The Good | Police Arrest Data Thief & Gain Insight into Black Basta Via Leaked Chats
Law enforcement officers in Thailand have arrested an individual linked to the leaking of stolen data from over 90 organizations globally. The suspect, a 39-year-old man named Chia, stands accused of exfiltrating over 13TB of data since 2020.
Chia, who also used the online aliases ALTDOS, DESORDEN, GHOSTR and 0mid16B, allegedly targeted companies in Asia-Pacific, Europe, and North America, largely using SQL injection and vulnerable remote desktop protocol (RDP) servers to deploy Cobalt Strike. Rather than leaking data on dark web forums, authorities say he pressured victims by notifying media and regulators to maximize the threat of reputational and financial damage.

The extortion tactics also included directly reaching out to the customers of his victims and, in rare cases, encrypting their databases. Chia was arrested in Bangkok through a joint operation between Thai and Singaporean police with assistance from Group-IB. Since then, he has admitted guilt and now faces multiple cybercrime charges.
Black Basta ransomware gang is the latest criminal outfit to have their internal chat logs leaked, exposing tactics, members, and details of internal conflicts. Active since April 2022, it has built up a worth of $107 million BTC through double-extorting at least 500 victims.
The leaked chats, reminiscent of those that presaged the demise of the Conti ransomware gang, offer a peek into the instability within Black Basta with key members defecting to CACTUS and Akira ransomware operations. The logs revealed that the groups’ primary attack vectors centered around SMB misconfigurations, exposed RDP servers, and the use of malware droppers for initial access.
These kinds of leaks provide the cybersecurity community with intelligence on adversarial structures and strategies, helping experts develop more tailored countermeasures. In cases like Black Basta, the exposure of internal conflicts can also disrupt their activities and support law enforcement in identifying key members.
The Bad | ‘Termite’ Ransomware Attackers Leak Fertility Patients’ Data on Dark Web
One of Australia’s largest fertility service providers, Genea, has confirmed the theft and leak of sensitive patient data following a cyberattack in late January. Genea operates 22 fertility clinics and offers a wide range of services, making up over 80% of the industry’s total revenue in the country alongside just two other companies. This week, the attack was officially attributed to the Termite ransomware group.
Like other ransomware groups, Termite engages in data theft, extortion, and encryption attacks. Termite operations have been active since October 2024 and it has tucked at least 18 victims under its belt since then. They use a variant of the Babuk encryptor, though researchers believe their malware is still in development due to coding flaws.
In the latest attack on Genea, Termite operators claim to have stolen 700GB of data, including full names, addresses, contact information, emergency contacts, personal health details, and medical histories and schedules of affected patients. Court orders reveal that the threat actors exploited a Citrix server to gain access to critical systems – the primary file server, domain controller, and patient management system.
🚨Cyberattack Alert ‼️
🇦🇺Australia – Genea
Termite hacking group claims responsibility for the cyberattack on Genea. According to the post, 700 GB of confidential and personal client data were exfiltrated.
Genea, one of Australia’s largest IVF providers, recently disclosed… pic.twitter.com/HIpRrXC5L8
— HackManac (@H4ckManac) February 26, 2025
Two weeks later, they exfiltrated 940.7GB of data to a DigitalOcean cloud server. Genea has stated that financial details were not affected and are working with the Australian Cyber Security Centre (ACSC) and the Office of the Australian Information Commissioner (OAIC) to continue investigations and prevent data distribution.
Patients are advised to watch for signs of identity theft scams and to be extra cautious of unsolicited messages, particularly those trying to exploit personal and financial information. To address the risk of potential identity theft, Genea is offering resources like IDCARE to provide free support to help impacted individuals.
The Ugly | ‘Ghostwriter’ Campaign Targets Belarusian Opposition & Ukrainian Government
SentinelLABS has exposed a months-long campaign targeting Belarusian-based opposition activists and Ukrainian military and government organizations with malware-laced Excel documents. The campaign aligns with the interest of Belarus and its closest ally, Russia, and aims to spread anti-NATO narratives. The researchers assess the cluster of activity is an extension of the long-running Ghostwriter campaign, active since 2016.
Ghostwriter tactics involve Macropack-obfuscated Visual Basic Application (VBA) macros and .NET downloaders obfuscated with ConfuserEx. Based on previous research, the Ghostwriter threat actor has a history of blending hacking with information manipulation, to target European entities. Recent attacks maintain this approach, leveraging Excel-based malware to infiltrate the Ukrainian military and government networks. PicassoLoader payloads, linked exclusively to Ghostwriter, have been observed deployed in cyber attacks against Ukraine and Poland.
