Your friend texts you at midnight saying he/she needs you to fill up a form on priority. You do that.
The minute you enter your details, the next day you never hear from them again. Later, you find out your account got hacked and you can’t log in. The sender of that message wasn’t your friend that night, they just posed as your friend and you never suspected it. Such is the case of many smishing attacks. These messages are disguised cleverly, often seeming too innocent.
Phishing uses the same tactic except over email, forums, or web. The attacker convinces the recipient to click on malicious links and attempts to bait them. These emails appear too legitimate but they don’t come from recognized sources.
Fortunately, we will tell you how to avoid falling for their tactics. In this guide, let’s demystify everything you need to learn about smishing vs phishing and explore additional details.
 What is Smishing?
What is Smishing?
Spam calls and text messages have increased over the years. Perpetrators use malicious links to compromise victims, lure out users, and attempt to make them leak sensitive information. Texts are instantaneous and users who are genuinely busy forget to verify the recipients’ identities or check their message trails, thus falling for their tricks within mere seconds. Hackers can impersonate officials or legal entities to make their messages appear legitimate and compromise the victims’ identities as a result. They may use local numbers to send genuine text messages and victims won’t suspect them. Some hackers even send smishing messages from unknown numbers and more than 1 billion unwanted messages are sent every minute!
How Smishing Works?
Smishing is SMS phishing and this is how it works. Imagine you receive a message saying you need to reset the password of your PayPal account soon. Or you are locked out of your account and need to verify your identity. You receive a text asking you to click on a link to resolve the issue, further saying that you need to follow the instructions in the message.
Most mobile users aren’t aware of how phishing works because they cannot determine the authenticity of these messages.
Smishing can cause millions of dollars in data losses. According to the FBI’s cybercrime complaint division, over 2,800 cases of smishing were recorded in 2023 alone that led up to USD 3 million in losses. A McAfee study shows that 1 in 4 Americans become a victim of tax scams. If you have ever received text messages asking to key in a code for multi-factor authentication unexpectedly without you issuing the request, chances are, that’s smishing!
SMS messages have a much higher rate of opening than emails and other forms of online communication. This makes them an attractive target for scammers and cybercriminals.
What is Phishing?
Phishing is a type of cyber attack where the attacker sends an email and masquerades as an official entity in it. He may emotionally manipulate the victim, instill a sense of urgency, or psychologically gaslight them into giving out sensitive information. What’s scary about phishing is that sometimes victims cannot detect these fake emails and assume they are genuine. They may be enticed into performing actions such as downloading malicious links, responding to fraudulent requests, or sharing confidential information.
How Phishing Works?
The classic phishing scheme sends mass emails to groups or organizations. Spear phishing is more targeted where the attacker will aim for specific entities within the company. For example, the executive of a company can be impersonated. The cybercriminal may pose as them and attempt to contact employees. New employees who are unaware often fall for these emails and they end up interacting with the cyber criminal without knowing or ascertaining their true identity.
Phishing tactics evolve over time which means that the attacker can bypass traditional email filters and security measures. They can maneuver their way out of critical security scanners, hack into the organization, escalate privileges, and cause data breaches. And all it takes is a simple email. Some emails may also include voice notes or ask the victim to engage with them over voice notes or live stream links. Cybercriminals can use AI deep fakes and take their impersonation tactics to the next level that way.
