Stéphane Nappo, VP of CISO, once rightly said: “Cybersecurity is much more than an IT topic.” Yet, most businesses treat it as if it is just that until disaster strikes. If our experiences with cybersecurity incidents have taught us anything, it is that ignoring security loopholes in your cloud infrastructure will not just cost you millions of dollars but also customer confidence.
According to data from the Ponemon Institute, reputational costs such as customer turnover and loss of goodwill can reach $1.57 million.
Every time you postpone incorporating Amazon Web Services (AWS) cloud monitoring tools, it further aggravates the damage.
Security cloud monitoring is important for protecting your cloud-based systems. It continuously monitors and analyzes your cloud environment to catch and address potential threats before they can cause harm.
In an era where customer trust drives growth, the companies that leverage AWS cloud security tools work as enablers, not just as safeguards. This article unpacks why AWS security monitoring tools are critical.
 What is AWS Security Monitoring?
What is AWS Security Monitoring?
AWS security monitoring is much like having a 24/7 surveillance system for your cloud setup. Just like cameras track movements in a building, AWS tools keep an eye on everything in your environment—API calls, network traffic, resource settings, and user behavior—to catch any unusual or unauthorized activity right away.
Besides detecting threats in real-time, AWS security monitoring also helps businesses stay on top of legal and regulatory rules.
Whether it’s keeping up with data policies or maintaining audit trails, these tools help you avoid compliance issues. And because business needs change, AWS works with third-party vendors to provide flexible security controls that can easily scale as you grow.
Need for AWS Security Monitoring Tools
AWS security monitoring is not just a malware detection setup or an anomaly tracker tool. It is a cloud monitoring service. Which means it monitors the health of cloud-based IT infrastructures.
With tools of this type in your arsenal, your organization can fix problems before they impact the end-user. Without it, you not only put your company at risk of data loss but also strain your operations as there could be interruptions in data recovery in case of a hack.
Most organizations are thus migrating critical workloads to the cloud. Microsoft reports that 62% of companies surveyed already have a cloud migration strategy. For businesses scaling fast in the cloud, using advanced AWS monitoring tools is essential. It ensures proactive detection and remediation, reducing accumulated downtime caused by cyberattacks.
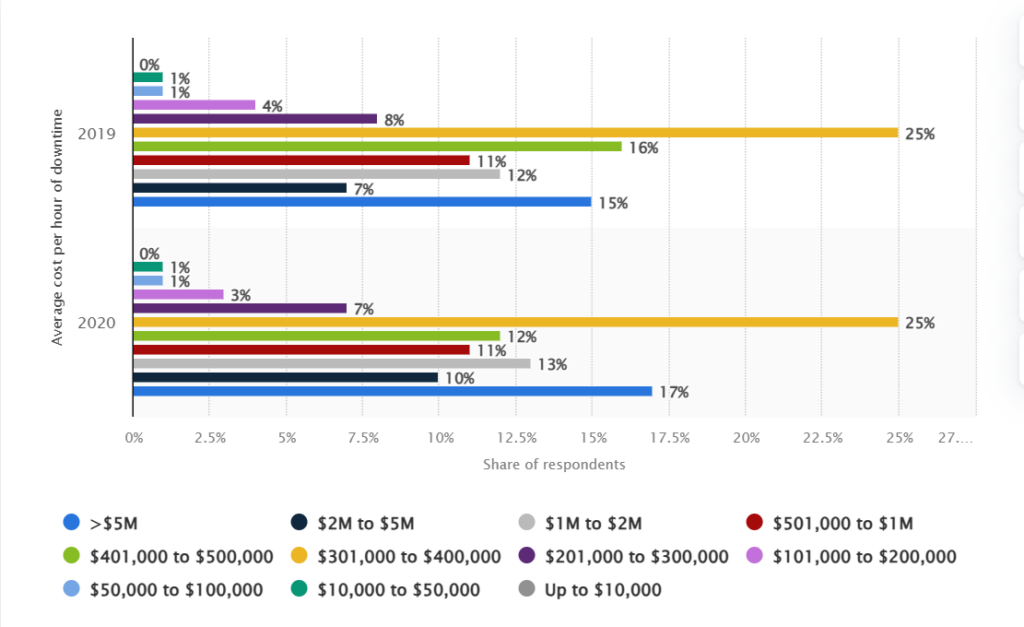
About 25% of companies worldwide report that IT server downtime costs are between $301,000 and $400,000 per hour. Failure to detect timely breaches could result in massive financial losses and brand reputational damage.
