You’ve hosted your workloads and data in Azure, enjoying the cloud’s global reach and its borderlessness. But this environment calls for an entirely new approach to security, different from the approach deployed in traditional perimeter environments.
To help you with this, the Azure security architecture offers a wide range of security features, spanning core areas like data protection, compliance management, identity and access management (IAM), and more. However, failure to understand the Azure security architecture can make navigating Azure’s security offerings a major headache.
This guide highlights key components of the Azure security architecture to look out for in 2025, and how these components work together to build resilient well-architected Azure cloud environments. It also digs into some challenges and best practices for your Azure security architecture.
 What is Azure Cloud Security Architecture?
What is Azure Cloud Security Architecture?
Azure security architecture refers to the varied tools, services, security principles, and best practices put together to help Azure users build secure, well-architected workloads in Azure. Fundamentally, it includes identity and access management (IAM), which controls who has access to what, acting as a gatekeeper to sensitive resources. Encryption safeguards data both at rest and in transit, ensuring that, even if intercepted, the data remains inaccessible.
Network security tools, like Azure Firewall and Network Security Groups, create virtual barriers, carefully monitoring and restricting any unauthorized access. Then there’s Azure Security Center, which functions as a constant lookout, detecting vulnerabilities and spotting threats in real time. Meanwhile, compliance management tools ensure that every action aligns with regulatory standards, while automated monitoring and logging provide continuous insights, reinforcing Azure’s security ecosystem. Together, these components form a strategic defense, an architecture that ensures every piece of data remains exactly where it should be—protected.
Need for Azure Security Architecture
Although Azure offers several security tools, vulnerabilities can creep up even in the most secure environments. Recently, a new improper authorization vulnerability, CVE-2024-38194, ranked critical, with a CVSS score of 8.2, was detected in Azure. If exploited, attackers could potentially access your mission-critical Azure workloads through compromised privileged accounts.
A robust cloud security architecture is like an adaptive immune system—constantly analyzing, adjusting, and defending. With it, you can detect and respond to hidden threats. Moreover, cloud configurations are notoriously fluid; they change over time, sometimes without anyone realizing it. Real-time monitoring embedded within the architecture ensures these shifts do not go unnoticed, allowing immediate adjustments to prevent malicious activity.
Also, effective architecture defends against threats like insider activity, data sprawl, and privilege escalation. Insider threats, whether intentional or not, are mitigated through strict access controls and continuous behavior monitoring. Data sprawl—a phenomenon where data disperses unpredictably, becoming harder to secure—is managed with centralized oversight and governance. Privilege escalation is contained by carefully monitoring and controlling access levels, ensuring no unauthorized person has excessive control.
So, the Azure security architecture is essentially a framework of pre-installed, layered controls designed to secure your critical IT assets in Azure and help you comply with data protection standards like GDPR, DORA, PCI DSS, etc. By adopting these controls, you can ensure data integrity and protect your stack from cyberattacks.
Azure Well-Architected Framework
The Azure Well-Architected Framework is a set of tenets provided by Microsoft to help organizations build secure, reliable, and efficient applications. The framework comprises five key operational pillars:
Security
The security pillar guides organizations in designing well-architected workloads using zero-trust and defense-in-depth approaches. Defense in Depth, – involves deploying multiple layers of security, ensuring other defense mechanisms remain intact if an attacker breaches one layer. Zero-Trust, meanwhile, assumes users are untrusted by default, requiring continuous authentication for each access attempt or privileged activity.
The security pillar includes core aspects of cloud security, such as data and secrets protection, IAM, data governance, and network and app security. It also defines what a secure Azure architecture should be: one that is attack-resistant and meets compliance requirements.
Azure offers a wide range of tools to facilitate app security, including Azure Key Vault, Azure Purview, Azure Security Center, and Microsoft Sentinel, among others.
Reliability
In the Azure Well-Architected Framework, reliability is a measure of how resilient your Azure workload is in the face of potential failures. This reliability depends on you implementing best practices like backup, disaster recovery, fault tolerance, and more. The two best native Azure reliability tools are Availability Zones and Azure Site Recovery.
