What Happened?
It was published on June 12th that security firm Okta unveiled a code signing vulnerability in macOS that revolves around validation of universal/FAT binaries. An attack exploiting this vulnerability may give an attacker the ability to make an improperly or weakly signed binary look like a signed binary with a valid certificate chain whose root is an Apple root certificate. These consequences are implied by the title that was given to the research: “I can be Apple, and so can you”.
Is SentinelOne Vulnerable?
SentinelOne confirms we are not vulnerable to this evasion. We have closely examined the details of this vulnerability. We have extensively verified that trust validations performed by the agent are not affected or fooled in any manner by this vulnerability. This takeaway is applicable for all supported agent versions.
We would also like to thank Okta for providing us in advance the details of the vulnerability and disclosing their findings responsibly.
Are other vendors vulnerable?
Yes, it’s believed that multiple other vendors are affected including other security firms such as Carbon Black (CVE-2018-10407), F-Secure (CVE-2018-10403) VirusTotal (CVE-2018-10408), Little Snitch (CVE-2018-10470), Facebook’s OSQuery forensic tool (CVE-2018-6336) and Google Santa and molcodesignchecker tools (CVE-2018-6336). For a full, comprehensive and up to date list please visit Okta’s blog post. Updates have already been released by multiple vendors before the disclosure by Okta.
How can I check if a binary uses this evasion technique?
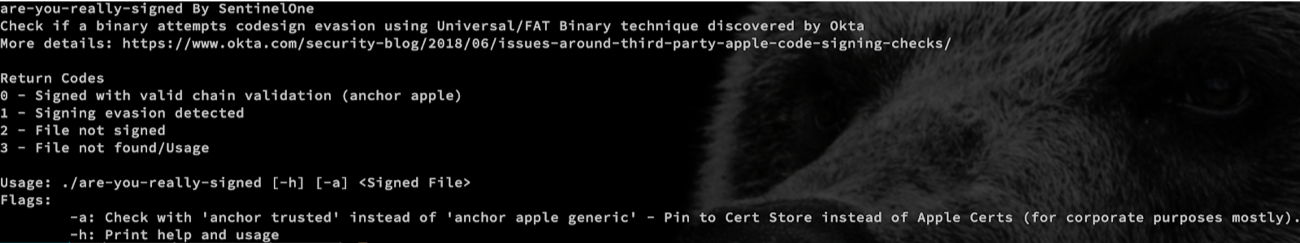
SentinelOne has released an open-source tool called are-you-really-signed which allows you to detect if a signed binary uses this evasion technique.
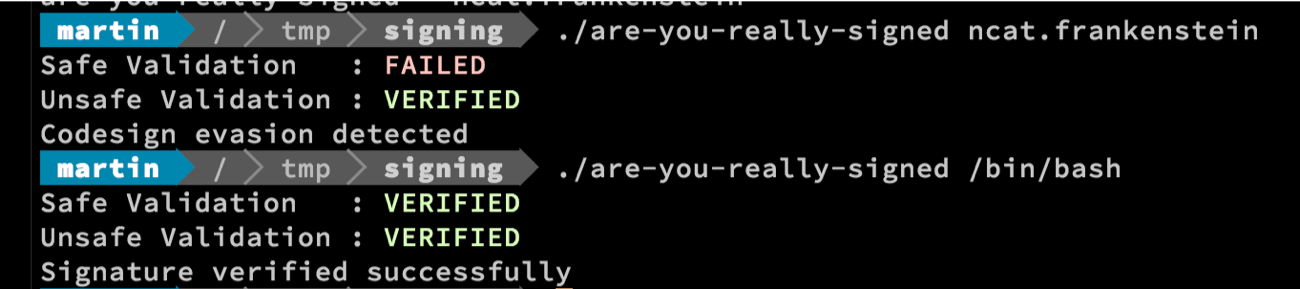
You can also easily integrate this tool with existing distribution solutions in your organization such as JAMF. The tool reports consistent and well-documented return values. Please refer to the documentation for more information.
Stay safe!



