Organizations are grappling with an unprecedented influx of vulnerabilities in today’s rapidly evolving cybersecurity landscape. In 2024 so far, over 29,000 new Common Vulnerabilities and Exposures (CVEs) were reported to the National Vulnerability Database (NVD) – a staggering number even NIST struggles to keep up with. This overwhelming volume makes it virtually impossible for security teams to address every vulnerability, forcing them to prioritize effectively to protect their organization.
Vulnerability prioritization, however, is a complex challenge. Traditional scoring systems like the Common Vulnerability Scoring System (CVSS) highlight the severity of vulnerabilities but often lack critical context about real-world exploitability. This can lead to a misallocation of resources, where teams focus on high-severity vulnerabilities that pose minimal immediate threat while overlooking those actively exploited by attackers. Adding to the complexity is the scarcity of vulnerability remediation data. Even when high-priority vulnerabilities are identified, security teams may struggle to find practical solutions – such as patches or mitigation steps – delaying remediation efforts and increasing risk exposure.
This blog post covers how forward-thinking organizations are adopting data-driven approaches to incorporate threat intelligence and predictive analytics to navigate these challenges. We explore the Exploit Prediction Scoring System (EPSS) and the Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) Catalog emerging as critical tools for understanding which vulnerabilities are being actively targeted by threat actors.

What is CISA KEV?
CISA’s KEV Catalog is a curated list of vulnerabilities actively exploited in real-world cyberattacks. Unlike traditional vulnerability databases that list all known vulnerabilities, the KEV Catalog focuses exclusively on those vulnerabilities that pose immediate and significant risks due to active exploitation. By providing this targeted information, the KEV Catalog helps security teams prioritize their patching and mitigation efforts effectively. CISA KEV enables organizations to move beyond theoretical risk assessments and focus on vulnerabilities being actively leveraged by attackers.
What is EPSS?
The Exploit Prediction Scoring System (EPSS) is a data-driven model designed to estimate the probability that a specific vulnerability will be exploited in the real world. Developed by the Forum of Incident Response and Security Teams (FIRST), EPSS leverages statistical analysis and machine learning techniques to process vast amounts of data related to vulnerabilities and exploitation activities. This system combines multiple factors, including historical data and characteristics of the vulnerability itself, to predict (with proven success) the likelihood of future exploitation.
Unlike traditional risk scoring models that focus solely on the severity of a vulnerability, EPSS emphasizes exploitability potential. This means it assesses how severe a vulnerability is and how likely it is to be used in an attack. This predictive insight is invaluable for organizations aiming to enhance their vulnerability prioritization efforts. By incorporating EPSS into their security strategies, organizations can more effectively allocate resources, focusing on vulnerabilities that pose the highest risk of exploitation. This proactive approach enables security teams to avoid potential threats and significantly reduce their risk exposure.
Enhancing Risk Prioritization & Remediation
Integrating CISA’s KEV Catalog with the Exploit Prediction Scoring System (EPSS) provides organizations with a comprehensive threat landscape view. The KEV Catalog identifies vulnerabilities actively exploited in the real world, highlighting immediate risks that demand attention from security teams. EPSS complements this by predicting the likelihood of vulnerabilities being exploited in the near future. By combining these two powerful tools into their risk scoring, organizations can pinpoint exactly where to focus their remediation efforts. This integrated approach ensures that security teams prioritize vulnerabilities that pose the most significant threats, thereby maximizing the impact of their actions in reducing the overall attack surface.
Alongside the KEV Catalog and EPSS, remediation data also plays a significant role in further reducing noise from vulnerability assessments. When EPSS scores and CISA KEV information are combined with up-to-date remediation options, organizations can reduce the risk of vulnerabilities becoming breaches by focusing on vulnerabilities that are likely to be exploited and having viable mitigation strategies available.
Making Vulnerabilities Actionable with Singularity™ Platform
SentinelOne recognizes the imperative need for more innovative vulnerability management. We’re excited to announce the integration of the Exploit Prediction Scoring System (EPSS) and CISA’s Known Exploited Vulnerabilities (KEV) Catalog support into Singularity Vulnerability Management. This enhancement empowers organizations to distinguish between potential threats and vulnerabilities that are actively or soon to be exploited. By leveraging these advanced vulnerability intelligence sources within Singularity, security teams can focus their efforts where it matters most – streamlining prioritization processes, reducing risk exposure, and making more informed decisions about vulnerability remediation.