Cost Optimization
Cost optimization is all about balancing cost savings with necessary trade-offs like ensuring the optimal performance, security, and compliance of Azure workloads.
For example, adopting the built-in tools in the Azure security architecture may seem costly in the short term. However, with data breaches reaching an all-time high cost of USD 4.88 million, the long-term ROI from avoiding costly compliance violation fines and lawsuits makes investing in the right security solutions a cost optimization tactic.
Azure Advisor, Azure’s cost management solution, helps enterprises efficiently allocate resources, track utilization, and eliminate idle resources.
Performance Efficiency
Performance efficiency refers to designing workloads in the Azure security architecture for geo-redundancy (when customers are widely dispersed), seamless scalability (to handle traffic spikes), and minimal to no latency (for optimal user experience). To boost performance efficiency, you need Azure’s autoscaling and load-balancing functionalities.
Additionally, Azure Cache for Redis and Content Delivery Network (CDN) services can further enhance efficiency by reducing load times and improving data access speed across global regions.
Operational Excellence
The operational excellence pillar encourages Azure customers to adopt practices like DevOps, observability, automation, and patch/upgrade management. These practices streamline workflows, reduce inconsistencies in DevSecOps processes, and minimize human error. Tools like Azure DevOps and Log Analytics support operational excellence by automating deployments, monitoring system health, and providing actionable insights into workload performance.
Furthermore, Azure Automation and Update Management can help organizations automate routine tasks and maintain compliance, ensuring workloads remain secure, up-to-date, and resilient against operational disruptions.
Adopting the five pillars of the Azure well-architected framework allows you to build secure workloads that align with the core principles of Azure security architecture.
 CNAPP Market Guide
CNAPP Market Guide
Get key insights on the state of the CNAPP market in this Gartner Market Guide for Cloud-Native Application Protection Platforms.
Read GuideComponents of Azure Security Architecture
The Azure security architecture covers a broad range of security components, including:
1. Identity and access management (IAM) in Azure
In Azure, IAM is powered by Microsoft Entra ID, formerly Azure Active Directory (AAD). Microsoft Entra ID is essentially your gatekeeper, helping to set up identities, authenticate access requests, and keep attackers out of your Azure stack. Key offerings of Azure’s IAM solution include:
- Single sign-on (SSO): Azure’s SSO functionality serves as a master key, allowing you access to multiple services in your Azure stack using a single set of credentials. This supports good password hygiene and helps protect your workloads against brute force and credential-stuffing attacks.
- Multi-factor authentication (MFA): Just like the multi-lock safes that require pins, keys, and biometrics to open, Entra ID’s MFA feature adds multiple authentication layers, including username/password pairs, security keys, biometrics, and OTPs. As it is difficult to bypass all layers at a go, this effectively denies attackers with stolen credentials access to your Azure infrastructure.

- Role-based access control (RBAC): Enta ID offers both inherent and custom roles for fine-grained access control. With Entra ID, you can control who has access to what resources, ensure least-privilege access, and monitor user activities.
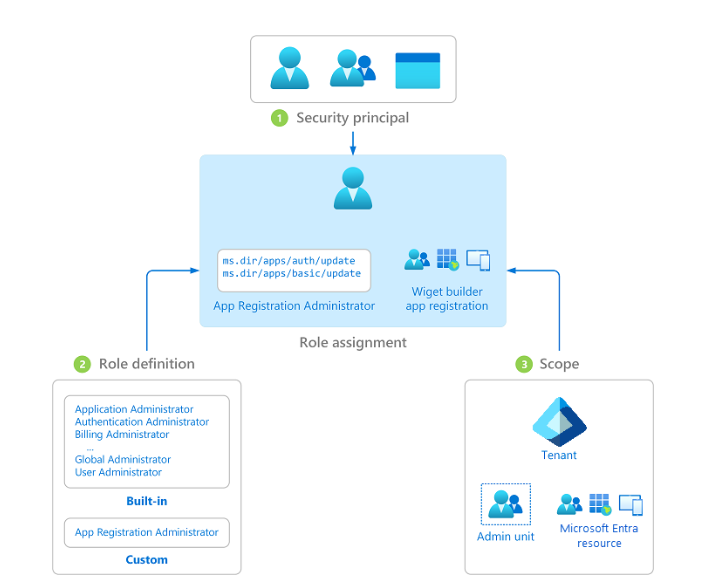
- Conditional access: You can use Entra ID to grant or revoke access and establish access levels based on factors such as user identity, IP location, department, device, or real-time risk detection signals.
