Hard on the heels of Black Hat USA 2019 came DEFCON and the 27th iteration of the venerable hacker conference that began all the way back in 1993, a time before a good portion of this year’s 20,000 plus attendants were even born! With four days of great talks, multiple subject-specific spaces like Wireless Village, Lockpicking Village, Cloud Village, as well as contests, workshops and, of course, all the after-hours parties, DEFCON is the main hacker event of the year. If you weren’t able to make it this year, or you just didn’t get the chance to see as much as you’d have liked, here’s our quick take on the highlights of DEFCON 27.

The Badge
This year’s electronic badge was created by Joe Grand and featured a quartz-face with microcontroller and Near-Field Magnetic Induction chipset. Amazingly, all 30,000 badges made for this year’s con were made with a unique gemstone.
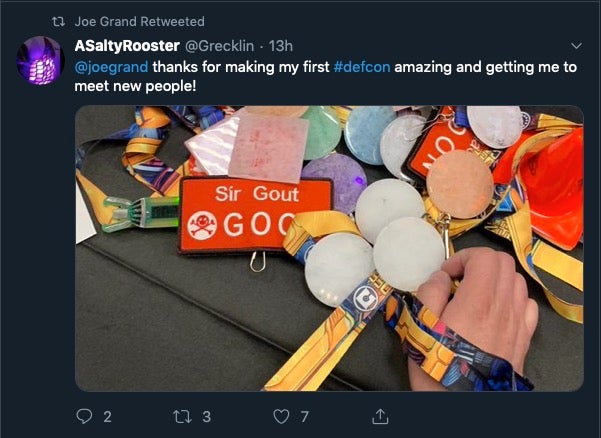
As is tradition with DEFCON electronic badges, the device also held a challenge for participants. This year it required attendees to either get close enough to lots of other types of badges (human and non-human) to complete the challenge or to hack the badge’s internal circuitry and force the badge to complete with a bit of hacker trickery! The badge quest involved, by hook or by crook, “interacting” with all the following:
// Bit masks for badge quest flags #define FLAG_0_MASK 0x01 // Any Valid Communication #define FLAG_1_MASK 0x02 // Talk/Speaker #define FLAG_2_MASK 0x04 // Village #define FLAG_3_MASK 0x08 // Contest & Events #define FLAG_4_MASK 0x10 // Arts & Entertainment #define FLAG_5_MASK 0x20 // Parties #define FLAG_6_MASK 0x40 /* Group Chat (all 6 gemstone colors: Human/Contest/Artist/CFP/Uber + Goon + Speaker + Vendor + Press + Village) */
For those interested in learning about hacking the badge, an excellent how-to is here.
The Workshops
There were 37 workshops spread over 3 days, from Thursday through to Saturday covering topics from beginner level “Hack to Basics” to advanced wireless exploitation. As places are always limited, this year there was a $25 sign up fee to discourage no-shows.
One of our favorites was Madhu Akula‘s ‘Breaking and Pwning Docker Containers and Kubernetes Clusters’. Security of cloud workflows is something enterprises need to pay more attention to, as vulnerabilities in applications running on containers is something most security solutions can’t offer visibility into. Being able to assess your cloud servers and workflows and protect them properly is a key defensive strategy organization need to have in place.
The Villages
This year there were a total of 30 villages, with DEFCON 27 hosting a Ham Radio Village for the first time. If you’re not familiar with the concept of DEFCON villages, the idea is that each village holds its own schedule of talks, workshops, labs and contests that are specific to the theme of the village. This allows for attendees to really focus on areas that interest them, meet like-minded hackers, and drill-down into the subject matter in various ways. From privacy to biohacking, the range of topics, talks and activities has something for everyone.
One of the more interesting villages this year was the Cloud village, an open space for people interested in offensive and defensive aspects of cloud security. One of the timely talks in the Cloud village this con was ‘Your Blacklist is Dead. Airgap Everything: The Future of CNC is the Cloud’. Eric Galinkin explained how SaaS platforms like Slack, Pastebin, Google and other social media sites are being exploited by hackers to get around URL blacklisting and the need to write domain name generating algorithms. With companies increasingly reliant on cloud and hybrid cloud infrastructures like AWS, understanding how threat actors are adapting their tools, tactics and procedures in light of that is essential.
With the 2020 elections just around the corner, the Voting Hacking Village was sure to receive a lot of attention, but unfortunately things didn’t quite go to plan. Thanks to a mixture of problems with the five prototype voting machines provided by DARPA, hackers were only able to stress test them for security flaws on the final day. Let’s hope they get a chance for a better community-driven security audit before next fall’s voting!
The Talks
Aside from the Village-hosted talks, there were four tracks of talks on demos, tools and exploits. High-school researcher Bill Demirkapi‘s talk on Friday, ‘Are Your Child’s Records at Risk? The Current State of School Infosec’, highlighted the difficulties of responsible disclosure for security researchers working in the education sector. Bill discovered vulnerabilities in two content management systems — Blackboard and Aspen — but faced an uphill struggle when he tried to inform the vendors of security flaws in their products. Fortunately, both vendors came round eventually, but not without some personal cost to Bill, who found himself temporarily suspended from school as he tried to gain attention to the cross-site scripting and SQL injection vulnerabilities in the widely used educational software.

Another interesting talk that caught our attention focused on one particular kind of IoT device that is pretty much ubiquitous in homes, reception areas and many offices but which receives little attention: the Smart TV. In ‘SDR Against Smart TVs: URL and Channel Injection Attacks’, Pedro Cabrera Camara demonstrated how internet-connected TVs present a readily-exploitable attack surface. Hackers can exploit flaws in the implementation of the HbbTV standard to pull off sophisticated remote attacks including keylogging and cryptomining.
We’d also like to give a shout out to Matt Wixey and his talk ‘Sound Effects: Exploring Acoustic Cyber-weapons’ for introducing the fascinating topic of how attackers can affect human health by bridging the divide between the digital and the physical. Matt’s talk covered acoustic malware that can cause physical or psychological harm, specifically through inaudible, ultrasonic frequencies. Matt showed how everyday IoT items like smart speakers and bluetooth headphones can be weaponized to both harm human users and damage the device itself.
Conclusion
While massive hacker cons might not be to everyone’s taste, the sheer size of DEFCON means there will always be plenty of content that covers whatever area of cybersecurity you happen to be interested in, and there’s always a good chance you’ll discover some new area of interest. It’s much of the reason why we all keep going back every year, as well as to meet up with old friends and to make some new. After an action-packed week in Las Vegas with both Black Hat and DEFCON, it’s time to bring all the new knowledge, insights and experiences back to base, share with our colleagues, and use what we’ve learned to develop new ways to improve our cybersecurity defences.



