The Good | Raccoon Infostealer Admin Pleads Guilty & Police Seize Two Extensive Dark Marketplaces
This week marks two wins for global law enforcement groups, leading to the takedown of Raccoon Infostealer’s operator, Mark Sokolovsky, and two alleged administrators of the Bohemia dark market and its sister market, Cannabia.
According to the DoJ, Sokolovsky, a Ukrainian national, pleaded guilty to running the Raccoon Infostealer, linked to the theft of sensitive data such as personally identifiable information (PII), bank account details, and cryptocurrency information. Sold as malware-as-a-service (MaaS), Raccoon Infostealer affected millions of users worldwide before it was dismantled by the FBI and international partners in 2022. Although operators attempted a comeback in 2023, Sokolovsky’s arrest and extradition to the U.S. in 2024 dealt a significant blow to the operation. In total, law enforcement recovered more than 50 million stolen credentials since the malware was seized.
In another success, the alleged administrators of Bohemia and Cannabia, two leading dark marketplaces, were arrested after attempting to carry out an exit scam. Dutch police uncovered the extent of the marketplaces’ involvement in illegal drug sales and distributed-denial-of-service (DDoS) tools, which came out to an average of 67,000 transactions per month, generating a staggering €12 million in turnover by September 2023.
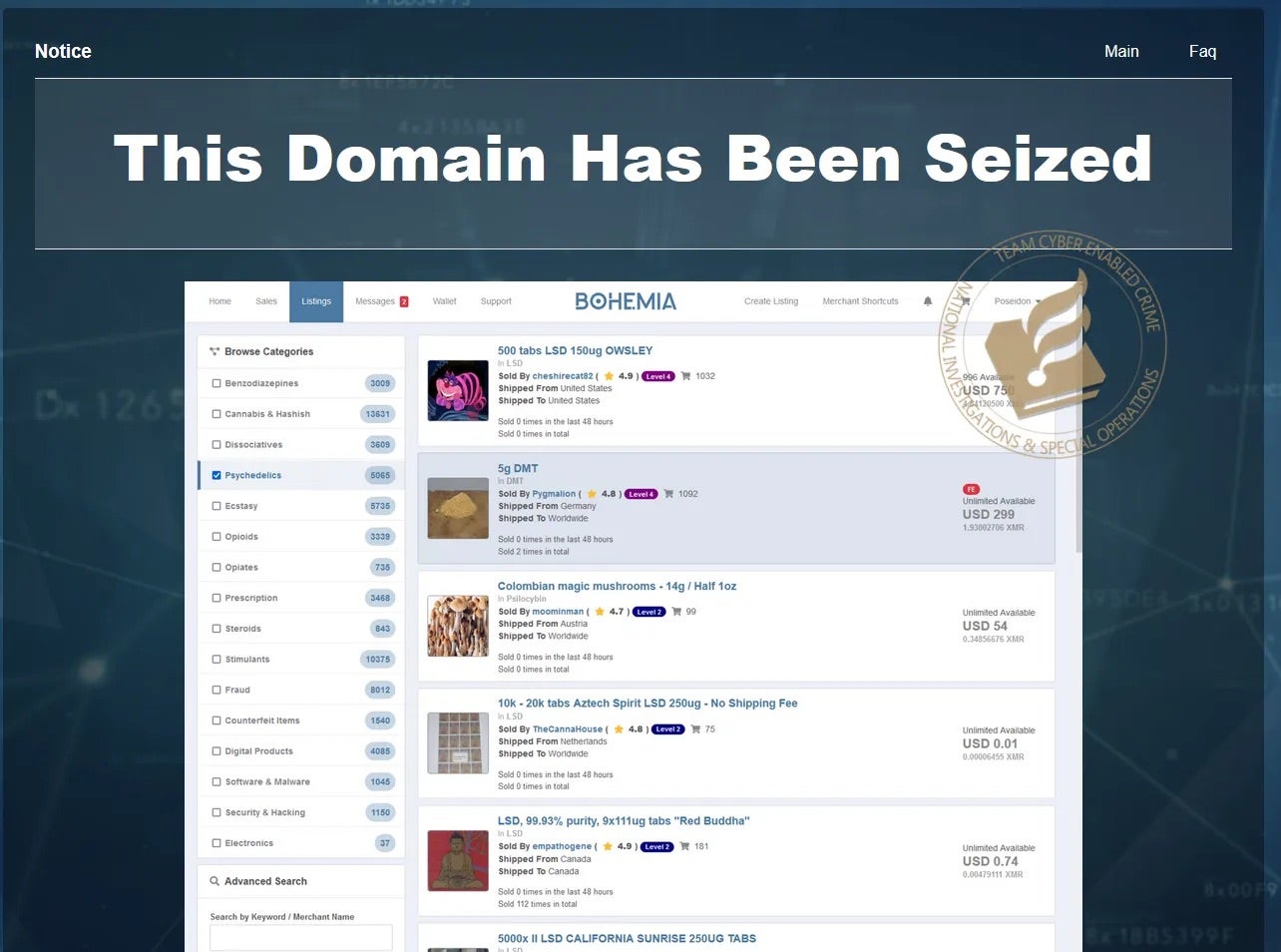
The administrators’ attempt to shut down the sites and escape with funds was thwarted by authorities in the Netherlands, Ireland, the U.K., and the U.S. These arrests send a clear message: the dark web is not as anonymous as criminals think, and international collaboration is key to disrupting longstanding and complex criminal infrastructure.