 AWS cloud security tools can also provide real-time insights into IT system vulnerabilities. But what makes them indispensable is their ability to automate responses to threats, reducing human error and response time.
AWS cloud security tools can also provide real-time insights into IT system vulnerabilities. But what makes them indispensable is their ability to automate responses to threats, reducing human error and response time.
Integrating these systems into daily operations ensures that security is not just an afterthought. It is an essential driver of operational resilience and long-term growth. Many like Stéphane Nappo have now realized that cyber security and an organization’s digital transformation journey are joint business requisites and should not be viewed in isolation. Maintaining a secure, efficient AWS environment is now an imperative business strategy.
 CNAPP Market Guide
CNAPP Market Guide
Get key insights on the state of the CNAPP market in this Gartner Market Guide for Cloud-Native Application Protection Platforms.
Read GuideAWS Security Monitoring Tools Landscape in 2025
With the sheer volume of cloud-native threats evolving at breakneck speed, the standard approach to security isn’t enough. That’s why we’ve compiled a detailed list of some of the leading AWS security solutions. We vetted each through extensive research and user feedback from trusted sources like G2, Gartner, Peerspot, and Capterra.
Knowing which one to pick can be the difference between safety and danger, and success and failure, for a business.
#1 SentinelOne Singularity Cloud Security
SentinelOne helps enterprises strengthen their security posture by offering a unified and scalable solution for Cloud Security Posture Management (CSPM) and Cloud-Native Application Protection (CNAPP). CSPM is the process of monitoring cloud-based systems and infrastructures for risks and misconfigurations, and CNAPP is a product offering support and protection to cloud workloads and various apps. SentinelOne is built to provide real-time detection, protection, and response across multiple environments, whether endpoints, cloud infrastructure, or containers.
The platform’s static and behavioral AI engines actively hunt for suspicious activity, locking into threats like ransomware, file-less attacks, and zero-day exploits. These engines empower your systems to automatically counteract and neutralize threats in real-time.
By addressing issues before they escalate in this way, the platform cuts down on mean detection (MTTD) and response (MTTR) times. This ensures that your IT infrastructure stays protected with speed and precision.
Integrating Endpoint Protection (EPP) with advanced Endpoint Detection and Response (EDR) capabilities, SentinelOne combines its Artificial Intelligence-driven analytics with comprehensive visibility across environments.
Its patented Storyline™ technology gives SOC teams deep insights and telemetry without added complexity.
SentinelOne’s Offensive Security Engine also goes beyond monitoring potential threats. It identifies verified exploit paths, allowing teams to hunt for threats proactively. With one-click automation, remediation thus becomes almost effortless.
Adhering to industry standards like ISO 27001, PCI, and NIST ensures compliance.
SentinelOne Platform at a Glance
SentinelOne’s cloud-native security is built to optimize enterprise protection for AWS environments. Powered by AI, the platform offers a unified code-to-cloud security solution that secures your cloud, endpoints, and identities.
It integrates smoothly with AWS services to provide real-time threat detection, protection, and response, so your cloud stays secure. With full visibility across your AWS setup, you get clear insights and automated solutions to quickly find and fix issues.
As a trusted AWS partner with over 20 integrations—including Amazon Security Lake, AppFabric, and Guard Duty—SentinelOne helps you boost security and simplify operations. It works with key AWS services like EC2, EKS, and S3, so deployment is easy and security stays strong.
