A few years ago public RaaS (Ransomware as a Service) offerings were plentiful. SATAN, Nemesis, Petya, RaaSberry, Shark, Data Keeper…the list goes on. However, the trend, especially in the last year, has been for these services to become increasingly exclusive. NEMTY Revenue & Zeppelin are two prime examples of this.
Still, every now and then we stumble across a fully public service. It gets even more interesting when that service offers a “seamless” experience across OS platforms. Ransomware families with full feature parity across Windows, Linux and macOS do not pop up all that often, which brings us to today’s topic: the SMAUG RaaS (Ransomware as a Service) offering.
SMAUG’s Differentiators
The SMAUG RaaS emerged towards the end of April 2020, and seems to have gained some traction in the following months. SMAUG appears to be a robust and full-service RaaS, with a few tweaks that set it apart from the others.
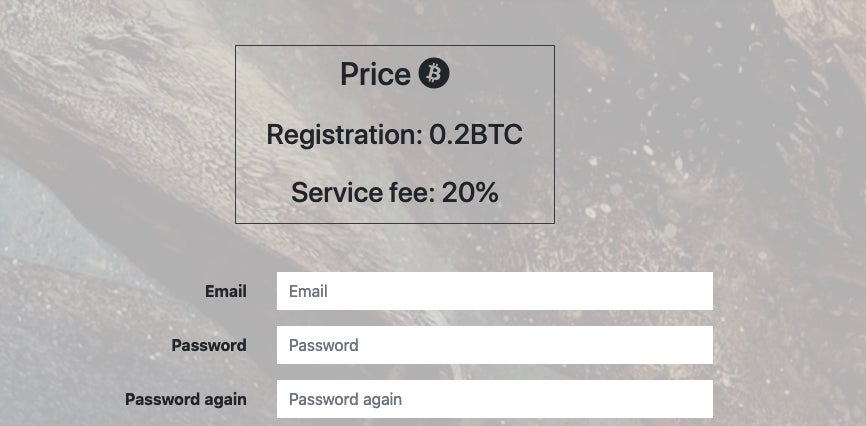
Criminals who wish to become SMAUG “distributors” will likely be used to the offerings associated with this type of service. The SMAUG operators currently charge a 20% service fee. However, there is also a registration fee which is quite steep when compared to other “fully-public” services. The current registration fee is .2 BTC, around $1800 USD at today’s prices.
There are some possible exceptions to getting around the registration fee. On some forums where SMAUG is advertising, the developers state that free memberships (owing only the service fees) will be given to the first five customers with a certain number of posts, and the ability to prove their past work (attacks).

Perhaps the most interesting differentiators are multi-platform support (all 64-bit) and the inclusion of a “Company Mode”, which allows for a single key to apply to an entire body of infected ‘hosts’ (aka a targeted company). If the victim chooses to comply with the attackers, then a single key can be used to decrypt (theoretically) all the encrypted hosts in that environment.
SMAUG also has offline capabilities, meaning that the payload does not have to have any amount of connectivity in order to execute and encrypt.
SMAUG is designed to evade traditional AV products. Along with crypting/obfuscation, the payloads have been developed to have as minimal a footprint as possible.
It should be noted that SMAUG does not appear to include a native crypting/packing feature. Consequently, the developers advise attackers to further obfuscate their payloads. They note the following within the Campaign configuration options of the SMAUG management interface: “Even though the payload is stealthy it is recommended to use crypting service to ensure the payload is undetectable by antivirus solutions.”
The operators advertise a fully automated payment system, as well as highly customizable campaigns. This allows attackers to streamline and organize multiple campaigns within the management interface.
Most RaaS operators offer a high level of “support” for their affiliates, and this one is no different. SMAUG offers full support for both their customers and victims.
Customizable Malware, But Mind Your Targets
In SMAUG’s service advertisements, they state “Infecting CIS is forbidden and will result in a ban” In this context, CIS is the ‘Commonwealth of Independent States’ aka the group of independent countries that were once part of the Soviet Union.
