The Good
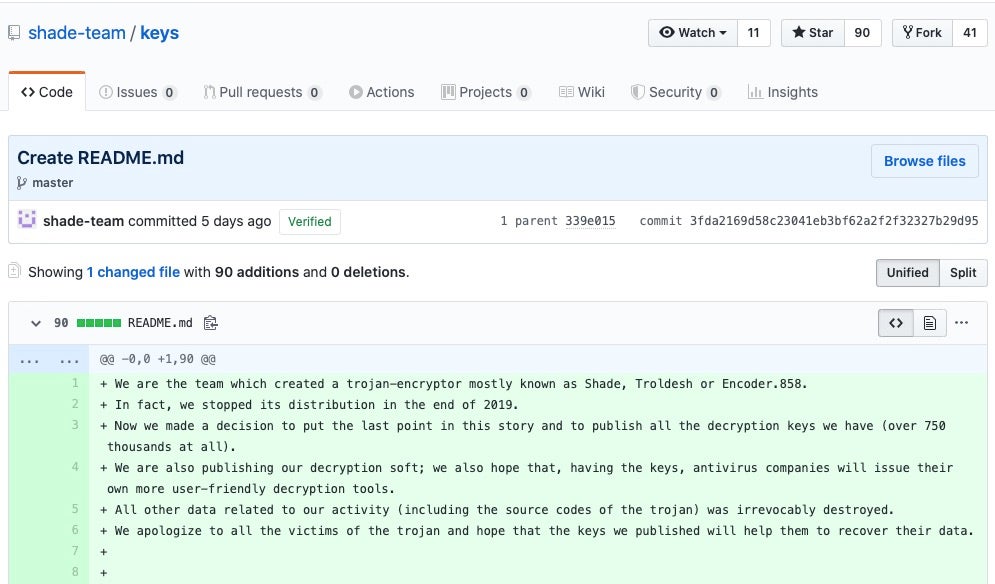
It remains to be seen whether this presages something worse to come, but for now there’s welcome news for potentially hundreds of thousands of ransomware victims. A github user claiming to represent the operators of Shade ransomware this week not only announced that the group had ceased attacks since late last year but also publicly released 750,000 decryption keys along with decryptor software. Shade, Troldesh or Encoder.858 ransomware first started circulating in 2014 and has been a constant menace ever since, with several security vendors noting a sharp increase in Shade attacks over late 2018 and early 2019. It remains unknown at this time whether the release is what it appears to be, or whether the ransomware group have been compromised by rivals or are shifting their attention elsewhere. In either case, the decryption keys look to be genuine and the apparent demise of Shade ransomware is welcome news indeed.
The Bad
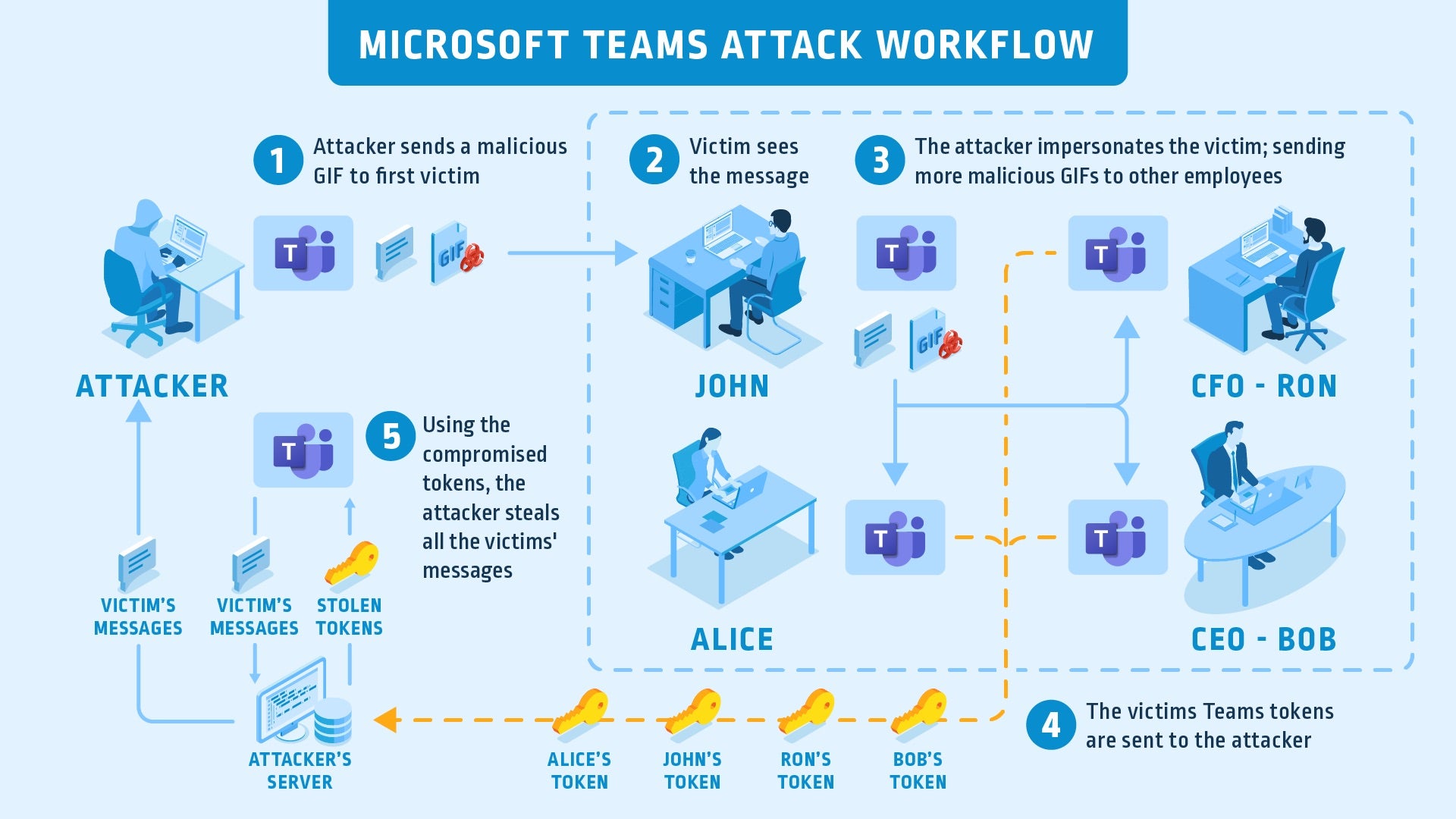
In these work from home times, we’re all relying on the security of our software more than ever, particularly when it comes to business meetings and conferences now being undertaken via teleconferencing apps. While Zoom’s troubles have been well-documented, less attention has been paid to Microsoft’s Teams. Turns out Teams had a major worm-like vulnerability that could have allowed a remote attacker to completely take over an organization’s Teams accounts and use it for lateral movement throughout the network. While the details are quite technical, the zero-click vulnerability could be exploited simply by sending an image or GIF to a victim. The attack succeeds as soon as the image is loaded in the viewer, and the victim would not even know they had been attacked, according to the researchers. The flaw was disclosed to Microsoft privately on March 23 and patched on April 20th. Needless to say, update immediately if you haven’t already.
In other news, attackers have been actively exploiting a zero-day flaw in the Sophos XG Firewall product, it emerged this week. A pre-auth SQL injection vulnerability (CVE-2020-12271) created a remote code execution (RCE) situation allowing attackers access to XG devices and exposing local usernames and hashed passwords of local accounts. The Asnarok Trojan was also seen used by the attackers on compromised devices. Sophos have pushed out a hotfix but users are advised to reduce the attack surface by disabling the HTTPS Admin Service and User Portal access on the firewall’s WAN interface where possible.
