
Amid all last week’s cybersecurity bad news, there was at least one bright spot for the security world to cheer about. On Thursday, Europol announced that they had dismantled the criminal network behind the GozNym banking malware, which has been aggressively targeting businesses and financial institutions in multiple countries. According to Europol, a botnet of some 41000 infected computers was using the GozNym malware to siphon up to $100 million from its unsuspecting victims.

What is GozNym Malware?
GozNym is a hybrid creation specifically coded to, among other things, avoid detection by legacy AV solutions. The gang had combined the Nymaim malware, a first stage loader with persistence capabilities, with a second-stage infection containing a version of the Gozi ISFB banking trojan, hence the name GozNym.
Nymaim has been around for several years but is notable for its ability to avoid security solutions. As previous researchers have revealed, Nymaim checks for running processes that belong to certain AV vendor products.
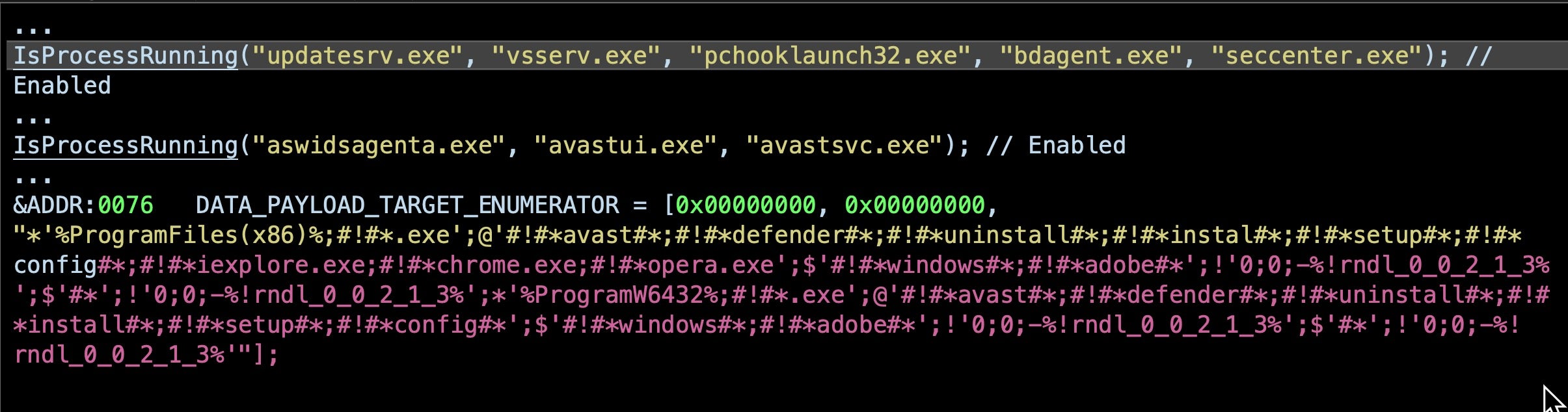
Although Nymaim was initially used as a dropper for ransomware, it has become increasingly associated with banking malware since around 2015. It was first combined with Gozi as a second stage payload in early 2016.
The Gozi banking trojan, aka Ursnif, is an established malware whose source code has been leaked and analyzed several times over the past few years. Leaks allowed the GozNym gang to cherrypick its most useful methodologies. Among those are the abilities to install an MBR (Master Boot Record) rootkit and to generate a custom list of C2 servers using its own Domain Generation Algorithms (DGA).
However, the primary engine underlying GozNym and related variants such as Dreambot, IAP and PowerSniff, is ISFB – a dynamic link library (DLL) designed to analyze and modify HTTP traffic on the victim’s computer. It is this component that allows the criminals to hijack the user’s banking credentials through its ability to inject and manipulate a browser’s web sessions.
Gozi ISFB also supports various plugins that are traded in underground marketplaces and which can give it a variety of capabilities, such as stealing emails and passwords.
