Linux Endpoint Protection aims to protect users and their devices from cyberattacks as the SaaS industry grows and cyber risks rise. A case in point is the ransomware attack, which shut down the entire judicial network in Los Angeles in July 2024.
In this article, we discuss how to safeguard Linux users and their endpoints from cyberattacks. We also cover the many challenges Linux Endpoint Protection faces and the promising solutions for the same. We aim to equip users of Linux OS with all the knowledge they need to ensure that their data is safe during every communication they establish over the IoT.
What Is Linux Endpoint Protection?
Linux endpoints are all the devices and hardware that are operating within a Linux OS network. To protect the entire framework from cyber threats, unauthorized access, malware, and other risks, a range of technologies and software are deployed. All these safety measures, such as antivirus, firewall, data encryption, access control, and more, define the process of Linux Endpoint Protection.
Why Is Linux Endpoint Protection Crucial?
The very feature that made it so “in-demand” – its open-source interface – is also the reason why Linux is vulnerable to attacks. The Elastic’s Global Threat Report states that Linux is now the most affected endpoint, with around 91.2% of malware infections.
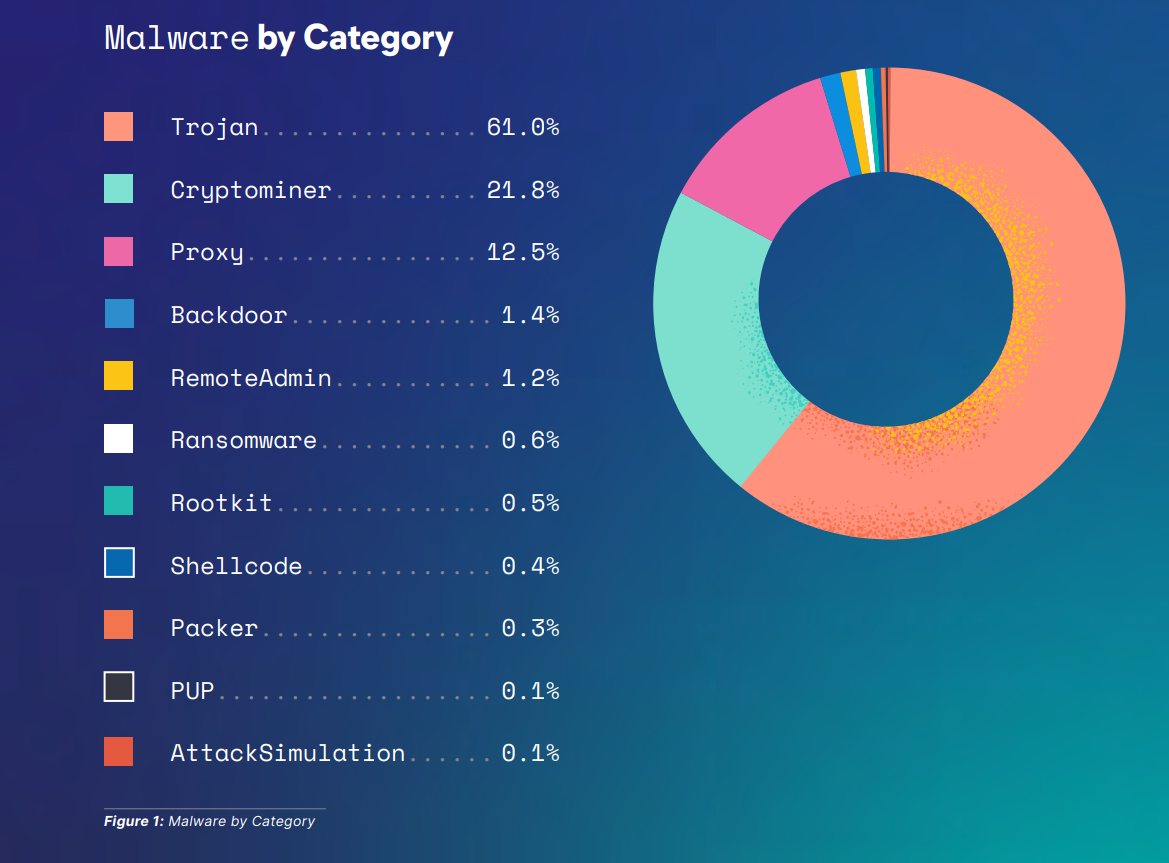 Given the diverse nature of these attacks, Linux Endpoint Protection becomes crucial for the following reasons:
Given the diverse nature of these attacks, Linux Endpoint Protection becomes crucial for the following reasons:
-
Growing Threat Landscape
News about data breaches and unauthorized access to sensitive data are commonly reported. In December 2023, the personal data of nearly three billion individuals was leaked during a cyber attack at National Public Data, a background-checking service. Therefore, Linux-based systems need to implement more robust security measures to protect themselves from ever-evolving threats.
