At Sentinel Labs, we have been closely tracking adversarial behavior as it pertains to COVID-19/Coronavirus. To date, we have observed a significant number of malware campaigns, spam campaigns, and outright scams that are preying on the fears and uncertainties of the global population.
Updates are tagged in-line with respective dates within each section of this post.
September 2020
[September 9, 2020]
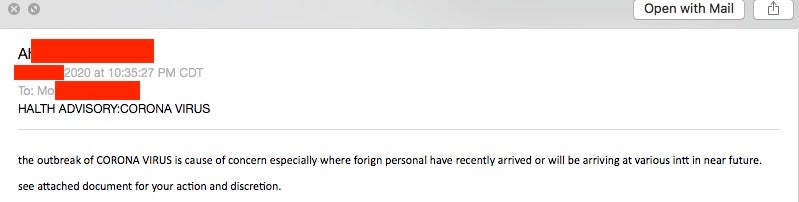
On August 27, the Health Sector Cybersecurity Coordination Center (HC3) released report ID: 202008271653. This report details a specific phishing campaign used to distribute the Agent Tesla RAT. The lure in the emails is centered around updates to COVID-specific PPE (Personal Protection Equipment). We have seen similar campaigns running since late April / early May, and these current example do not stray far from the standard template. The emails contain a RAR’d or Gzip’d attachments that install the Agent Tesla RAT upon execution.

During the first week of September, we observed multiple campaigns delivering the Sepulcher trojan. The phishing emails appear to be sent from the World Health Organization, claiming to contain updated technical and geographical guidance around Coronavirus safety measures. As with the Agent Tesla campaigns, these have been ongoing for several months, and the general templates have changed only slightly in the following months.
Following the same theme and cadence we continue to observe campaigns spreading the Lemon Duck cryptomining trojan via Coronavirus-themed phishing emails. Lemon Duck is a primarily “file-less” cryptomining trojan which is also able to spread via Eternalblue. Phishing emails will typically be disguised as messages from the WHO, or as more ‘conspiracy’-minded messages with subjects similar to “The Truth of COVID-19” or “What you have not been told about CORONAVIRUS”.
August 2020
[August 21, 2020]
Throughout July and August 2020, we have continued to observe malicious actors leveraging COVID-19 as a social-engineering lure. In addition, prominent malware families continue to spread though COVID-19-themed messages and/or websites.
The rise of so called ‘contact tracing’ applications have provided malware authors with yet another easily exploitable path to infection. One such example was observed in the form of CryCryptor. CryCryptor is focused on Canadian citizens, capitalizing on the recent announcement of a nation-wide tracing app, named “COVID Alert”. Victims are instructed to contact the attacker via email following the encryption of common file types on the infected device.
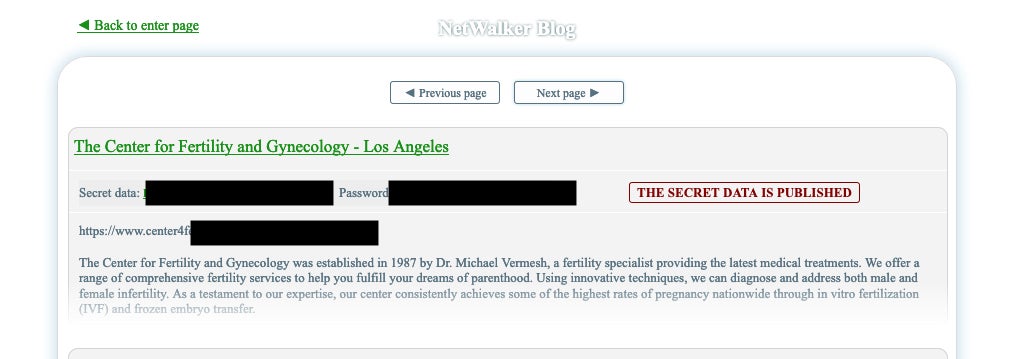
We have continued to observe Ransomware campaigns leveraging COVID-19 as a lure. NetWalker, in particular, has been highly prolific in this area. There has also not been any observable slowdown in the targeting of medical facilities/entities. NetWalker, Maze, and Snake have all successfully targeted Healthcare and medical facilities over the last 2 months. In fact, of all the industries represented on NetWalker’s victim shaming blog, the most prevalent is Healthcare.
As our time w/ this pandemic progresses, and our medical and science experts gather more data on COVID-19, they also become larger and more valuable targets. In July 2020, The United States Department of Justice, along with other authorities, release details surrounding an extended campaign targeting COVID-19 research data. Authorities involved have attributed campaigns aimed at COVID-19 research data to both Chinese and Russian-backed actors. One such advisory specifically covers the use of CVE-2019-11510 (Pulse Secure VPN) to gain initial access into targeted environments.
June 2020
[June 12, 2020]
We continue to observe the use of COVID-19 as a lure in malicious Android applications. This has been somewhat amplified in the uptick in publishing of ‘contact tracking’ or ‘contact tracing’ applications. The Anubis and SpyNote trojan families have been particularly prolific in this area. Both Anubis and SpyNote have been identified in contact tracing apps aimed at various locales (ex: Indonesia, Iran, Russia, Italy). Both trojan families aim to extract sensitive or personal information from the target device. Malicious functionality in these trojanized contact-tracing applications includes:
- Full access to SMS data and activity
- Injection and visibility into other applications (ex: banking applications and password vaults)
- Keylogging
- Voice, Screen, and Camera recording and exfiltration
- Access to critical device information and system details

These types of malicious apps have been observed in official app stores/distribution channels, as well as ‘less-than-official’ app stores. We encourage all users to be extra critical of what apps they install, and where they are installing from. It is not always enough to ensure that you are squiring Android applications from the ‘official’ Google store.
The rise of unemployment and the need for medical/sick leave has brought about a new angle for COVID-related social engineering lures. Criminals have increased the use of weaponized medical leave forms, PTO requests and resume/CV forms and templates in an effort to further spread malware. In recent weeks, Trickbot, ZLoader and other high-profile malware families have been embracing these particular vectors. Weaponized forms are spread via email, primarily as Word documents, however we have observed alternate file formats as well (ex: ISO). Researchers at Checkpoint have expanded on these campaigns in recent weeks as well.
On June 11, the FBI released PSA (Public Service Announcement) 1-061120-PSA. This bulletin details the use of fraudulent shipping and insurance fees being charged by criminal actors. Opportunistic actors are citing false COVID-19-related updates to shipping laws, regulations, and requirements as justification for charging the unnecessary fees. According to the PSA, “Examples of this criminal activity include demanding fraudulent COVID-19 insurance fees after the purchase for the delivery of live pets from online U.S. websites. An additional example includes criminal actors fraudulently collecting “refundable” maritime insurance fees, citing fake COVID-19 laws.”. Per the FBI’s guidelines, we encourage all to be extra careful and always avoid giving any personal information to non-trusted companies or individuals. Verify all charges related to shipping and processing upon any transaction and be particularly wary of any new or unnecessary charges tied to COVID-19 laws and regulations.
Criminals are continuing to target government entities and task forces directly tied to COVID research and PPE production. IBM’s X-Force recently documented a wide-spread campaign targeting ~40 critical organizations in an effort to disrupt operations and extract sensitive information. Spearphishing emails were sent to high-level executives at the targeted organizations, which included an unnamed German corporation tied to procurement of personal protective equipment. These attacks serve as a reminder on just how successful email-based distribution of malware still is. Email / Phishing / Spearphishing remains to be the most effective method of malware distribution.
May 2020
[May 28, 2020]

The fuckunicorn ransomware “family” was observed in a typo-squatting campaign focused on the Italian Federation of Pharmacists. The legitimate domain serves timely information on Covid-19 to the Italian community. The ransomware campaign crafted a malicious website mimicking the IFP site, along with a slight variation of the IFP site domain name. Similar to past attacks, users are lured into downloading the ransomware which masquerades as a Covid “dashboard tracker”. This threat was also highlighted by @JAMES_MHT on May 25th. The ransomware itself is based on the aging open source ransomware “kit” Hidden Tear. As a result, the ransomware is non-complex, easy to analyze, and should pose little issue when it comes to detection and prevention. Keeping with the theme, the ransomware note is also in Italian.
From May 21st onward, we observed multiple COVID-themed spam campaigns distributing the Warzone RAT (Remote Access Trojan). The malicious spam messages were crafted to exploit CVE-2017-11882. The remote code execution flaw is specific to Microsoft Word Equation Editor. Once exploited, the Warzone RAT payload is downloaded and installed.
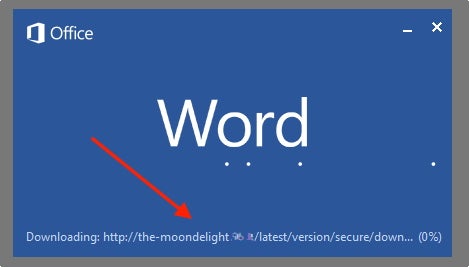
We have also observed multiple COVID-themed spam campaigns spreading the IcedID trojan. These are rather generic maldocs which contain obfuscated VB/Macros which retrieve a specially-crafted .PNG image file. The malware is subsequently extracted from the .PNG images and launched.
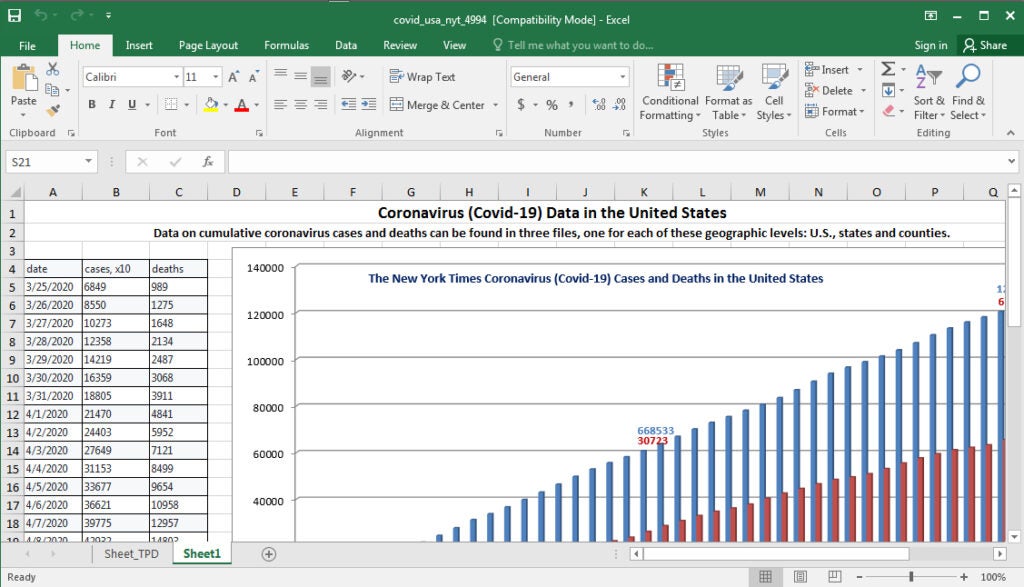
The Johns Hopkins Center continues to be a valuable lure for potential attackers. Microsoft recently disclosed details around a COVID-themed phishing campaign which leads to installation of the NetSupport Manager RAT. These campaigns are reportedly very prolific, and leverage maliciously-crafted Excel documents to facilitate the delivery of the malware. Most of the samples we have observed follow a predictable naming convention (ex: covid_usa_nyt_*) where “*” is replaced with a series of four numbers (ex: covid_usa_nyt_8072.xls). The Excel documents, which contain updated information and statistics around Coronavirus, contain macros which download and launch the malware. Microsoft states that there are “hundreds of unique Excel files” used by the campaign, however they all communicate with the same C2 server. The NetSupport infections are particularly problematic as they download and install multiple additional components post-infection.