The Ugly
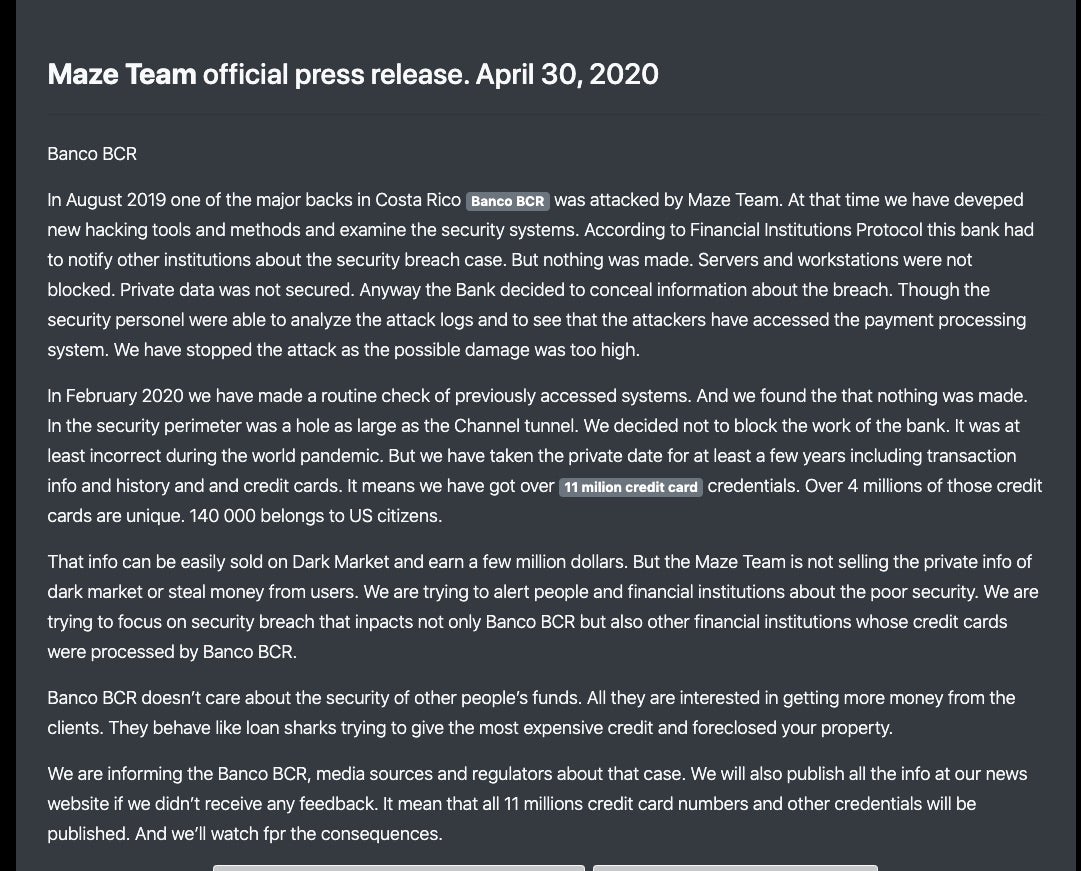
Maze ransomware crew are often featured in our Ugly section and this week is no exception as the gang’s “innovative” MO takes yet another odd turn. Their usual encrypt, exfil and leak tactic has a new twist as the group now claim to be turning down the chance to profit from one of their victims and insist instead that they have more altruistic motives. A statement from the group claims that they compromised state-owned Banco de Costa Rica (Banco BCR) in August last year and again in February this year, gaining access to the payment processing system and stealing 11 million credit card credentials, including 140,000 belonging to US citizens. So far, par for the course.
The twist comes in that the ransomware group claim not to have “blocked the work of the bank” as it would be “incorrect during the world pandemic”. However, they appear to be more concerned that the bank failed to both disclose the initial breach last year and to take the necessary action to secure the compromised systems. Maze claim that in February this year they were able to re-access the systems with ease and that the bank is culpable for its woefully lax security. The statement goes on to say that the Maze crew do not intend to sell the data but rather are “informing Banco BCR, media sources and regulators about the case.” The statement ends with a chilling threat, however. “We will also publish all the info…if we don’t receive any feedback. It mean that 11 million credit card numbers and other credentials will be published.”
It’s not clear what “feedback” the group are hoping for, but we wouldn’t be surprised if it amounted to a financial incentive not to leak. Seems like an easier way to make money than trading with criminals on the Darknet, anyway. Meanwhile, there is one thing we can agree on with the Maze ransomware operators if, indeed, their story is true: Banco BCR need to do better at security, and fast.