Encryption is a critical partner to organizational security. Except when it isn’t!
It’s clear that encryption has a key role in ensuring that organizational data stays invisible and protected. Technology giants such as Google are pushing us towards encryption – whether it’s via prioritizing search results[1] or flagging unencrypted sites as unsafe[2]. WordPress, the most widely used content management system on the Web, is also ensuring that every site built using WordPress will use HTTPS as the default[3]. The average volume of encrypted traffic has now crossed the 50% mark – in other words more traffic on the network is now encrypted than is clear-text.
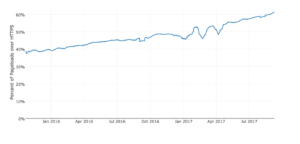 Figure 1: Growth in encrypted web traffic (Source: https://letsencrypt.org/stats/ )
Figure 1: Growth in encrypted web traffic (Source: https://letsencrypt.org/stats/ )
What does that mean in the context of security? This is obviously great news since organizations are taking security more seriously. But attackers, as we all know, are constantly challenging our ability to innovate – always looking for ways to hide as they infiltrate organizations. What better way to hide than within encrypted traffic – since it renders security solutions that rely on deep packet inspection in the data pathways blind to the traffic!
Attacks such as Dridex and Gootkit rely on this invisibility cloak to conceal their movements and exfiltrate information. Dell pointed out in its report[4] that this tactic was used in a crafty malvertising campaign in 2015 to expose as many as 900 million Yahoo users to malware by redirecting them to a site that was infected by the Angler exploit kit!
Protecting against these hidden attacks is going to be increasingly crucial for organizations to safeguard their information assets. Gartner predicts that more than 80 percent of enterprise web traffic will be encrypted by 2019[5] . Visibility into the encrypted traffic is the first step towards achieving security. But you’ve got to be able to achieve that without complicating your networks or impacting your user-experience. Complicated deployments will increase the operational overheads and cause users to undermine security.
SentinelOne Deep Visibility can help you achieve the rich visibility and automate your threat protection, without the performance overheads. Click here to learn more about SentinelOne Deep Visibility.
Join us for a webinar with SentinelOne CEO, Tomer Weingarten, on September 20th, 2017 to learn how SentinelOne can help you address encrypted threats.
[1] https://thenextweb.com/google/2015/12/17/unsecured-websites-are-about-to-get-hammered-in-googles-search-ranking/
[2] https://motherboard.vice.com/en_us/article/xygdxq/google-will-soon-shame-all-websites-that-are-unencrypted-chrome-https
[3] https://thenextweb.com/insider/2016/04/08/wordpress-rolls-encrypted-https-standard/#.tnw_XrLtIUDG
[4] http://www.dell.com/learn/us/en/uscorp1/press-releases/2016-02-22-annual-threat-report-details-the-cybercrime-trends
[5] Security Leaders Must Address Threats From Rising SSL Traffic