The GozNym Criminal Network
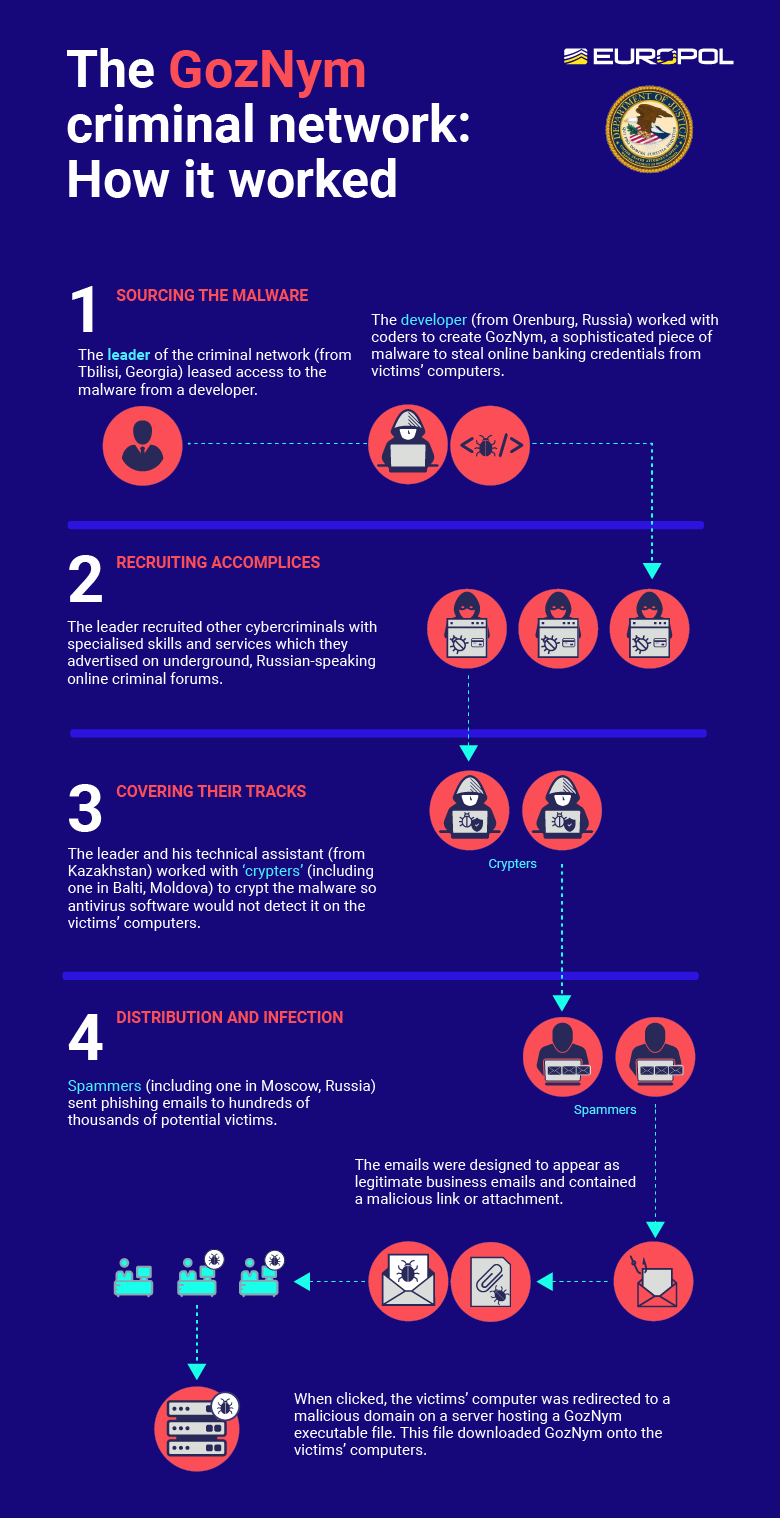
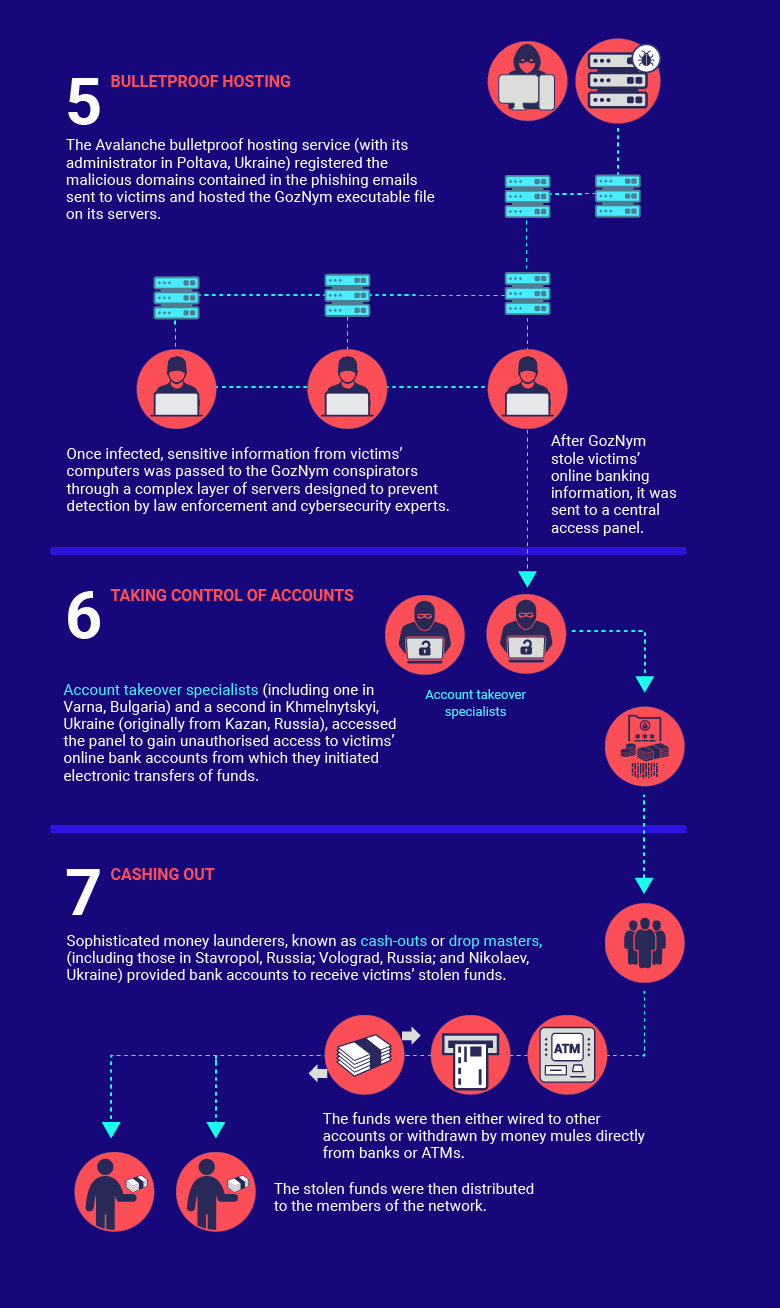
The criminal network behind GozNym was a sophisticated setup, Europol reported, spanning four East European countries and orchestrated through underground, Russian-speaking online criminal forums.
Spammers were employed to create and send hundreds of thousands of phishing emails. The emails, designed to look like legitimate business correspondence, encouraged the recipient to click on a malicious link or file attachment. Word.doc attachments with encrypted VBA macros are, surprisingly, still