The Good
In response to Biden’s recent Executive Order and ongoing concerns about the poor state of cybersecurity, particularly in relation to critical infrastructure, the good news this week has to be Microsoft and Google pledging to reach into their deep pockets to help fight cybercrime.
Google has said it will stump up $10bn over the next five years after meeting with Biden and other tech leaders on Wednesday. Among projects earmarked for the funding, Google says it will expand the rollout of its SLSA framework, which is aimed at helping fight supply chain attacks through open-source software, and invest in training more people to address the cybersecurity skills shortage.

Reuters
Meanwhile, Microsoft appears to have seen Google’s hand and raised it by another $10bn, pledging a total of $20bn. Around $150m is allotted to help US government agencies upgrade protections and expand cyber security training. Given that Microsoft software is a prime target in so many cyber attacks, particularly when it comes to ransomware, we hope that a good portion of that funding goes to plugging existing gaps more effectively.
At present, there’s no word from Apple about whether they also intend to contribute funding in response to the government’s call-to-arms. The Cupertino outfit is somewhat preoccupied with defending its plan to run (what some have called) “warrantless searches” on its customers’ iPhones, as well as dealing with other security hiccups with its planned iOS cloud anonymizer service.
The Bad
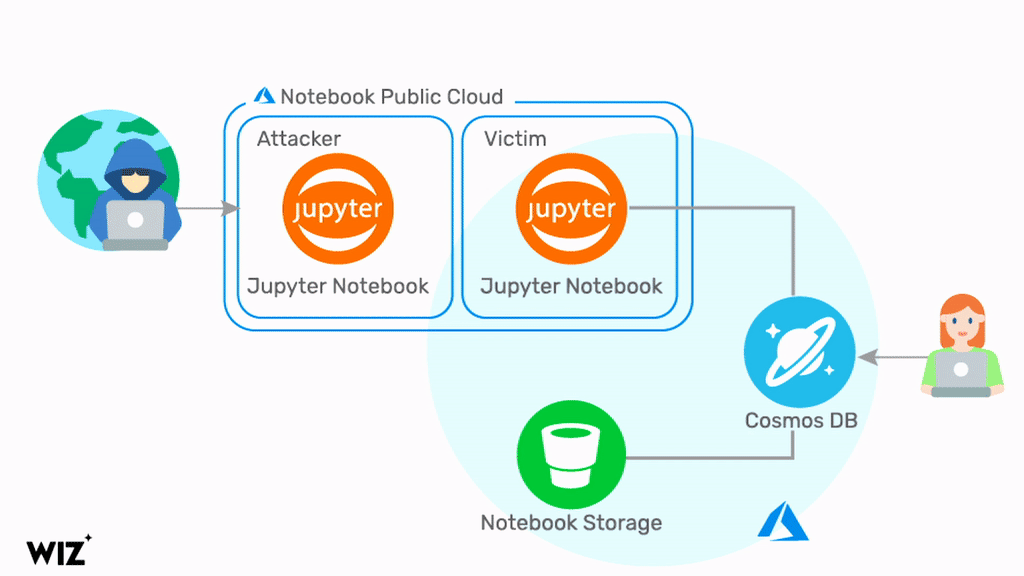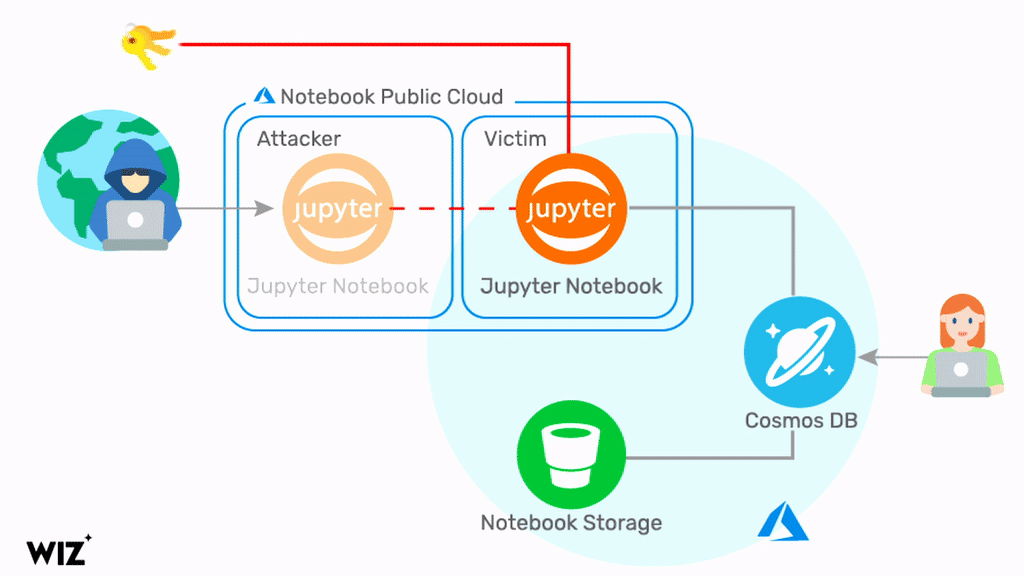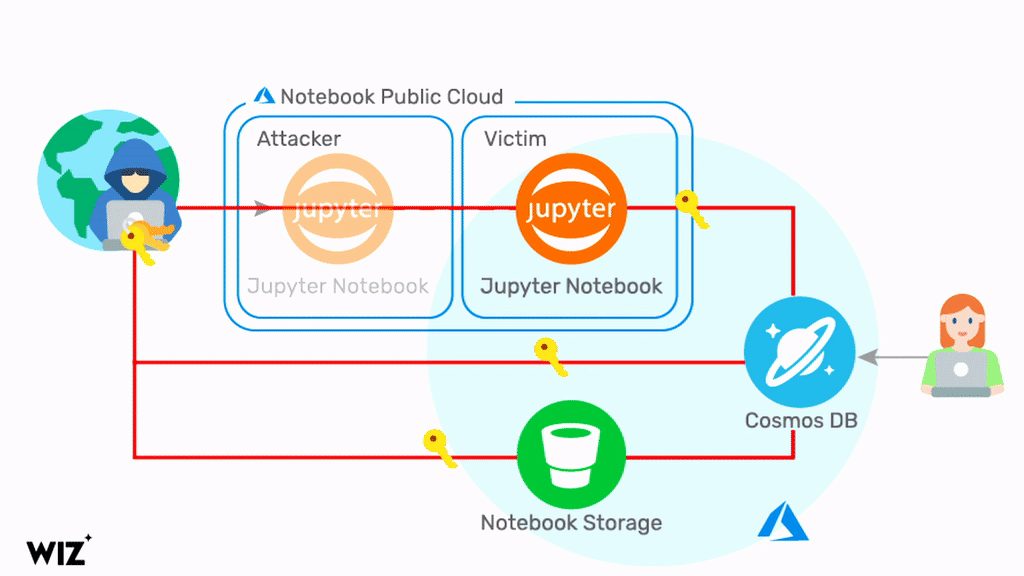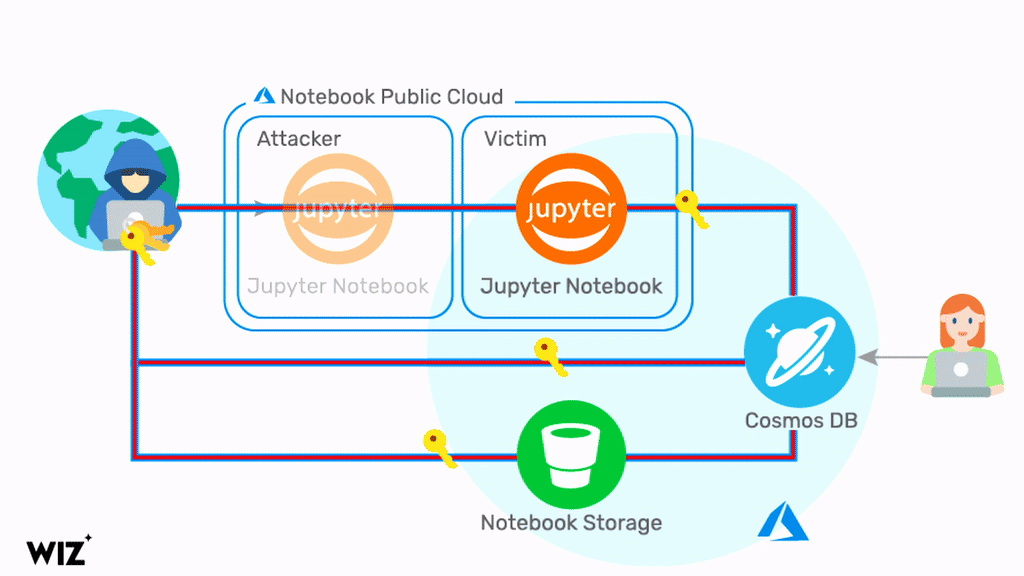
A critical vulnerability in Microsoft’s Azure cloud platform was revealed this week that lay exposed for months and could have allowed attackers to remotely take over a target’s Cosmos DB instances without authorization.
ChaosDB, as researchers at Wiz have dubbed it, gives any Azure user full administrator access to another MS customer’s Cosmos DB instances. The researchers say that the flaw is trivial to exploit and does not require previous access to the victim’s environment. Fortune 500 companies are among thousands of organizations impacted, it is claimed.
For their part, Microsoft reportedly plugged the vulnerability within days of being notified of the problem. After receiving the bug report on August 12th, the company disabled the problematic feature on August 14th, and rewarded the researchers with a $40,000 bug bounty shortly thereafter. Wiz published details of the findings this Thursday.
