Sarwent has received little attention from researchers, but this backdoor malware is still being actively developed, with new commands and a focus on RDP.
Executive Summary
- Updates to Sarwent malware show a continued interest in backdoor functionality such as executing PowerShell commands.
- Updates also show a preference for using RDP
- Sarwent has been seen using the same binary signer as at least one TrickBot operator[1]
Background
Sarwent appears to have been actively used since at least 2018 but not a lot has been publicly reported about it during that time period.
Research Insight
Sarwent functionality has historically revolved around being a loader, as shown by the limited number of original commands:
|download| |update| |vnc|
Some other functionality that has remained consistent is its AV(AntiVirus) checking.
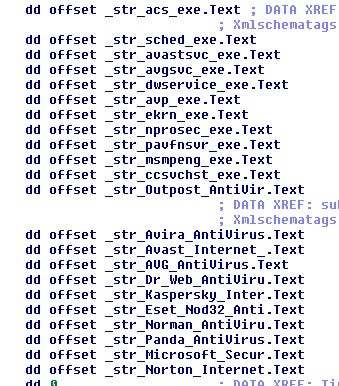
Recent updates include a minor change to their C2 URI structure[2].
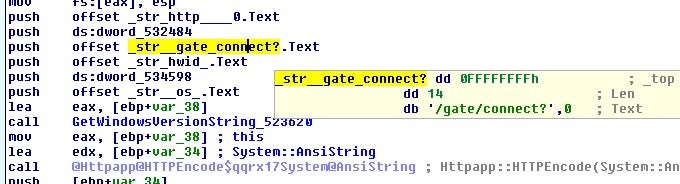
Also, there has recently been the addition of a number of commands that would normally be seen in malware that focus more on backdoor or RAT like capabilities.
|cmd| |powershell| |rdp|
These are interesting updates and additions; cybercrime groups have continued to try to leverage as much as they can for monetization and RDP continues to be a focus as can be seen in the recent proliferation of services selling access to systems[3].
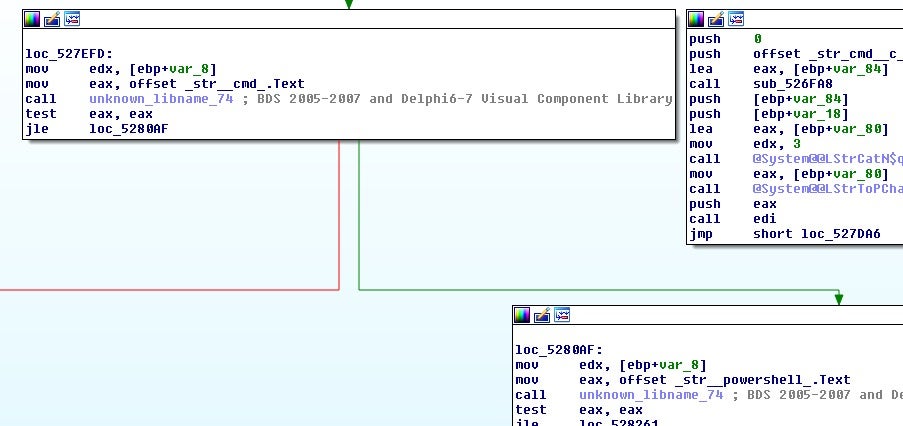
The ‘cmd’ and ‘powershell’ commands are simply commands to be detonated.
The results are base64 encoded and sent back to the C2 through the matching URL route.
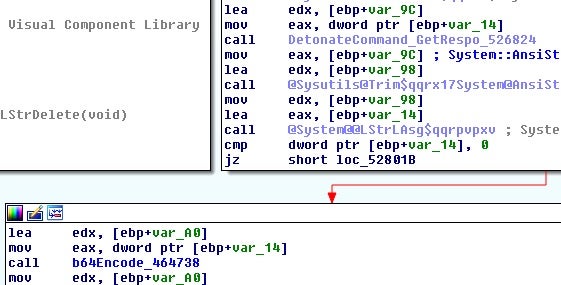
C2 routes for sending responses:
/gate/cmd_exec /gate/powershell_exec
The ‘rdp’ command is a bit different; the code execution looks like it serves to tell the bot to perform a series of tasks:
- Add a new user
- List groups and users
- Punch hole in local firewall
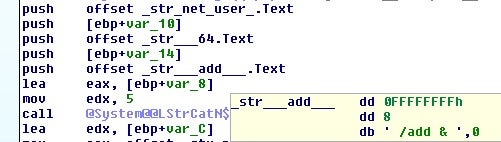
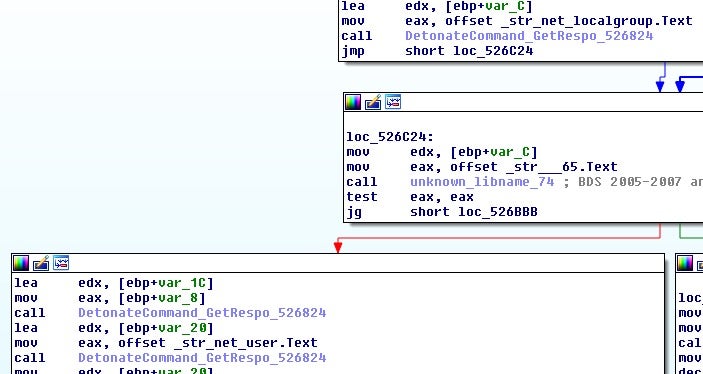
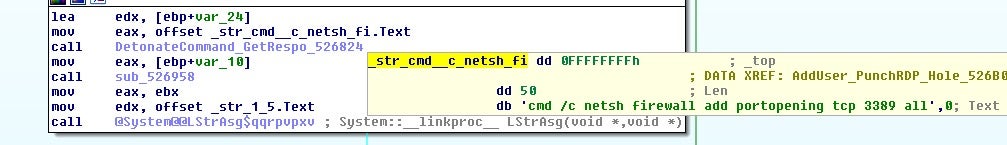
This command, then, is more related to setting up the system for RDP access at a later time.