2. Network Security in Azure
Network security is an essential part of your Azure security architecture. Azure offers a number of solutions designed to protect enterprise networks from unauthorized access.
Think of Azure Firewall and Network Security Groups (NSGs) as your bouncers, controlling ingress and egress traffic to workloads and virtual networks (VNets) based on predefined rules. Using either solution, you can protect your Azure apps from SQL injection and cross-site scripting attacks.
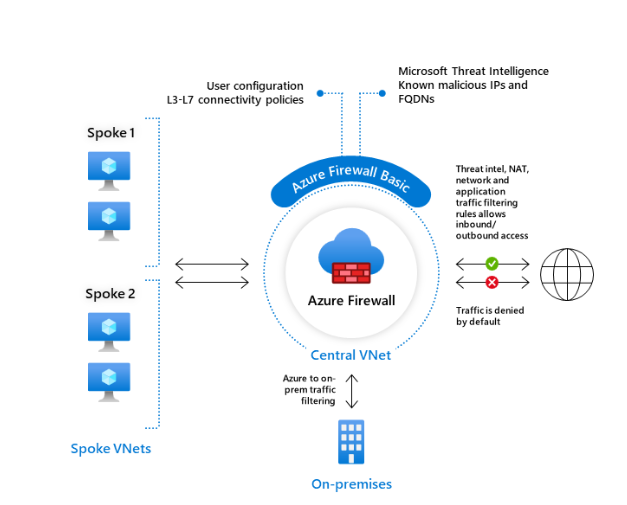
- Azure DDoS Protection protects your Azure apps and services from distributed denial of service (DDoS) attacks. It’s basically your flood control system, designed to prevent malicious traffic surges from overwhelming your systems.
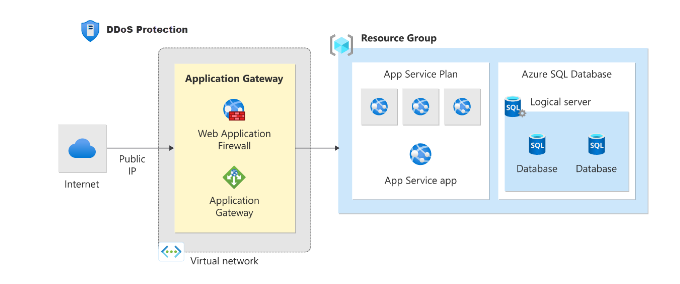
3. Data Protection and Encryption in Azure
Protecting secrets and sensitive data is a core function of Azure’s security architecture. Azure provides a range of tools:
Azure Key Vault stores and manages secrets like encryption keys, certificates, and API tokens, providing developers with an efficient and secure alternative to hardcoding secrets. This prevents unauthorized access to sensitive assets and reduces the risk of data breaches.
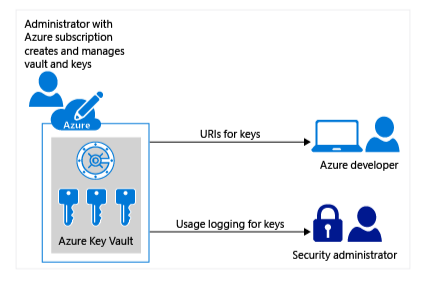
- Azure Disk Encryption (ADE) encrypts Windows and Linux operating systems and data disks using the Windows BitLocker and the Linux DM-Crypt.