[May 20, 2020] The last 2 weeks have seen an increased number of COVID-themed campaigns from both Trickbot and Formbook. The Formbook campaigns have been targeting educational institutions, via phishing messages with a trojanized application for teachers. Formbook. like other stealers, is focused on harvesting sensitive data. Recent Trickbot phishing emails have been masquerading as official details around the Family Medical Leave Act and other similar (and timely) lures.
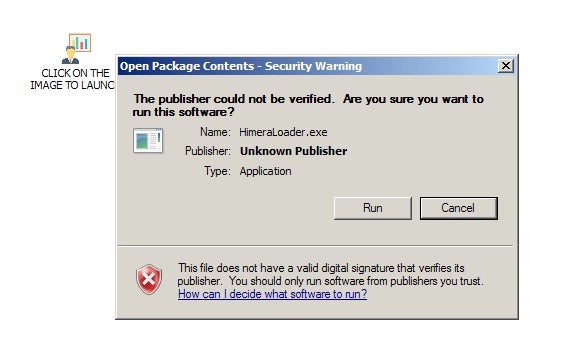
On May 11th, twitter user @cocaman tweeted information on a COVID-themed dropper for HimeraLoader. Similar to the previously mentioned Trickbot campaigns, the HimeraLoader-centric attacks utilize the FMLA as a lure, prompting victims to open a malicious Word document, leading to the installation of the malware. Upon installation, the malware will create a schedule task for persistance, as well as drop additional components.

On May 17th, @JAMESWT_MHT, along with @malwrhunterteam noted a new variant of MBRLocker dubbed “CoViper”. This variant displays Coronavirus-related warnings after the host has been infected and rebooted.
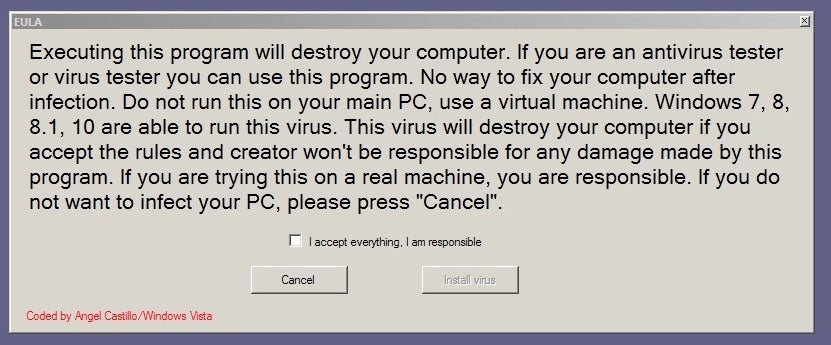
On May 14th, the MalwareHunterTeam noted a new Node.js-based trojan spreading with the help of COVID-themed lures. Initial delivery appears to have been via phishing email, with .jar attachments (Company PLP_Tax relief due to Covid-19 outbreak CI+PL.jar). Upon execution, the .jar (a downloader) retrieves additional malware, written in Note.js. Once infected, the attackers have RAT-like control over the targeted host. Persistance is achieved via an entry in the registry ‘run’ key (HKCUSOFTWAREMicrosoftWindowsCurrentVersionRun).
With regards to mobile platforms, we continue to see malicous apps, disguised as Covid-releated resources, being seeded though multiple outlets. These are all primarily infostealer trojans or other similar spyware. One such example was discovered simply named “Covid.apk” with the package name “DZ.Eagle.Master” (or variants thereof). These trojans are engineered to harvest and transmit personal information.
On May 14, Microsoft announced a new initiative to provide COVID-19-themed IOCs/indicators via a free feed. These indicators are automatically wrapped into various Microsoft-base protection technologies. However, environments that utilize other vendors are able to leverage the IOCs as needed. The hash-based IOCs cover multiple file and threat types, and are readily available via the Microsoft Graph Security API and the Azure Sentinel GitHub. Enterprise customers using MISP can easily imp0rt/ingest the data as well.
Credential-harvesting spam/phish campaigns and COVID-themed ransomware for Android top the highlights for this week’s update. Attackers are employing a few novel lures in their phishing campaigns, as well as modifying some well-known ones (ex: FedEx and UPS phishing lures).
Early in the week, the FBI issues Flash Alert MI-000124-MW, covering specific indicators for COVID-19 phishing email campaigns. The listed indicators cover more of what has been observed over the last few months. That is, generic phishing emails enticing victims with COVID-based details including “Updated COVID Tracking Details” , “Updated WHO Recommendations for COVID-19” and similar. The covered campaigns have primarily been engineered for credential harvesting. Some utilize commodity malware, where others simply redirect to weaponized phishing sites. We have observed the following families tied to the malware-based campaigns:
- Lokibot
- Agent Tesla (MITRE S0331)
- AZORult (MITRE S0344)
- Adwind
- Generic exploitation of CVE-2017-11882
Throughout the last few weeks, we have seen an uptick in the use of UPS or FedEx-based lures used in phishing campaigns. While this alone is not new, these tried-and-true lures have been modified for the current times. Combining these methods within the context of ‘shipping delays’ due to the pandemic is more novel. Generally, these messages claim to be from FedEx, UPS, or DHL, prompting the victim for action due to a shipping delay resulting from Coronavirus. A majority of these are redirect-based credential harvesters, however many do also contain malicious attachments.
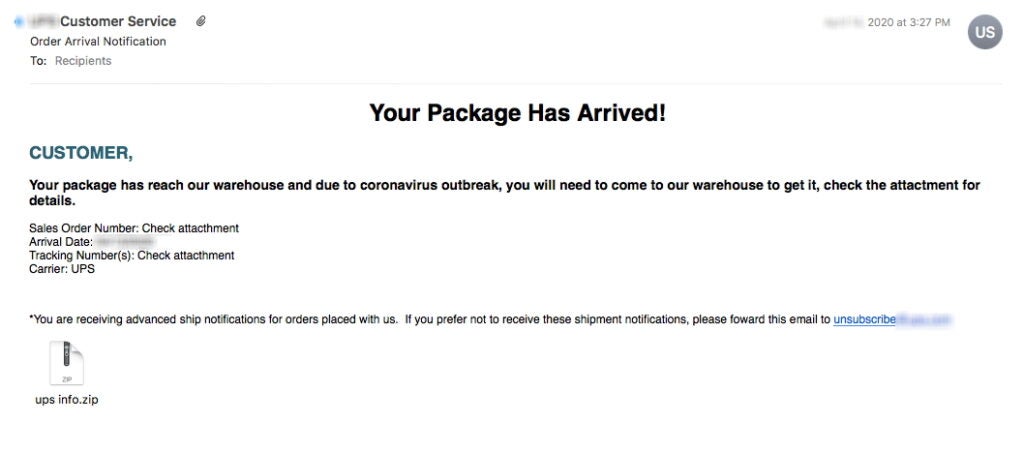
We have also seen a slightly new theme in the form of fake employment termination messages. These are targeted messages, which cite the pandemic as the cause for the victim’s termination from their respective company.
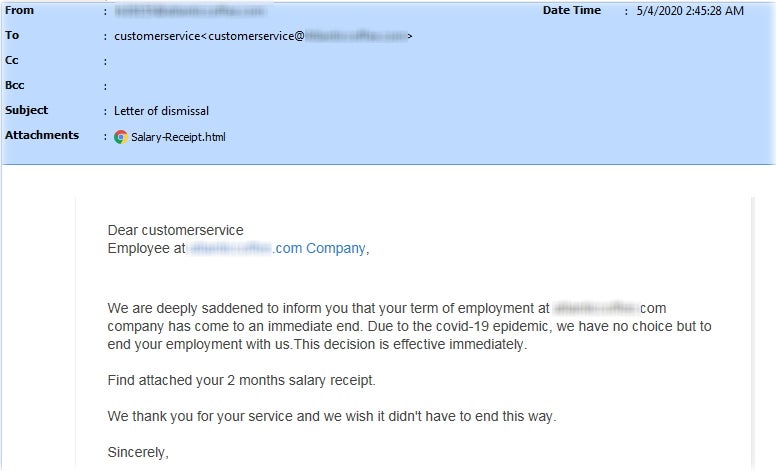
Associated malware includes:
- Remcos RAT (MITRE S0332)
- Bsymem
Cyber criminals are still taking advantage of the pandemic to spread ransomware, including on Android. In the last few weeks, we have observed multiple instances of the SLocker trojan. This is a very basic “locker” which masquerades as an informative application for Coronavirus. Once installed, the malicious application will block user activity, requesting payment (PayNet). When infected, users are met with the following (translated) message:
Congratulations!Your phone is blocked! You have 20 minutes to enter the code, otherwise the phone will not turn on again …Don’t see this as an arbitrary message, it will be difficult for you 🙁Unlock passwordExact timeTo unlock the code, call +998 998 910 312 Make 8000 paynet and get the code. (Don’t ask for the code without Paynet, I won’t tell you anyway)

Behavior varies across different versions and flavors of Android.
April 2020
[April 27, 2020]
Attacks/campaigns using COVID-themed lures has continued to increase over the last week. We continue to observe increasing amounts of malicious messages and websites preying on the fear and uncertainty around the pandemic. There has been an overall increase in pure credential-harvesting, many of which are referencing U.S. government stimulus payments and small-business loan packages. In that category, multiple campaigns have been observed which directly masquerade as the United States Small Business Association (SBA).