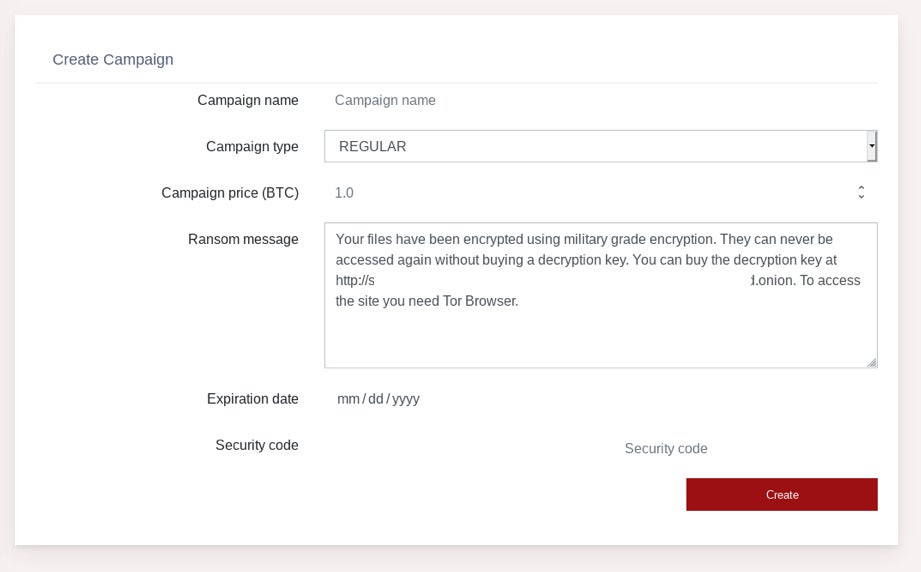
Campaigns created by SMAUG are, as stated, fully customizable, allowing attackers to set their desired price (BTC), deadline/timing constraints, as well as the actual ransom note’s message.
SMAUG-generated malware is designed to execute extremely fast. They tout this as follows:
“The payload utilizes multi-threaded native code which ensures the encryption is done before your victims can react to it.”
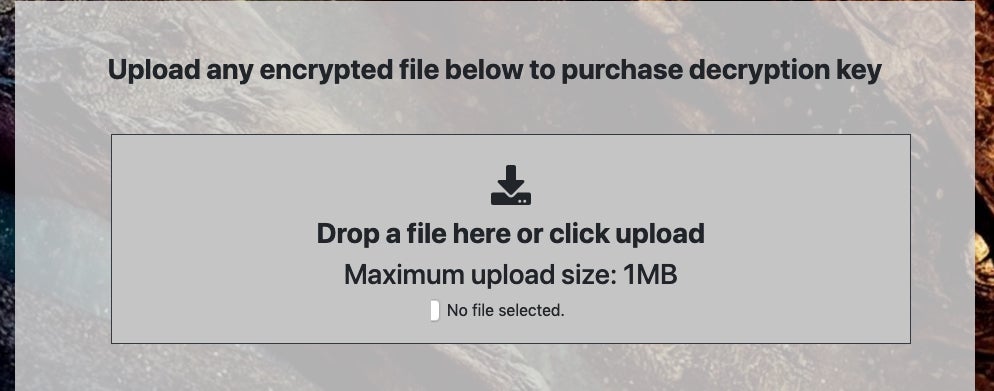
Payloads are generated directly in SMAUG’s web-based management interface. While many RaaS offerings provide their own offline builder, this can often complicate the process, and lead to issues for the aspiring attackers. SMAUG works around this with their “simple web UI”. Victims are able to submit a single file for decryption for free. Beyond that, they must comply with the ransom demands as set in the campaign.
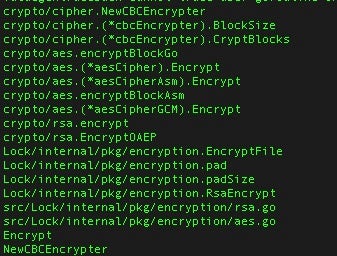
Individual files are encrypted via AES-256. An RSA-2048 public key is used to encrypt the AES encryption key.
