The Good | Chrome & Firefox Release Patches for Several High-Severity Vulnerabilities
This week, Google and Mozilla released a new round of critical updates for Chrome 133 and Firefox 125, patching several high-severity memory safety vulnerabilities. These updates are available for Windows, macOS, and Linux, all addressing flaws that could allow attackers to execute arbitrary code.

Chrome updates fixed two high-severity issues. The first, CVE-2025-0999, is a heap buffer overflow vulnerability in the V8 JavaScript engine that, in the hands of an attacker, could enable remote code execution (RCE). This vulnerability happens when a program writes more data to a dynamically allocated memory buffer than it can hold, which then potentially allows attackers to overwrite adjacent memory and execute arbitrary code.
The second, CVE-2025-1426, is another heap buffer overflow in Chrome’s graphics processing unit (GPU) component. Finally, a medium-severity use-after-free bug (CVE-2025-1006) in the Network component was patched. Use-after-free bugs occur when a program continues to use a memory pointer after it has been freed, giving attackers a potential shot at executing arbitrary code or causing crashes by accessing invalid memory. To date, Google has not disclosed active exploitation of these flaws.
Firefox 135.0.1 addresses high-severity memory safety issues tracked as CVE-2025-1414. Mozilla warns that these vulnerabilities could lead to code execution if exploited. The bugs in this release showed evidence of memory corruption, increasing the risk of arbitrary code execution if exploited by a threat actor.
Attackers frequently exploit known vulnerabilities, making regular patching a critical process in maintaining good cybersecurity hygiene. Delayed updates increase the risk of compromise, allowing cybercriminals to execute malware, steal data, or gain control over systems. Implementing automated patch management strategies and vulnerability assessments ensures organizations can complete timely updates.
The Bad | Latest Version of ‘Darcula’ PhaaS Now Auto-Generates Phishing Kits for All Brands
The DIY scene continues to grow in the cybercriminal space with phishing-as-a-service (PhaaS) platforms like Darcula offering phishing kit generators that can create spoofed pages of any brand. Darcula Suite, the third major iteration of the service, has now removed previous targeting limitations and lowered technical barriers with a user-friendly admin panel, IP and bot filtering, automated credit card theft, and campaign performance management.
Darcula emerged first as a large-scale phishing operation, leveraging 20,000 domains to impersonate brands and steal credentials from mobile users across more than 100 countries. Even before the official release of Darcula 3.0, cybercriminals were already testing its capabilities, as indicated by a significant rise in usage metrics. Security researchers tracking this latest release have confirmed the legitimacy of these new features.
The standout feature of Darcula Suite is its automated phishing site creation, where attackers provide a brand URL and the platform clones the site using a tool called Puppeteer to replicate its original design and functionality. Scammers are able to modify login fields, payment forms, and security prompts to steal user data. Once configured, the phishing site is packaged into a “.cat-page” bundle for deployment via the Darcula admin panel.
Additional features in Darcula 3.0 also include advanced anti-detection techniques, a redesigned admin dashboard with real-time credential logging, and tools to convert stolen credit card data into virtual cards for use in digital wallets. Though cyber defenders have blocked almost 100,000 Darcula 2.0 domains and thousands of its associated phishing sites, new iterations like Darcula Suite and other increasingly sophisticated PhaaS platforms will keep driving phishing volumes higher, making detection and prevention more difficult.
The Ugly | Russia-Linked Actors Exploit Signal’s ‘Linked Devices’ for Phishing Campaigns
Though Signal quickly rose in popularity for its strong encryption, privacy-focused policies, and minimal data collection, it has caught the attention of threat actors, particularly state-backed attackers, who are developing phishing tactics to hijack notable accounts.
A new report finds an uptick in threat actors leveraging Cybercrime-as-a-Service (CaaS) tactics to exploit legitimate app features for cyber espionage. It highlights a new phishing campaign where Russian state-aligned hackers abuse Signal’s Linked Devices feature to gain unauthorized access.
Instead of compromising devices directly, the attackers trick their targets into scanning malicious QR codes, which sync their Signal messages to attacker-controlled devices. These phishing operations vary by target type; some impersonate Signal group invites, while others masquerade as official instructions provided by the messaging app itself. Many of these attacks involve highly tailored phishing pages that are specially-crafted to the victims’ interests.
At the same time, Russia-linked threat group, Sandworm (aka APT44), has been observed using this method to access Signal accounts on devices captured on the battlefield. It also appears in activity clusters attributed to UNC5792 that modified legitimate Signal group invite links and redirected users to attacker-controlled infrastructure that secretly links their accounts to malicious devices. UNC4221, another Russia-nexus actor, specifically targeted Ukrainian military personnel using phishing kits disguised as Kropyva artillery guidance software (see below).
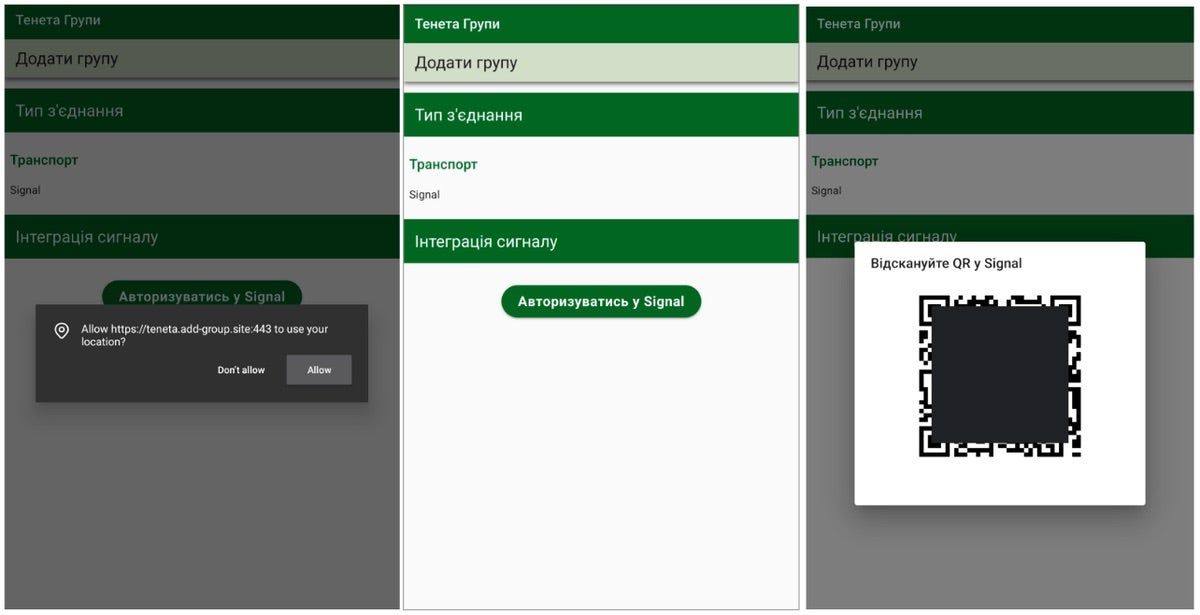
To mitigate risk, Signal users should update to the latest version, regularly audit any linked devices, stay cautious of unknown QR codes, enable two-factor authentication, and use strong screen lock passwords.