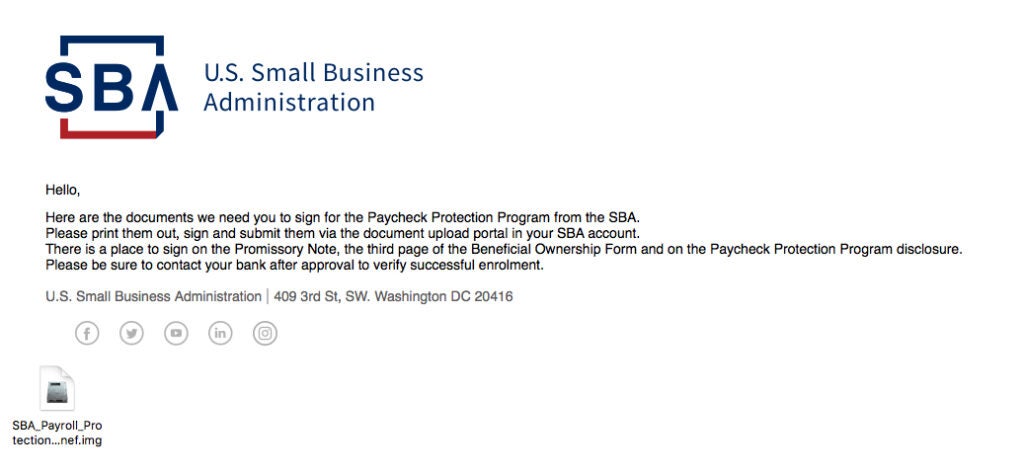
This particular example was part of a widespread campaign used to spread Remcos RAT. (MITRE S0332). Remcos is a full-feature RAT capable of harvesting credentials, sensitive documents and information, as well as compromise basic functionality (keylogging, microphone access, screenshots, webcam control) and beyond. There are similar attacks focused on non-United States countries and financial entities as well
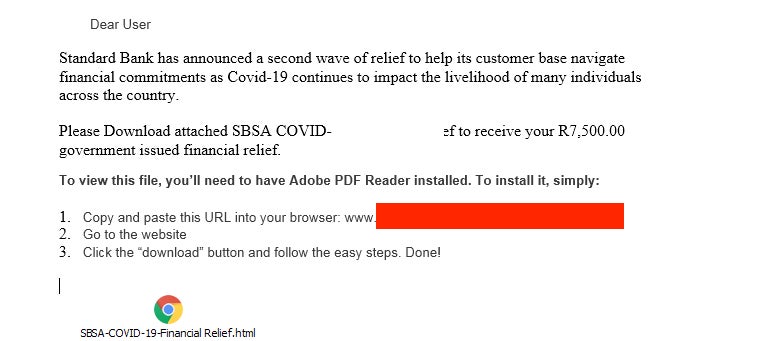
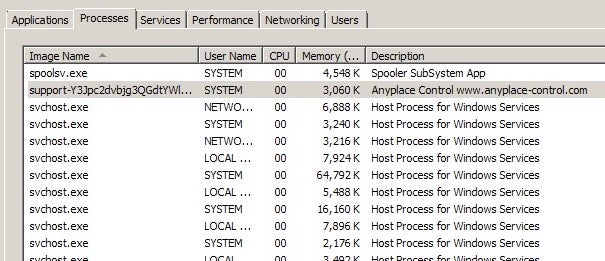
In mid-April, we observed a variant of the Anyplace RAT as it was uploaded to multiple malware sample collection repositories.
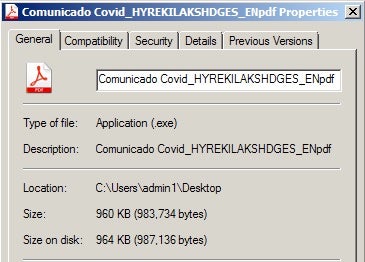
The Anyplace RAT campaign masquerades as an official communication from Epay, providing updates on their current operating abilities. Like Remcos, Anyplace is a full-featured remote access trojan. Upon execution, the dropper and primary executable are written to c:Program Files (x86cdc.
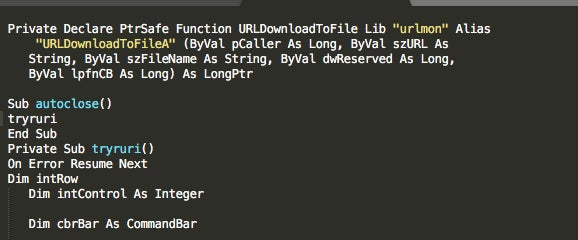
The actors behind Trickbot have continued in their prolific ways throughout the last month. We have observed multiple spam campaigns spreading Trickbot (along with additional subsequent threats). Many of the lures are centered around false DocuSign forms hosted on Google Docs, or shared directly as an attachment. When the documents are opened, the embedded macros run, leading to the Trickbot infection.
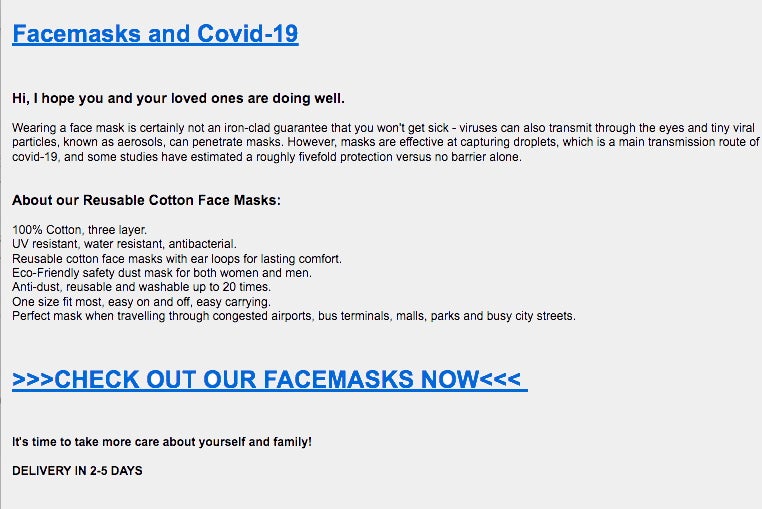
Rounding out some of the latest highlights, we have continued to observe malware campaigns utilizing more ‘commodity’ families (Loki, Tesla, Gomorrah). As with previous examples, COVID-themed attachments or email lures play a major role in these attacks. In one such example, we have Tesla Keylogger disguising itself as an image of “protective face masks”.
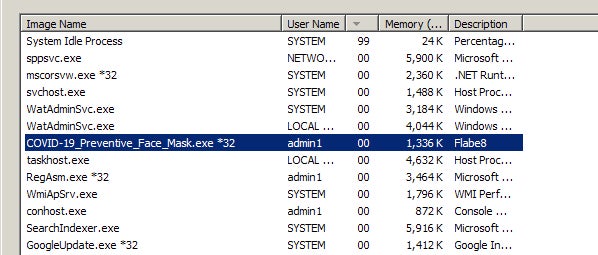
This is a lure which is repeated frequently in Tesla Keylogger campaigns.
As a reminder, beyond the onslaught of malware and attacks that we all battle with every day, the outright scams associated with COVID-19 have not slowed down.
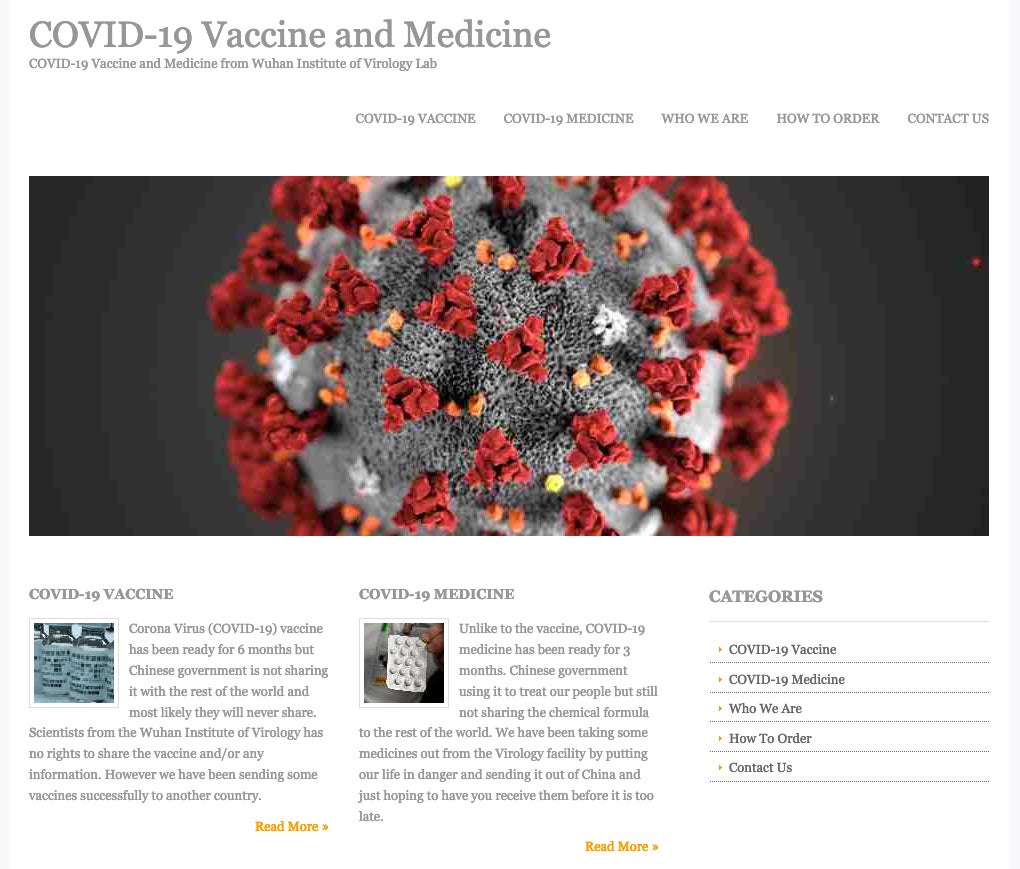
There are many low-sophistication scammers out there using current events for quick financial gain. Continue to be hyper-aware and cautiously-critical.
[April 14, 2020] In mid-April, we observed a short-lived COVID-themed ransomware attack. Spam email messages, containing COVID-themed malicious word documents were used to drop a ransomware payload based on HiddenTear (open source ransomware)
Once opened, the document drops the ransomware into ~AppDataLocal and executes it. When executed the ransomware attempts to contact the C2 server for additional components (desktop image) and communicates data on the victim host. Encrypted files are renamed with a “.locked20” extension.
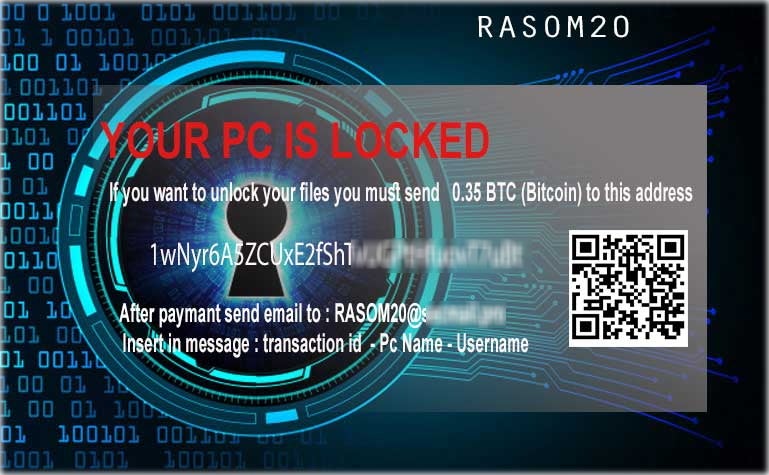
[April 14, 2020] HiddenTear is a long-standing open source ransomware framework. SentinelOne Endpoint Protection detects and prevents all malicious activities associated with this threat.