Here is an example of a phishing email:
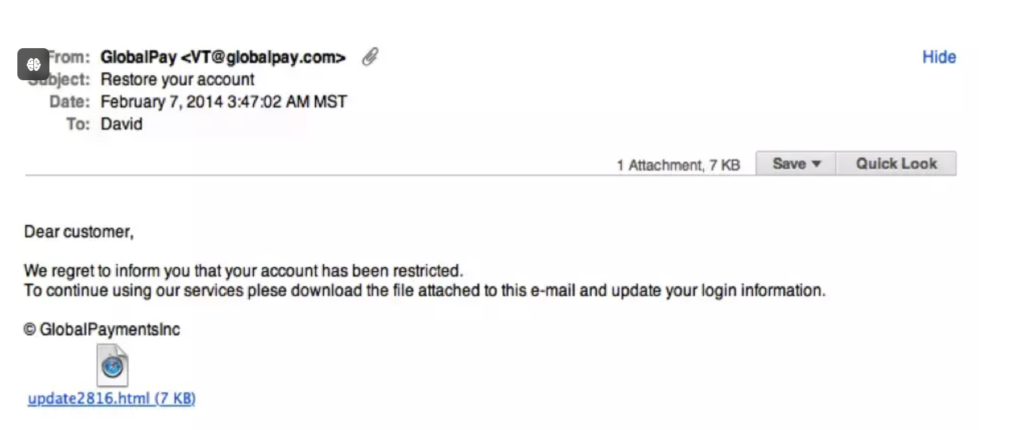 As you can see in the above email, the real name of the attacker was not disclosed. The email appears to be from an official organization or resembles similar counterparts. An attacker posing as a representative of Paypal may use the domain Paypal.org instead of Paypal.com
As you can see in the above email, the real name of the attacker was not disclosed. The email appears to be from an official organization or resembles similar counterparts. An attacker posing as a representative of Paypal may use the domain Paypal.org instead of Paypal.com
The domains look so similar that victims or individuals opening these emails often forget that they’re not the official website or source. The attachment included in this email can be a malicious script. If the recipient downloads and runs it, the executable code can install malware or spyware into their system.
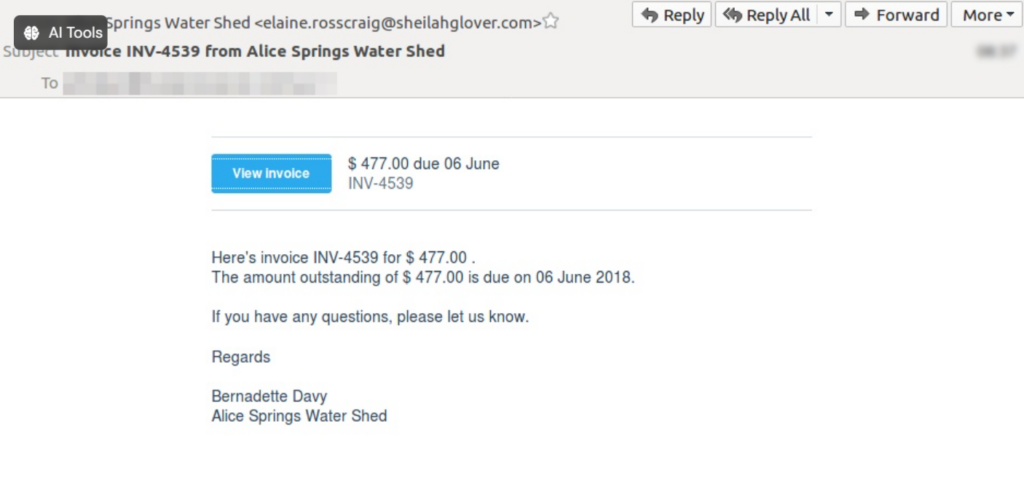
For B2B businesses, cybercriminals can send invoices and ask to clear pending payments to organizations.
Here is another example of that:
 3 Critical Differences Between Smishing and Phishing
3 Critical Differences Between Smishing and Phishing
There’s a difference between phishing and smishing. One uses phone messaging and the other uses email communication channels to target users. Both operate on the same mindset: jolt the user with emotionally charged interactions and get them to divulge critical information.
