With ever-increasing threats becoming increasingly sophisticated and plentiful, old-school security controls often need to be more robust in filling the detection and response gaps. Enter Extended Detection and Response (XDR), a potent, unified security approach that promises to help raise your threat visibility while streamlining your defense mechanisms.
But what is XDR, really, and is it good enough to secure your organization and its various digital assets? This post will break down the concept of XDR architecture and reveal further actionable insights through which you may implement it within your environment to really advance your security posture.
And will just leveling up your security posture work? Well, let’s discuss below.
 What Is XDR?
What Is XDR?
XDR is a cybersecurity solution designed to address today’s threats by bringing multiple layers of detection and response under one umbrella and extending their capabilities. Think about an old medieval castle. In the old days, it might have been enough to defend the castle with solid walls and a watchtower. But since the more the threats evolved so did the invaders, which could dig or climb through tunnels or walls in the dead of night. To continue their safety, castle defenders had to undergo changes by watching the gates and the skies, underground, and everywhere else where risk could appear.
Traditional security tools, such as firewalls or antivirus apps, focus on only one specific threat vector, like a knight watching the castle gate. Because they focus only on that one vector, they will miss subtler attacks. XDR is like a modern castle defense system: all those watchtowers are connected and monitored gates, walls, tunnels, and messengers so as not to let any threat go unseen.
XDR integrates data from many sources—endpoints, servers, cloud services, and networks—into a holistic view of attacks. It is not a detection tool but an instrument through which your organization can respond to all those threats promptly and efficiently by automating and prioritizing responses according to the danger. XDR is like a vigilant fort with eyes everywhere. It views the whole battlefield and is ready to defend from all sides.
Core Components of XDR Architecture
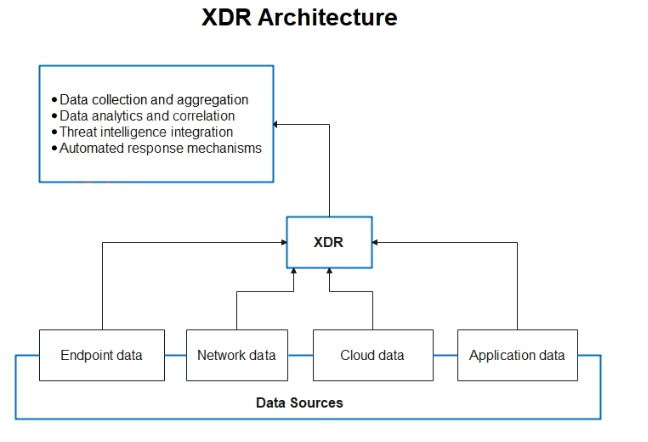
An XDR Architecture
As illustrated above, an XDR architecture combines various elements of cybersecurity to present an overall view of threat detection, analysis, and response. Its core elements provide an integrated platform for seamless detection, analysis, and response in several domains.
Below is a breakdown of its core components.
1. Data Collection and Aggregation
This forms the foundational layer of XDR, where raw data is collected from various sources. It integrates telemetry from multiple environments to provide complete visibility. The primary data sources include:
Endpoint data: Gather logs or behavioral data generated from your endpoints, whether servers, laptops, mobile devices, or any IoT device. This helps track anomalies such as malware in your systems or unusual behavior.
Network Data: To detect network-based threats, collect information about your network traffic, including packet flows, network anomalies, firewall logs, and connection history.
Cloud data captures activities within your cloud environments, whether IaaS, PaaS, or SaaS. It analyses access patterns, application usage, and API activity within the cloud, which may detect misconfigurations or breaches.
Application data: This includes application-level data, such as logs from your applications, databases, and web services. You would find this information very useful in identifying attacks, such as SQL injection, XSS, or illegal access to the application.
2. Data Analytics and Correlation
XDR architecture incorporates the collection of vast security data from different sources. Advanced analytics and machine learning algorithms correlate events from your systems to identify patterns that are actually indicative of a cyber threat.
3. Threat Intelligence Integration
XDR systems incorporate feeds from threat intelligence platforms that provide real-time information about emerging threats, vulnerabilities, and attack tactics. Thus, through such intelligence, the detection mechanism in XDR will be enhanced, and your security teams will even be notified beforehand of risks.