4. Application Security in Azure
Azure’s primary web app security solution, Azure Application Gateway, automates geoIP load balancing and traffic routing, working alongside Azure Web Application Firewall (WAF) to protect web applications.
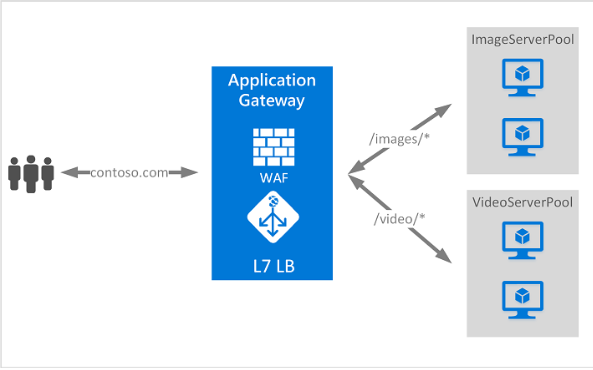
Additionally, Azure App Service includes built-in security features like SSL/TLS encryption, service-to-service authentication, and automated patching to secure apps and data in transit.
5. Monitoring and Threat Detection in Azure
An ideal Azure security architecture is one that implements continuous monitoring to detect and respond to threats in real time. Four relevant Azure-native tools are:
- Microsoft Defender for Cloud, a cloud-native application protection platform (CNAPP) that scans your Azure deployments for vulnerabilities and alerts you in real time.
- Azure Security Center, which is a cloud security posture management solution for Azure workloads, offers actionable remediation steps for vulnerabilities.
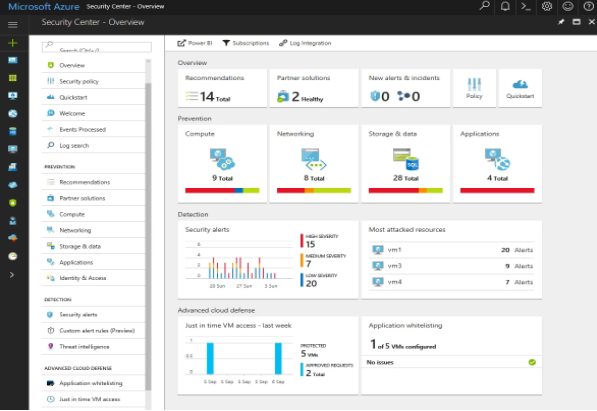
- Microsoft Sentinel, previously known as Azure Sentinel, is a security information and event management (SIEM) tool. Comparable to an automated SOC analyst, Microsoft Sentinel collects and analyzes logs to provide instantaneous insights into usage and access patterns indicative of potential or ongoing breaches.
- Azure Monitor, a diagnostic dashboard that aggregates, analyzes, and alerts on security and performance issues.
6. Governance and Compliance in Azure
Data governance and standards compliance are fundamental to Azure security architecture; they ensure policy consistency and data privacy. Two Azure-native tools for data governance and compliance are:
- Microsoft Purview (formerly Azure Purview), is like a GPS for your Azure workloads. It discovers where your sensitive data is, maps data lineage, and assesses data for non-compliance issues—like lack of encryption or weak access controls.
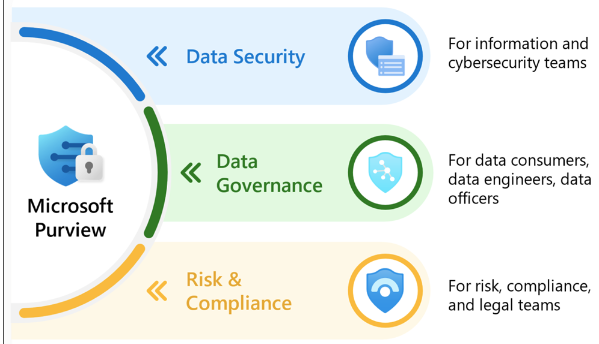
- Azure Policy, which enforces policies for access control, resource provisioning, and more. Azure Policy continuously hunts for compliance failures and can automatically remediate them.