Features:
The cloud environments today demand real-time proactive defenses that go much further than just surface-level monitoring. The idea is to move from a reactionary firefighting approach to anticipating them. Here’s how SentinelOne does precisely this:
1. Real-time detection and prevention of credential leaks
SentinelOne actively scans secrets in real-time, detecting more than 750 types across platforms, such as BitBucket, GitHub, and GitLab. Catching these leaks before they happen, it stops cloud credentials from slipping through in private repositories. This helps with cutting down on potential data exposure.
Let’s assume there is a common threat vector like crypto miners. When a threat gains credential access to an EC2 computer cluster and launches a crypto miner like xmrig through a simple remote shell script, SentinelOne’s platform quickly detects the malicious activity.
In such cases, multiple engines, including the Application Control Engine, flag the detection, thus consolidating everything into a single alert.
In the image above, it’s safe to say that had the agent been set to “Protect Mode,” it would have triggered an automatic response action. However, with “Detect Mode” enabled, the cloud security engineer can still remediate the issue with just a single click and notify DevOps. The DevOps can then conduct root cause analysis, preventing future credential compromise.
2. Shift-Left security for Infrastructure as Code (IaC)
Detects misconfigurations across Infrastructure as Code (IaC) templates, such as Terraform and CloudFormation, enforcing Shift-Left security to catch vulnerabilities early in development. This strengthens cloud infrastructure by addressing issues before deployment.
3. Near zero false positives with an Offensive Security Approach
By adopting an Offensive Security approach, SentinelOne minimizes false positives. It thus provides SOC teams with only actionable and verified threats. In other words, it reduces alert fatigue and increases operational efficiency.
4. In-built and customizable threat detection policies
The platform allows users to access SentinelOne’s detection engines’ built-in AI algorithms. These algorithms have been trained on the behavioral patterns of about a billion malware samples.
Or, you could also write your own custom policies for threat detection and event analysis, enabling them to query, search, and enforce new security rules tailored to your organization’s specific environments.
Here, SentinelOne’s behavioral AI engine flags suspicious malware and captures vital details like the source process path (e.g., Python), command line arguments pointing to a base64-encoded script, and the process user. The platform goes on to automatically contain the origin of the threat.
5. Accelerates cloud threat discovery and mitigation
SentinelOne empowers enterprises with real-time cloud threat discovery, in-depth investigations, and rapid risk mitigation. It enhances incident response and ensures faster resolution times.
6. Automated compliance reporting and domain monitoring
The platform generates compliance reports, exports Software Bill of Materials (SBOM) from code, and can monitor domain names. In doing this, it provides businesses with the tools to stay compliant and aware of external risks.
Core Problems That SentinelOne Eliminates
Organizations are grappling with a growing range of security threats. Nearly 68% of businesses experienced a cyberattack in 2022. And as cloud environments proliferate, IT teams struggle to keep pace.
Without complete visibility into cloud assets or automation to address misconfigurations, problems compound over time.
The cost of one misstep can be astronomical, yet many enterprises are still stuck with legacy tech that keeps their IT departments blindfolded and constantly firefighting.
