The Good | U.S. Officials Crackdown on Russian State-Backed Disinformation Campaigns Ahead of Presidential Elections
Amid ongoing concerns about U.S. election interference, the DoJ seized 32 domains this week used by Russian-linked threat actor, Doppelgänger, to spread disinformation campaigns. The campaigns aimed to influence the upcoming U.S. elections and sway international support for Ukraine. Officials explain that Doppelgänger worked to spread their propaganda by mimicking legitimate media sites through a technique called “cybersquatting”. Threat actors register domain names that are very similar or even identical to popular brands with the intent of hijacking traffic and profiting off the trademarks. In Doppelgänger’s case, the domains were used to disperse its AI-generated content promoting pro-Russian narratives, banking on legitimate sites media brands such as Fox News, the Washington Post, and more.
Yesterday, @TheJusticeDept seized 32 websites linked to the Russian influence operation (IO) network #Doppelganger. @USTreasury added to the SDN list individuals and entities involved in Russia-aligned IOs, including Doppelgänger.
🧵A few thoughtshttps://t.co/VSxA7GSoNg
— Aleksandar Milenkoski (@milenkowski) September 5, 2024
Alongside the domain seizures, the DoJ also indicted two Russian nationals, Konstantin Kalashnikov and Elena Mikhaylovna Afanasyeva, for funneling almost $10 million to disseminate thousands of propaganda videos through a Tennessee-based digital content creation company. The videos saw millions of hits on YouTube while targeting U.S. social issues such as immigration and inflation rates. Kalashnikov and Afanasyeva’s operation also involved a network of social media influencers and paid ads, all with the shared goal of manipulating voters while hiding its Russian ties.
The U.S. Department of the Treasury further sanctioned 10 individuals and two entities, including high-level executives from Russia Today (Russia’s state-funded news outlet), for their roles in covertly recruiting American influencers to help spread disinformation. All of these actions flow into a broader strategic effort by U.S. law enforcement to combat rising foreign influence ahead of the 2024 U.S. presidential elections.
The Bad | Critical-Level Remote Code Execution Flaw Found in Veeam’s Backup & Replication Software
Popular business data protection company, Veeam, has released security updates for 18 high and critical-rated vulnerabilities that affect a number of its products, including Veeam Backup & Replication (VBR), Veeam ONE, and Veeam Service Provider Console.
The most severe of these vulnerabilities is tracked as CVE-2024-70411 (CVSS v3.1 score: 9.8) and described as one that could allow remote code execution (RCE) in VBR without user authentication, which can lead to complete system takeovers. Used to manage enterprise-level backup and recovery infrastructures for virtual, physical, NAS, and cloud-native environments, VBR is considered a high-value target for ransomware operators looking to steal or encrypt backups. With no viable backups available for business critical data like applications and databases, victims are left without recovery options making them even more vulnerable to double extortion ransom requests.

CVE-2024-70411 affects VBR version 12.1.2.172 and earlier versions of the 12 branch. Users are strongly advised to update to VBR version 12.2.0.334 to mitigate potential risks. To address the other 17 vulnerabilities, users are warned to upgrade immediately to Veeam ONE version 12.2.0.4093 and Veeam Service Provider Console version 8.1.0.21377.
Ransomware gangs like Cuba, FIN7 – all associated with the likes of BlackBasta, Conti, Maze, and REvil – have been observed zeroing in on VBR-based vulnerabilities in past attacks. Given the critical role products like Veeam VBR play in data protection, prioritizing patching is essential to keeping enterprise systems safe from ransomware actors on the lookout for low-hanging ‘fruits’ that give access via unauthorized RCE.
The Ugly | Crypto Firms Targeted by North Korean Actors Exploiting Chromium Zero-Day
Combining social engineering tactics, a zero-day vulnerability in Google’s Chromium browser, and the FudModule rootkit, DPRK-backed threat actors are targeting cryptocurrency firms to gain kernel-level access and steal crypto. Security researchers tracking these attacks attribute the ongoing exploitation to North Korean group ‘Citrine Sleet’, also known as UNC4736, AppleJeus, and Labyrinth Chollima. The threat actor is known for its attacks on financial institutions, particularly those in the cryptocurrency sector. In the past, they have been observed using fake crypto trading platforms to infect their victims with malware disguised as job applications or trading apps.