The Bad | GoldenJackal Deploys New Toolsets Against Government Air-Gapped Systems
Two advanced toolsets used by little-known threat actor, GoldenJackal, have been identified in a string of cyberattacks on embassies and government organizations. These attacks, all focused on infiltrating air-gapped systems, share a common goal of stealing sensitive data that has been deliberately isolated from external connections like the internet. Air-gapping as a security practice is most typically seen for uber-sensitive networks or devices, such as those used for voting, manufacturing, and critical industrial services.
GoldenJackal has been active since at least 2019 but gained widespread attention in May 2020 when it was linked to a cluster of attacks on diplomatic entities across South Asia and the Middle East. This week, cyber researchers offered insight into GoldenJackal’s completely revamped toolset within just five years, made apparent during its targeting of E.U. government organizations between 2022 and 2024.
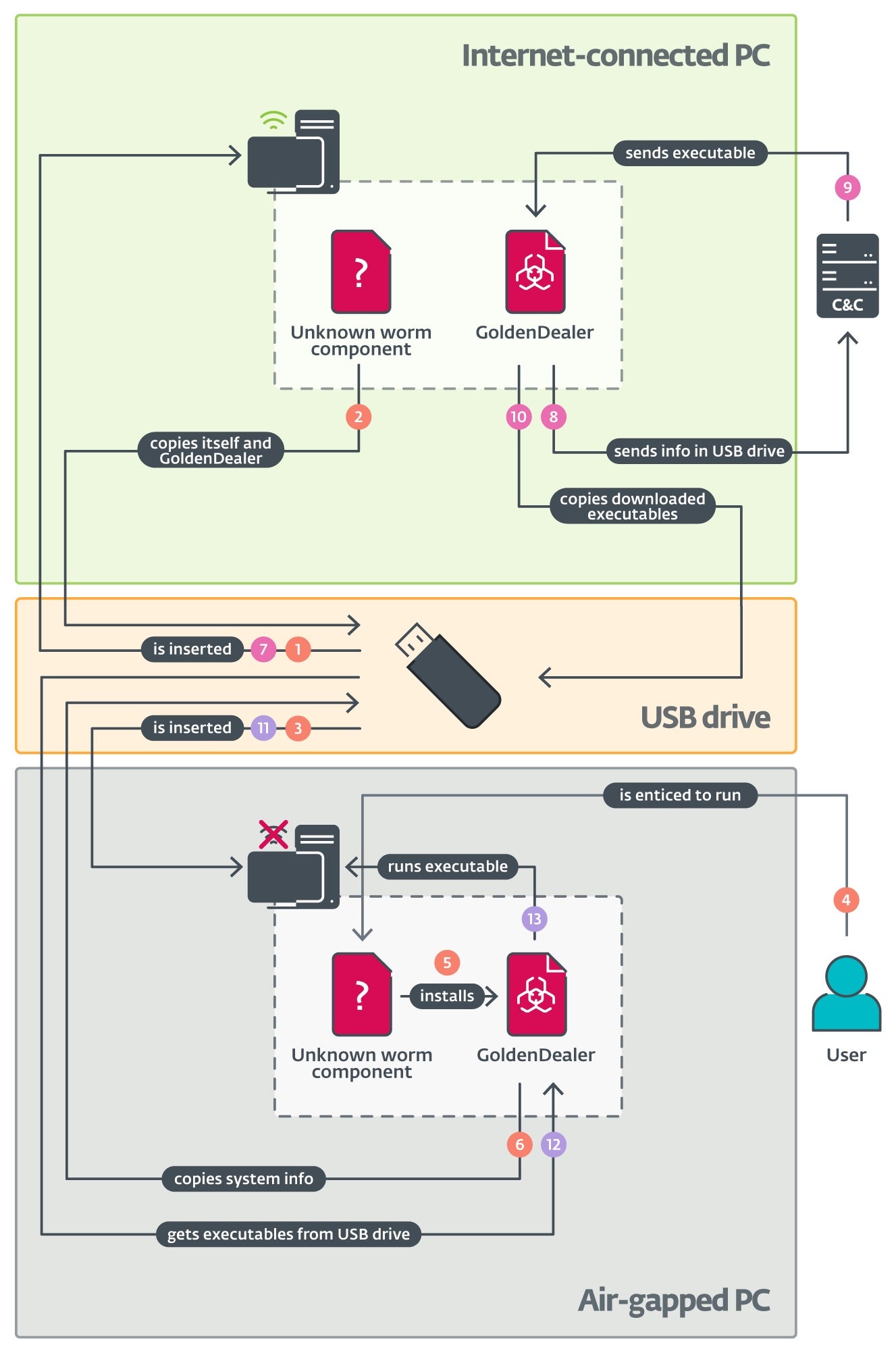
The new air-gapped infiltration techniques include malware families GoldenDealer, to infect USB drives and deliver malware to isolated systems, GoldenHowl, a backdoor that steals data and establishes remote access, and GoldenRobo, for exfiltrating data and files. GoldenJackel’s latest toolset (comprised of GoldenUsbCopy, GoldenUsbGo, GoldenAce, GoldenBlacklist, GoldenMailer, and GoldenDrive) is written in Go and engineered to drive malware propagation, perform data collection, and leverage machine servers to stage and distribute payloads to other hosts.
While its initial compromise methods remain unclear, other researchers suspect that trojanized Skype installers and malicious Word documents are serving as entry points. GoldenJackal remains highly sophisticated and resourceful, creating and managing two bespoke toolsets to breach air-gapped networks in only five years. For now, the group’s advanced capabilities, especially in targeting segmented networks, highlight the growing threat to high-profile government and diplomatic systems.
The Ugly | Mamba 2FA Phishing Kit Targets Corporate & Consumer Microsoft 365 Accounts
An emerging predator in the adversary-in-the-middle (AiTM) phishing ecosystem has been targeting Microsoft 365 accounts through convincing login pages and various security evasion techniques. ‘Mamba 2FA’, a phishing-as-a-service (PhaaS) platform, is relatively new having first been documented in spring of this year. It enables threat actors to bypass multi-factor authentication (MFA) by capturing authentication tokens from victims. Sold for a considerably low cost of $250 per month, Mamba 2FA has quickly become one of the most attractive phishing platforms in the current market.
