Back in 2018, we announced Device Control to our platform, offering admins and security teams the ability to manage the use of USB and other peripheral devices across the network. Today, we are excited to announce the latest updates to this feature, which now allows management of USB, Bluetooth and Bluetooth Low Energy devices with the greatest granularity possible. Our updated Device Control feature means IT and SOC teams can ensure business continuity for all end users requiring the use of external devices while limiting the attack surface to the bare minimum.

What Are the Security Risks of USB and other Peripherals?
Peripherals connected via USB or Bluetooth are ubiquitous and still a necessary feature of business devices, from laptops to workstations and even IoT smart devices. The prevalence of peripherals connected to endpoints in the enterprise has not gone unnoticed by malicious actors. A recent report found that cyber threats to operational technology systems through USB removable media devices have almost doubled in the last 12 months, for example. Malware borne on removable media has been used for opening backdoors, establishing persistent remote access and delivering further malicious payloads, among other things.
Attackers have been finding creative ways to lure users into plugging alien USB thumb sticks into their corporate devices. In one incident, hospitality victims were sent an envelope containing a fake BestBuy gift card, along with a USB thumb drive containing malware. USB drives are also a prime vector for the egress of confidential and business critical data, and the recent shift to “work from home” (or anywhere except the office) only adds to the risk of employees connecting non-company sanctioned peripherals to facilitate this new work environment.
In designing this feature we took into account requirements like system stability, interoperability and cross-platform support (Windows and macOS).

Device Control: Simple Policy Management to Add, Block or Restrict Devices
To facilitate implementation, we’ve designed this feature to allow maximum granularity and flexibility when defining an enterprise Device Control policy.
You can set a Device Control policy for the entire enterprise, a specific Site or even a specific Group of devices. Policy is constructed by a set of Device Control rules.
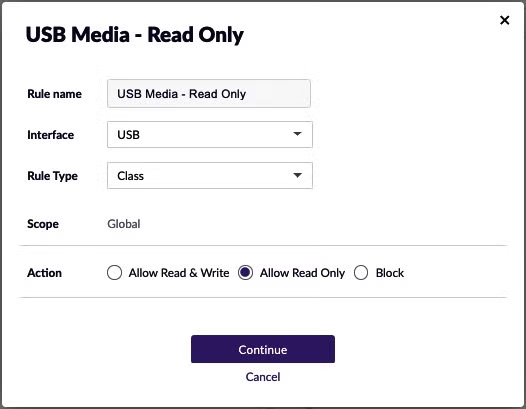
Rule definition starts by selecting the interface type (USB or Bluetooth), then rule type and action. For instance, we can control USB devices based on the following attributes:
- Vendor ID
- Class
- Serial ID
- Product ID
Then the desired action:
- Allow Read & Write
- Allow Read Only
- Block
This enables the administrator to set fine-grained policies. For example, it is possible to construct a rule that allows specific users to access certain types of USB devices, permits others to use USB removable media to read files only, and blocks all other users from using external USB devices completely.
Bluetooth Security – Plugging the Gaps
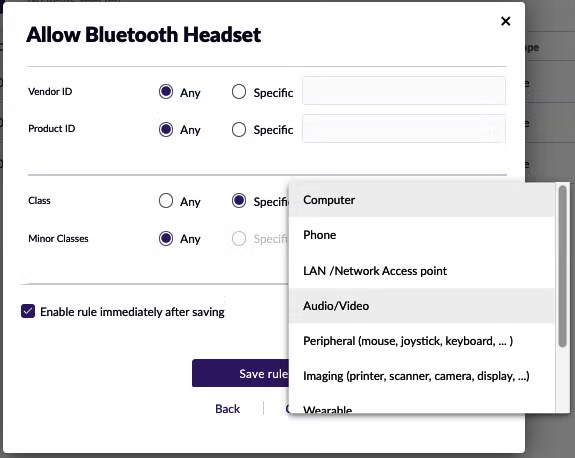
The Bluetooth protocol has been riddled with vulnerabilities. Most of these reside in older Bluetooth versions and security-conscious enterprises should refrain from allowing users to connect such devices to corporate endpoints (and, subsequently, networks).
For Bluetooth devices, SentinelOne Device Control makes it possible to allow or restrict the use of all Bluetooth devices, Bluetooth devices according to their type (e.g. keyboard, mouse, headset) or to allow the operation of devices based on the Bluetooth protocol version they support (to reduce the risk stemming from vulnerabilities in older Bluetooth versions).
Flexibility and Control Over Every Device
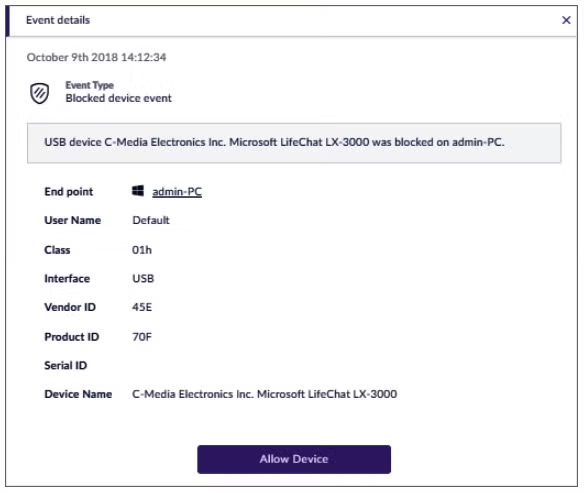
SentinelOne Device Control allows administrators to easily define policies, but we also recognize that new devices can be introduced to the enterprise every day. We realize that administrators need the flexibility to respond “on the go” and approve new USB devices as they appear on (and are blocked by) the system.
To facilitate this, an administrator can see every case of a device that was blocked in the management console’s Activity Log, and directly from there, approve the blocked device if they choose.
Conclusion
Together with SentinelOne Firewall Control, Device Control provides what some considered the missing pieces to fully replace legacy antivirus (AV) solutions with its next-gen product. Like other features of the platform, these are delivered via SentinelOne’s single agent across all platforms and from the same management console.



