We’re happy to announce SentinelOne 2.5/Bahamas is now available including updates such as Deep Visibility, Insights Reporting, improved prevention, detection, and response, and many more features, fixes, and enhancements. Let’s go over the most significant changes.
Deep Visibility
The new network is no longer defined by a perimeter. Users may be anywhere at any time, which introduces a new challenge for the sysadmin. Deep Visibility allows for full IOC search on all endpoint and network activities and provides a rich environment for threat hunting that includes powerful filters as well as the ability to take containment actions. It also monitors traffic at the end of the tunnel, which allows an unprecedented tap into all traffic without the need to decrypt or interfere with the data transport. This allows the engine to stay hidden from attacker evasions while also minimizing user-experience impact.
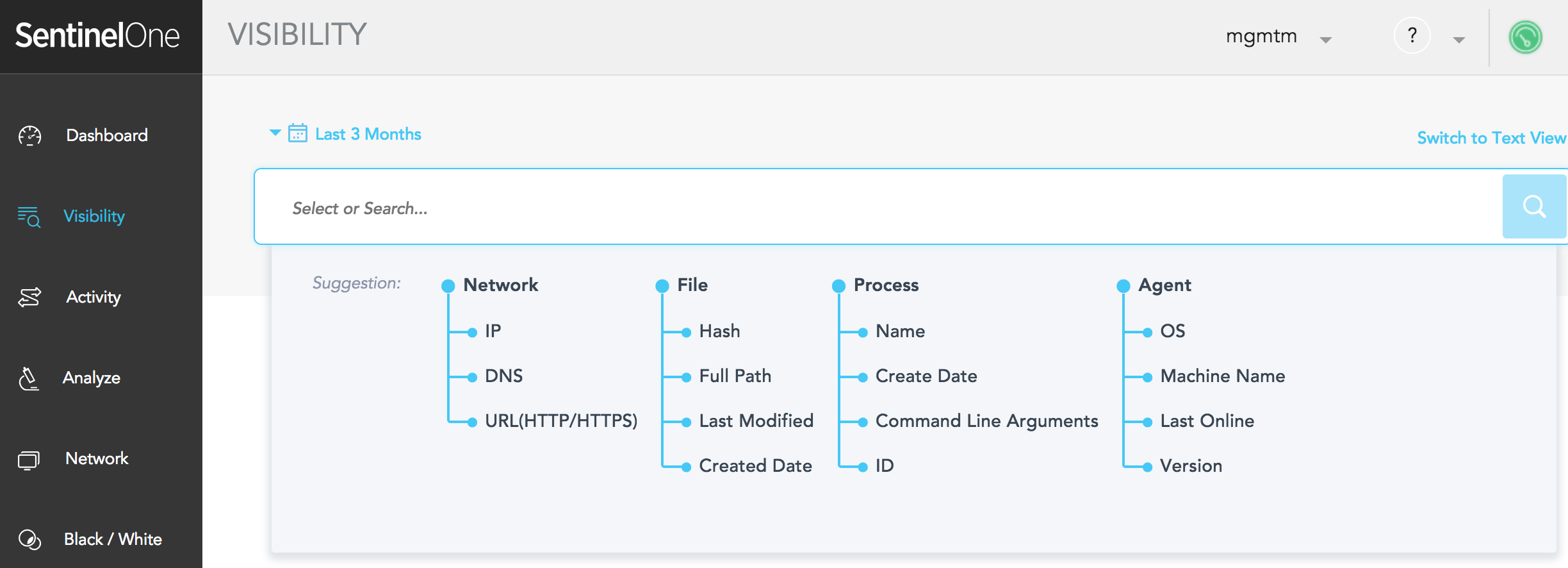
Insights Reporting
Different customers may want to see different items in their reports, but everyone wants information that easy to digest and act upon. Insight Reports lets you make data-driven decisions to improve your team’s security and performance. We also added the option to create new insight reports without the need for a release, so if you want us to build a custom report for you, just ask!
These Insight Reports are already available:
- Executive Insights
- Executive Insights by Group
- Threat Insights
- Mitigation and Response Insights
- Application Insights
You can read all about it in our Feature Spotlight.
Mimikatz – Password Masking
Mimikatz is a tool developed by Benjamin Delpy that is used to gather credential data from Windows systems. There are many ways in which an attacker can utilize it. Although some security products block it by its hash or name, this is highly ineffective since anyone can compile Mimikatz as new versions making its hash unknown to reputation services. The SentinelOne agent prevents this by identifying and blocking it from reading the device passwords. In addition to other built-in protections, we have added a mechanism that does not allow the reading of passwords, regardless of the policy settings.
You can see a short demo below:
New Exclusions option – “Do Not Monitor”
The SentinelOne platform has multiple exclusion options including hash, path, file type, certificate or browser type. These are designed to allow the administrator flexibility and options in responding to any case of miss-classification of benign files or activity. However, the agent still continues monitoring every activity that happens on the endpoint, at all times.
There are some special cases where one may want to stop this monitoring of a certain path or files such as to resolve interoperability or performance issues with specific files or processes.
For example:
- An endpoint security product injects code into processes and interferes with SentinelOne processes.
- An application such as Microsoft Exchange generates many events and significantly impacts performance on the endpoint (high CPU, memory usage, or disk input/output).
To resolve these situations, you can now create “Do Not Monitor” exclusions to exclude the paths and folders necessary for your mission-critical applications.
More improvements starting in 2.5/Bahamas
- Performance improvements (cross-platform)
- Full Disk Scan efficacy
- Stronger password requirements for Management Console users.
What’s next?
Our team is already working on the next release, building comprehensive multi-tenancy and RBAC capabilities. On the agent side, we are working on new innovative detection. Our next version will include improved deployment, performance, and more detection indicators for a better understanding of detection reasons.
Stay tuned!


