SentinelOne
+ Splunk
Streamline security operations
with EDR and SIEM
No Code Needed
Enhance Threat Detection
Consume and correlate high fidelity endpoint logs and alerts
Accelerate Alert Triage
Investigate endpoint information at a glance with predefined filters, dashboards and forensics
Increase Response Efficiency
Automatically initiate SentinelOne endpoint response capabilities within the Splunk console
Splunk App Integration Overview
The integration of SentinelOne and Splunk empowers organizations to combine the strengths of their Splunk deployments to collect, monitor, analyze and visualize massive streams of machine data, with the visibility, detection, response, remediation and forensics capabilities of SentinelOne. SentinelOne offers deep integration with Splunk, enabling joint customers to maximize the value of their SIEM and EDR investments.


How Does it Work?
With the SentinelOne Technology Add-on (TA) for Splunk, clients can take advantage of a prebuilt ingestion pipeline that includes parsing of syslog events, mapping to Splunk Common Information Models (CIM), and saved searches.
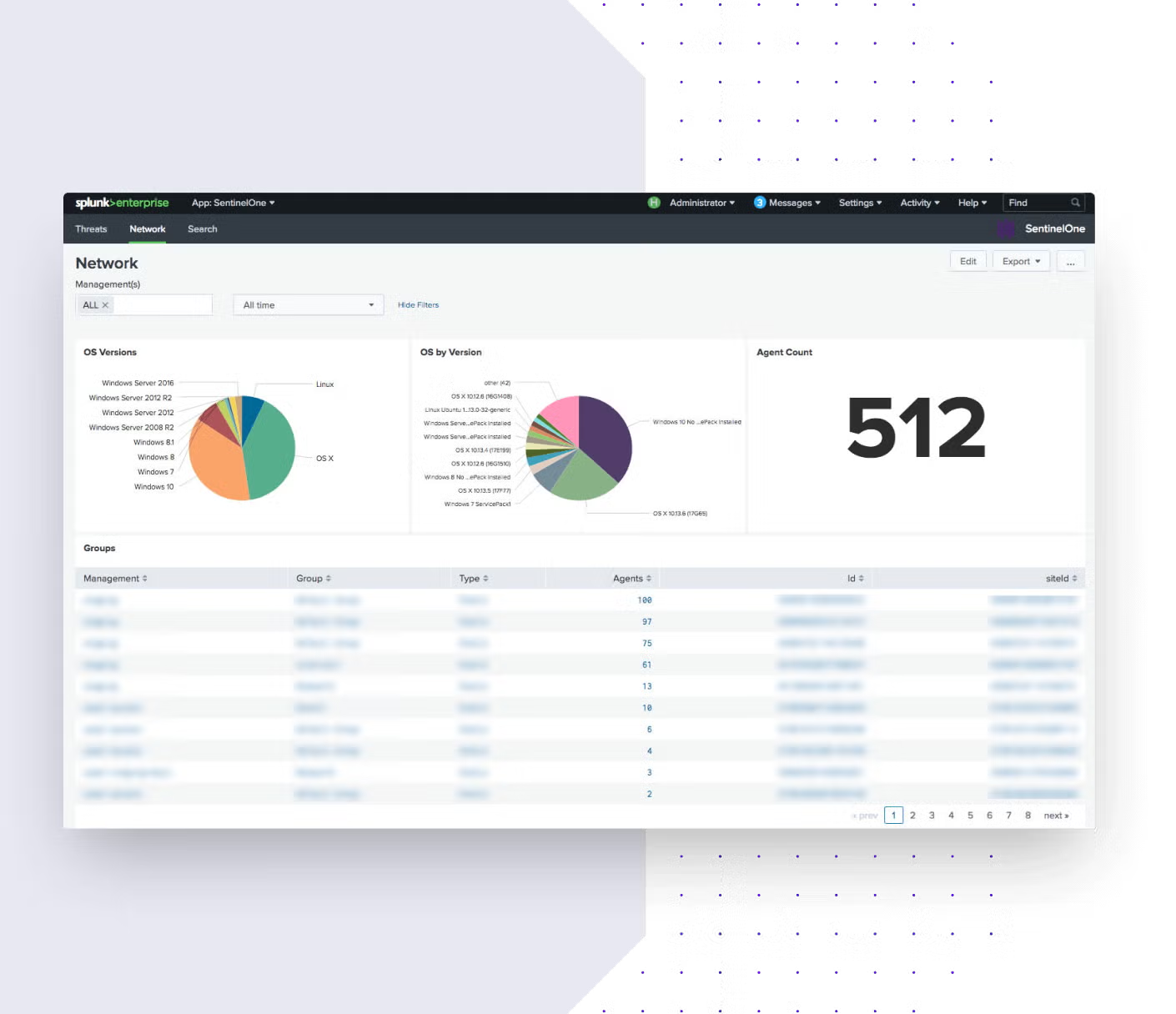
With the SentinelOne App for Splunk, clients can easily perform endpoint triage and response from within the Splunk console. The app provides rich capabilities for viewing endpoint and threat information at a glance and once a threat has been confirmed, Adaptive Response Actions in Splunk can automatically trigger a response in SentinelOne. The combined solution provides SOC teams with unparalleled visibility and context. An integrated workflow to respond to threats with consistency and reduce mean time to response (MTTR).

“Data is the common currency for enterprises; our bidirectional integrations with SentinelOne for SIEM and SOAR capabilities are used by some of the largest enterprises in the world.”
Learn More About the SentinelOne + Splunk Integration