7. Securing DevOps with Azure
An important component of the Azure security architecture is integrating security into each phase of the software development lifecycle (SDLC) through practices. This involves using static application security testing (SAST) and vulnerability management tools across DevOps and Continuous Integration/Continuous Deployment (CI/CD) pipelines.
In Azure, this requires using a series of solutions— including Entra ID—to synchronize directories, Azure DevOps to ship secure code, and a host of others.
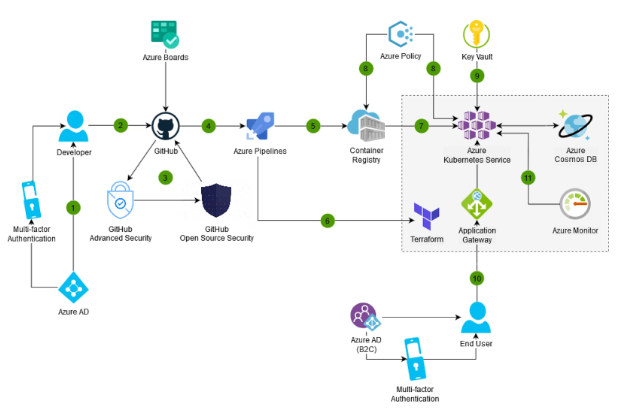
The components of Azure security play a crucial role in overall defense. Learn how Singularity Cloud Workload Security can secure cloud workloads in Azure environments.
Challenges in Implementing Azure Security Architecture
Though Azure offers countless security tools, organizations still face the following challenges when implementing the Azure security architecture.
1. Cloud Misconfigurations
Cloud misconfigurations account for over ver 20% of cyberattacks, often due to the complexity and dynamic nature of cloud environments like Azure. Each misconfiguration, no matter how small, can open a door for unauthorized access or data exposure. To counter this, sophisticated cloud security posture management (CSPM) tools act as vigilant inspectors, identifying potential vulnerabilities, enforcing policies, and continuously monitoring for misconfigurations that might otherwise go unnoticed in Azure’s sprawling architecture.
2. Tool Complexity
Navigating Azure’s extensive suite of security tools can feel like assembling a vast, intricate puzzle. With each tool serving a unique function, keeping track of them without a centralized approach can lead to fractured visibility and fragmented security defenses. This lack of cohesion allows attackers to find hidden vulnerabilities. The solution? Cloud-native application protection platforms (CNAPPs), create a unified security framework, ensuring that each tool operates in concert with the others to seal potential gaps.
3. Over-Permissions
5 out of 10 organizations have excessively privileged accounts. Over time, roles and permissions in Azure accumulate like unchecked clutter. The initial intent may be to grant access quickly, but this unchecked growth leaves critical resources open to abuse or accidental exposure. In fact, half of all organizations experience over-permission issues. Adopting a least-privilege principle and conducting regular access reviews are essential—each review is a meticulous audit to ensure only those who need access have it, minimizing unnecessary risks and creating a more controlled environment.
 CNAPP Buyer’s Guide
CNAPP Buyer’s Guide
Learn everything you need to know about finding the right Cloud-Native Application Protection Platform for your organization.
Read GuideBest Practices for Implementing Azure Security
Here are 7 top Azure security architecture best practices:
- Enable Multi-Factor Authentication (MFA): Consider MFA as an additional layer of verification, allowing only authenticated users to proceed. By demanding more than a simple password, it significantly lowers the risk of unauthorized entry, creating a robust defense against common threats like phishing attempts and brute-force attacks.
- Carefully Manage Secrets: Sensitive assets like tokens and encryption keys are the backbone of security, yet they’re vulnerable if not properly managed. Azure Key Vault is invaluable here, securely storing these secrets away from prying eyes and reducing the risk of accidental exposure.
- Enforce Single Sign-On (SSO): SSO serves as a streamlined entryway, giving users access to multiple applications with a single credential. It promotes stronger password practices by reducing the need for multiple passwords, making it easier to enforce secure access without sacrificing convenience.