[April 14, 2020] In early April, several Android-focused campaigns were observed spreading the Anubis and Cerberus banking trojans to victims seeking additional information on Coronavirus in their area. Many were specifically targeted towards users in Italy and China. The malicious apps claim to track and inform users of COVID-specific updates for their region (a very common lure). Often times, the data in the app will be legitimate (redirection) but the app will request permissions beyond what is needed or required, allowing it to exfiltrate personal data to the remote location of their choice.
[April 14, 2020] In late March, a wide-spread phishing campaign was observed using COVID-themed email messages masquerading as notifications from the “Department of Health”. The email messages contained a malicious link which leads victims to a page designed to harvest Outlook/Office credentials. Email sender and subject examples are below:
- Sender: “Department of Health” <department[.]health-pandemic[@]zacks[.]com>
- Subject: “HIGH ALERT: COVID-19 cases surpassed 300,000 globally”.
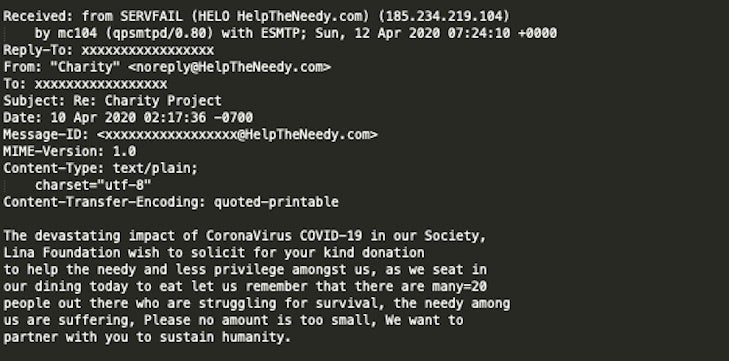
[April 14, 2020] Fake charity and donation scams have become more and more frequent since the onset of the pandemic. Criminals are constantly pivoting though COVID-themed lures while preying on the fear and uncertainty looming over the population. An example of one such scam (“Lina Charity Foundation”) can be seen below. These messages are distributed en masse. In the example below, we have removed the supplied banking details. The groups behind these do often include these details (Bank name, Address, Swift codes, IBAN numbers) in order to enable their victims to complete the fraudulent donations / transfers.
[April 14, 2020] Throughout late March/early April, multiple COVID-themed Ursnif campaigns were observed. Traditionally, Ursnif is utilized for information theft and data exfiltration. This includes credential harvesting, banking information and similar. Malicious messages arrive with malicious Word documents. When opened (and macros run) the documents will execute scripts to pull additional components from a removed server. Through multiple stages of obfuscated JavaScript, VBS scripts and/or PowerShell, the final Ursnif payload is written to the victim host.
[April 6, 2020] In early-to-mid-March 2020, Redline Stealer was distributed via a spam campaign using Coronavirus-themed lures. Victims were enticed into downloading and installing a trojanized version of the “Folding@home” client software.
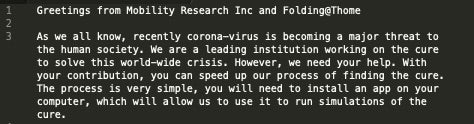
[April 6, 2020] When choosing to download the malicious software, users are presented with the trojanized “foldingathomeapp.exe” executable. Redline Stealer is a well-known commodity malware which can pilfer browser information, credential sets, as well as user and system information.
Throughout March 2020, the Qbot banking trojan was distributed via aggressive spam campaigns. Victims are enticed via messages which claim to link to refreshed PPE supplies (ex: masks & gloves). When following the malicious links, users are led to the Qbot trojan in either EXE or ZIP archive form.
[April 6, 2020] Attackers have been leveraging the United States Stimulus Relief package to entice users into following malicious links which ultimately lead to leakage of personal data in multiple forms. We have observed email and SMS-based campaigns which offer updated information around the stimulus bill, or promise short term loans with the victims expected stimulus to be used as collateral.
These attacks are ongoing and we encourage users to be extra cautious when interacting with COVID-related emails and SMS/TXT messages.
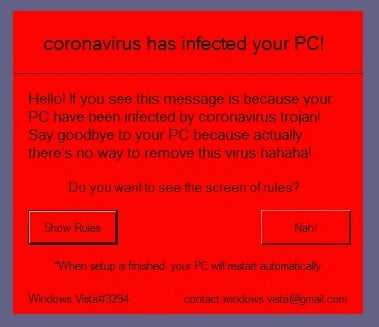
[Update April 1, 2020] On April 1st, a new, multifaceted, malware emerged which leverages the Coronavirus in an attempt to target the emotions of their victims. When executed, the dropper will deposit numerous scripts and dependent files. The threat then proceeds to make a number of configuration changes which negatively affect the security posture of the infected host. The infection routine requires a reboot due to the changes to UAC. After reboot, additional payloads are executed, resulting in the display of an image of the Coronavirus adorned with additional messages following the theme.
In some scenarios, an additional payload will execute which is responsible for overwriting the machine’s MBR (Master Boot Record). The user is then presented with a simple message on a dull grey background, with their access to local data restricted.
Note: SentinelOne Endpoint detects and prevents all artifacts and behaviors associated with Wiper.coronavirus
March 2020
Malware authors are continuing to utilize COVID/Coronavirus as a lure. We have seen ongoing activity from the malware families outlined in this original post, including AdWind, LokiBot, NetSupport RAT, Tesla Keylogger, and Kpot. We have also observed additional malware families joining in on the exploitation of fear around COVID-19.
[March 31, 2020] Coronavirus-themed email messages are used to spread the Hawkeye trojan. Hawkeye is a long-standing credential stealing trojan. In recent campaigns users are targeted via spam messages claiming a “cure” in China and Italy (ex: CORONA VIRUS CURE FOR CHINA, ITALY)
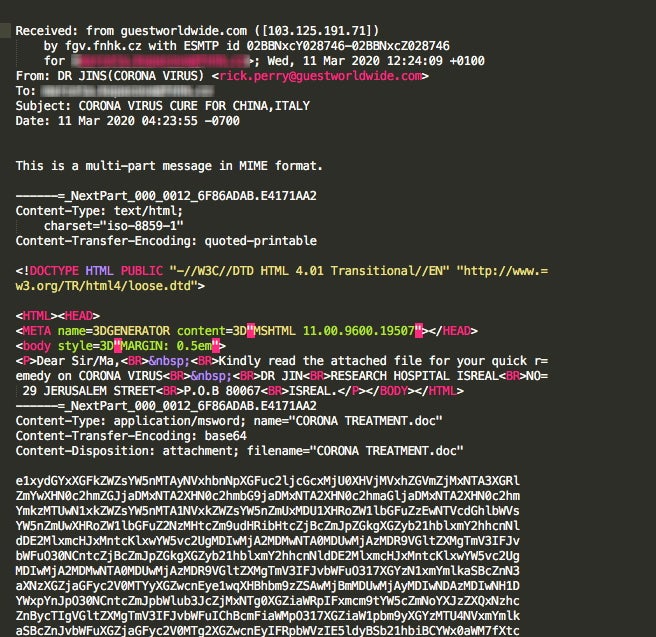
[March 31, 2020] Actors behind the Metamorfo (Casbaneiro) trojan launched a COVID-19-themed spam campaign to spread their malware. Similar to other uses of this lure, victims are enticed to follow a malicious link to receive “more or updated information” on COVID-19 in their region. The malicious links lead to a malicious MSI installer which downloads additional malware and establishes persistent C2 communications.
[March 31, 2020] Coronavirus-themed email campaign used to spread the Nanocore trojan. Victims are enticed with misinformation tied to an update on COVID-19 vaccines. Malicious downloads are named following this theme (ex: “Covid-19 Vaccine.gz”)
[March 31, 2020] Late in March, we observed the Sphinx banking trojan, which is largely based on leaked source code for Zeus, began to aggressively spread via email with COVID-themed messages. In some observed cases victims were enticed to complete a form related to receiving government assistance during the outbreak. The malicious document then proceeds to drop and execute a VBS script. This script establishes C2 communication channels, and downloads additional executable payloads. Beyond the COVID-themed lures, the functionally is largely unchanged with regards to data inception via web injects.
In mid-March 2020, a new family of Android ransomware, CovidLock, began targeting users via malicious app (APK) downloads. The malicious apps were hosted on sites masquerading as hosts for valid real-time information tracking apps. Upon infection, the ransomware tricks users into providing full device control via misleading permissions request dialogs. The malware sets itself to load upon device startup and leads to a lock-screen style ransom request. This specific family utilizes Pastebin to aid in the construction of the displayed ransom notes.
In early March 2020, the APT group Mustang Panda (China) utilized multiple spam campaigns to deliver implants. Spam messages made use of multiple COVID-19-themed lures. Malicious documents were used to execute additional scripts, and leverage subsequent LOTL tactics to retrieve and launch payloads.
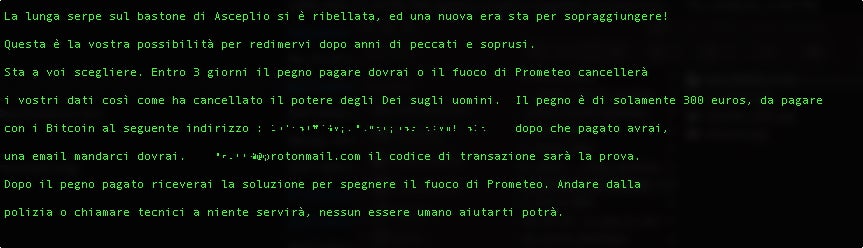
In mid-March 2020, we observed multiple websites hosting fake versions of WiseCleaner utilities. These sites were used to distribute the Kpot Infostealer trojan, along with a new ransomware family dubbed “CoronaVirus”. From the fake WiseCleaner-themed sites, a malicious version of “WSHSetup.exe” was used to download both the CoronaVirus ransomware along with Kpot Infostealer. Once-infected, a customized ransom message is displayed at boot, prior to the loading of Windows. Victims are instructed to email attackers, as opposed to interacting with them via a payment portal site.
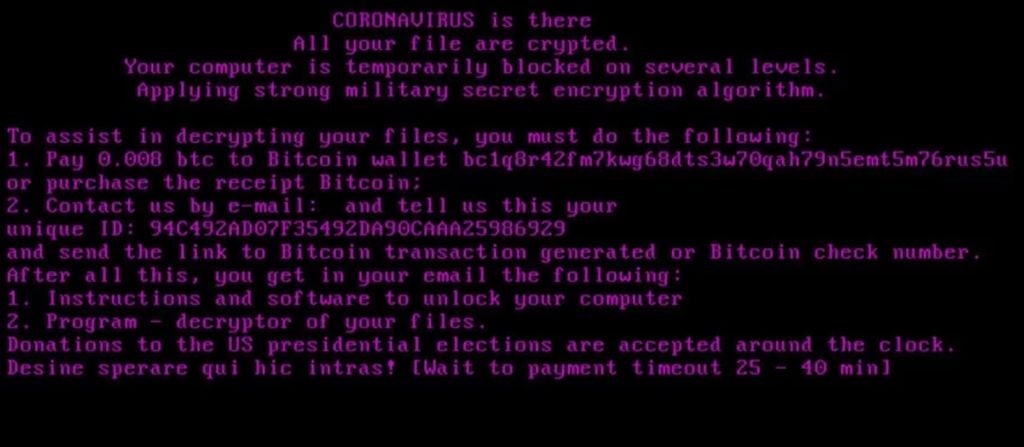
The Kpot Infostealer trojan is coupled with the ransomware in order to harvest cryptocurrency wallets, browser data and credential sets. The requested ransom is typically ~$50.00 USD.
