The Good | Feds Dismantle Major GenAI-Based Bot Farm Spreading Pro-Russian DisInformation Campaigns
In a joint international operation led by the FBI, law enforcement have seized two domain names and nearly a thousand social media accounts all controlled by a large bot farm dedicated to spreading Russian propaganda. Under the management of a Russian FSB officer and a deputy editor-in-chief at news organization Russia Today (RT), the bots have spread disinformation campaigns globally through a generative AI-based software called Meliorator since 2022. Based on the FBI’s findings, RT leadership have been focused on expanding their information dissemination beyond traditional television.
Meliorator allowed the bot farm operators to create highly convincing X (formerly Twitter) profiles and personas designed to amplify Russian foreign interest as well as false narratives in order to sway public opinion and fuel discord online. As of June 2024, the functionality of the generative AI software was limited to X, but the FBI are predicting its expansion into other social networks with time. Use of Meliorator has been seen across Germany, Israel, the Netherlands, Poland, Spain, Ukraine, and the United States.
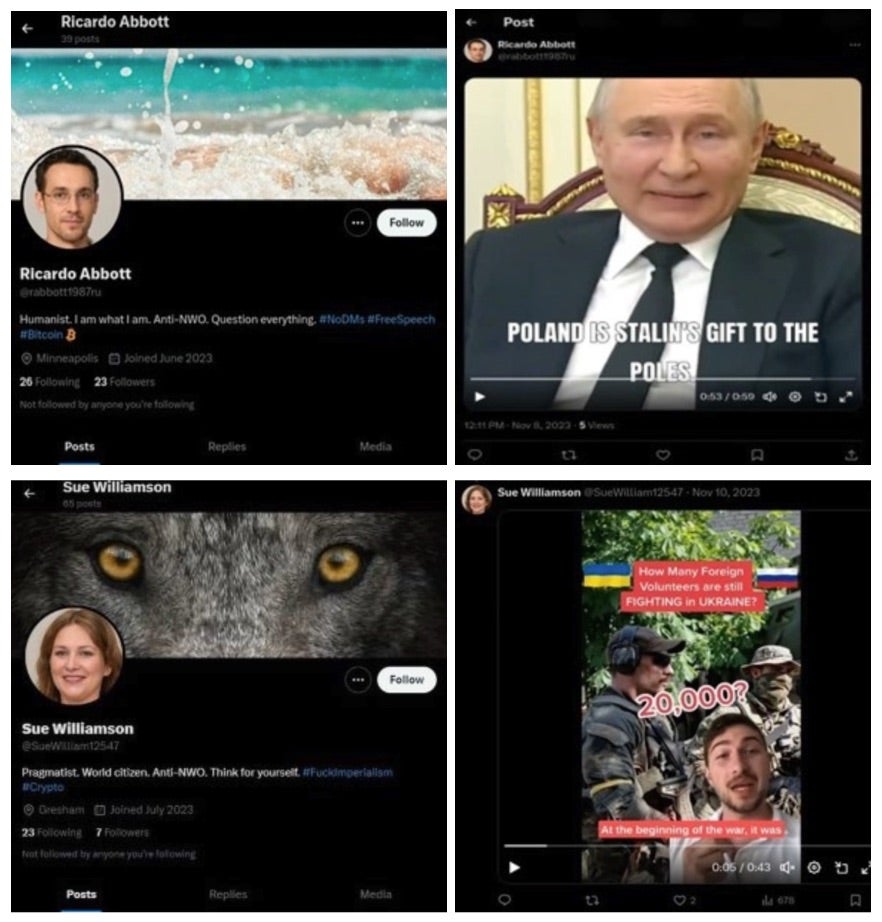
As part of the joint operation, the two domains mlrtr[.]com and otanmail[.]com used to register the bots were seized alongside 968 X accounts directly linked to RT’s bot farm. This is a first major action in disrupting Russian state-sponsored social media bot farms. A joint advisory between all involved global law enforcement agencies provides a technical breakdown of the Meliorator software, recommended mitigation measures, and a list of resources on combating malign influence and disinformation campaigns. X has since suspended the remaining bot accounts listed in court documents for violating the platform’s terms of service.
The Bad | Scammers Leverage Over 700 Domains to Sell Fake Tickets to Olympic Events
As anticipation for the Olympics mounts, threat actors are ramping up their large-scale fraud campaigns designed to target hopeful buyers seeking tickets to the Paris Summer games. Security researchers tracking the activity have dubbed the campaign ‘Ticket Heist’ where threat actors offer fake tickets to Olympic events and other major sports games, concerts, and music festivals.
Researchers found that the threat actor began registering domains in 2022, averaging 20 new registrations each month since. With online hype surrounding the Olympic games and discussion about the International Olympic Committee’s ban on Russian and Belarusian athletes rising, analysts tuned in to monitor increasingly suspicious activities. They uncovered 708 domains hosting convincing websites all selling fake tickets and accommodation options for the summer games.
These fraudulent sites offer inflated ticket prices to create a perception of VIP treatment or to generate interest through a scalping operation. When researchers attempted a purchase, finding transactions processed through Stripe and funds transferred only if the card had sufficient funds, pointing to the goal of stealing money rather than collecting credit card information. Further, 98% of these domains were found to be malware-free, indicating the threat actor’s aim to steal directly from victims via legitimate payment services.
