackers put effort into creating a hacktivist cover like @AnPoland to release documents stolen from the World Anti-Doping Agency (WADA) or the Court of Arbitration for Sport (Tas-Cas). Around the same time, Sofacy was seen registering WADA and Tas-Cas typosquatted domains for use in their phishing campaigns.
A possible coincidence? Sure. But we can add ‘overlap with a state-sponsored operation’ as another soft indicator in our assessment matrix for hacktivist covers.
These examples are practically ancient history in InfoSec years. We’re revisiting them precisely because the benefit of hindsight does a lot to dispel the confusion that accompanies fresh enemy incursions. For example, while we suspected that Yemen Cyber Army (YCA) was another Sofacy front due to a combination of soft indicators, Simin Kargar’s 2021 Cyberwarcon talk weighed the possibility of Iranian vs. Russian state-sponsorship behind YCA.
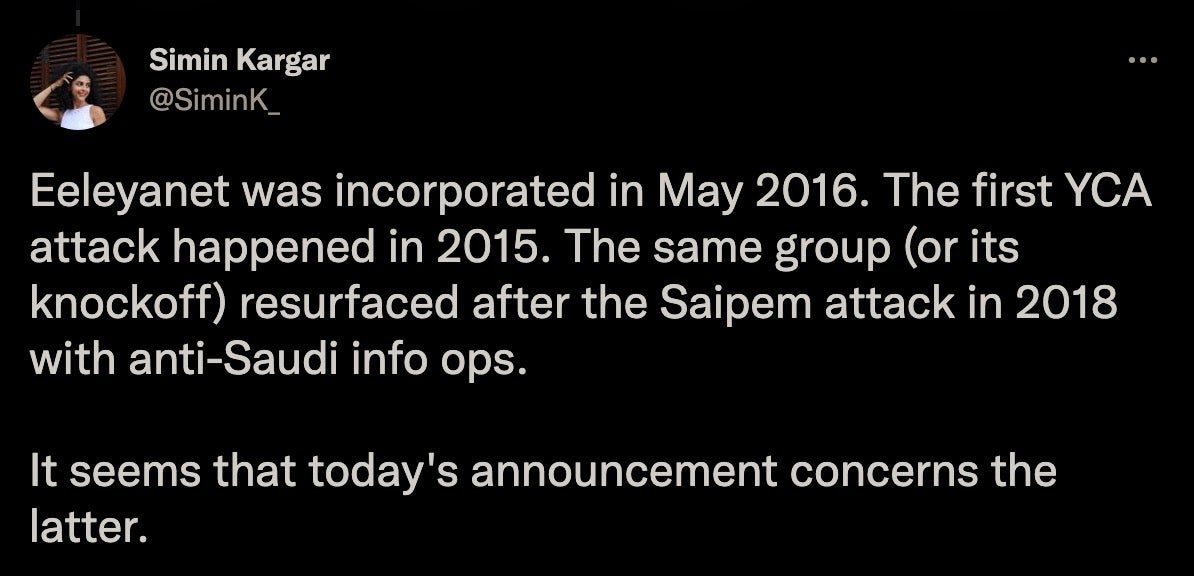
With the timely release of the FBI’s report on Iranian-based company Emennet Pasargad (a.k.a. Eeleyanet Gostar), the benefit of hindsight may ultimately tip the scale in favor of Kargar’s Iranian hypothesis. The FBI connects Emennet Pasargad with both 2018 YCA activity as well as a 2020 U.S. voter intimidation and disinformation campaign under the cover of Proud Boys.
That said, keep in mind that the Yemen Cyber Army activity referenced occurs in 2018 and is not expressly linked back to the 2015 activity (as noted by Kargar). As she hints in her tweet, there’s always the possibility of yet another turn, a ‘knockoff’ hijacking the pedigree of this hacktivism cover for themselves.