Here is a quick breakdown of how SentinelOne addresses prevalent enterprise security problems, how legacy solutions fail, and how this platform intelligently fills these gaps:
| Ongoing IT Issues in Organizations | Gaps Left by Legacy AV/Outdated Cybersecurity Systems | How SentinelOne Solves It |
|---|---|---|
| Cloud complexity and fragmented visibility | Older solutions often fail to monitor hybrid cloud environments, leading to gaps in oversight. | SentinelOne delivers complete visibility across cloud and on-premise assets, simplifying cloud data security and ensuring nothing is overlooked, whether in AWS, Azure, or elsewhere. |
| Undetected misconfigurations before deployment | Traditional systems focus on post-deployment, allowing risks to slip in during production. | With proactive scanning of IaC templates like Terraform, SentinelOne catches misconfigurations early, addressing vulnerabilities before they make it into the cloud environment. |
| Manual and slow response times to emerging threats | Many legacy systems rely on manual intervention, delaying containment and remediation efforts. | SentinelOne automates threat response with customizable policies. It allows tailored and immediate reactions to incidents, minimizing the window of exposure and harm. |
| Malware spreading unchecked through cloud storage | Outdated solutions lack proactive scanning in cloud storage environments, letting infections spread. | SentinelOne’s automated in-file scanning and instant quarantining prevent malware from propagating, stopping the threat at its source within storage systems like NetApp. |
| Lack of coverage for unknown cloud deployments and shadow IT | Most legacy solutions overlook hidden or unmonitored cloud assets, increasing risk exposure. | SentinelOne actively discovers and secures unknown cloud deployments, eliminating blind spots and mitigating the risks that shadow IT brings to cloud ecosystems. |
| Slow, inefficient investigations after a breach | Fragmented forensic tools make tracking attack vectors and assessing damage a drawn-out process. | SentinelOne’s Storyline™ technology delivers real-time forensic telemetry, mapping out the attack’s path, enabling swift analysis and decision-making for the security team. |
| Difficulty meeting compliance with manual reporting | Compliance tracking and reporting are typically tedious and prone to errors with outdated systems. | SentinelOne streamlines compliance with automated reports, CI/CD pipeline scanning, and SBOM generation, ensuring alignment with PCI DSS and HIPAA regulations. |
SentinelOne Secures Rapid Deployment for Protection of Over 3,500 Endpoint Devices for Canva
SentinelOne collaborated with Canva, a recognized tier-one enterprise leader in design development. Here’s why:
- Challenge:
Canva had no on-premise servers or networks, as it would be in most typical enterprise networks. The bulk of their environment was built on the cloud, and their rapid growth required that they secure their global workforce with a solution in the fastest time.
SentinelOne’s Impact:
- Quick go-to-live rollout
SentinelOne enabled seamless deployment across Canva’s 3,500+ endpoints in just weeks. In no time, it offered 360° visibility for the company to monitor compliance and software use cases.
- Reduce Management Complexity
The platform’s lack of kernel integration in Linux, along with feature parity across OS (Mac and Windows), eliminated the need for deep system-level access, reducing complexity and improving stability.
- Cross-Platform Consistency
SentinelOne provided near-feature parity across Linux, Mac, and Windows. Canva’s security engineers could respond consistently across platforms without worrying about specific limitations or visibility gaps.
- Improved Response Times
With reliable, cross-platform telemetry, Canva could quickly identify and respond to threats, enhancing overall security operations efficiency.
Look at Singularity Cloud Security’s ratings and review counts on peer-review platforms such as Gartner Peer Insights and PeerSpot.
See SentinelOne in Action
Discover how AI-powered cloud security can protect your organization in a one-on-one demo with a SentinelOne product expert.
Get a Demo#2 AWS Security Hub
AWS Security Hub is a CSPM tool. It continuously checks your AWS security tool’s resources against security best practices. These checks are automated and based on predefined security controls that map your systems with compliance frameworks like CIS and PCI DSS.
Features:
AWS Security Hub continuously checks your AWS resources against security best practices. It centralizes findings from multiple AWS services and partner products into one format, making it easier to manage and respond to security alerts.
It also does the following:
- Automate compliance checks using standards such as CIS AWS Foundations
- Offer security posture management with a customizable dashboard
- Integrate with AWS Lambda for remediation purposes
- Support multi-account environment security auditing
Check out TrustRadius and PeerSpot reviews to see what users have to say about AWS Security Hub
#3 AWS CloudTrail
Amazon’s Cloudtrail is an aws cloud monitoring tool that records user activities and API usage from all AWS services to support better auditing and compliance processes. It logs events from AWS Management Console, CLI, and SDKs. CloudTrail Lake, a managed data lake, stores and analyzes these events and converts them from JSON to Apache ORC formats for querying and auditing.