Go Payloads
The SMAUG payloads for Windows are obfuscated Go binaries. With that in mind, these payloads begin to bear a resemblance to other similar Ransomware services (ex: Project Root).
Upon launch the malware will drop a copy of itself into a local driver directory, such as:
C:WindowsSysWOW64driversC:WindowsSystem32drivers
The malware will then attempt to establish persistence via LoadAppInit_DLLs key in the registry. For example,
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionWindowsLoadAppInit_DLLs
The SMAUG payloads contain additional functionality to gather system information and stored browser credentials. Encryption is achieved via simple AES-256, again similar to Project Root and other Go-based ransomware services. Upon encryption, affected files will have a lengthy extension added (e.g., 11bdd939-1d45-421c-9be0-0addcdc8181c)
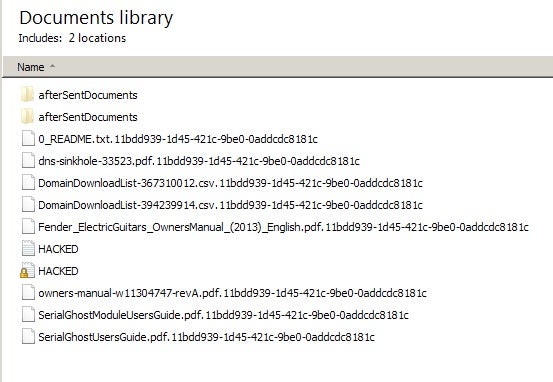
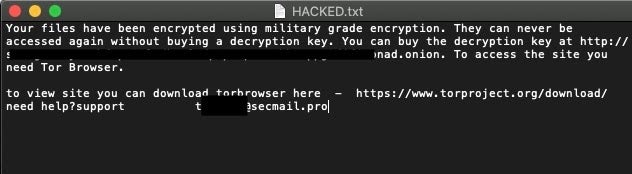
A ransom note is deposited in all directories containing encrypted files. In our analyzed example, the dropped ransom note was simply named “HACKED.TXT” with the following contents:
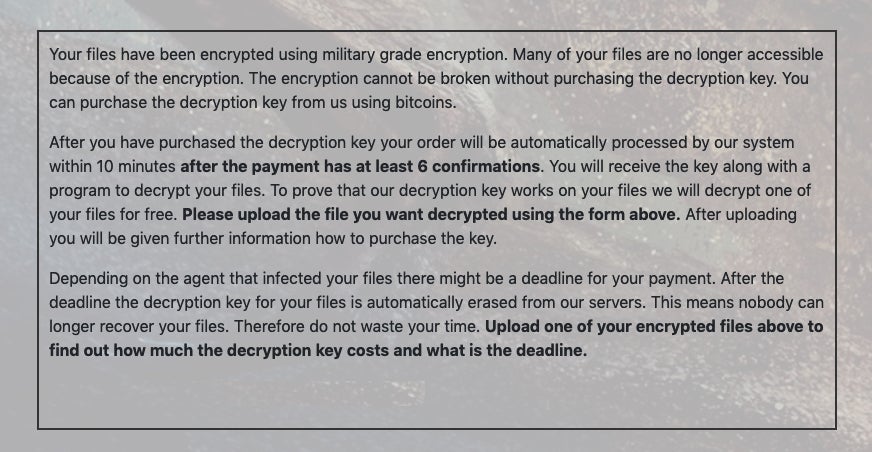
“Your files have been encrypted using military grade encryption. They can never be accessed again without buying a decryption key. You can buy the decryption key at http://[redacted].onion. To access the site you need Tor Browser.
to view site you can download torbrowser here – https://www.torproject.org/download/
need help?support [redacted]@secmail.pro”
Victims are instructed, via the ransom note, to visit SMAUG’s onion-based portal for payment instructions and processing.