In mid-March, NetWalker ransomware campaigns were observed attacking multiple targets classified under Health and Human Services offices (ex: the Illinois Champaign-Urbana Public Health District). The malware was delivered via email with malicious VBS attachments. Upon launch, the malware proceeds to encrypt targeted file types as well as disabling known anti-virus products (if found).
February 2020
In early February 2020, multiple COVID-19/Coronavirus-themed phishing campaigns were tracked, targeting primarily the shipping and logistics industry. The phishing campaigns were used to spread the AZORult trojan to high-value targets in the shipping sector. Some message samples contained malicious Microsoft Office documents designed to exploit CVE-2017-11882. CVE-2017-11882 is a memory corruption vulnerability in Equation Editor. Successful exploitation allows for the execution of arbitrary code across affected versions of Microsoft Office.
In early February 2020, a massive COVID-19/Coronavirus-themed phishing campaign targeted large swaths of Office 365 users. The motive behind these campaigns was basic credential harvesting. Victims were urged to open malicious attachments which were disguised as updates on COVID-19 patterns in their local areas. Most observed samples masquerading as updates from the “Centers for Disease Control and Prevention”. Attackers took advantage of ‘look-a-like’ domains for added authenticity (ex: cdc-gov[.]org)
In early February 2020, we tracked COVID-19/Coronavirus-themed spam campaigns spreading LokiBot, specifically targeting Chinese entities. Spam messages were seen masquerading as updates from the ‘Ministry of Health in the People’s Republic of China’. Messages were written in English but appear to have been written by a non-native English speaker. The LokiBot malware was distributed in these messages in the form of RAR archives (with .arj extensions).
In mid-February 2020, multiple malicious websites were constructed to deliver the Grandoreio banking trojan. Multiple weaponized sites were utilized, primarily targeting users in Mexico, Spain, and Brazil. The sites utilized a ‘video player’ download-style lure to entice victims into executing the Grandoreio payloads.
In mid-February, the “Corona Virus Map Phishing Kit” was advertised for sale in various underground forums. The kit ranged in price from $200 USD to $700 USD. Buyers are able to customize the kit to embed their own payloads or force a redirection (upon execution of the trojanized map EXE) to remote payloads. The malicious map executable masquerades as legitimate map data from Johns Hopkins University. Indeed a picture (in this case an interactive map) is worth a thousand words, with attackers offering up the ability to load payloads to victims that visit this nefarious coronavirus spread map:
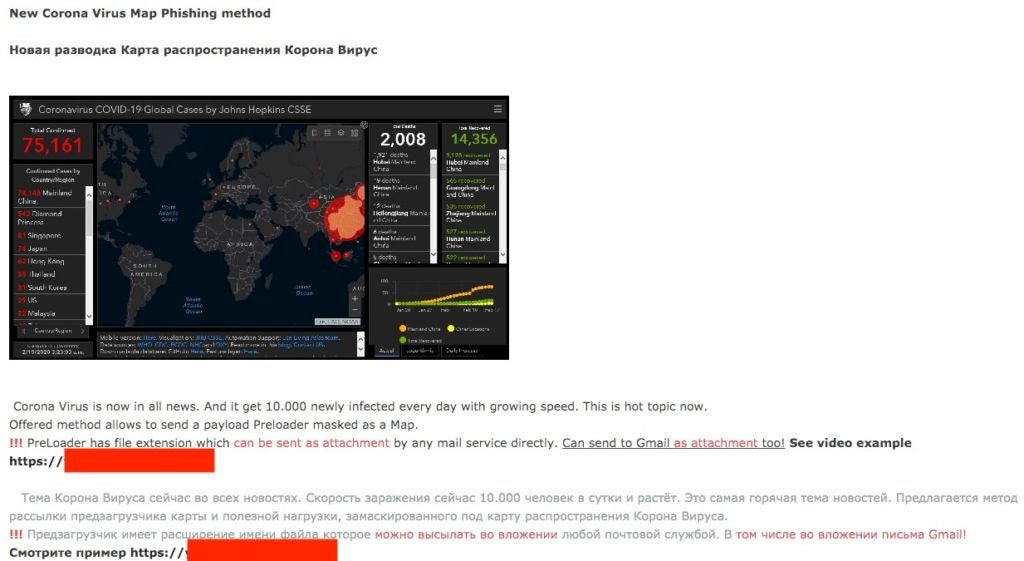
In late February 2020, we observed COVID-19/Coronavirus-themed spam campaigns targeting users in the Ukraine. Spam messages are disguised as updates from the ‘Center for Public Health of the Ministry of Health of Ukraine’. The messages claim to contain updated information for the public pertaining to COVID-19/Coronavirus. Initial waves of the campaign were used to distribute various dropper and downloader trojans.
In late February 2020, COVID-19/Coronavirus-themed spam emails were used to distribute the Tesla Keylogger. Spam messages were constructed via a customized phishing kit. Observed samples are disguised as updates from ‘The Centers for Disease Control’. Victims are enticed into following malicious links in order to access informational “updates for their area”.
In late February 2020, we observed a spam campaign targeting South Korean entities. The spam campaigns were used to distribute BabyShark implants, often associated with the cyber operations of North Korea. Malicious attachments were disguised as official updates on South Korea’s response to COVID-19.
In late February 2020, multiple spam campaigns were observed distributing the FormBook. malware. Messages were disguised as updates from FedEx on their current plans for dealing with issues and delays around COVID-19.
In late February 2020, Trickbot campaigns were tracked, primarily targeting Italian entities. Spam messages were constructed with a customized phishing kit, and redirected victims to Trickbot payloads.
January 2020
In late January 2020, we observed Coronavirus-themed Emotet spam campaigns, primarily targeting Japanese entities. Message templates for the spam runs were updated frequently (as is normal with Emotet). That being said, most messages masquerade as “urgent notifications which urge the victims to open malicious email attachments. The malicious attachments are disguised as updated information briefings on COVID-19 patients in their particular region.
Update (Friday, March 27th)
Covid themed campaigns have started to slow this week, while criminals were quick to capitalize on the news heavy topic of ‘Covid-19’ for their campaigns we suspect this slow down will continue due in part to the current situation where many countries, cities, and provinces have started to order “stay at home” or “shelter in place” orders. These orders could impact local governments and businesses in a way that will slow down a criminal’s ability to move money. We are still following to see what the effect will be on the underground economy as the global economy becomes more turbulent.
This is a concerning time for our industry and the public at large. We are in the midst of a global health crisis. In such times, we all need to be working together and ensuring that everyone has the most accurate and reliable data. We all want assurance that we can trust the resources available to us. Anything counter to that is destructive and potentially harmful to society. However, we all know that cybercriminals and sophisticated adversaries seize opportunities like this to further their own cause. This not only leads to the usual barrage of complications inherent to any cyber attack or event, but in this case it can translate to real harm to those we love and protect.
Domain Registration and Squatting
From the onset of the SARS-CoV-2 virus’s spread, opportunistic cyber-criminals have taken to proactively registering relevant domain names for malicious use. According to data from Recorded Future, “Beginning on January 12, the number of domain registrations started to increase, with an additional large spike on February 12”.
While domain registration alone is not proof of ill-intent, it is a reminder that we need to be extra cautious when interacting with “COVID” and “Coronavirus” related domains.
To provide some context, consider the following data:
Registered domains including “coronavirus” in the last 7 days = 5762
Registered domains including “covid” in the last 7 days = 6155
Registered domains including “covid-19” in the last 7 days = 934
Registered domains including “covid19” in the last 7 days = 3098
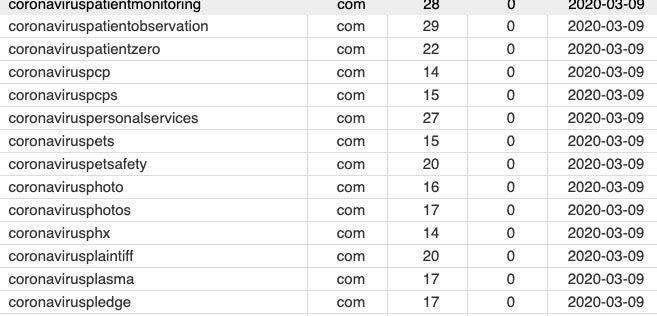
Src: DN Pedia
In the more scam-centric realm, registered domains including “coronacure” in the last 7 days = 934.
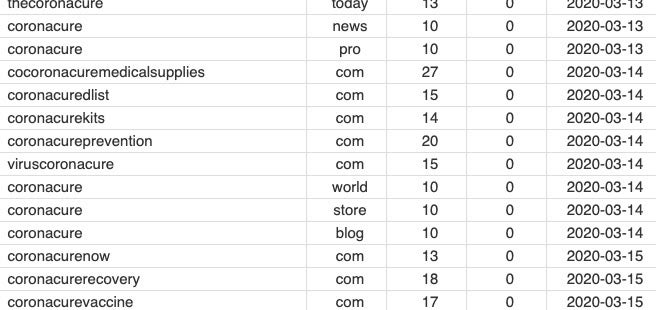
Src: DN Pedia
Some of these domains claim to offer medical supplies at exorbitant prices; would-be buyers pay up-front and take their chances as to whether they will ever see a delivery.
