The Good
Back in November we reported on the formation of the ByteCode Alliance, a joint venture involving Mozilla, Fastly and others, to build security components on top of the WebAssembly project. This week, Firefox announced RLBox, in part born out of the fruits of that joint project. RLBox allows Firefox components to run code inside a WebAssembly sandbox, protecting the host OS from any unknown vulnerabilities. The technology will come to Linux users in Firefox 74 and macOS in Firefox 75. Windows support will arrive “soon after”, according to Mozilla.
That’s not the only update Mozilla have been working on as they continue to impress by adding security features to their Firefox browser that should really make a difference. This week, the browser was also updated with a new encrypted-DNS service for US-based users. The encrypted DNS over HTTPS (DoH) protocol will ensure that DNS lookups are not snooped on by 3rd parties, such as your ISP, some of whom have been up to no good by selling customers’ real-time location data and delivering targeted ads without consent.
The Bad
There’s been a lot of headlines this week about kr00k, aka CVE-2019-15126. This is a vulnerability in Broadcom and Cypress Wi-Fi chips that could allow unauthorized decryption of some WPA2-encrypted traffic and which is said to affect over a billion devices. An attacker would need to be in Wi-Fi range and would only be able to capture a limited amount of traffic. Even so, that could represent a serious leak, particularly if the underlying communication was not itself encrypted (e.g., such as using http rather than https, or chat apps that do not encrypt messages prior to transmission).
Among many devices vulnerable to the flaw, at least 14 Cisco products are said to be affected. The networking hardware giant says it is actively working on patches and that there is no workaround. Apple users on iOS 13.2 or above and macOS Catalina 10.15.1 or higher have already received patches several months ago.
The Ugly
As we predicted, Maze ransomware has started a trend among fellow cyber criminals, who’ve caught on to the enticing prospect of ‘naming and shaming’ victims to add extra incentive to pay. Now, DoppelPaymer have added themselves to the list of ransomware operators who are doubling up on this new twist in the extortion racket. Aside from Maze and now DoppelPaymer, Sodinokibi and Nemty are also intent on playing the shame game.
To that end, DoppelPaymer ransomware operators have this week published their own “Leaks” site, listing victims who have been attacked along with details of infected machines and sample files. For one recent victim, the site claims to have compromised 1438 devices.
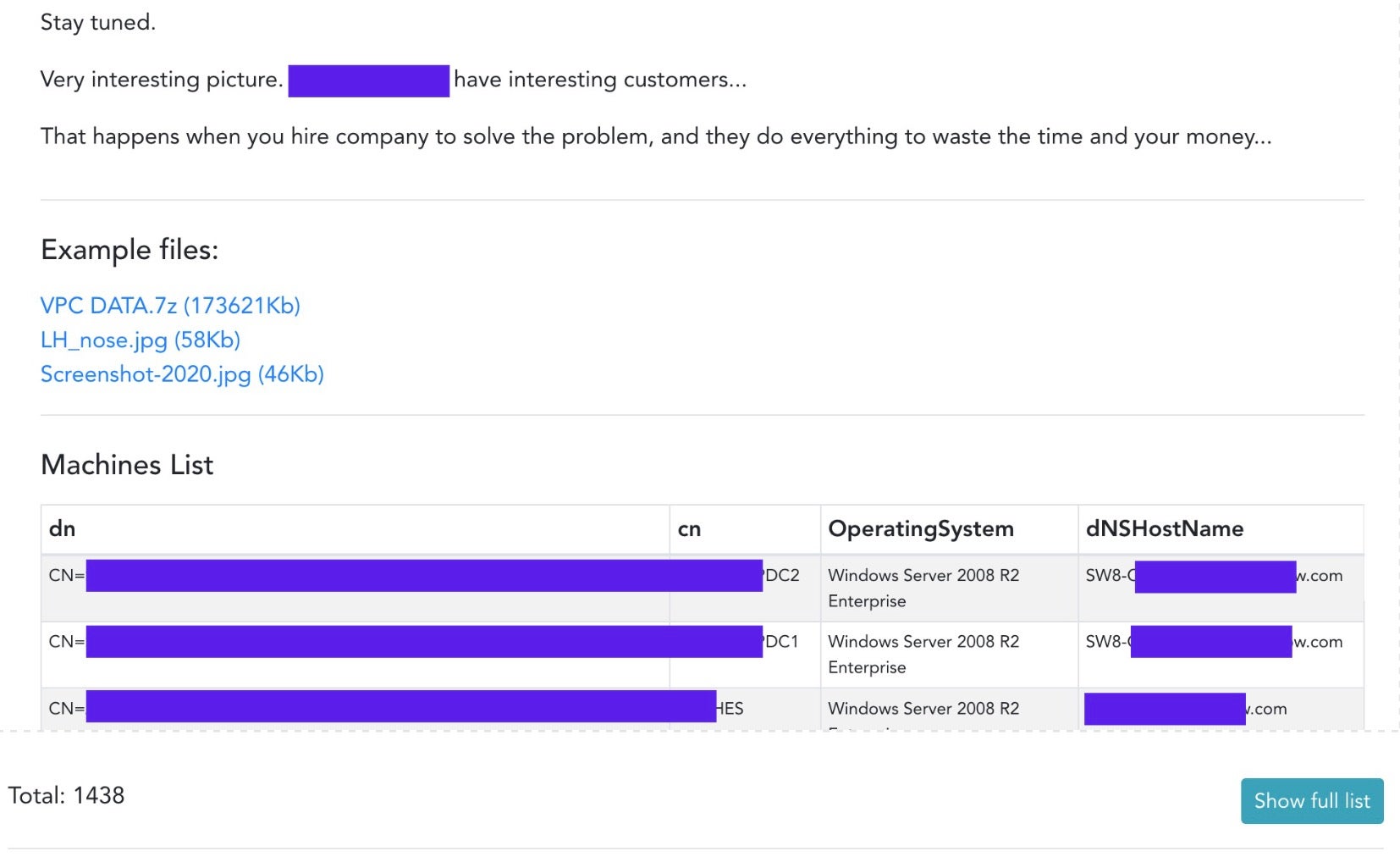
The attackers have recently added 3 more victims to the original 4 published when the site went up earlier this week, and the signs are that the number will continue to increase. According to reports, the operators have themselves stated that they plan on performing more data exfiltration now that they have created their own leaks site. The site’s URL, which we’ll refrain from publishing here, is helpfully tagged by most browsers as being a dangerous phishing site, so that should help to keep most of the general public away. Unfortunately, that won’t stop the data being shared with other criminals, who will be only too interested in exploiting it any way they can.
This kind of technique only adds to the dilemma for victims of ransomware as to whether they should pay or not pay, and underscores the need to ensure cybersecurity 101 for every organization: get protected before you get pwned.