If you can avoid getting triggered by smishing and phishing tactics and learn how to ignore them, you will be far ahead. Here are a few critical differences between phishing vs smishing:
#1. Target Devices
Phishing attacks can target laptops, network systems, mobile infrastructure, tablets, and other electronic devices. Smishing is limited to mobile phones or smartphones only. Smishing is evolving though as threat adversaries use messaging apps like Telegram, Discord, and Slack to target mobile users.
#2. Links and Attachments
Smishing links may redirect the user to an operating line or ask them to call up the attacker to talk to them. Phishing simply redirects users to a fake website or requests the user to fill up web forms and submit their personal details. Phishing emails usually contain malicious attachments but smishing messages contain malicious links and phone numbers in them.
#3. Communication Methods
Smishing uses text messaging on mobile phones. Phishing targets any computers or devices that have access to email clients.
Smishing vs Phishing: Key Differences
Smishing and phishing have different delivery methods but they have similar attack objectives. Both aim to gain unauthorized access to sensitive data and resources. Smishing attacks use phone texts to instill a sense of urgency or take immediate action. Phishing occurs mostly through email or by sharing fraudulent websites. The attacker may conduct sufficient reconnaissance and profile their victims for months before launching a spear phishing attack.
Here are the following key differences between smishing vs phishing:
| Smishing | Phishing |
| Smishing text messages can get flagged by your phone’s spam filter or land in the junk. | Phishing emails can evade human detection and spam filters. |
| Attackers mostly target cell phones, smartphones, mobile devices, and any electronic communications that use SMS text messaging. | Attackers lure out victims over email communication channels only. |
| These scams can take the form of fake lotteries, financial scams, or emergency messaging. | Scammers may send links to malicious websites or web forms and ask the victim to visit them. |
| The goal of a smishing attack is to steal personally identifiable information and distribute malware | Phishing attacks will steal corporate credentials or attempt account takeovers on a deeper level within the organization. |
5 Ways to Avoid or Eliminate Smishing and Phishing Attacks
Now that you’ve understood the different ways in which smishing and phishing work, you can take steps to avoid falling victim to them. Here are five ways you can avoid or eliminate phishing and smishing attacks:
- Be vigilant and skeptical – Don’t respond to unknown emails. Stay vigilant when interacting online with anyone. Verify the sender’s identity before revealing any personal information or phone numbers. Do not click on any links or attachments.
- Implement multi-factor authentication (MFA) – Add an extra layer of security to all your devices by implementing multi-factor authentication. It’s better than two-factor authentication and will prevent cyber adversaries from hijacking your physical hardware in case they have access to the premises.
- Educate your employees – Just installing the latest antivirus software or spyware monitoring solutions isn’t enough. Attackers don’t target technology but the people using them. Build a culture of cyber security awareness within your organization and educate your employees on various social engineering strategies. Tell them what to watch out for and how to spot suspicious behaviors online.
- Regularly patch and update – It is very important to regularly patch and update your software and hardware systems. Install the latest updates for your mobile devices, firmware, and applications. This will help prevent any potential bugs or hidden vulnerabilities that attackers may possibly exploit if they find them.
- Use threat monitoring solutions – You can use any counter-smishing tools or anti-phishing technology solutions to prevent smishing and phishing attacks. They are not bulletproof but will drastically cut down on risks by detecting and filtering threats. The amount of manual supervision you need will become much less.
Why Organizations Need to Keep Themselves Safe from Smishing and Phishing Scams?
Global awareness levels about phishing and smishing scams are very low. According to the State of the Phish report, only 22% of users report knowing about these malicious schemes. Knowledge gaps about smishing and phishing tactics can hurt your cyber resilience. Many users don’t understand the technical limitations of safeguards when it comes to automatically identifying and preventing malware-related incidents.
Some victims leave their devices open and many users don’t opt for biometric locks or four-digit pins. Connecting to unsecured public WiFi networks and transmitting corporate data over them can present numerous safety risks and data privacy concerns. Networks are never absolutely protected and cyber criminals can intercept communication channels or study their victims covertly.