Features:
CloudTrail has a variety of great features, and many users find it very helpful. Here’s why:
- It assists with enabling risk and compliance auditing of your AWS accounts
- It automatically records and monitors AWS API calls for your account
- It delivers log files straight into your Amazon S3 bucket for secure storage and accessibility
Evaluate these reviews and get an informed opinion about AWS CloudTrail’s capabilities.
#4 Amazon GuardDuty
Amazon GuardDuty is a security monitoring tool that keeps up with and protects your AWS accounts. It does this by helping to analyze metadata from CloudTrail, VPC Flow Logs, and DNS Logs. It uses ML to detect and identify potential security risks within your AWS environment.
Features:
Amazon GuardDuty strengthens cloud security with advanced detection and monitoring capabilities. Capabilities include:
- Able to share findings with AWS Security Hub for centralized compliance and security monitoring
- Audit risks to S3 assets by analyzing AWS CloudTrail management and S3 data events
- Detect malicious activity in Amazon EKS clusters using Kubernetes protection
Explore feedback and ratings on PeerSpot and SourceForge to get further insights into Amazon GuardDuty’s capabilities.
#5 Prisma Cloud by Palo Alto Networks
Prisma Cloud manages security posture and protects workloads as a cloud security platform. It offers visibility, monitoring, and fundamental alerts for deviation in operational normalcy. Allowing teams to automate workflows, it improves communication between your SecOps and DevOps departments.
Features:
Some of the best features of Prisma Cloud become evident once you understand how it works to strengthen security for multi-cloud environments. It does this by:
- Safeguarding configurations, reviewing codes, and integrating with other tools
- Offering cloud security tools for enterprise-grade container security
- Implementing permissions and protecting user identities across cloud platforms like Azure and GCP
- Enforcing micro-segmentation for enhanced security
Review PeerSpot and Gartner Peer Insights to hear from real users about Prisma Cloud.
#6 Check Point CloudGuard
Check Point CloudGuard’s solution helps provide security and compliance automation setups for both your public cloud and Kubernetes environments. Its centralized management system is founded on a multilevel security architecture that systematically syncs with advanced threat prevention measures across cloud, network, and mobile devices.
Features:
This solution automates security and helps organizations track compliance regulations to manage posture for your cloud environments. It also:
- Uses precise security policies to limit threat movement and safeguard different cloud workloads.
- Preemptive AI-based web application firewall to stop zero-day threats
- Automatically scales protection to meet your cloud environment’s needs
- Monitors and secures exposed API keys, tokens, credentials, and risky configurations
Evaluate customer experiences on PeerSpot and G2 to assess Checkpoint’s strengths.
#7 Amazon Macie
Amazon Macie is a security tool in AWS that uses machine learning to find, label, and protect sensitive data. It scans your AWS environment and helps keep your data safe. Currently, it supports Amazon S3, with plans to expand to more AWS data stores. Macie can identify PII and PHI in your S3 buckets and monitor the buckets for security and access control.
Features:
- This solution improves data protection security by grouping related findings and centralizing reports to better manage security across large environments. Other features include:
- Creates and manages an “allow list” that defines specific text patterns that you want Macie to disregard when inspecting S3 materials for sensitive data
- Allows secure review of sensitive data in Amazon S3 objects using customer-managed KMS keys
- Aggregates sensitive data discovery findings in the administrator account and sends findings to Amazon EventBridge
Read through reviews to form an educated perspective on Amazon Macie’s capabilities.
#8 Amazon KMS
AWS Key Management Service (KMS) manages encryption keys within AWS environments. It generates and controls cryptographic keys to secure assets like S3 buckets, databases, API keys, and logs.