an effective technique. If the social engineering trick worked, the victim’s machine was redirected to a server that dropped the GozNym malware.
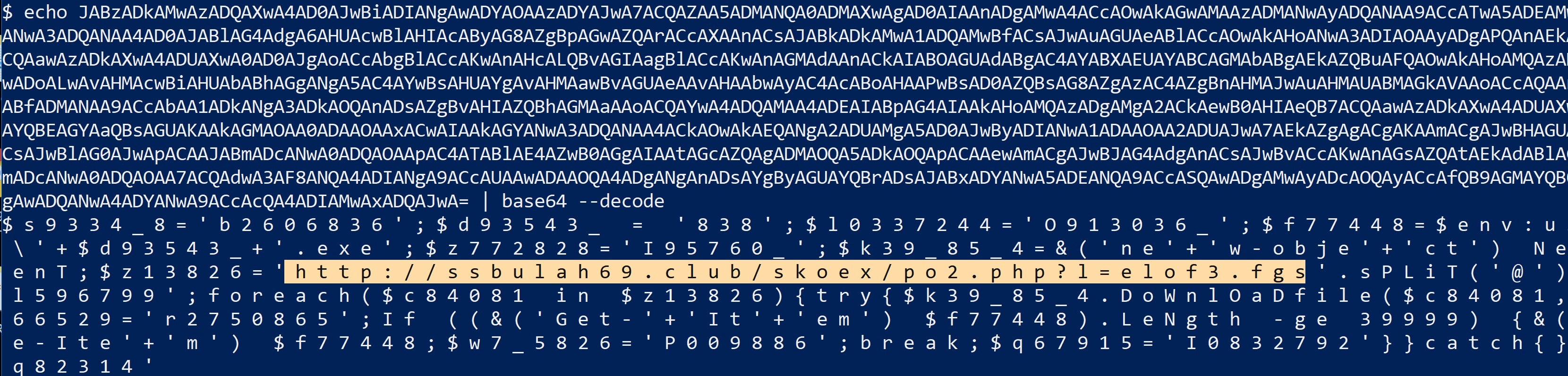
The purpose of the GozNym malware is to capture victims’ banking login credentials and deliver these to the gang, who would then use the captured credentials to fraudulently gain access to victims’ accounts. The stolen funds were then laundered through U.S and other foreign bank accounts controlled by the criminals.
The gang’s complex operation required many layers of enterprising criminals tasked with different duties.