-
Data Security Concerns
Nowadays, most businesses need to store data, even if it is of no use. Even when you install a new application on your phone, you are obligated to allow access to data. This data includes sensitive information and intellectual property, which, if placed in the wrong hands, can create significant disruption across the globe. When you protect these Linux endpoints, you’re also securing confidential information.
-
Compliance Requirements for Data
Strict data protection measures are in place across many industries. Companies are thoroughly assessed to check if their data protection policies are in place. Otherwise, they are fined heavily for any shortcomings and could risk losing their reputation in the market, especially among their customers. Linux endpoint protection measures help companies comply with these regulations and avert fines and other legalities.
-
Protection of Infrastructure
Linux is widely used in enterprise environments, especially over cloud servers. A single compromised endpoint can bring the entire system down and cause major disruptions within the organization. To prevent such unbearable losses and minimize attack surfaces, having an extra layer of security via endpoint protection is always recommended.
-
Long-Term Continuation of Operations
A common myth is that Linux endpoints are less susceptible to attacks. The rise of threats in various forms has made endpoint protection necessary. Sometimes, accidentally authorizing access to a hacker can bring downtime and damage a company’s reputation. Setting up a secure Linux environment can build trust between the company and its stakeholders, protect reputation, increase the lifespan of operations, and ensure long-term success.
A Four-Time Leader
See why SentinelOne has been named a Leader four years in a row in the Gartner® Magic Quadrant™ for Endpoint Protection Platforms.
Read Report
5 Key Features of Linux Endpoint Protection
From behavioral analysis to intrusion detection and prevention systems, the features comprising Linux Endpoint Protection are comprehensive. These features are upgraded regularly to match the ever-changing nature of most cyber attacks. The key features to look for when searching for an endpoint protection solution are:
- Antivirus and anti-malware: The primary feature of a Linux Endpoint Protection solution is detecting and removing malicious activities targeting Linux systems. It uses antivirus and anti-malware tools to continuously scan files, applications, and system processes for anomalies
- Real-time monitoring and reporting: Any solution aiming at endpoint protection for Linux must gain real-time insights into the health of the entire Linux fleet. Historical data and detailed reports on a centralized dashboard will help in making better decisions to improve overall security
- Scalable and flexible: Most endpoint solutions are scalable and flexible to suit the size of the organization and adapt to its infrastructure, whether it is a cloud computing network or machines deployed on the premises
- Centralized management console: Linux Endpoint Protection comes with a unified interface where you can monitor multiple endpoints simultaneously while taking care of pending security policies. Automating security workflows will also help take the burden off your IT team
- Behavioral analysis: An endpoint protection for Linux uses techniques to detect any anomaly in the behavior of both the user and the system. This helps identify any unauthorized access to the system and prevents any potential attack in the foreseeable future.