It helps organize keys into a clear hierarchy of aliases, identifiers, and versions. It simplifies encryption management while offering granular control over who can access what.
Features:
This solution encrypts data across services like S3, EBS And RDS. Its core features include:
- AWS KMS allows you to create and use asymmetric KMS keys and data key pairs for signing, encryption, or key agreement purposes.
- AWS CloudTrail logs requests made to AWS KMS, capturing details like the user, time, date, API action, and key used, and stores these logs in an Amazon S3 bucket.
- AWS KMS guarantees that plaintext keys remain secure by using hardware security modules (HSMs) validated under NIST FIPS 140-2 standards.
No available ratings on Gartner and Peerspot
#9 Amazon Inspector
AWS Inspector scans EC2 instances, container images, and Lambda functions to detect security flaws. It uncovers vulnerabilities, referred to as Common Vulnerabilities and Exposures (CVEs), which are publicly shared to enhance transparency and raise awareness.
Features:
Amazon Inspector provides users with a dynamic vulnerability management model that’s tailored to your cloud setup. Its features include:
- Adjusting the National Vulnerability Database (NVD) base score to provide severity scores tailored to your specific environment.
- It can be activated for your entire organization with a single click, and you can automate activation for future members when they join.
- Offers a “Findings View” that lists all findings and provides detailed information, allowing you to group findings by category or vulnerability type.
Explore PeerSpot reviews for firsthand accounts of Amazon Inspector usability
#10 AWS Config
AWS Config monitors and records changes, such as modifications to security groups, in real time. It also enables the creation and application of built-in or custom rulesets to assess these changes.
For example, you can schedule a Lambda function to track newly created events or detect rule violations and trigger an SNS notification.
Features:
AWS Config records configurations for custom resource types, like on-premise servers and version control systems. Other features include:
- Retrieval of detailed information about a resource’s configuration at any point in the past using the AWS Management Console, API, or CLI.
- Automatically map and track relationships between AWS resources, like recording changes when an EC2 security group is associated with an EC2 instance.
- Support extensibility by allowing you to publish the configuration of third-party resources into AWS Config using public API operations.
Take a look at user testimonials for a comprehensive view of AWS Config.
How to Choose the Right AWS Security Monitoring Tool
In 2021, 71% of IT decision-makers identified monitoring and observability as their top cloud priorities. Yet a survey by LogDNA and Harris Poll shows that 74% of companies fail and fall short of achieving true observability. This shows that getting the right tools can not be stressed enough.
When selecting the right AWS security monitoring tools, you must first think beyond today’s looming threats. Future-proofing your IT department’s cloud security should be a top priority.
This simply means that your enterprise must adopt systems that not only respond to current risks. It must also adapt and remedy “mutated” emerging ones.
Legacy tools may detect basic misconfigurations, but what happens when threats evolve faster than your detection capabilities? This shows that transitioning to AI-powered (continuous self-learning models) intelligent systems is no longer optional; it is a necessity.
Some key factors to consider when evaluating your AWS security monitoring tools include the following.
1. Focus on What Truly Needs Protection
Rather than going for a one-size-fits-all approach, do not forget about the most critical components that run your business. For instance, protecting a database hosted in the cloud with customers’ information is more urgent than protecting a simple web app. Data breaches hit the bottom line hardest and have a severe impact on revenue.
Every dollar spent should match the risk, especially when the cost of data breaches in 2019 saw an increase of up to 4% in customer churn, with an average cost of $5.7 million. This is 45% above the average total data breach cost.
2. Compliance should be more than just a checkbox
It’s not just about meeting GDPR or PCI DSS. The right tools also streamline audits, provide real-time tracking of compliance violations, and avoid surprise regulatory fines. With 87% of organizations reporting poor outcomes due to low compliance maturity or reactive compliance measures, finding tools that simplify the process can give you a real edge.