Using smartphones and electronic devices is second nature for younger workforces. And unlike millennials, not all of them are aware of the best cyber security practices. Security automation is good but social engineering can pervade it. Incoming texts on mobile phones don’t have traditional authentication systems or spam filters. And when these texts mix business with personal information, they obscure the element of suspicion.
Mobile users receive hundreds of texts every day and it can be difficult to determine how threat actors can exploit opportunities to steal their information.
Can SentinelOne Help Protect Me from Phishing and Smishing Attacks?
SentinelOne’s Singularity™ Data Lake can ingest your data from multiple sources and transform it to gain actionable threat intelligence. It can connect disparate, siloed datasets to gain visibility into threats, anomalies, and behaviors across the entire enterprise.
You can accelerate mean-time-to-response and remove threats completely with full event and log context.
Singularity™ Endpoint will secure your endpoints, servers, and mobile devices. It offers superior enterprise-wide visibility and speeds up your responses to malware, ransomware, and other emerging threats. You can use SentinelOne’s patented Storylines technology to conduct real-time cyber forensics and probe into your cloud infrastructure. Use its endpoint protection features to automatically identify and protect unmanaged, network-connected endpoints that are known to introduce new risks. Purple AI is your personal cyber security analyst and will give you real-time feedback and insights about your current infrastructure.
Singularity Ranger is a real-time network attack surface control solution that finds and fingerprints all IP-enabled devices on your network. It requires zero additional agents, hardware, or network changes. SentinelOne’s unique Offensive Security Engine™ and Verified Exploit Paths will help you stay one step ahead of attackers. If there are any hidden or unknown vulnerabilities within your cloud estate that you aren’t aware of yet, you will find them.
You can learn more about other SentinelOne product offerings that can protect your organization from phishing and smishing threats by visiting here.
Conclusion
You can also look for a sudden increase or decrease in ongoing or outgoing SMS messages to determine if you are being targeted by smishing threats. Monitor SMS gateways for potential anomalies and install anti-spoofing mechanisms to protect your mobile messaging channels.
Avoid getting emotionally charged and don’t react impulsively to threatening emails or any messages that appear to be urgent. Sit back on them, relax, and don’t be intimated. Take your time and use common sense when sharing or handling sensitive information.
You can also run phishing simulations on your infrastructure to see how likely to be targeted. Check with your HR department before you do this. Encourage your employees to report phishing incidents and make them feel comfortable enough to share. Another good tip is to allow them to report anonymously.
We hope our guide helps you understand the differences between smishing vs phishing. You can reach out to SentinelOne for additional assistance.
Smishing vs Phishing FAQs
1. Which is worse: smishing or phishing?
Both smishing and phishing are notorious and can put your personal and financial information at risk. It’s equally critical to incorporate safety and security measures to fight against both smishing and phishing threats.
2. How do I stop receiving spam texts?
You can check your phone SMS settings and turn on the spam filter. Block any unknown or suspicious numbers that are trying to reach you. Turn on the filter to automatically block messages from unknown senders. It’s almost always available on every phone by default.
3. How do I identify fake emails?
If a sender uses a public domain like Gmail, it’s pretty obvious it’s a phishing email. Most companies have their official domain. Another dead giveaway is if the domain name is misspelled. For example, sentinl1.com instead of sentinelone.com
If the email contains poor grammar, or spelling errors, or has mentioned wrong dates, venues, and other errors in details that only you or your employees know from the inside, those are clear signs as well.
4. Are there any tools to stop phishing and smishing attacks?
Many web browsers have built-in security features that warn users about potential phishing emails. There are free browser extensions that can filter phishing emails to a certain degree. SentinelOne Singularity™ Platform is a complete solution that will protect your mobile devices, servers, endpoints, clouds, identities, and users from various phishing and phishing schemes. It is fully scalable, and customizable, but it’s not free due to its advanced features.