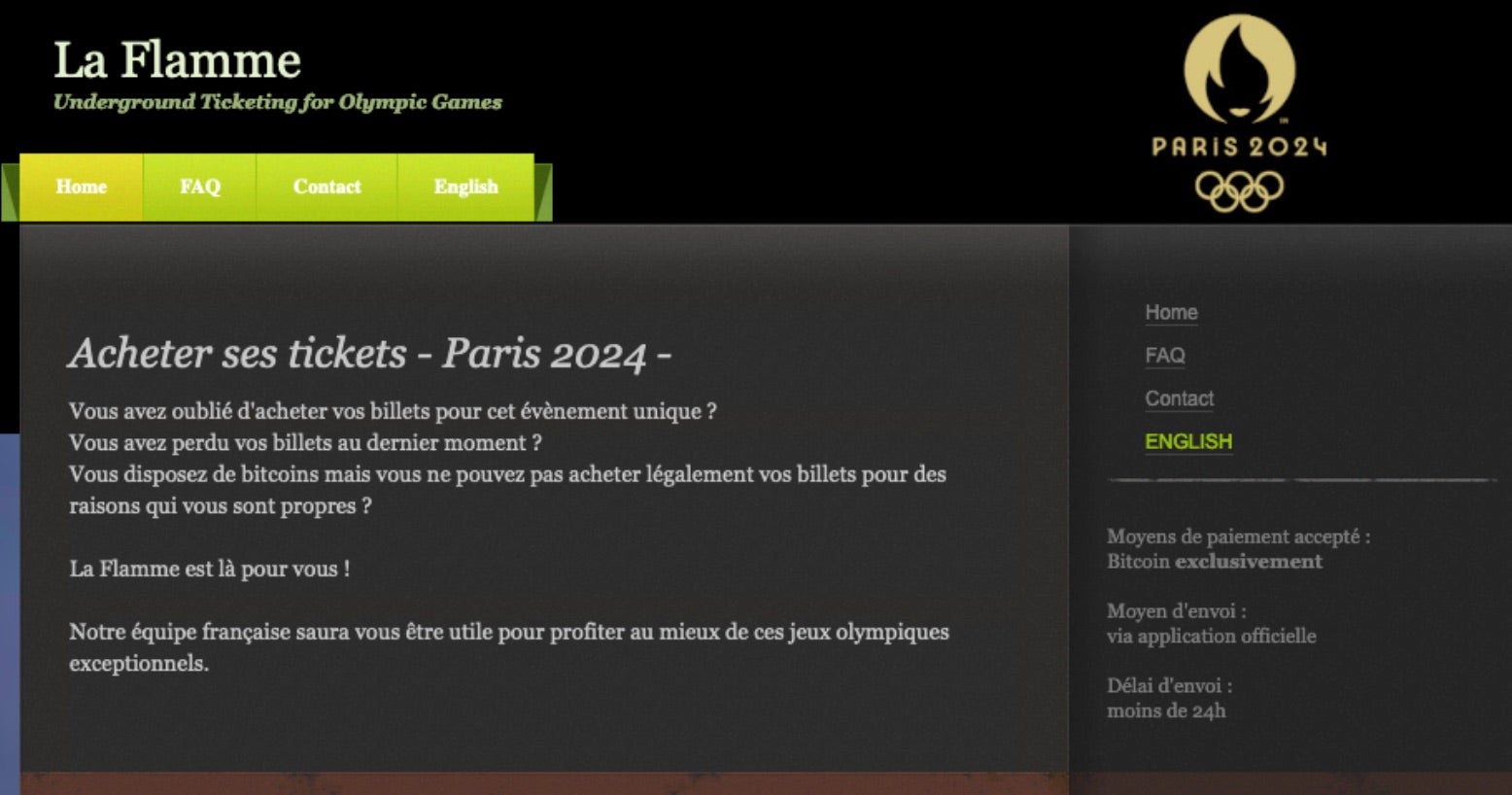
All domains were hosted at IP address 179[.]43[.]166[.]54, which is notably associated with malicious activities. Despite each site having unique SSL certificates, the recurring domain structures and subdomain names revealed an interconnected network. The Ticket Heist operation is ongoing and security experts warn buyers that a variety of fraudsters are operating similar scams online, capitalizing on the weeks leading up to this year’s Olympics. Indicators of compromise (IoCs) can be located here.
The Ugly | Critical-Level Vulnerability Allows Unauthorized Pipeline Jobs In GitLab CE/EE
GitLab is warning customers to patch a critical-level vulnerability that could allow attackers to run pipeline jobs as other users in all its Community Edition (CE) and Enterprise Edition (EE) versions from 15.8 to 16.11.6, 17.0 to 17.0.4, and 17.1 to 17.1.2. Tracked as CVE-2024-6385 and scoring a 9.6 out of 10 on the CVSS scale, this flaw enables an attacker to trigger a pipeline as an arbitrary user under the specific circumstances.

GitLab pipelines are a feature of the company’s Continuous Integration (CI) and Continuous Deployment (CD) system designed to automate the process of building, testing, and deploying code. Like any CI/CD processes, pipelines are commonly targeted by threat actors based on how they are configured, managed, and utilized.
If permissions are not properly configured, unauthorized users can gain access to run or modify pipelines. Sensitive information like tokens, API keys, and passwords are often stored as environment variables that can be exposed if not properly masked or secured. CI/CD pipelines can also play a significant role in software supply chain attacks due to their central position in the software development and deployment process.
The released patch for CVE-2024-6385 follows hard on the heels of another almost identical flaw in GitLab tracked as CVE-2024-5655. This flaw, patched in late June, could also be exploited by attacks to run pipelines as other legitimate users. These two extremely similar and back-to-back flaws highlight how important it is to properly secure CI/CD environments in order to minimize the risk of supply chain attacks, data breaches, or denial of service incidents.