More recently, we investigated the case of MeteorExpress, a previously unknown actor conducting wiper attacks across Syria and Iran since 2019. This brought back the question of inauthentic hacktivism as MeteorExpress activities were claimed by different short-lived, no pedigree ‘hacktivist’ groups under names like ‘Indra’, ‘Predatory Sparrow’, and possibly ‘Adalat Ali’.
Each appeared to have their own delimited campaigns, Telegram channels, social media accounts, and dropped stolen files via MEGA. The handling of the diverse fronts was inconsistent. Indra and Predatory Sparrow attacks were correlated by the use of slightly altered versions of MeteorExpress malware. Notably, there are even two separate Predatory Sparrow accounts, pointing to a possible hijack or something as embarrassing as a loss of credentials for the first.
We can at least say that inauthentic hacktivism is alive and well as a cover for action for state-sponsored attacks looking for a modicum of plausible deniability.
What Might Real Hacktivism Look Like?
Having discussed so many examples of fake hacktivism, we can distill the more useful soft indicators we’ve previously used in evaluating authentic hacktivism in a modern context.
- Pedigree
- Where did they come from? What have they done before?
- Continuity
- What happens after the initial attack?
- Sourcing of Materials
- How did they arrive at the materials pilfered or leaked?
- Release Coordination
- How are their released materials disseminated and amplified?
- Cui bono
- Who benefits? Who is negatively affected? Who should be negatively affected but isn’t?
- Consistency of Objectives
- Are the attackers consistently working towards their stated cause?
- Secondary Effects
- What effects are being courted? Media attention? Government response? Regional tensions?
- Targeting
- How are their targets selected? What prior knowledge would someone require to select or reach these targets?
- Consistency
- How well defined is the group? What ties one claim of ownership over a campaign to another? Is it a nebulous collective that different actors could hijack?
In the absence of hard technical indicators, these are some of the questions analysts should consider as they evaluate the authenticity of a hacktivism group. At this point, I’ll admit a tendency towards default skepticism, but we’d do well not to discount the possibility of a true homegrown asymmetrical threat.
Play Along at Home
For those analysts eager to try their hand at some of this analysis, there are multiple unsolved mysteries to choose from.
- Lab Dookhtegan and GreenLeakers, two notorious groups sporadically leaking tools and materials allegedly belonging to Iranian APTs OilRig and MuddyWater, respectively.

LabDookhtegan and GreenLeakers
- SpiderZ, a mysterious group responsible for hacking the Al-Qard Al-Hassan financial organization and disclosing mechanisms used by Hezbollah to bypass U.S. sanctions in Lebanon.

SpiderZ logo from their Anonymous-themed YouTube video
- AgainstTheWest, a persona brought to my attention by Aaron DeVera during the CyberWarcon Q&A. ATW stages sporadic attacks against the Chinese government. DeVera recently published a profile of ATW.
- IntrusionTruth, is a notorious outfit in the threat intelligence space. They intermittently release blogs profiling the individuals and companies behind different Chinese APTs with a decent level of detail substantiated via public sourcing or different telemetry services.

IntrusionTruth logo consistent across their blog and Twitter account
- ‘John Doe’ is purportedly the sole source behind the Panama Papers, claiming responsibility for the hack against Panamanian company Mossack Fonseca that set off the global tidal wave of revelations on the illicit use of offshore companies to hide wealth. Despite an initial mistaken arrest of a local employee, little is known about this attacker beyond their statement of intent. Further releases by the International Consortium of Investigative Journalists (ICIJ), titled ‘Pandora Papers’, have been more opaque about their sourcing, so what happened to John Doe?
- Last, but most certainly not least, is the mythical ‘Phineas Fisher’.

Sock puppet used to represent Phineas Fisher at their request during a Vice CyberWar interview While it’s hard to assess the authenticity or provenance of PF, they’re arguably the most successful modern hacktivist outfit with a confirmed kill under their belt –HackingTeam. PF gets their name from their first publicly attributed hack against Gamma Group (the makers of FinFisher) in 2014. They would then go on to breach HackingTeam so epically that they essentially left the company to slow bleed and ultimately shut down.

ASCII art from one of Phineas Fisher’s HackBack Guides While PF is better known for these big hacks, they would also go on to release multiple hacking guides rife with Anarcho-Marxist references. The stated purpose being to empower others to follow in their footsteps and stand up to capitalist abuses. That mission would be further bolstered by hacks against the Mossos D’Esquadra police union of the Catalan Police, the AKP party in Turkey, and the Cayman Island National Bank and Trust. Consequently, PF set up the ‘Hacktivist Bug Hunting Program’, offering up to $100,000 in cryptocurrency as a reward for hacks against companies contributing to our ‘hypercapitalist dystopia’.
An Authentic Example?
Keen readers might note that I haven’t pointed to any groups as authentic modern hacktivist outfits. Rather than embrace skepticism entirely, I’ll go out on a limb and point to the recent rise of the Belarusian Cyber Partisans as a group with all the hallmarks of authentic hacktivist behavior, fully allowing for the possibility that I’ll end up eating my words. Let’s apply the metrics we’ve previously discussed.