An attack observed by the SentinelLABS team began with a Google Drive-hosted RAR archive from an account named “Vladimir Nikiforech”. The RAR file contained a malicious Excel file that, when opened, executes an obfuscated VBA macro which in turn deploys a simplified version of PicassoLoader malware.
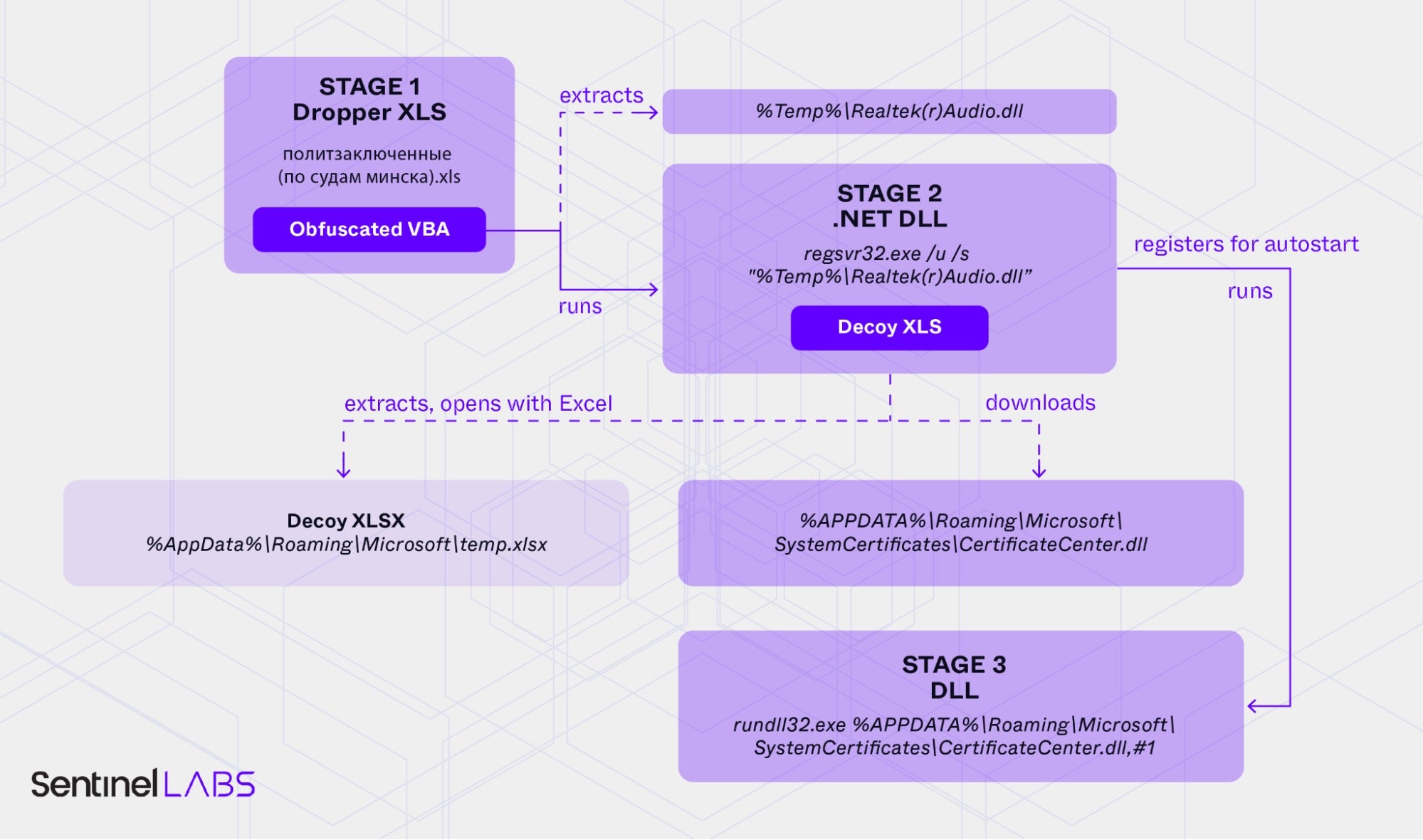
Victims see a decoy document while the malware is silently installed. Ukraine-themed lures then deliver second-stage malware hidden in a JPG image while another method deploys a .NET DLL named LibCMD, which executes further commands through cmd.exe.
Although Belarus has avoided direct military involvement in the war on Ukraine, the latest cluster of Ghostwriter activity reflects Belarusian-linked cyber espionage efforts against domestic opposition and Ukrainian targets. As cyber warfare escalates in many parts of the world, organizations can stay vigilant by collaborating with security experts to mitigate evolving threats.