The first stage primarily involved two people, the leader of the criminal network and a developer. Other cybercriminals were recruited to provide specialist services and skills, including coding. In order to cover their tracks, crypters were used to improve the malware’s ability to evade AV solutions. The gang also employed spammers to create mass email phishing campaigns to lure in potential victims. Another layer in the network involved the Avalanche hosting service, which was used to register malicious domains and host the malware. The web of criminals involved spread further to include account takeover specialists who managed the victims’ hijacked online banking accounts and initiated electronic transfers of funds. Finally, money launderers were used to provide bank accounts that received the victims’ stolen funds.
Is That the End of GozNym?
While the good news is that the actors behind GozNym have been unmasked, unfortunately they have not all been apprehended. The source code and methodology behind GozNym’s creation is at least partially available (it is not currently known if the Nymaim source code has been leaked), and there is clear evidence of cybercrime-as-a-service being an active business model on the Dark Net and elsewhere.
Defenders should realize also that GozNym is only part of a family of related malwares that have a long history and complex relationships:
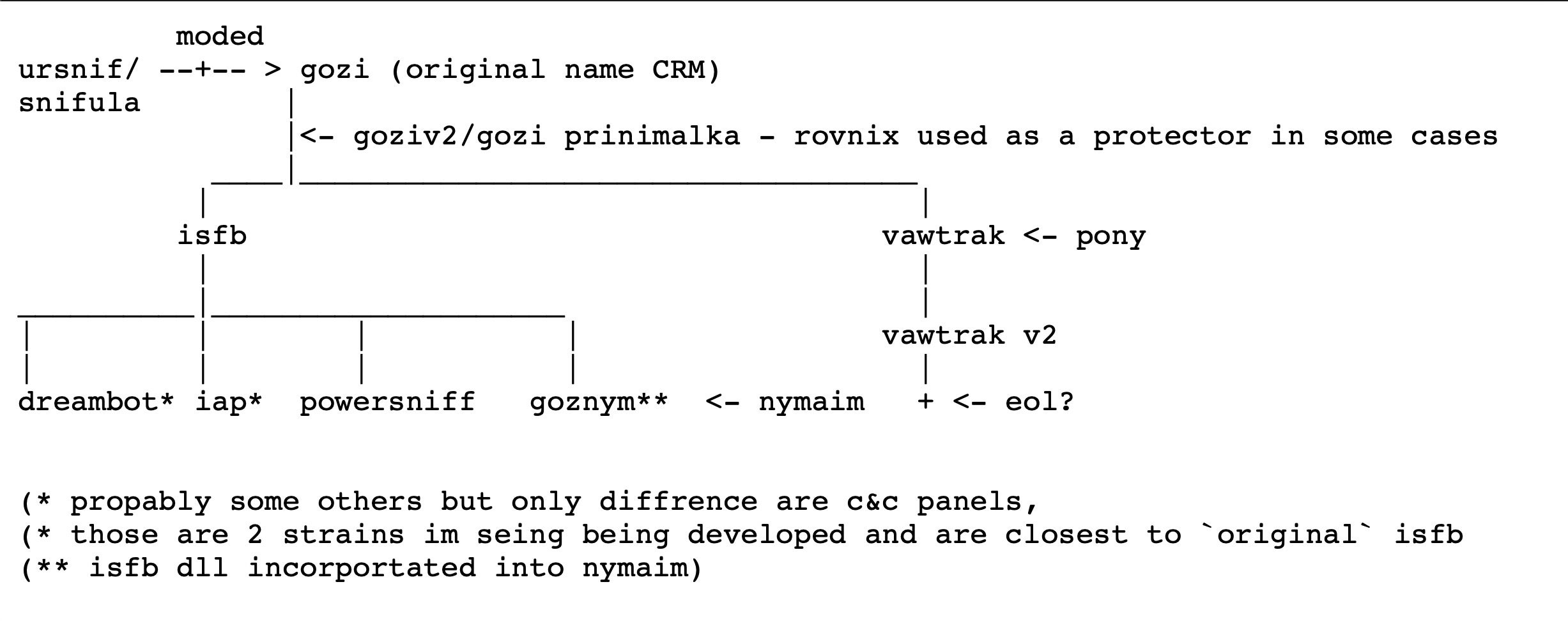
It has also been suggested that the powerful ISFB module that underlies this form of banking trojan may be maintained and developed by at least three independent groups.
Given all that we know, it’s reasonably likely that GozNym or something similar will be seen active in the wild again before long.
How to Protect Against GozNym
SentinelOne customers are already protected against GozNym malware as demonstrated in this video. As soon as the malware attempts to execute, the SentinelOne agent on the endpoint detects the threat and quarantines the malicious file, leaving the device in a clean, uninfected state.
If you are not already protected by SentinelOne, try a free demo to see how our easy-to-use, autonomous endpoint solution can protect your business.