- Encrypt Data in Transit and at Rest: Encryption is like a coded language for your data, readable only by those with the key. Encrypting data both in transit and at rest means that, even if intercepted, sensitive information remains incomprehensible to unauthorized parties, protecting its integrity.
- Adopt a Zero-Trust Architecture: In a zero-trust model, no entity—internal or external—is inherently trusted. Every request must be authenticated and validated, creating a secure perimeter around each interaction. This framework limits the potential impact of insider threats and ensures constant verification.
- Grant Least Privilege Access: Following the principle of least privilege is about minimizing potential exposure. Granting users only the permissions they need to do their job reduces the risk of unauthorized access or accidental data leaks. It’s a meticulously controlled environment where access is only a necessity.
- Continuously Monitor for Threats: Continuous monitoring is like having a 24/7 surveillance system for your Azure environment. Real-time tools like Microsoft Sentinel and Azure Security Center offer immediate alerts, catching vulnerabilities early and preventing potential attacks from escalating unnoticed.
Selecting an Azure Security Solution
Despite Azure’s many preconfigured security tools, enterprises still need a comprehensive solution like SentinelOne that combats the common challenges of implementing an Azure security architecture. SentinelOne consolidates Azure security, providing a single point of reference for all your security management tasks.
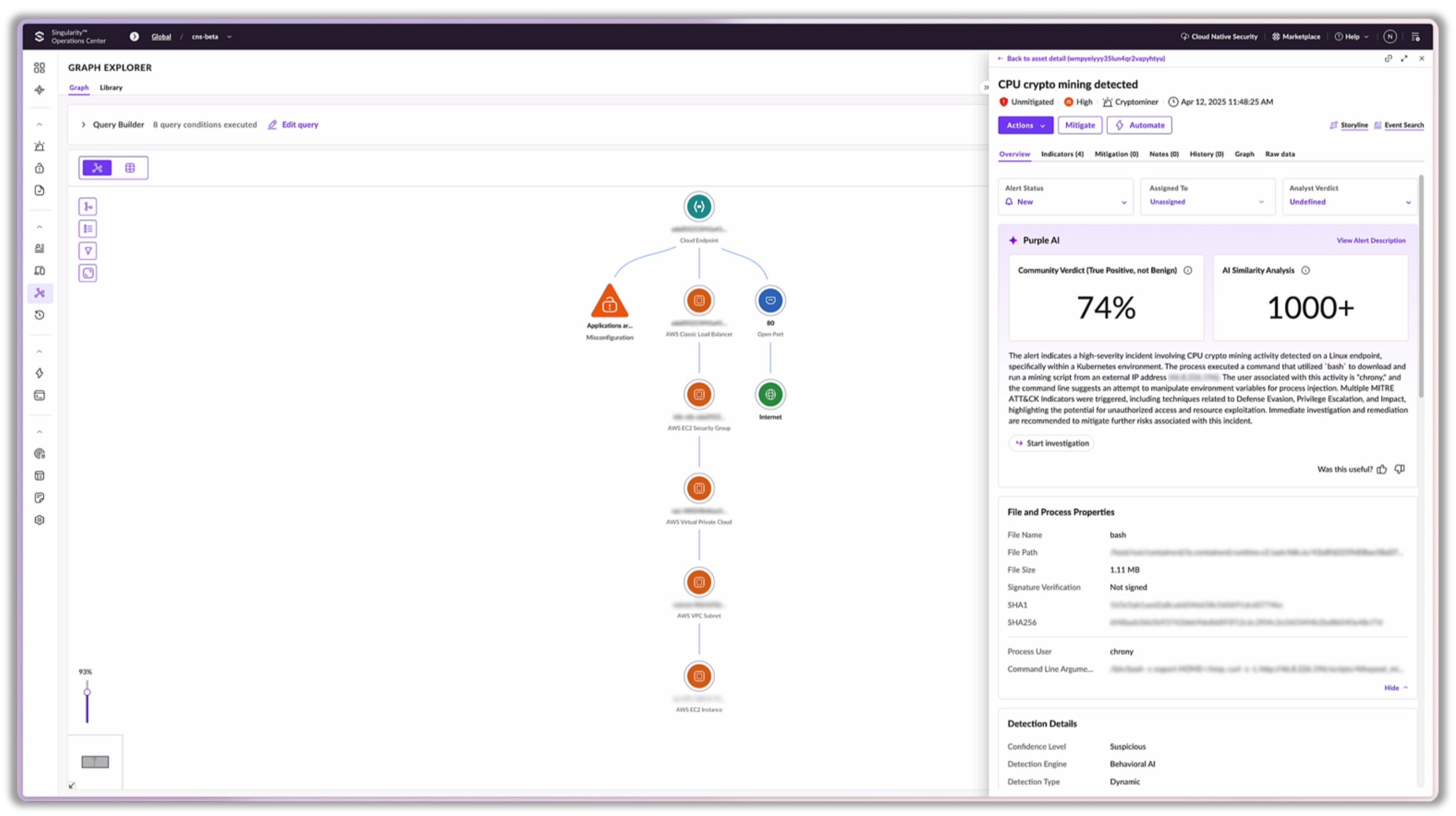 SentinelOne integrates with your Azure stack and DevOps pipelines, and provides deep visibility into your Azure workloads from code to cloud. It also automates threat and misconfiguration detection and remediation. With the SentinelOne CNAPP solution, you can overcome the siloed security challenge of Azure security solutions, and consolidate security posture management across your hybrid and multi-cloud environments.
SentinelOne integrates with your Azure stack and DevOps pipelines, and provides deep visibility into your Azure workloads from code to cloud. It also automates threat and misconfiguration detection and remediation. With the SentinelOne CNAPP solution, you can overcome the siloed security challenge of Azure security solutions, and consolidate security posture management across your hybrid and multi-cloud environments.