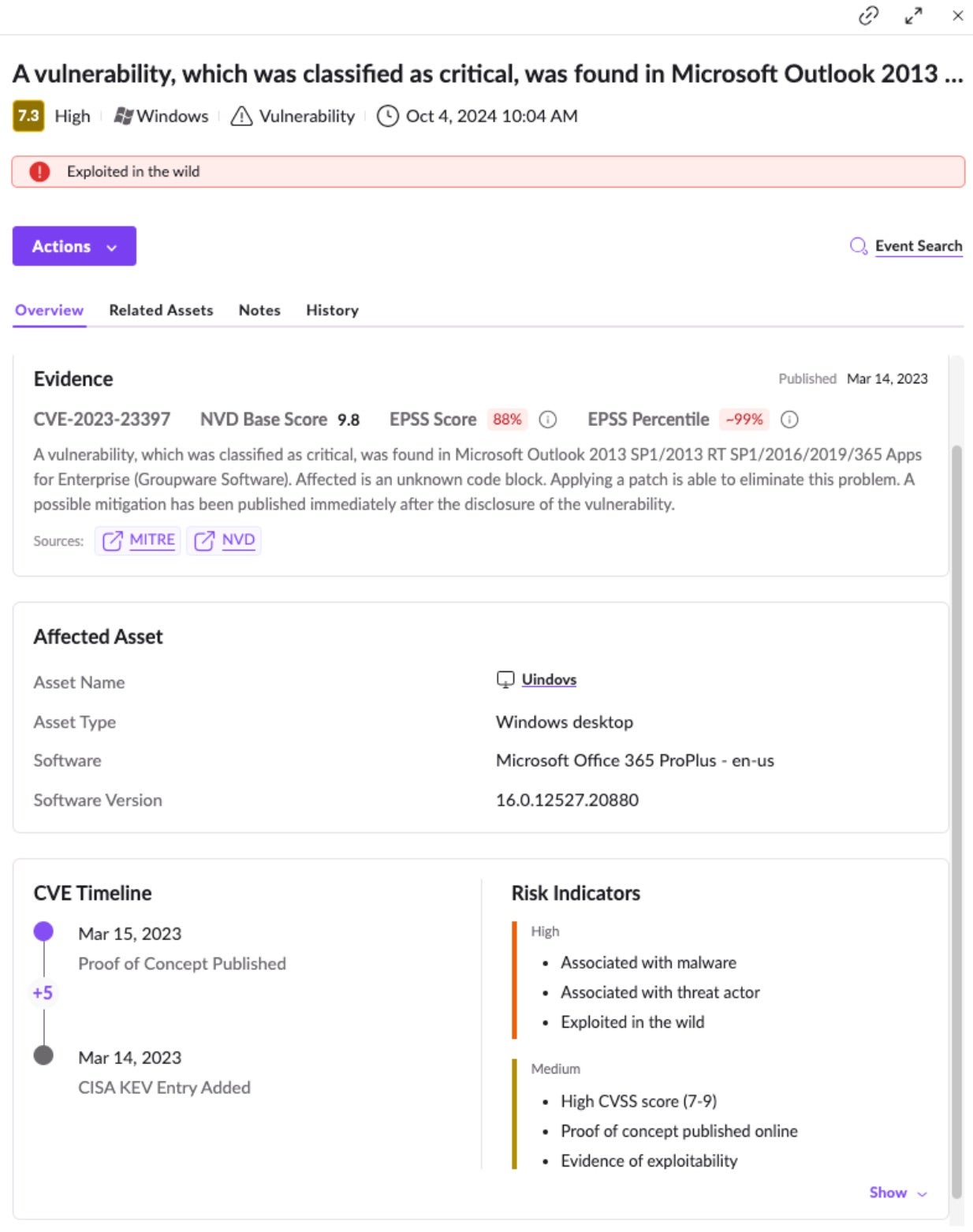
In addition, Singularity Vulnerability Management has launched a new vulnerability scoring system designed to provide a comprehensive assessment of vulnerabilities by incorporating multiple data sources. These include up-to-date threat intelligence, EPSS, CISA’s KEV Catalog, and insights on remediation options. This scoring approach goes beyond traditional metrics by factoring in the real-world likelihood of a vulnerability being exploited, as EPSS indicates, and whether it has been associated with known attacks listed in CISA’s KEV Catalog.
The scoring system helps organizations prioritize their response efforts effectively by including information on available patches or mitigation strategies. The result is a more accurate and actionable vulnerability score that enables security teams to focus on the most critical threats, enhancing overall risk management in the cybersecurity landscape.
Conclusion
Relying solely on traditional scoring systems without considering real-world exploitability exposes organizations to significant risks. By integrating advanced tools like the Exploit Prediction Scoring System (EPSS) and CISA’s Known Exploited Vulnerabilities (KEV) Catalog, security teams can prioritize threats more effectively, focusing on vulnerabilities that are not just severe but are likely to be, or already are, exploited by attackers.
Singularity Vulnerability Management elevates this strategy by incorporating these critical intelligence sources alongside up-to-date remediation data, providing a comprehensive assessment of each vulnerability so you can allocate resources where they matter most. Don’t let the overwhelming number of vulnerabilities compromise your security efforts – take control with vulnerability management solutions designed to keep you ahead of emerging risks.
Contact us today to find out how SentinelOne can transform your vulnerability management strategy and empower your security team to make informed, impactful decisions.