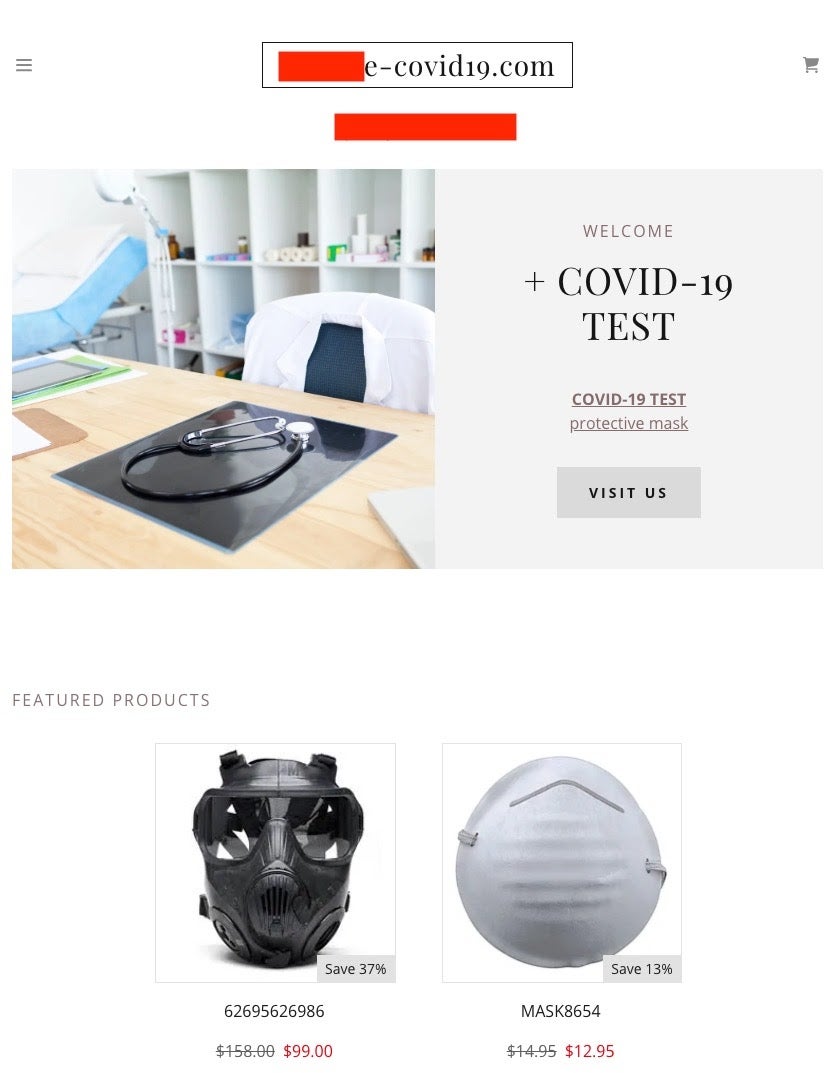
It is important to note that these numbers do not account for typo-squatting or subtly-varied names (homographic attacks), or numerical-replacement variants (aka ‘hackerese).
Emergence of Blatant Scams
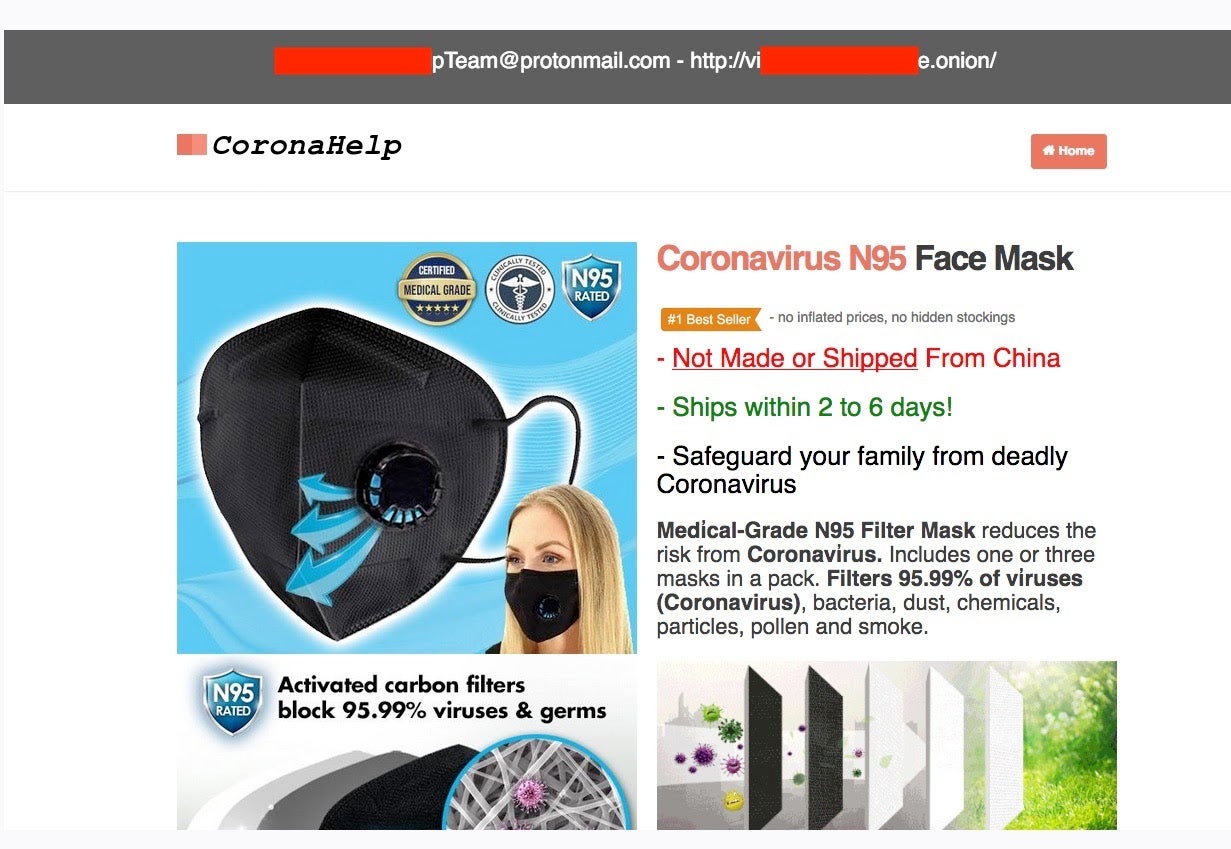
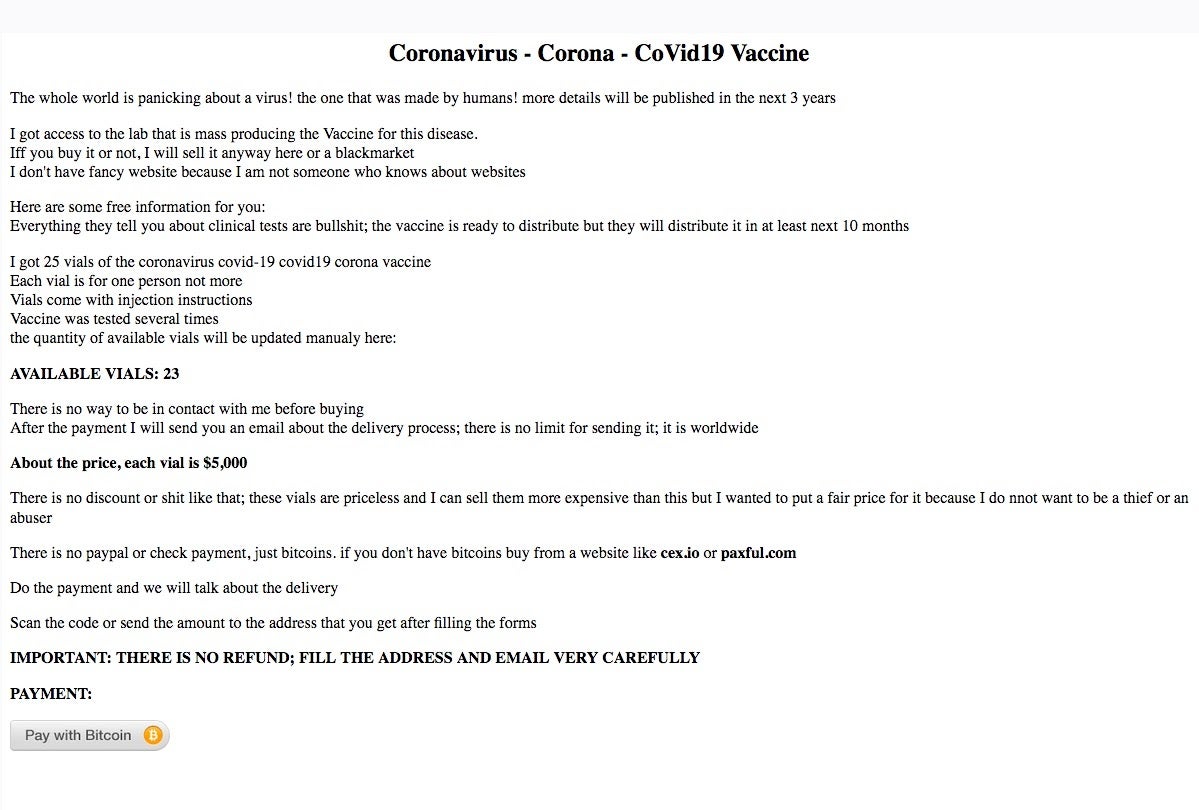
Multiple dark web (.onion) sites claim to sell COVID-19/Coronavirus supplies (masks, sanitization and cleaning supplies) directly for BTC (bitcoin). These are outright scams, which just collect BTC and deliver nothing to their victims. To add insult to injury, we have also seen sites reporting to sell non-existent vaccines, charging $5000.
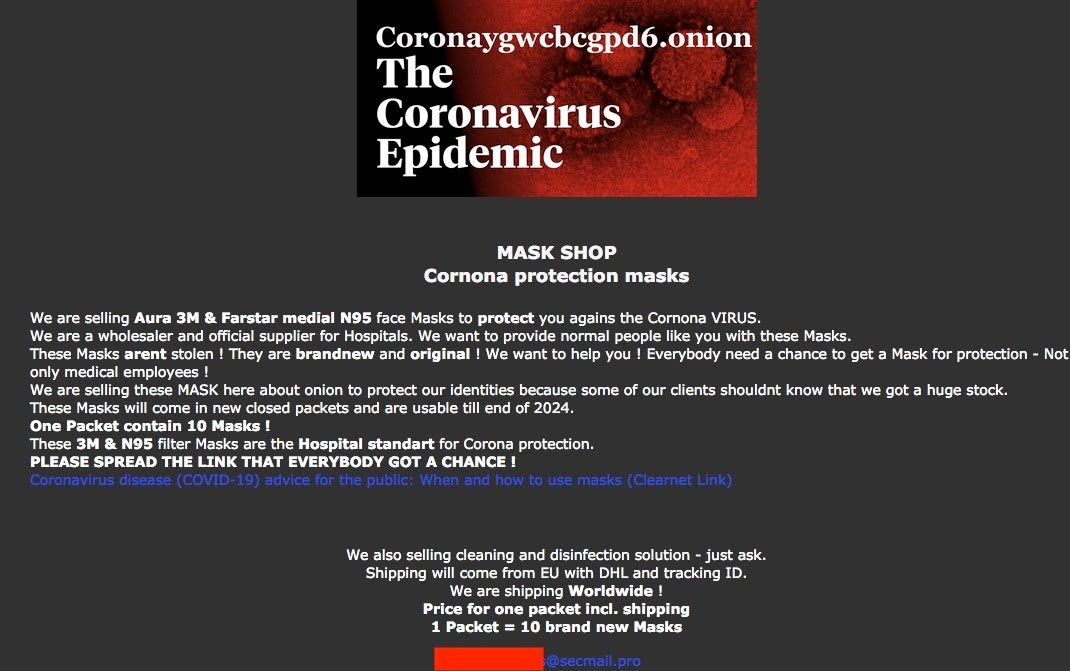
Scammy COVID-19 supply sellers
Infrastructure & Misinformation Attacks
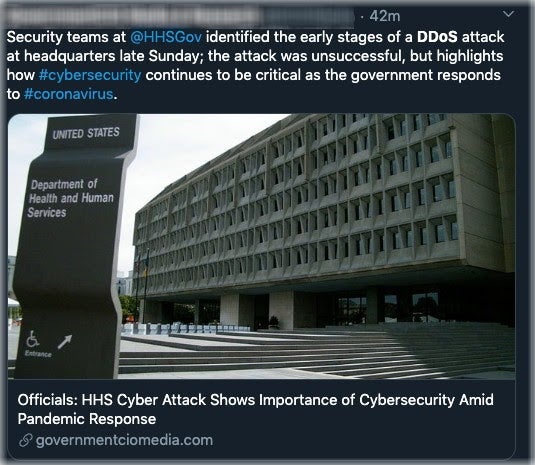
On Monday, March 16 an attempted DDoS attack was carried out against the US Health and Human Services Department. While the HHS infrastructure remained “fully operational” there was a perceived strain on the targeted systems given the increased activity. The attack comes at a critical time given the current influx of requests to their site (and services) seeking information and updates around protection against COVID-19. In this situation, the HHS was prepared. According to an HHS spokesman, “while preparing and responding to COVID-19, HHS put extra protections in place”.
