Last week, we highlighted NIST’s recently released standards for post-quantum cryptography and provided recommendations for organizations on quantum resilience.
This week, we draw attention to the threat of North Korean IT workers infiltrating global firms and offer tips to understand and mitigate the risk.
Please subscribe to read future issues — and forward this newsletter to interested colleagues.
Contact us directly with any comments or questions: [email protected]

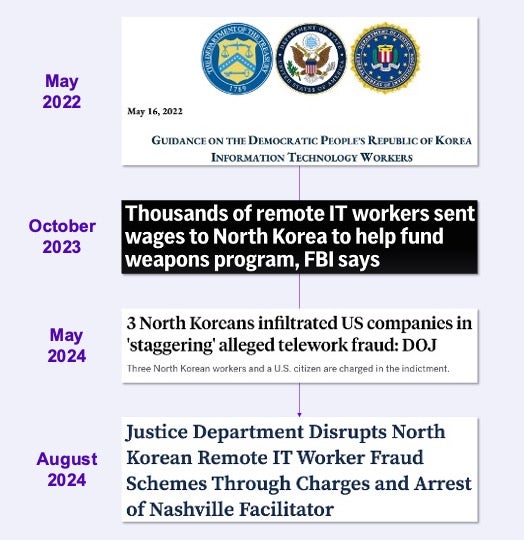
North Korean IT workers are covertly infiltrating U.S. companies through fraudulent employment practices, generating revenue for the DPRK’s regime while bypassing sanctions and security measures. These workers exploit vulnerabilities in hiring processes and use U.S.-based individuals to disguise their identities, posing significant risks to corporate networks and national security. The threat is real and growing, as evidenced by recent law enforcement actions.
On August 8, 2024, the Justice Department disrupted a North Korean IT worker fraud scheme, leading to the arrest of Matthew Isaac Knoot in Nashville, Tennessee. Knoot was instrumental in helping North Korean IT workers secure employment under false identities. He facilitated their access to U.S. company networks by hosting company laptops at his residence and installing unauthorized software, which allowed the workers to operate remotely from abroad. The payments for these services, which were laundered through various channels, ultimately supported North Korea’s illicit weapons programs.
This case is just one example of a broader pattern identified by the FBI and other agencies, where North Korean workers earn up to $300,000 annually, collectively generating millions of dollars for the DPRK’s weapons programs.
Case Study – KnowBe4 Infiltration
The seriousness of this threat was highlighted in July 2024, when KnowBe4, a leading security awareness training firm, discovered that they had unknowingly hired a North Korean IT worker. Despite following standard hiring procedures, including background checks and reference verifications, this individual infiltrated the company. Upon receiving a company-issued Mac workstation, the worker immediately attempted to load malware onto the system.
The subsequent investigation revealed significant gaps in the hiring process, such as inadequate background checks, poor vetting of references, and weak access controls. This incident underscores the need for companies to implement stronger security measures to protect against such threats.

DPRK IT Worker Tactics
North Korean IT workers employ a range of sophisticated tactics to infiltrate organizations. These include:
- Identity Theft and Impersonation: North Korean actors use stolen U.S. identities and AI-enhanced photos to pass background checks. In the Knoot case, workers used a U.S. address to receive company laptops, which were then accessed remotely from abroad.
- Social Engineering: These workers are adept at conducting convincing video interviews under false identities and using VPNs to mask their true locations, making it appear as though they are working domestically when they are actually operating from North Korea or neighboring countries.
- Malware Deployment: Once inside a company, they may attempt to install malware or facilitate access for other malicious actors, significantly compromising corporate networks.
- Evasion Techniques: To avoid detection, they use pseudonymous accounts, proxy computers, and false websites, which complicates efforts to track their activities.
Red Flag Indicators
To protect against these threats, companies must be vigilant during the hiring process and beyond. Key warning signs include:
- Identity Inconsistencies: Discrepancies between a candidate’s online profiles and their resume, use of multiple conflicting profiles, or frequent changes in contact information.
- Interview Behaviors: Reluctance to appear on camera, inconsistencies in appearance or background during video calls, and signs of cheating during technical assessments.
- Resume Discrepancies: A pattern of education from Asian universities combined with employment records that predominantly feature U.S.-based positions, and addresses linked to freight forwarding services.
- Financial Anomalies: Requests for prepayment, frequent changes in payment methods, or aggressive behavior when such requests are denied.
Mitigations
Given the sophisticated nature of these threats, companies must take proactive steps to safeguard their operations:
- Enhanced Background Checks: Thoroughly vet all candidates, including international database searches, and verify references using trusted sources.
- Identity Verification: Require notarized proof of identity and validate it during live video calls. Train interviewers to detect signs of document tampering and other red flags.
- Financial Verification: Implement robust systems to verify financial documents and detect potential money laundering activities.
- Recruitment and Onboarding: Vet job platforms carefully, maintain detailed records of all hiring interactions, and ensure that company devices are shipped only to verified addresses.
- Monitoring and Access Control: Deploy insider threat monitoring systems, enforce geolocation checks, and adopt a Zero Trust security model to limit access to sensitive information.
- Device and Network Security: Disable remote desktop protocols for new hires and enforce a least-privilege model, ensuring regular audits of user permissions.
Key Takeaway
The case of Matthew Isaac Knoot and the broader issue of North Korean IT worker infiltration illustrate the critical importance of vigilance in today’s globalized workforce. The financial, operational, and reputational risks posed by such infiltrations are significant, and the consequences can be dire—not only for individual companies but for national security as well.
By implementing stringent hiring practices, robust identity and financial verification processes, and comprehensive monitoring and security measures, companies can protect themselves from becoming unwitting accomplices in the DPRK’s illicit activities.