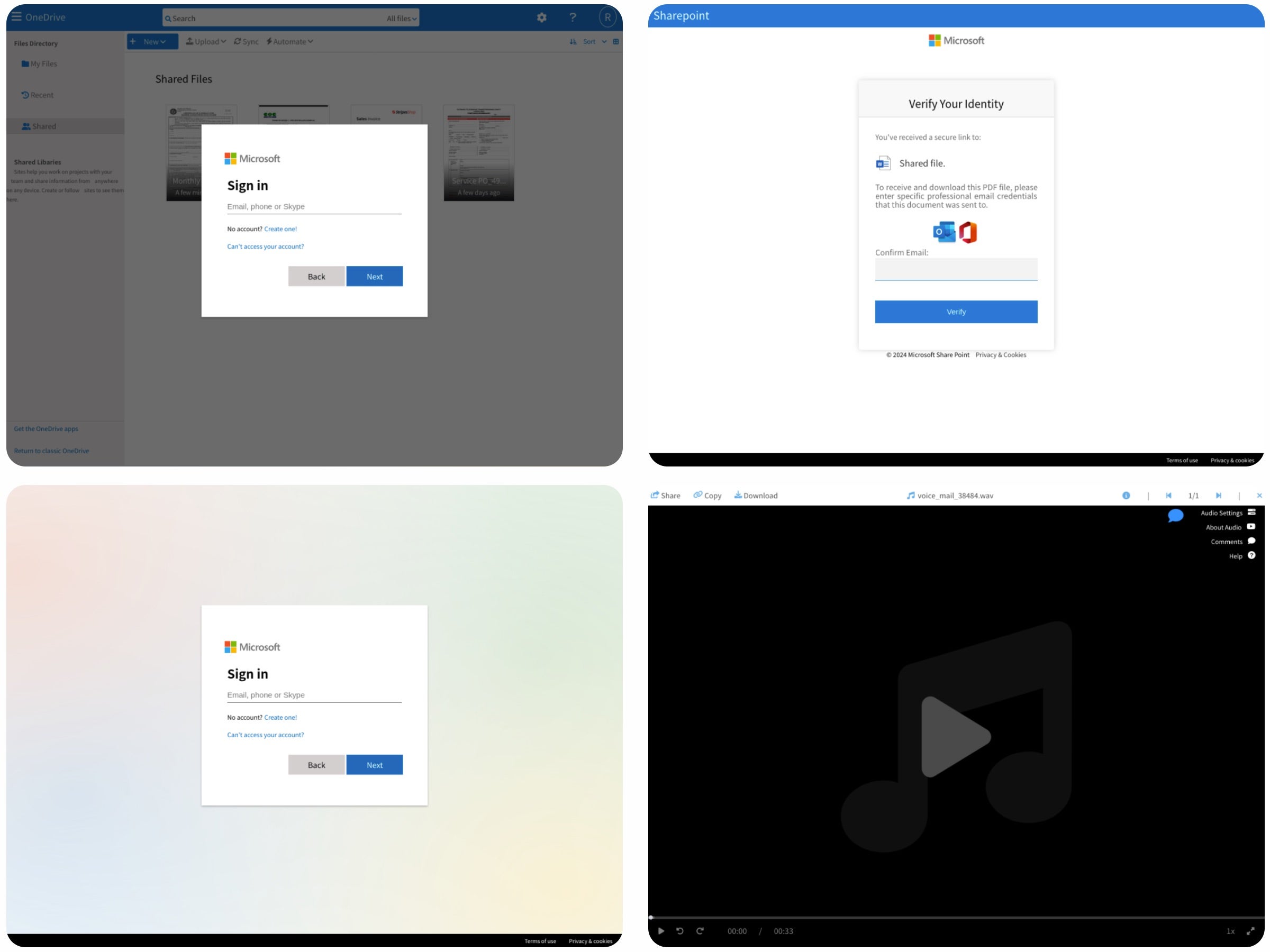
The Mamba 2FA kit is used to primarily target Microsoft 365 users, including corporate and consumer accounts, and offers advanced phishing templates for services like OneDrive, SharePoint, and Microsoft login pages. It enables attackers to customize phishing pages and reflect the branding of targeted organizations, adding credibility to the phishing attempt. Stolen MFA codes, credentials, and cookies are then sent to the attackers via Telegram bots, which allow them to hijack user sessions immediately.
Most recently, Mamba 2FA has improved its stealth tactics by using proxy servers from a commercial provider called ‘IPRoyal’ to hide relay server IPs, rotate phishing link domains weekly, and embed malicious JavaScript in benign-looking HTML attachments. These capabilities make it difficult for organizations to detect unusual logins. Another key feature of Mamba 2FA is its use of sandbox detection to redirect analysis attempts to Google 404 pages instead to throw security teams off its scent.
Phishing continues to top the ways attackers steal sensitive data and deploy malware. Given Mamba 2FA’s accessibility to non-technical and low-skilled cybercriminals, the kit has become a potent threat. To defend against sophisticated AiTM phishing tactics, organizations can implement hardware security keys, certificate-based authentication, geo-blocking, IP and device allowlisting, and limit token lifespans.