3. Budget Where it Matters Most
Cloud security can balloon costs, but prioritizing high-risk assets and leveraging cost-efficient tools ensures you remain protected without breaking the bank. Focus on tools that offer scalability without sacrificing performance as your cloud grows, aligning costs with evolving risks.
4. Seamless Integration is Non-Negotiable
You don’t need more tools; you need better integration. A tool that doesn’t play nice with your existing AWS ecosystem adds more complexity than security. Instead, choose tools that can smoothly work within your infrastructure, minimizing operational friction and ensuring complete coverage.
5. Grow Without Redoing your Entire Security Stack
The security landscape shifts fast. So, choose scalable tools that evolve with your AWS environment. With more than 50% of companies accelerating cloud adoption by 2028, your security tools should adapt effortlessly as your workloads change. You should not feel forced to redesign your approach.
6. User Experience Matters More than You Think
A poorly designed tool that requires weeks of training to use effectively can cripple security response times. Opt for intuitive systems with clear interfaces and abundant training resources. This will help your team start preventing threats, instead of spending time figuring out how the tool works.
 CNAPP Buyer’s Guide
CNAPP Buyer’s Guide
Learn everything you need to know about finding the right Cloud-Native Application Protection Platform for your organization.
Read GuideConclusion
AWS security monitoring tools are primarily functional for preventing data breaches and attacks. However, they are also key drivers in ensuring business resilience in the long term.
Security gaps are inevitable, but focusing on critical assets and using scalable, adaptive tools makes all the difference. Tools like SentinelOne Singularity Cloud, with its advanced AI-powered threat detection and seamless AWS integration, are crucial to future-proofing your infrastructure.
FAQs
AWS Security Monitoring is important because it gives you constant visibility into your AWS setup, helping you spot and deal with security threats in real-time.
Since AWS uses a lot of complex infrastructure and integrates with third-party tools, vulnerabilities can pop up. Good monitoring helps catch issues like misconfigurations, unusual activity, or unauthorized access right away.
Plus, it helps you stay compliant by tracking who’s accessing what, how things are being used, and when settings are changed, keeping you in line with industry standards.
AWS Security Monitoring Tool is a collection of built-in AWS-native services which allow you to monitor your AWS environment in real-time. It enables the user to identify security risks, control changes, and maintain the necessary measures.
Tools like CloudWatch monitor performance and catch any unusual activity, while CloudTrail logs all API calls and resource changes. GuardDuty adds an extra layer of protection by using machine learning to detect threats, so you can stay on top of security without the guesswork.
AWS Security Monitoring Tools give an early warning of security threats, which means they can be dealt with before they escalate into more serious risks. Equally important, they are capable of doing so without necessary manual site checks constantly as they release preprogrammed alerts and notifications in real-time.
Additionally, they are adaptable, allowing you to incorporate additional security measures by linking up to third-party security systems. On the compliance side, these tools automatically and continuously monitor the AWS environment templates for PCI-DSS, ISO 27001, etc.
As a result, it reduces the risk of penalties or interruptions in operations due to violations, which not only ensures safety but also secures your company’s image.
SentinelOne is a great option for AWS security monitoring because its AI-powered platform provides real-time protection, detection, and response across your AWS setup. With features like Cloud Detection & Response (CDR) and Cloud Workload Security (CWS), you get full visibility and automatic fixes for any issues that pop up.
One big plus is how easily SentinelOne integrates with AWS Security Hub, pulling in high-quality threat data from its agents, so your security team can quickly prioritize and handle threats. It also offers agentless vulnerability scans and checks for over 750 types of secrets across both public and private clouds, keeping your environment secure from end to end.
As an AWS partner with over 20 integrations, SentinelOne works closely with AWS services, making it easy to deploy through the AWS Marketplace and keep your cloud secure with minimal effort.
Amazon CloudTrail is AWS’s native monitoring tool. It is primarily used to track API calls and user activity across your infrastructure. It provides visibility into actions taken by users, roles, or services, enabling better auditing of governance, compliance, and operational risks.