Mitigation & Recommendations
Endpoint:
CommadLine="cmd /c ping localhost & regsvr32 /s *"
Network: A number of network rules already exist in Emerging Threats[4], so I decided to look at adding some Suricata rules that might not be currently covered.
Suricata rules:
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:”Sarwent CMD response Post”; content:”POSt”; http_method; content:”/gate/cmd_exec”; http_uri; classtype:trojan-activity; sid:9000040; rev:1; metadata:author Jason Reaves;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:”Sarwent Powershell response Post”; content:”POST”; http_method; content:”/gate/powershell_exec”; http_uri; classtype:trojan-activity; sid:9000041; rev:1; metadata:author Jason Reaves;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:”Sarwent RDP exec response”; content:”GET”; http_method; content:”/gate/rdp_exec?command=”; http_uri; content:”&status=”; http_uri; classtype:trojan-activity; sid:9000042; rev:1; metadata:author Jason Reaves;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:”Sarwent update exe response”; content:”GET”; http_method; content:”/gate/update_exec?command=”; http_uri; content:”&status=”; http_uri; classtype:trojan-activity; sid:9000043; rev:1; metadata:author Jason Reaves;)
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:”Sarwent update command”; content:”200″; http_stat_code; content:”fHVwZGF0ZX”; startswith; http_server_body; flow:to_client, established; classtype:trojan-activity; sid:9000044; rev:1; metadata:author Jason Reaves;)
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:”Sarwent download command”; content:”200″; http_stat_code; content:”fGRvd25sb2Fkf”; startswith; http_server_body; flow:to_client, established; classtype:trojan-activity; sid:9000045; rev:1; metadata:author Jason Reaves;)
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:”Sarwent powershell command”; content:”200″; http_stat_code; content:”fHBvd2Vyc2hlbGx8″; startswith; http_server_body; flow:to_client, established; classtype:trojan-activity; sid:9000046; rev:1; metadata:author Jason Reaves;)
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:”Sarwent rdp command”; content:”200″; http_stat_code; content:”fHJkcH”; startswith; http_server_body; flow:to_client, established; classtype:trojan-activity; sid:9000047; rev:1; metadata:author Jason Reaves;)
Indicators of Compromise
Download Location:
whatsmyhomeworthlondonontario[.]ca/wp-admin/version.exe
beurbn[.]com/install.exe
V2 samples
Hash:
3f7fb64ec24a5e9a8cfb6160fad37d33fed6547c
Domains
seoanalyticsproj.xyz
seoanalyticsproewj.xyz
seoanalyticsp34roj.xyz
seoanalyticsptyrroj.xyz
seoanalyticsprojrts.xyz
seoanalyticspro32frghyj.xyz
Hash:
ab57769dd4e4d4720eedaca31198fd7a68b7ff80
Domains
vertuozoff.xyz
vertuozoff.club
vertuozofff.xyz
vertuozofff.com
vertuozofff.club
vertuozoffff.club
Hash:
d297761f97b2ead98a96b374d5d9dac504a9a134
Domains
rabbot.xyz
terobolt.xyz
tebbolt.xyz
rubbolt.xyz
rubbot.xyz
treawot.xyz
Hash:
3eeddeadcc34b89fbdd77384b2b97daff4ccf8cc
Domains
rabbot.xyz
terobolt.xyz
tebbolt.xyz
rubbolt.xyz
rubbot.xyz
treawot.xyz
Hash:
106f8c7ddbf265fc108a7501b6af292000dd5219
Domains
blognews-journal.com
startprojekt.pw
blognews-joural.com
blognews-joural.best
blognews-joural.info
startprojekt.pro
V1 Samples
Hash:
83b33392e045425e9330a7f009801b53e3ab472a
Domains
212.73.150.246
softfaremiks.icu
shopstoregame.icu
shopstoregamese.icu
Hash:
2979160112ea2de4f4e1b9224085efbbedafb593
Domains
shopstoregame.icu
softfaremiks.icu
shopstoregamese.icu shopstoregamese.com shopstoregames.icu
References
1: https://twitter.com/VK_Intel/status/1228833249536987138
2: https://twitter.com/James_inthe_box/status/1228788661006659584
3: https://twitter.com/VK_Intel/status/1242587625409609731
4: https://github.com/silence-is-best/c2db