3 Common Challenges in Linux Endpoint Protection
Linux has come a long way since its inception. Even the most popular mobile operating system, Android, uses a Linux kernel for its operations. Despite being the world’s biggest open-source project, it is still vulnerable and comes with its own set of challenges:
#1. Unseen Security Loopholes
Linux is considered a community project to which hundreds of developers contribute. A common assumption is that with so many developers working on the distribution system, they would be able to identify and rectify any bugs or threats they come across. This was the case with the Shellshock vulnerability, also known as the Bash Bug, which is a major security flaw in Linux systems.
First discovered in 2014, this flaw enables attackers to execute a random code on different formatted environment variables and gain unauthorized access to the system. To mitigate the risks, Linux users were advised to run security updates and apply patches. Although the impact of Shellshock has gradually decreased, this unforeseen security loophole has called for stringent safety measures on Linux systems.
However, it is quite possible that they may overlook these while focusing on improving Linux systems. The pressing priority is having a more advanced security system in place.
#2. Evolving Viruses and Malware
Linux is increasingly used for cloud infrastructure and IoT. This growing popularity is also being noticed by cybercriminals, who are looking for opportunities to damage systems on a massive scale. According to Trend Micro, there has been a 62% increase in ransomware attack attempts across Linux systems from 2022 to 2023.
In the recent past, ransomware attacks like the BlackCat ransomware exposed Linux systems to more risks. In this case, cyber extortionists enter a network, steal sensitive data, and encrypt files. They then use this data to extort money or threaten to release the stolen data. There is no doubt anymore that attackers are developing newer forms of viruses, malware, and ransomware to attack Linux endpoints at any given hour.
#3. Added Risk to Sensitive Information
Although Linux has good safety procedures like data encryption and firewall authentication in place, many users take data protection for granted and neglect adding data safety measures to their systems. This leads to many challenges that hamper Linux’s performance, such as insider threats, poor management of user permissions, and limited integration. It is essential to address them so that individuals and companies can adopt proactive security measures and keep themselves safe against the complexities of cyberattacks happening now.
7 Best Practices for Linux Endpoint Protection
Best practices for Linux endpoint security boil down to security measures like running only essential services, conducting audits for malicious activities, avoiding open ports, and configuring and updating your OS. Here are some more practices to ensure your Linux security is ironclad against cyber risks:
#1. Update Systems Frequently
The simplest and most effective way of protecting Linux endpoints is by updating the systems regularly. When you regularly run updates on your systems, you will protect them from potential risks and security loopholes. When you install the latest security patches, you can fix bugs, and enhance features on your current OS.
#2. Practice PoLP
The Principle of Least Privilege(PoLP) is a part of everything constituting data protection 101. Just as you’re restricted from accessing the cash counter at a grocery store, PoLP restricts a user to limited resources at any given time. PoLP is an essential component of information security measures companies undertake, especially in today’s hybrid work culture. Here’s how PoLP works in Linux:
- Allows a user to create files with only read and write permissions and not execute
- Protects superusers and limits access to administrator privileges
- Prohibits the installation of applications and limits an attacker’s lateral network movement
- Improves operational performance by restricting breaches and malware spread
#3. Install an Antivirus Software
Consider antivirus software as a bodyguard for your digital security. The software continually patrols your systems, scanning for any suspicious activity happening in the background. This extra layer of defense helps you find any cracks in the safety net you have deployed for your Linux endpoints. Running complete scans will help you uncover and destroy trojans, bugs, ransomware, and anything posing a risk to data security before it is too late.
#4. Configure Firewall and Iptables
Configuring your firewall and Iptables is a great way to ensure that there are no unwarranted entries in your network. A firewall is a network security device that monitors the incoming and outgoing traffic on your systems and prevents unauthorized access.
Iptables is a command-line program that helps you customize traffic rules on your Linux system’s firewall. With Iptables, you can audit and filter traffic on your firewall by mentioning protocols, IP addresses, flags, etc., that can potentially harm your entire endpoint network.