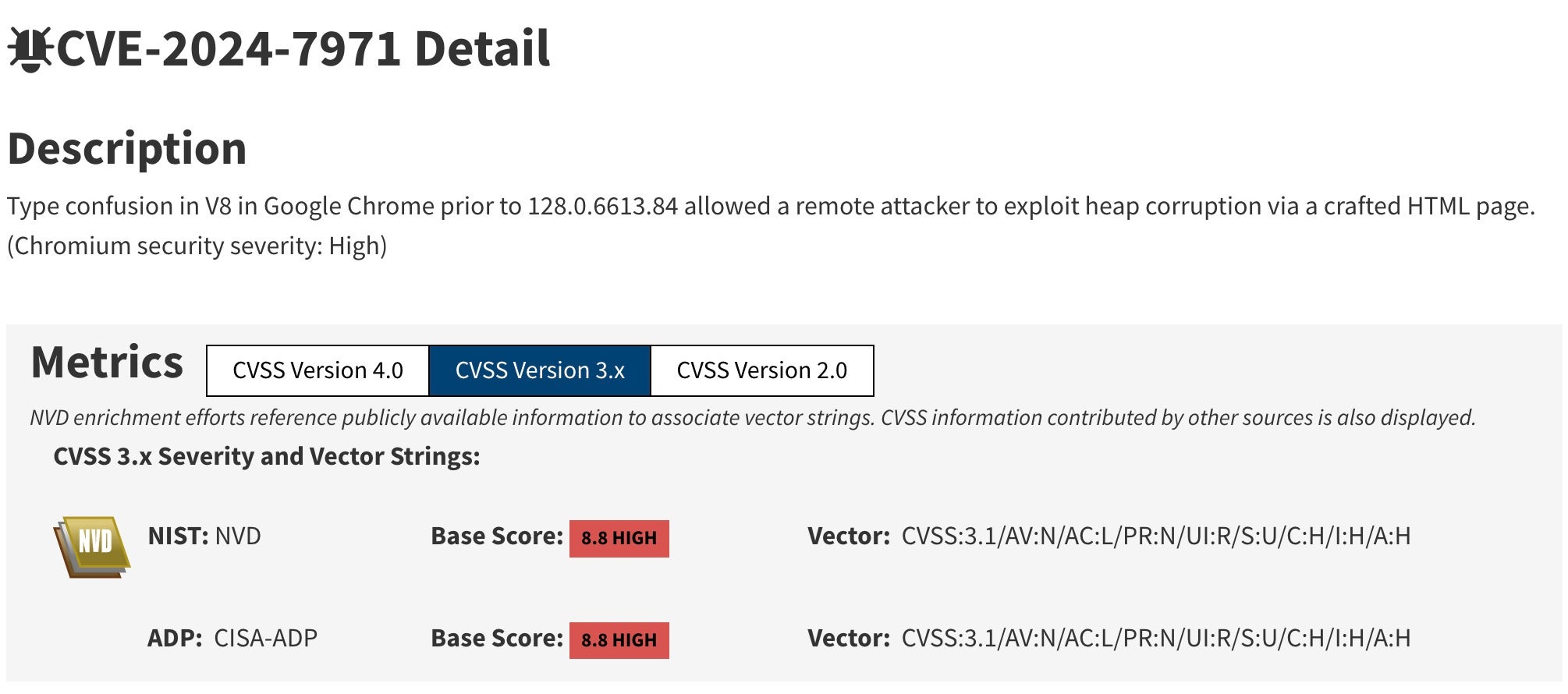
Specifically, the CVE-2024-7971 vulnerability is a type confusion flaw in Chrome’s V8 JavaScript engine that could allow remote attackers to exploit heap corruption via a crafted HTML page. Though patched just in late August, Citrine Sleet attackers exploited the flaw to gain remote code execution (RCE) in Chromium browser’s sandboxed environment before downloading a Windows Kernel exploit for system privileges. After, the threat actors loaded the FudModule rootkit, which enabled kernel tampering, direct kernel object manipulation (DKOM), and a bypass of kernel security mechanisms. These actions all provide the actors with persistent backdoor access to compromised systems, allowing them to steal data or deploy more malware later on.
The FudModule rootkit has made its rounds within other North Korean threat groups since its discovery in October 2022, shedding light on how these state-backed actors continue to share malicious tools and attack infrastructure. In addition to expediting the patching process for critical-level and RCE vulnerabilities, organizations can work with security vendors that provide full and real-time visibility across all their attack surfaces with a focus on detection and detainment of malicious activity.