SentinelOne’s AI-powered CNAPP gives you Deep Visibility® of your environment. It provides active defense against AI-powered attacks, capabilities to shift security further left, and next-gen investigation and response. Multiple AI-powered detection engines work together to provide machine-speed protection against runtime attacks. SentinelOne provides autonomous threat protection at scale and does holistic root cause and blast radius analysis of affected cloud workloads, infrastructure, and data stores.
Context-aware Purple AI™ provides contextual summaries of alerts, suggested next steps and the option to seamlessly start an in-depth investigation aided by the power of generative and agentic AI – all documented in one investigation notebook. Singularity™ Cloud Security can enforce shift-left security and enable developers to identify vulnerabilities before they reach production with agentless scanning of infrastructure-as-code templates, code repositories, and container registries. It significantly reduces your overall attack surface.
See SentinelOne in Action
Discover how AI-powered cloud security can protect your organization in a one-on-one demo with a SentinelOne product expert.
Get a DemoConclusion
For enterprises hosting workloads and data in the cloud, security must remain paramount. Recognizing this, Azure provides a myriad of tools, principles, and best practices to help organizations implement the Azure security architecture. But navigating these diverse tools, especially in the face of the rapid pace of innovation necessary to stay competitive, can feel overwhelming.
SentinelOne consolidates AI-powered, real-time vulnerability and threat detection across Azure and multi-cloud environments, creating a seamless line of defense, adapting to rapidly evolving threats, and ensuring your infrastructure remains protected without compromise.
Ready to fortify your cloud security? Discover how SentinelOne can safeguard your Azure environment today.
FAQs
Azure facilitates secure access through Entra ID, which enforces SSO, MFA, ZTA, and least privilege.
The top Azure-native monitoring and threat detection solutions are Microsoft Defender for Cloud, Azure Sentinel, Azure Security Center, Azure Monitor, and Log Analytics. However, enterprises looking to consolidate monitoring and threat detection will benefit greatly from SentinelOne’s unified, AI-powered CNAPP solution.