#5. Secure SSH Access For Endpoints
SSH (Security Shell) is a protocol used in corporate networks to provide safe access to users and all automated processes. SSH helps automate file transfers, solve connectivity issues, and successfully avoid security risks while exposing a cloud-based system on the internet. Securing SSH access is recommended to reduce the chances of attackers entering your system. Here are a few ways to secure SSH access:
- Disable SSH root login and log in through an alternate account
- Set timeouts on SSH connections to prevent unauthorized access
- Disable password authentication and instead use public key authentication for SSH sessions on your device
- Limit the number of SSH login attempts by making your Linux server forcefully stop the connection
- Establish firewall rules to stop attempts to sign in to SSH using weak passwords with default SSH credentials, usernames, etc.
#6. Enable Two-Factor Authentication
Adding another layer of security to your Linux systems through two-factor authentication(2FA) will protect you from brute-force attacks and credential theft. This method requires more than one credential to prove your identity before granting access to an account. Apart from the usual password login, you will have to enter an OTP received via email/SMS or a code on an authenticator app.
#7. Use an EDR solution
Finally, a guaranteed way to ensure endpoint protection for Linux systems is by implementing an EDR (Endpoint Detection & Response) solution. This EDR solution constantly checks for gaps across the network and fixes them on the go, thereby ensuring that all your endpoints are secure. It also alerts users of any incoming suspicious activity or an attack, preparing you to ramify a safety blanket on all the devices on the Linux OS network.
For example, SentinelOne EPP collects, investigates, analyzes, and automatically blocks and responds to security threats. It automatically and safely blocks threats without the user having to worry about security management and minimizes the impact of endpoint device resources despite having various analysis functions.
Choosing The Right Linux Endpoint Protection Solution
There are many well-performing endpoint protection solutions in the market that can cover all your safety needs. However, here are some key factors to consider while choosing the most suitable one:
- Platform compatibility, especially for cloud and hybrid environments
- Comprehensive threat detection and prevention
- Potential for appropriate endpoint detection and response
- Minimal impact on system performance and scalable as per your environment
- Automatically applies patches and upgrades whenever a vulnerability is detected
- Easy to configure, monitor, and manage from a single interface
- Compliant with different security standards, such as GDPR, HIPAA, and PCI DSS
- Cost-effective and has 24/7 support.
Discover Unparalleled Endpoint Protection
See how AI-powered endpoint security from SentinelOne can help you prevent, detect, and respond to cyber threats in real time.
Get a DemoWrapping UP: Navigating The Scope For Linux Endpoint Protection Ahead
From global business to data systems, we see Linux endpoint protection playing a critical role. After going through the challenges, features, and best practices for endpoint security discussed in this article, here are the key takeaways:
- Linux Endpoint Protection solutions protect devices from various cyberattacks through integrated tools such as firewalls, data encryption, and antivirus software
- Always update your Linux OS because it is the best way to stay protected against sudden attacks
- Having endpoint protection for Linux systems will not only strengthen your organization’s security stance but also improve operational efficiency through task automation and a centralized interface for management
- It is best to go with an endpoint protection solution that prioritizes real-time threat detection, is scalable with the company infrastructure, and keeps advancing to fight against new versions of malware
There are many excellent endpoint solutions in the market, and the best one will depend on the organization’s needs. However, our platform SentinelOne’s Singularity Core emerges as a strong contender and a must-have tool in your cybersecurity arsenal. It harnesses data and AI to protect your organization now and in the future. Join forces with Sentinel One today to add an impenetrable layer of security.
FAQs
Yes, Linux is vulnerable to malware and viruses due to its increased usage in enterprise and cloud environments.
Yes, you can use open-source tools for Linux Endpoint Protection, but they will require more manual configuration compared to other commercial tools.
The key features you should look for in a Linux endpoint protection solution are:
- Real-time threat detection
- Integration with other tools
- Centralized management
- Minimal impact on system performance
- Vulnerability management