Your organization keeps abreast of world threat trends with this kind of integration. It also means your organization can always defend against known attacks and exploits just found.
4. Response Mechanism Automated
XDR systems have automated response mechanisms, which make incident response more efficient. Once the threat is detected and confirmed, the platform can take pre-defined actions, such as isolating affected devices, blocking malicious IPs, or initiating system scans.
Automation, therefore, keeps the distribution of attacks localized, reduces response time, and mitigates the speed at which damage is reduced. It also prevents overloading security teams and allows them to focus more on complex or strategic issues.
Key Features of XDR
As you already know, XDR improves the security across your organization by integrating various security tools and systems into a unified solution. The following are the key features of XDR.
 1. Unified Visibility
1. Unified Visibility
XDR integrates and consolidates data from multiple security layers into a single platform. This unified view helps your security teams to gain a holistic understanding of your security posture and detect threats across various environments.
It reduces data silos and allows seamless correlation across your security tools, providing better situational awareness.
2. Advanced Threat Detection
XDR uses sophisticated analytics, AI, and machine learning algorithms to identify advanced threats that traditional security tools might miss. By analyzing your data from multiple sources and applying behavioral analytics, XDR can spot anomalies, detect zero-day attacks, and uncover hidden threats such as fileless malware or insider threats.
3. Automated Threat Response
XDR automates the process of responding to threats through predefined playbooks and workflows. When a threat is detected, it can initiate actions such as quarantining affected systems, blocking malicious traffic, and remediating compromised assets without your manual intervention.
Such automation helps reduce response times, minimizes the risk of human error, and enables your teams to focus on more strategic tasks.
4. Simplified Security Operations
By consolidating alerts, analysis, and response mechanisms into a unified platform, XDR simplifies security operations and reduces alert fatigue. The platform prioritizes alerts based on their severity and context, allowing your security teams to focus on the most critical incidents.
XDR vs. Other Security Frameworks
As mentioned, XDR provides an integrated approach, correlating data from multiple sources for holistic detection and automated response. For instance, SIEM (Security Information and Event Management) focuses on log aggregation and analysis; however, it often lacks automated response. EDR (Endpoint Detection and Response), on the other hand, focuses on endpoint-specific detection, while NDR (Network Detection and Response) is dedicated to network traffic analysis.
In the table below, we will compare XDR with SIEM, EDR, and NDR security frameworks.
XDR vs SIEM
| XDR | SIEM |
| Includes automated response actions such as quarantine, remediation, or policy enforcement | Typically involves a lot of manual investigation and correlation by security analysts |
| Proactive in threat hunting with automated responses to incidents | Slow in terms of response time as it focuses more on data collection and analysis than on automated response |
XDR vs EDR
| XDR | EDR |
| Aggregates data from various layers to provide comprehensive threat detection and response | Detects and responds to endpoint-specific threats such as malware or ransomware |
| Provides enhanced visibility and context by correlating data across multiple environments | Primarily analyzes endpoint activity such as process execution, file changes, and network connections |
XDR vs NDR
| XDR | NDR |
| Provides a broader scope for detection and response, including network and non-network events | Primarily concerned with threats that originate or propagate via the network |
| Offers centralized detection, correlation, and response capabilities across all layers | Often used for detecting lateral movement and stealthy attacks within the network |
For comprehensive security, Singularity™ XDR by SentinelOne combines the strengths of all the above systems into a single platform, reducing silos and offering faster, automated response capabilities. You can try the free demo and protect your systems from ever-changing cyber threats.
Implementing XDR in an Organization
Implementing an XDR involves a multi-step process, from assessing your security needs to selecting the right solution. This ensures smooth integration with existing tools. Proper planning and execution can improve your organization’s threat detection, incident response, and overall cybersecurity posture.
Below are the guidelines on the key stages of XDR implementation.
1. Assessing Security Needs and Risks
Before you implement XDR, ensure you conduct a thorough assessment of your organization’s security posture. It involves identifying key assets, potential threats, vulnerabilities, and current detection and response capabilities.
Understanding the specific risks your organization faces will help you define the scope and objectives of the XDR deployment. This ensures that the platform addresses the most critical security challenges.
 2. Selecting the Right XDR Solution
2. Selecting the Right XDR Solution
With numerous XDR solutions available, choosing the right one requires careful evaluation of features, scalability, and vendor reputation. Look for platforms that align well with your security goals and offer compatibility with existing tools.