In addition to the DDoS attempt on HHS, we have seen a flurry of social media campaigns specifically crafted to spread misinformation, and increase paranoia around the Coronavirus pandemic. There appear to be multiple, ongoing misinformation campaigns across all social media platforms (ex: Twitter, Facebook, Telegram).
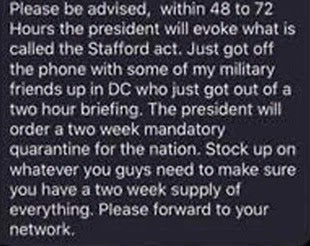
For this reason, we all need to be extra careful and ultra-discerning. The NSC has been quick to alert on and clarify most of these attempts, but again they are ongoing. It is recommended that the public continually monitor the NSC (and other official outlets) for accurate data and updates, as well as alerts on misinformation campaigns.
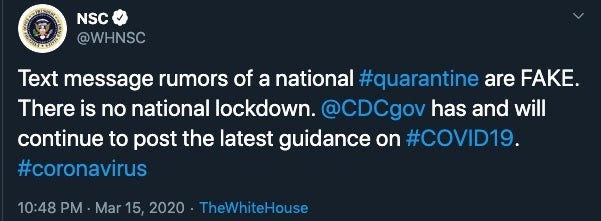
Supply & Lockdown Effects on the Criminal Element
Cyber criminals can be affected by the societal impacts of COVID-19 as well. Perhaps as a ‘positive’ side-effect, some underground vendors are having to cease operations due to increased risk or limited supplies.
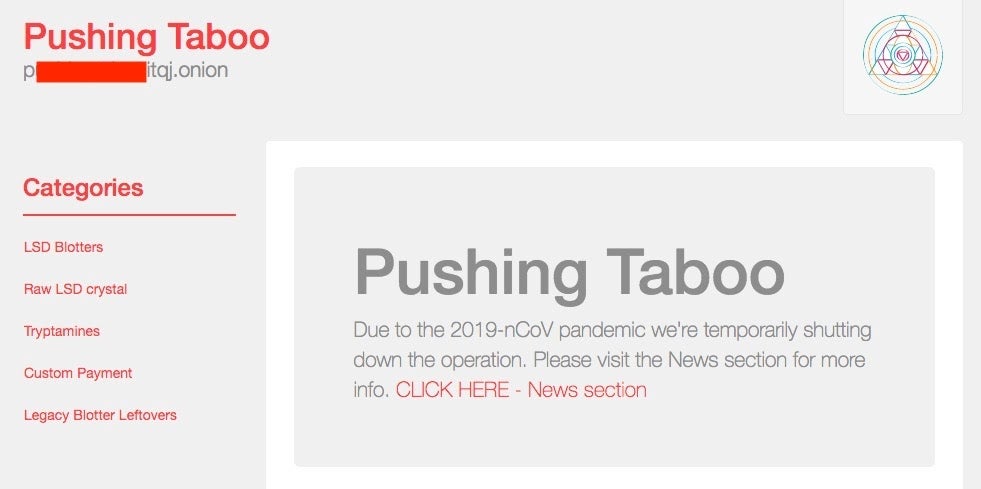
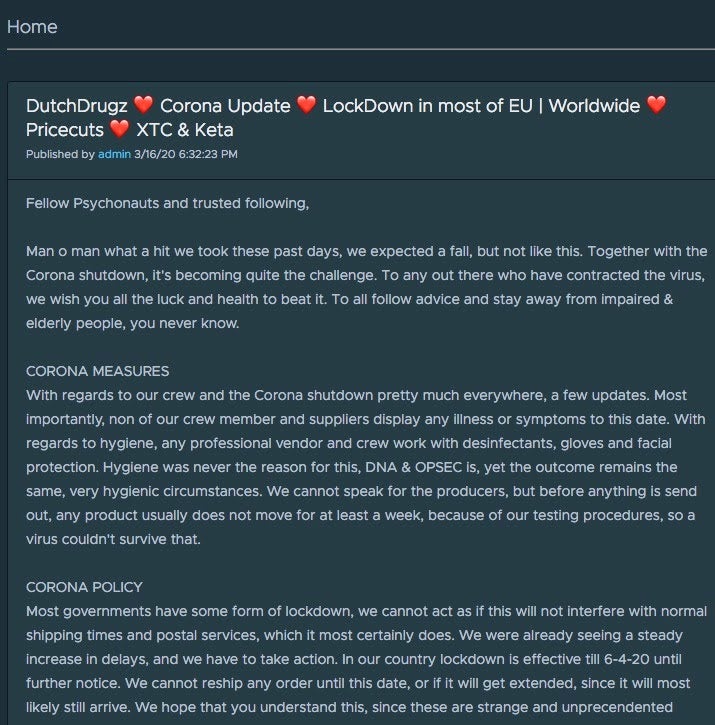
Conclusion
The psychology of fear, uncertainty, and doubt is a powerful weapon. Criminals have become more advanced in their understanding of manipulating human emotion to achieve a targeted action. Social engineering is based on the premise that I can get a victim to take action the victim believes to be trusted, but which is actually malicious, using manipulation, influence, and deceit. It can also be based on downright intimidation, authority, and extortion. The net result is a victim taking actions they otherwise never would have in the absence of social engineering.
Nation-state actors have long relied upon social engineering to achieve targeted goals for espionage, system compromise, election influence, and social media manipulation.
While this is still very much a ‘living’ situation, Sentinel Labs has already observed the ability for enterprising cybercriminals to capitalize on the fear and uncertainty of the general public. As is the case with any large and newsworthy event, our adversaries have no scruples when it comes to social engineering and malware distribution. Nothing is out of bounds, and the main difference with the current climate is that the stakes are much higher. It is enough of a challenge to get accurate data and information from known-and-reputable sources. The criminal element further muddies the water and makes our attempts to protect our loved ones (and selves) that much more of a challenge.
Resources
Sentinel Labs will be posting updates and details as they become available at https://www.sentinelone.com/labs/
This post draws out critical lessons we can learn from both cyber and biological threats:
In addition, the US-CERT/CISA has posted a list of additional resources which can assist in avoiding COVID-19-related scams and attacks. They cover cyber-hygiene recommendations and link additional helpful resources as well:
US-CERT: Defending Against COVID-19 Cyber Scams
CISA Insights: Risk Management for Novel Coronavirus (COVID-19) (Note: PDF)
CISA Alert (AA20-099A) – COVID-19 Exploited by Malicious Cyber Actors
FBI Alert I-032020-PSA – FBI SEES RISE IN FRAUD SCHEMES RELATED TO THE CORONAVIRUS (COVID-19) PANDEMIC
Indicators of Compromise
Zeus Sphinx DFF2E1A0B80C26D413E9D4F96031019CE4567607E0231A80D0EE0EB1FCF429FE Zeus Sphinx 3c115864cb93746b3745a119855b17442ef9415ccc2bf1531fc5a269e4714c66 Zeus Sphinx 511dab2388e7a98cc70a8e6abbfe3c47f170c9fc616941a2c05c08b1fc449ef1 Zeus Sphinx f40d11f983151b6f0405db63a3424e5063a7294f42bdbde07f7aed5fd96f4563 Zeus Sphinx c89c43d51eba1eb522cca6ec720f778a59638a09ea07ce10a60dd1929023a8d5 Zeus Sphinx 66fc5d683cf76c3c4b53199fc0796b7a13afba22fca8d97ef4dfd07249e5a9f1 Hawkeye 0b9e5849d3ad904d0a8532a886bd3630c4eec3a6faf0cc68658f5ee4a5e803be Hawkeye 82f9157507edd82634feb23213b70730701b274eb65c63e9dea6d7acef154d51 Nanocore 2cf2568dad46a638b8e4d86aa46f4cd279511dba9900286e22aeaefc39189a88 Emotet 4c9e35f3d5f555dda5f4373cf23fbb289c6067c70841be7022ba6da62e49cccb Emotet b49c9eba58537f8d856daded80bc9493a83c508d73423b98686d4e8b232d61c3 Emotet 7cbcad4d6e9ad8438e5febd3830bff9aef4729b98d23935ad7f9e6d290272732 Emotet acec0bb9d9bd199d3e6a77b763cebee8f67275996d3c55af8c617fef76f2e87f Emotet 109[.]236[.]109[.]159 Emotet 85[.]96[.]49[.]152 Emotet 186[.]10[.]98[.]177 Emotet erasmus-plius[.]tomasjs[.]com/ Emotet easytogets[.]com/ Emotet drhuzaifa[.]com Emotet dewarejeki[.]info Emotet dewakartu[.]info AZORult d2b231eb83de043acfcdf1c938c6b49e465d585fe4ce79f42add43a17aba1300 AZORult 2b35aa9c70ef66197abfb9bc409952897f9f70818633ab43da85b3825b256307 LokiBot 198[.]23[.]200[.]241 LokiBot 198[.]23[.]200[.]241 LokiBot 906EFF4AC2F5244A59CC5E318469F2894F8CED406F1E0E48E964F90D1FF9FD88 Grandoreiro 08710023c219f26237a9c8de5454a1de17117a2da651b4391afce8e331f31dfa Grandoreio 3bbd2beaa7953543e3cfb09d064db83b11034ff81255429b82e2de40d661ee29 Grandoreio 13[.]72[.]105[.]98 Generic Downloader/Dropper 9aea43b22f214228caf4fc714f426c0a140b7dd70b010bf3778cd1c0ec440851 NetWalker 9f9027b5db5c408ee43ef2a7c7dd1aecbdb244ef6b16d9aafb599e8c40368967 RedLine Stealer 0ddd7d646dfb1a2220c5b3827c8190f7ab8d7398bbc2c612a34846a0d38fb32b Ransom20 (COVID-Themed HiddenTear ransomware) 2779863a173ff975148cb3156ee593cb5719a0ab238ea7c9e0b0ca3b5a4a9326 Anubis dfb54d6c468271c73865d45e54b9dd942a18e716d608cf9233f1122cf79bab8c Anubis 1de6e6c140ff1b301b7df12d4b6388a21a6fbf0f141347dd2f9289740438a6d8 Anubis 5c4a0458c581c9bc0a7729b01926cd7b1f6b5b58aaecb2f31f571d4ded7ee419 Anubis 9ebc2996f2d08258d9119e01c9b00d1b8bf01b838c54dee9a675b28b9697e38f Anubis 0052751f0f11af674c479c2083c1f9f88a503b1189b7ebc095a38c4970b8a899 Anubis 60c957d19a81b795053b5d6e5b0372df0326c07b730718cba627f993261a6a5e Anubis bb27202091a065f3261e1625cbc7a0661a538b6e9aecfcb2069c71a680c61970 Cerberus 604b3cd50ef3b0df46bcb07a1d2d0fad31f517f4ef541036d9f0161d3c69499b Cerberus 93288d18a7b43661a17f96955abb281e61df450ba2e4c7840ce9fd0e17ab8f77 Cerberus c3096b341d6807a5a7d353f97554017a6242349b081837de60908081bcada1d0 Cerberus 2086af24ef1bd41939f4e2da8e1d17fbbd4de75d04143c758cbed133a8202d01 Cerberus de1ffdb17ac2f8d1b02972e11b2bff0a9a2cd27be4f20d44aece5227006eba8b