The Belarusian Cyber Partisans claim to be a collective of local system administrators fighting against the Lukashenko regime. Most of their attacks have focused on disclosures of stolen government information in the hopes of attracting further scrutiny on the practices of the incumbent leadership. By their own admission in private communications, the Partisans felt that the media were not paying enough attention to these revelations. They’ve now graduated to a new strategy of leveraging ransomware to disable strategically significant institutions, starting with the Belarusian Railways company (BCh) in an attempt to hinder Russian troop movements within Belarus and demanding the release of political prisoners.
Applying our soft indicators, we see the Partisans activity establishing a clear pedigree of activity and continuity of operations that’s continually emboldened but not suddenly enhanced by outsized capabilities. As reports are leaked detailing some of the means of their attacks, we see rather mundane technical indicators, largely abusing free services and commonly available tooling, though by their admission the alleged ransomware used at BCh is one they wrote (something we haven’t independently confirmed due to a lack of samples).

Most importantly, their limitations and tasking appear organic. They claim that in order to discover important government targets, they collaborate with a union of current and former Belarusian security officers (BYPOL) better acquainted with the inner workings of the government. That organic tasking stands in stark contrast to the example of MeteorExpress’ Indra campaign where a no pedigree ‘hacktivism’ group knew the exact companies allegedly supporting Iranian Revolutionary Guard Corps (IRGC) operations in Syria to hack-and-leak. This pinpoint targeting goes unexplained in the MeteorExpress narrative, and in most state-sponsored fly-by-night covers.
Signaling and Secondary Effects
There are reasons that we should foment greater analytic rigor when it comes to the authenticity of hacktivist operations. The use of a hacktivist cover goes hand-in-hand with the intention to release materials publicly and amplify a narrative for a given audience.
That’s a non-trivial change when it comes to state-sponsored operations, most of which are designed to remain undiscovered for as long as possible. Hack-and-leak operations are meant to court (selective or wide) attention and cause an effect. In the process, these groups are leveraging two audiences– security researchers and journalists.

I’m afraid to say that we both prove susceptible conduits for different but similar reasons. We as security researchers are fascinated by new attacks, by the thrill of a new puzzle to put together. Our jobs often entail sharing information with other companies, reporting to governments, or publishing to as wide an audience as we have at our disposal. Similarly, journalists are always on the lookout for the next big story, they have editors and metrics. And neither group benefits from a wealth of time to scrutinize all aspects of a possible deception operation before amplifying it.
It’s easy to dismantle the ethical implications of our respective roles in these ops, but I think it’s important to sit with the discomfort and weigh (perhaps fruitlessly) how we might serve as more conscious stewards of the information we come across. We are not an incidental part of the dissemination aspect of these operations but a vital aspect, and we’d do well to act as a discerning one.
Concluding Thoughts
Hacktivism has come a long way from the late 90s and early 2000s years of nuisance hacks and naive collectives. If we distill what we’ve learned over the past decade of hacktivism abused as a cover for action, clear insights come into view:
- State-sponsored groups use the guise of grassroots motivations not just for plausible deniability but also to imbue their leaks with legitimacy not afforded by the obvious intervention of a government.
- Given the comparative volume of hacktivism ops that have turned out to be state-sponsored deception ops in the past ten years, we may also lean towards the conclusion that most hacktivism is used as a cover.
- We actually struggle to narrow in on the examples of authentic hacktivism in the past decade, though it surely exists.
- Our ability to assess these operations with certainty remains weak and is untimely compared to the speed with which their information is disseminated and amplified.
As a partial salve, we should hold steadfast to the attributes and soft indicators that have served us in determining the (in)authenticity of previous groups and apply them to these operations as they arise.
And for those avid practitioners and hungry analysts out there, it’s clear that the hacktivism space contains a wealth of unsolved mysteries to tackle.