While that may sound like a happy ending for all concerned, there is still some concern for affected parties. Microsoft has said that it informed customers who may have been impacted and that “no one exploited it in the wild”. The researchers, however, believe that Microsoft has only notified around 30% of its customers and that the number of affected parties is much higher. To ensure mitigation, Azure users are being advised to regenerate Cosmos DB primary keys as soon as possible.
The Ugly
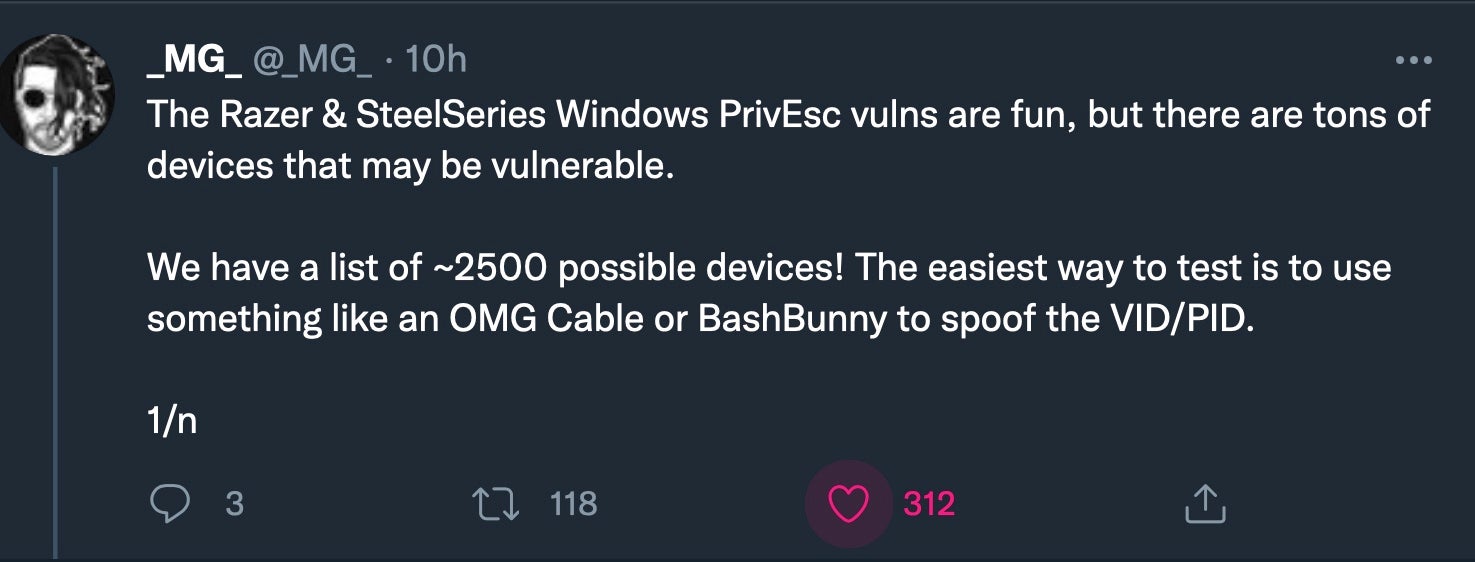
Zero days are never pretty, and sadly this week saw another one affecting Windows 10, offering a path to a local privilege escalation when plugging in certain peripherals. The story began with a Tweet describing how popular Razer Synapse products prompt Windows 10 to automatically download Razer Synapse software when plugged in. The software provides services to users to manage settings on the associated peripheral. It’s a common enough architecture used by many device manufacturers (much to the chagrin of some) and Razer alone is said to have some 100 million users.
Unfortunately, it turns out that when the installer, which runs with SYSTEM privileges, offers users the option to specify the install location, pressing Shift and right-clicking the dialog throws a prompt to “Open PowerShell window here”. The PowerShell window inherits the SYSTEM privileges of the opening process and thus allows the user to enter commands with the same privileges.
According to one estimate, there’s around 250 or so affected Razer products, but other Twitter users picked up on the vulnerability and quickly disclosed thousands of other devices that may trigger the same behavior.
While this is a LPE that won’t help remote attackers, it does open the door to the possibility of an unattended PC being exploited simply by an attacker plugging in a mouse or spoofing tool. Perhaps this will serve as a timely reminder to readers to always lock the screen when stepping away from the workstation.
It is also worth noting for worried users that the exploit only works if Windows Update runs the installer automatically. Devices that already have the software installed should not be vulnerable, although that assumes there are no other problems with the driver. Unsafe Windows drivers is a bit of a thing at the moment, and we’re sure we haven’t seen the last of such reports.
On the back of the disclosure, Razer announced that they were working on a fix and even offered a bug bounty to the researcher, despite his dropping it as a zero-day on social media. For that, the company at least deserves some credit, for not every bug bounty operator is quite so generous.