Additionally, it’s important to consider the vendor’s level of support, innovation roadmap, and how well the solution integrates with your organization’s operational environment.
3. Integration With Existing Security Tools
XDR is designed to enhance visibility by integrating with existing security tools. A smooth integration process is crucial for minimizing disruption and ensuring that data from these tools flows seamlessly into the XDR system.
You should select a vendor that ensures interoperability and allows, if need be, you to reconfigure or upgrade some tools for full compatibility.
4. Staff Training and Skill Development
To successfully implement an XDR that goes beyond technology, your security teams have to train on how to use the new platform effectively. This includes understanding how to interpret the insights generated by XDR, adjusting workflows, and honing incident response strategies.
Continuous learning and upskilling are essential as XDR solutions are gradually evolving. This ensures your staff can leverage the platform to its full potential and respond effectively to threats.
Benefits of XDR Architecture
Here are some key benefits of XDR architecture:
- Improved detection rates: XDR integrates data from various sources, enabling better identification of sophisticated threats through advanced analytics and behavioral insights.
- Faster incident response: Automated response capabilities and streamlined investigation processes allow your security teams to react to and mitigate potential threats on time.
- Reduced alert fatigue: XDR correlates and prioritizes alerts, minimizing noise and allowing teams to focus on critical threats without being overwhelmed by irrelevant notifications.
- Enhanced security posture: By providing a comprehensive view of the threat landscape, XDR helps organizations identify vulnerabilities and adapt their security strategies. This leads to overall improved defenses.
Challenges and Considerations
XDR implementation and maintenance sometimes come with a range of challenges and considerations. The following are some key areas to explore.
1. Data Privacy and Compliance
You already know that XDR platforms collect and analyze vast amounts of data across your networks, endpoints, and applications. Ensuring that such data complies with regional and industry-specific regulations such as GDPR or HIPAA proves critical. Privacy concerns arise when your sensitive data is aggregated and shared across multiple systems.
Therefore, you should consider implementing strong access controls, encryption, and data anonymization practices to avoid breaches and ensure compliance.
2. Integration Complexities
XDR architecture aims to unify data and security alerts from various sources. However, integrating disparate security tools and legacy systems can be challenging. Compatibility issues between existing security infrastructure and the XDR platform can complicate deployment. The practice may lead to delays, increased costs, or incomplete visibility.
Ensuring seamless integration requires careful planning and may involve significant customization or reconfiguration of your existing systems.
3. Cost Implications
Deploying an XDR solution often involves significant financial investment. Beyond direct license costs, you should consider infrastructure upgrades, training for your security teams, and ongoing management expenses.
Balancing your security against the costs is crucial, as an XDR can offer you long-term savings through faster detection and response.
4 Vendor Lock-in
Adopting an XDR platform from a single vendor can create dependencies, potentially undermining flexibility in the future. Vendor lock-in may hinder you from adopting new technology or changing providers without incurring substantial costs.
Your organization should assess the long-term implications of committing to a specific XDR vendor. This ensures you retain the ability to adapt and scale your security architecture over time.
 Final Thoughts
Final Thoughts
XDR architecture represents a transformative leap in cybersecurity, uniting different security layers into a cohesive, intelligent, and proactive defense system. To implement XDR effectively, organizations must prioritize comprehensive integration. This ensures the alignment of security tools and fosters a culture of continuous adaptation to evolving threats.
When done right, XDR not only boosts your threat detection capability but also enables your teams to act swiftly and decisively, thereby turning chaotic data into actionable insights.
Embrace XDR to shift from reactive to proactive defense, thereby building a resilient security posture that can withstand tomorrow’s threats today.
FAQs
1. What is XDR architecture?
XDR is an integrated cybersecurity framework that combines data from various security layers into a unified system to detect, analyze, and respond to threats more effectively.
2. How is XDR different from traditional security solutions like EDR or SIEM?
XDR extends beyond EDR by integrating multiple security layers into a single platform, rather than only monitoring endpoints like EDR. XDR is also unlike SIEM, which collects and correlates logs but doesn’t provide automated response actions.
3. Does XDR require specific hardware or software?
XDR typically operates as a software solution by leveraging your existing security tools, since it does not require specialized hardware. However, it needs proper integration with your current infrastructure to be effective.