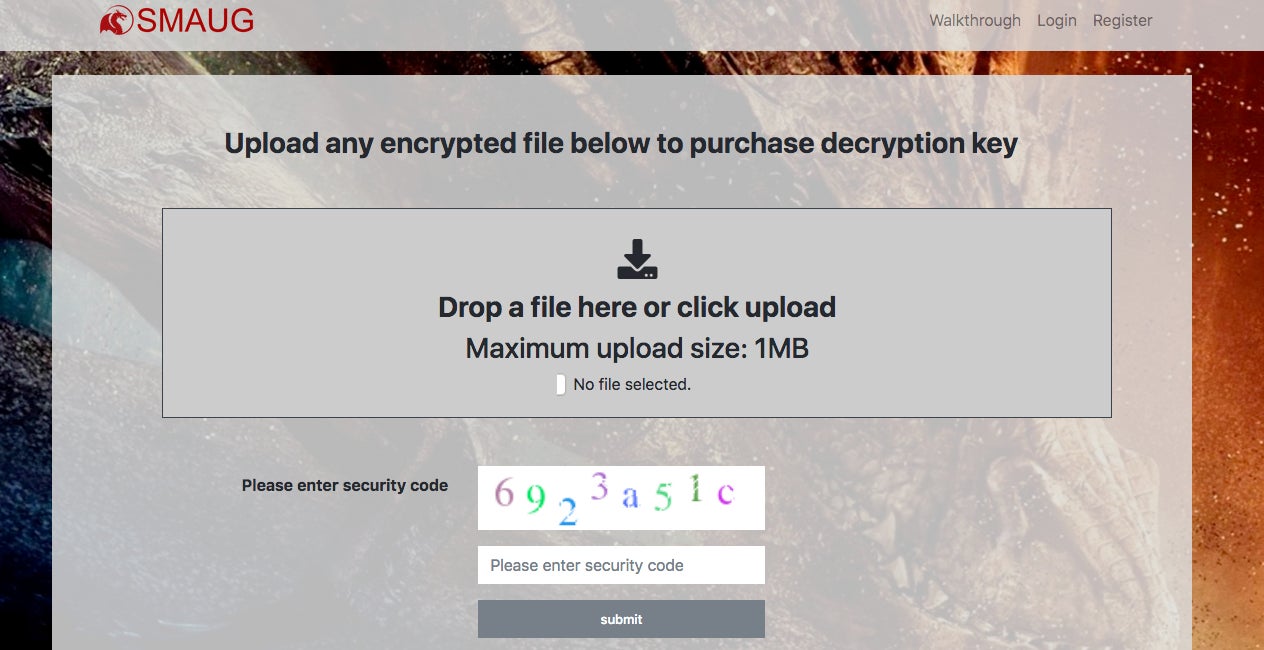
Oddly enough, SMAUG appears to have one of the most “helpful” payment (aka extortion) portals we have seen. Their walkthroughs (for both victims and affiliates) are very thorough:
Conclusion
Protecting your environment against threats like SMAUG is more critical than ever. In order to prevent loss of data and the consequences of a large-scale data breach, organizations must rely on a modern, well maintained, and properly-tuned and trusted security solution. Prevention is key with these attacks. Even in the event that the encryption/data-loss can be mitigated through decryptors, backups or rollbacks, victims still face the problem of their data being posted publicly. We encourage security teams to analyze and understand the threats and to take swift and appropriate action to prevent incidents occurring in the first place.
Indicators of Compromise
SHA1
929b10f78565660535a07917d144d00b0c117571
SHA256
F2363a355fe226cb2f7f1afa72daecc5edfe1cb0edc1295856fb3f874d941b6d
MITRE ATT&CK
Data Encrypted for Impact T1486
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder T1547
Exfiltration Over C2 Channel T1041
Obfuscated Files or Information T1027
Credentials from Password Stores T1555
Credentials from Password Stores: Credentials from Web Browsers T1555.003
Inhibit System Recovery T1490