Cerberus cfcc5ed7da99eee17c7d7179e0ee3b20f2df43126277c3c6670a1943e64e788e Cerberus 178b0878f1d485ecdb3626c8122424e818c92bab8101d2baf7be8eb0188ed5c7 Credential Harvesting intvmdt[.]us Credential Harvesting whintdm[.]us Ursnif 17c8d552a8ba063372f43b3a719eda76f6a3a2612e9a0bf329f26b4cc31579d5 Ursnif 4640edbda4a76f7baeeaad983afe8c742fa10becaa67b07e2c2effadc1711649 Ursnif e9697d963d66792a91991e64537707a94f466421615277d91675b83a408eef93 Ursnif e8ae0f7afaa6ce080567267759e7b9e02547b5174a9fce3f379792d499503c2f Ursnif a4bbf7654331415c4f7d0306066ececa014a27d706deca83bd7113ad4cd28d2e Ursnif f1[.]pipen[.]at Ursnif io[.]laurela[.]at Ursnif ya[.]aftnoop[.]at Remcos 28d692bdce30404b89c0d2c4758ee6f7f16a397ef51d0ddae4b3e2e4c1de4c0b e1d9ad1e0019d716ea5ef003880945bb356d24f0 Remcos 73734608e9413c807c8f09f793b55b77425b328052b5fa4ff82d66d6d4c15a34 251863798fa7ea99d20a4d2f15d246d6d09313e8 Anyplace 2196168d675e51bc9eba95a61b1d952a3587c9a7b33264c2ba11b070017cd2ae 3596db3dc83b20cb4ffcde2dfa7fa9ffc8fde38e Trickbot 1e6891472de82be04e4cf9177bdc68b59b22e72aaef1d6a4aa31892463902f09 c372f39c0592ac8e9249890f6327791eebc340f9 Tesla Keylogger c24de0d16850d2ef0aeb3b6b8efc21f66d11111702ba76c6cf5113bdb272a9c9 5c62c2d6a061cc4d6eaade8d2d73d1be39cca6f1 Lokibot f7b0d6d95f2644e32c22eb3e681e33387ac27d71dd73eee3ff37ce77985ab177 2073403dc04dd90140135e0cce1b504d5fcc6876 Agent Tesla 3e1fb4ff54112a78d8bdccbe596c119201f079010c4f69cdf2c99385e7aee3dc d2743385d48a823d8a464c1d6dd20216395a0a43 AZORult 15e029c3834435150c76741e714540fcb799662db8cc2c61ba4ef192a781727b 1b8aec9750e643ce27b82bbf1c2a78dedcbcc212 Exploit.CVE-2017-11882 47f1570e770d236836c0d3cb50755b6dd91e1be58a0d3e61507c7baacfd27784 1a431c3c0097063bba8df0a5fb66779dbd725998 Adwind 5b0ba8d58a64630cb5fcb80e72520bd2ef6f322003fa2588d4d594620e6685ae a45f057cbf44a70d010ea02e5417e06314b60a0a Bsymem 10afc9220fe1d9f53377f6b2b1ee9d6c06a027a84df1d462183691167a3f2a95 7357c38f8c1623e8f4bd2a12ff61825c2868fbe1 SLocker (Android) add9a29ee75b55ec8d6d7ee4f5119084edbeb3db04cbcce0af30c28758182296 785b89af9e4200ad1c3ae32033dc370210d20109 Formbook cfc573d1ea473dcb5bcfb0c3f869cc73f464dc3e697dca44d245c402803a5c90 4167996f71988539dc800a13a4667794e5c423ad Trickbot 875d0b66ab7252cf8fe6ab23e31926b43c1af6dfad6d196f311e64ed65e7c0ce cf2ab79310720800f707c18b45d54ea2a9959258 HimeraLoader 501ac08ebac646517b00d3234dfe58837b460bd5f045822d9fb5999f00979bfe 7fb3218b1ca76c379e08e7ce4942c2ead4c1e115 HimeraLoader b23724855af6b07ff6e34f1f834327cd8c000434a59da1af506afeb815642f4c 2d36864683aa5cf83ac4a4edd017aa098dd44af7 CoViper (MBRLocker) 8777fd250623c8a7211bc9d28b00c593149795739eedde531728fb34bcf0ee4f 1da8de8b5f6dcbe258a4d962faaeed1886a3da6c NodeAgent 5210afa4567b98fb3f8aee513206b5fd466d3afe01dd576a2bee4a623f2cdae2 ccd1312f6a444492301674d7cf2a45995dd86e0b SpyAgent (Android) bb1b70b7f6d8fc18e5a5fd743242836475bc6ad978780adec18a8f92c7e9cf89 63152ae5ea7408e8d6998c84b105e7cf703b1670 SpyAgent (Android) adf46dc686d35a659a3cff76648c9c036dfc95167b9f4dcb7409dc79d92eb510 58cfeec8493417a1f0e6157a3328d10b0467342f Fuckunicorn (Ransomware) 7980ef30b9bed26a9823d3dd5746cdefe5d01de2b2eb2c5e17dbfd1fd52f62bf 110301b5f4eced3c0d6712f023d3e0212515bf99 CVE-2017-11882 Exploit (Word Document) 904e966da7b38514f6ac23bba1dac1858888cd48fa77b73c770156b19a88a4c8 2c6ecbfb674168a7015cf060007447a80823a567 Warzone RAT 67cacba2f313fd69b51eb0bc495ee79ce7f2706f068cb35a5419edc03c97449b 8fed92c2cf9e089458d944b1b549d46200cdf5e0 IcedID ee9fd78107cdcaffc274cf2484d6c74c56c7f3be39b1896894d9525506118d1e 5b8740836144163c4de591ff1dfe7c92f116c5e0 IcedID 822a8e3dfa14cd7aaac749dc0515c35cf20632717e191568ba5daf137db7ec17 06f6de4f48dbd69d8f8dd5ff1a33a8eeffc94bad IcedID (.PNG) d40566808aead4fecec53813d38df4fbe26958281a529baf5b6689f0163d613f d1a08faa1b8b84283acf7594a82fb2d71ce6e455 IcedID c35dd2a034376c5f0f22f0e708dc773af8ee5baf83e2a4749f6f9d374338cd8e 81091df7da53160dacacf25bb4b97eb95cad2970 NetSupport RAT 1ff9615577cc6cd702d847672a34260a72ba5a71f4b7dd5ebfd844d4835c68a7 6b00e4c85ab9c2a0a724fc77177d5b55ff4369e5be068605a29fffe7173919f9 NetSupport RAT c40a712cf1eec59efac42daada5d79c7c3a1e8ed5fbb9315bfb26b58c79bb7a2 f5f523afd0ec76f4721a91d30a014bc400cb60b5 NetSupport RAT 4ac785bd8812439fa694a6333e7fe0b99a984411baedb383178a732f04076d3e 1331a440998746a4be091adb28f8405f5dbb2e85 NetSupport RAT 3f07ca87744046610dc98ef317a7e8082bd08e288dd41e3818be1c140744664c 572f66155c91c1a33af4507a1dadafbb66eccf07 NetSupport RAT 4989e1ec9fb3dcff504e3ef297a0019abc3717e1961fec33cffc4f6fb5fec87a 16b9ef9db123751f52e4acc2e613c25079fa1131 SpyNote / CovidSpy (Android) 1d94952245f517602227938a26c498006143d7b8a92dd259f595715255b99ade 6ffe03aad1b06238e9692aa90f6bdc5dbb6a1024 SpyNote / CovidSpy (Android) 885d07d1532dcce08ae8e0751793ec30ed0152eee3c1321e2d051b2f0e3fa3d7 c2a9a3521bf390c3fbf56d3cbf584d30dba69aa9 SpyNote / CovidSpy (Android) 41bb86666543349bbf82e157b4d69a893f9b9c0fd37a8dce59048d8e000af3d6 08733be27096c75c2e2d1b91618944a8bb96ec06 SpyNote / CovidSpy (Android) add9a29ee75b55ec8d6d7ee4f5119084edbeb3db04cbcce0af30c28758182296 785b89af9e4200ad1c3ae32033dc370210d20109 ZLoader (maldoc) 436b0c94c1be2be6b328830568ef7f031b45bf6d2377fa9f4b1f872ffb39b369 30199408f1098b595ce6744b7fd17cbc833a2841 Agent Tesla a27086b4b0a6674bb085ae428270bf1ee5cfcd7c4a3b66eac7e2869fafee7899 42702a6c77fc215146f97d531f3055d81ff77b92 CryCryptor (Android) d77077500b768415215f4b76f686f1cbfe74bd5ef6bc990ac2c75cc599685337 59818b0c6c85859b8e43f5beda24c3cb1c4e186f CryCryptor (Android) faa0efaad40e78bf27ca529171aaf0551db998a276d4ff501209d1f5ef830dfb 322aab72228b1a9c179696e600c1af335b376655 CryCryptor (Android) f3a7fec9ab690ccd33c75345f0313bc3c6850c9c69c63d928dba8e3b3ce43473 5d74684f80d6b3d410997b850d7a92db8646aa07 CryCryptor (Android) 0bc5016520780a16ec1ee5fd5116111ab68897d541967addb0fc09422f231d1f b35800768c9efe0e3212f50ad2ffc870f71c339c CryCryptor (Android) 0bc5016520780a16ec1ee5fd5116111ab68897d541967addb0fc09422f231d1f b35800768c9efe0e3212f50ad2ffc870f71c339c Agent Tesla b419849ce915ede72fda1ea0b566651e233ef5eaffbf8b9211bd44085407ad5e 846da85a2f2e6e79ebc7ed84b00ed97af513c80f Sepulcher Trojan e89614e3b0430d706bef2d1f13b30b43e5c53db9a477e2ff60ef5464e1e9add4 e47a821ef85d722f01f10adff227f45552e4ec73




