The Good | China Spy Handed 4-Year Jail Term
Good news for national security this week as the U.S. Department of Justice successfully prosecuted a 59-year-old man for spying on behalf of China. Ping Li, of Wesley Chapel, Florida, was sentenced to four years in prison for conspiring to act as a spy for China’s Ministry of State Security (MSS).
Li, originally from China, had been employed first by Verizon and later Infosys and admitted to sharing sensitive information about cybersecurity, training materials, and the SolarWinds cyberattack. Using anonymous Gmail and Yahoo! email accounts, the spy also shared information about Chinese dissidents, Falun Gong members, and U.S.-based NGOs.
It is believed Li was engaged in espionage activities for MSS, the PRC’s unit for civilian intelligence collection, for at least a decade, beginning around 2012. In addition to his prison sentence, Li received a $250,000 fine and three years of supervised release.
Florida Telecommunications and Information Technology Worker Sentenced for Conspiring to Act as Agent of Chinese Government
🔗: https://t.co/99aMVkTlQs pic.twitter.com/cfPbrFRfMx
— National Security Division, U.S. Dept of Justice (@DOJNatSec) November 25, 2024
The case brought by the DoJ is part of broader U.S. efforts to counter Chinese espionage. Recently, Shujun Wang, another covert Chinese agent, was convicted for infiltrating a New York-based pro-democracy group while secretly reporting to the MSS.
According to a report, Chinese espionage has been linked to over 55 cases across 20 U.S. states, involving military secrets, trade theft, and repression of dissidents. Between 2000 and 2023, 224 incidents of Chinese espionage were reported, including the theft of sensitive military information and trade secrets as well as repression of Chinese dissidents.
The Bad | Cloud Phishing Campaign Targets OneDrive Credentials
A sophisticated operation designed to steal OneDrive credentials was detailed by researchers this week, highlighting the increased interest of cybercriminals in attacking enterprise cloud resources. Dubbed “Beluga”, the phishing campaign uses tailored email attachments and a fake OneDrive login page pre-filled with the target’s email address and company logo.
Researchers say that when recipients open the attached .htm file, they are presented with a page prompting them to view a fake PDF entitled “Protected Document 043.pdf”. Clicking the button labelled “VIEW DOCUMENT” leads to a fake login form. The email field is pre-populated and uneditable, while the password field always returns an error no matter what is entered, a trick scammers often use to get victims to input the password multiple times.
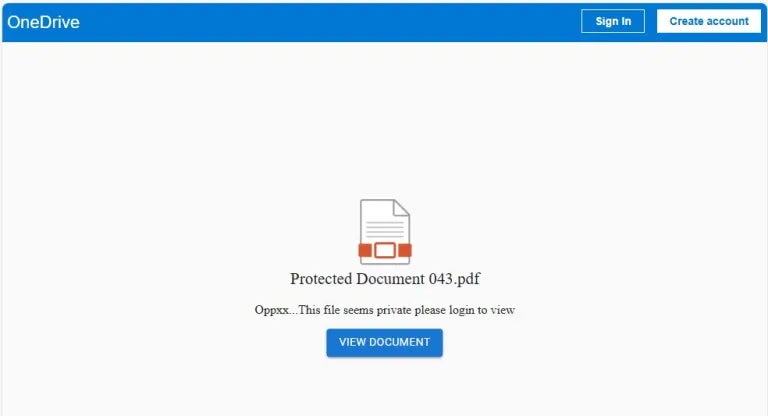
Behind the scenes, the credentials entered are sent via HTTPS to a Telegram bot, which also receives the victim’s email and IP address. Telegram bots are increasingly used by cybercriminals for credential harvesting and campaign management due to their ease of use and automation capabilities.
Compromised OneDrive accounts pose significant risks to organizations as they are routinely used to store sensitive information. Due to their ability to synchronize with files on local devices, and to perform operations such as deletion and file encryption, they can also act as a vector for cloud-based ransomware attacks.
The Ugly | Russian APT Exploits Firefox and Windows Zero Days
Researchers detailed this week how a Russia-aligned threat actor group widely known as RomCom (aka Storm-0978, Tropical Scorpius, UNC2596) has been exploiting a vulnerability in Mozilla products, including its popular Firefox browser, to infect Windows users with malware. The exploit chain includes leveraging a privilege escalation bug in Microsoft’s operating system. The bugs, now patched, were unknown to both vendors at the initial time of exploitation.
CVE-2024-9680 is a critical vulnerability in Firefox, Thunderbird and the Tor browser which allows the execution of code within the browser when a user visits a malicious website. CVE‑2024‑49039 is a bug in Windows 10, 11 and Server releases that allows such code to escape the browser’s sandbox.
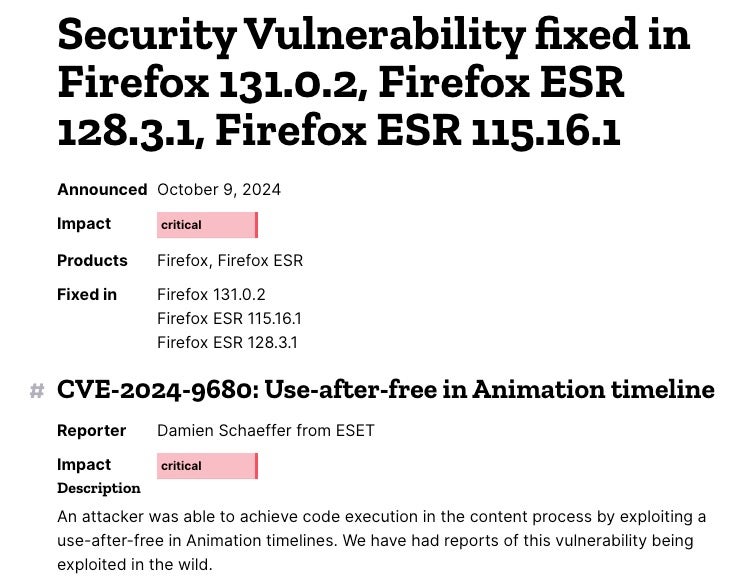
According to researchers at ESET, the Russia-aligned APT chained the two vulnerabilities together to infect visitors to actor-controlled websites with the RomCom backdoor. Victims only needed to land on the malicious webpages to become infected, with no further user interaction required.
While it is not clear how links to the malicious websites were distributed to targets, it is thought that the campaign was widespread and involved fake servers of legitimate websites redirecting users to deliver the exploit. The researchers say targets were mostly in Europe and North America.
The bugs were patched by Mozilla and Microsoft on October 9th and November 12th, respectively, and users are urged to update both products without delay.


