
The Good
Upgrading legacy systems is a huge headache. Anyone involved in IT and systems engineering knows that. People involved in such processes are so reluctant to upgrade working (albeit ageing) systems that organizations hold on to legacy systems for years. When the systems in question manage the launch of nuclear missiles, the concerns are of different magnitude. That’s why we were delighted to learn that the US Airforce will stop using Floppy Disks for nuclear launch coordination. The Airforce currently uses an 8-inch floppy disks in a ’70s computer to receive orders from the President. According to the U.S. military, this antiquated system has been replaced by a “highly-secure solid-state digital storage solution.”
Anyone one who is old enough to remember the utter misery of working with these antiquated storage devices must be delighted that such a sensitive system is no longer reliant on 1980’s technology.

The Bad
The famous saying “there’s no honor among thieves” is apparently true for cyber espionage groups. The combined efforts of the UK National Cyber Security Centre (NCSC) and the NSA revealed that a Russian APT group “piggybacked” an Iranian APT infrastructure and tools to target 35 countries in an effort to obtain sensitive information. The APT group, nicknamed “Turla”, “Waterbug” or “VENOMOUS BEAR”, regularly collects information by targeting government, military, technology, energy and commercial entities.
Their latest trick involved the reuse of Iranian tools and infrastructure to disguise the origin of their activity. This is a dangerous step in the already escalating cyber warfare domain – the fact that one nation can masquerade as another can trigger a series of cyber operations that may lead to a kinetic conflict.

The Ugly
No one can afford to be lax on security, particularly companies that offer security-related services. That is the reality of doing business nowadays. But for a security-related company to get hacked and to delay disclosing the information to its clients for more than a year and a half is dismal.
NordVPN, a virtual private network provider that promises to “protect your privacy online,” was breached back in March 2018.
“One of the data centers in Finland we are renting our servers from was accessed with no authorization,” a NordVPN spokesperson said.
The breach was the result of hackers exploiting an insecure remote-management system that administrators of a Finland-based data center installed on a server NordVPN leased. The breach was made public in a series of Tweets, exposing the fact that NordVPN keys had leaked.
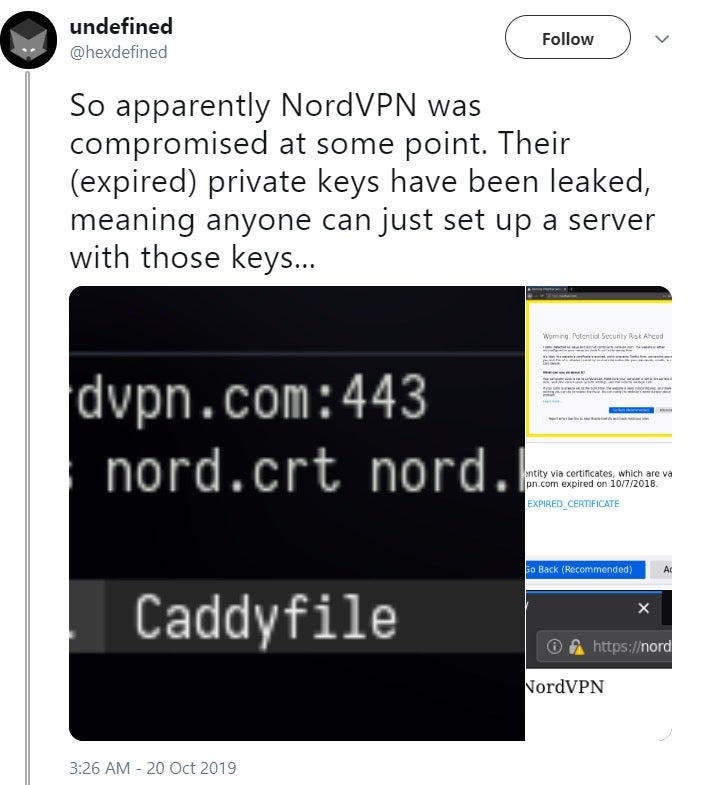
Although the company insists that no personal information was compromised, a log suggests that the hackers had root access, meaning they had almost complete control over the server and could read or modify just about any data stored on it.
In addition, it seems that two additional VPN services, TorGuard and VikingVPN, also experienced breaches that leaked encryption keys.
These types of incidents raise serious concerns about the vendor’s credibility – were they aware of the hack but opted to keep that a secret? Or were they unaware of it for so long? Even worse, this is a service billed as one providing greater security and privacy for their customers, and it seems they did not deliver on their promise.

