The Good
Cyber grave robbing, sadly, is not a new crime. Identity thieves are known to scour obituaries looking for information that can be used in bank account takeovers. However, after the appalling collapse of Champlain Towers South condo in Surfside, Florida a few months ago, many were shocked by the report that cyber grave robbers were stealing the identities of victims of the Surfside tragedy. The good news this week is that authorities have arrested four individuals in connection with the reported cyber crimes.
Nelson Garcia-Medina’s arrest followed that of his sister and two other individuals. The gang are accused of stealing identities of at least five deceased and two surviving victims of the collapse. Police also said that Medina’s sister was recorded posing as someone who survived the collapse and seeking a replacement credit card.

Law enforcement have been on the trail of the suspects since June and say that their IDs, car registrations and addresses were all fake, describing the gang as “professional crooks”. Searching the premises of the accused, police found credit card-making equipment, blank checks, birth certificates and credit cards in the names of Surfside victims. The gang could face 15 to 30 years in prison if convicted. Local Mayor Charles Burkett said “Today they got what they deserved, and we’re all much happier for it”. The investigation continues as police widen the hunt for other possible co-conspirators and victims.
The Bad
Two weeks ago, we reported on ChaosDB, a critical vulnerability in the Azure cloud platform that allows for remote account takeover of Cosmos DB instances. That flaw was quickly plugged, but this week Microsoft revealed details of another Azure-related flaw that could allow an attacker to execute malicious code on other users’ Azure containers.
Researchers described an attack that could allow a malicious Azure tenant to gain admin privileges over multitenant Kubernetes clusters hosting Azure Container Instances (ACI), Microsoft Azure’s Container-as-a-Service (CaaS) offering. As the researchers described it, the vulnerability could allow one user of a public cloud service to break out of their environment and execute code on environments of other users in the same public cloud service.
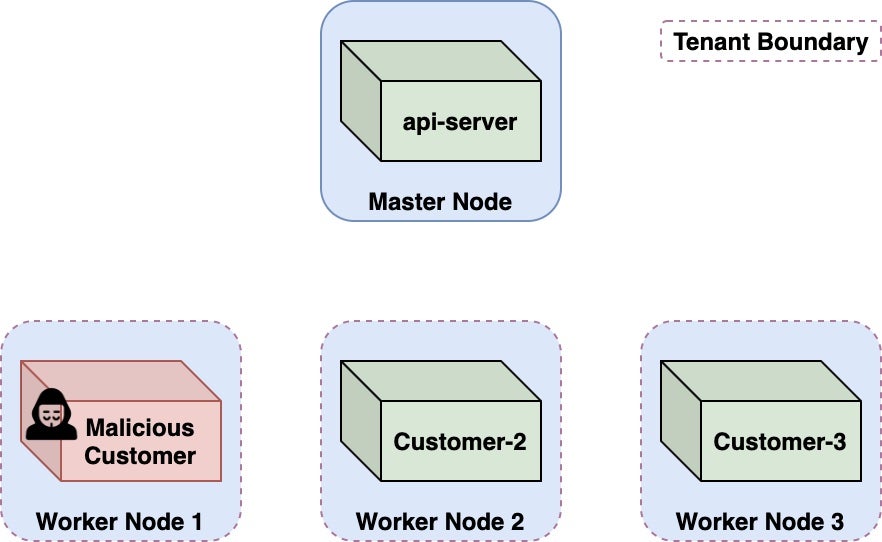
While there is no evidence that this attack has been used in the wild, anyone running containers on ACI that were deployed prior to Aug 31, 2021 is advised to revoke privileged credentials and check access logs for suspicious activity. Microsoft patched the flaw prior to publication of the research.
This and the ChaosDB bug are good reminders that despite the effort cloud service providers put into the security of their offerings, enterprises need to ensure they have security tools that can protect Kubernetes and cloud workloads with the same kind of defense-in-depth approach they are used to taking with traditional endpoints.
The Ugly
It has been a particularly ugly week in the world of ransomware, with hits taken by various public sector organizations including health, education, and government. On top of that, SentinelLabs has also seen a worrying new tactic being employed by at least one ransomware operator that could well become a standard approach.
Desert Wells Family Medicine was hit in yet another critical infrastructure attack focusing on health services as long ago as May and is still struggling to get services back online. However, it has only this week come to light that the attacker both stole patient data and corrupted the Arizona clinic’s backup of 35,000 patient records.
Meanwhile, Washington DC’s Howard University cancelled classes, stood down its campus wifi and went into a “heightened security” posture after being hit by a ransomware attack beginning last Friday. The University said on Tuesday that it was in contact with the D.C. city government and the FBI in its attempts to deal with the attack.
The ransomware problem isn’t unique to the U.S., of course. The South African Department of Justice said Monday that it was also victim of an attack that affected its offices and courts around the country. All network-based services remained offline at the time of writing.
In what could be a worrying development for organizations seeking to engage professional help with ransomware attackers, SentinelLabs observed that ransomware operator Ragnar_Locker has threatened to punish victims faster if they use negotiators.
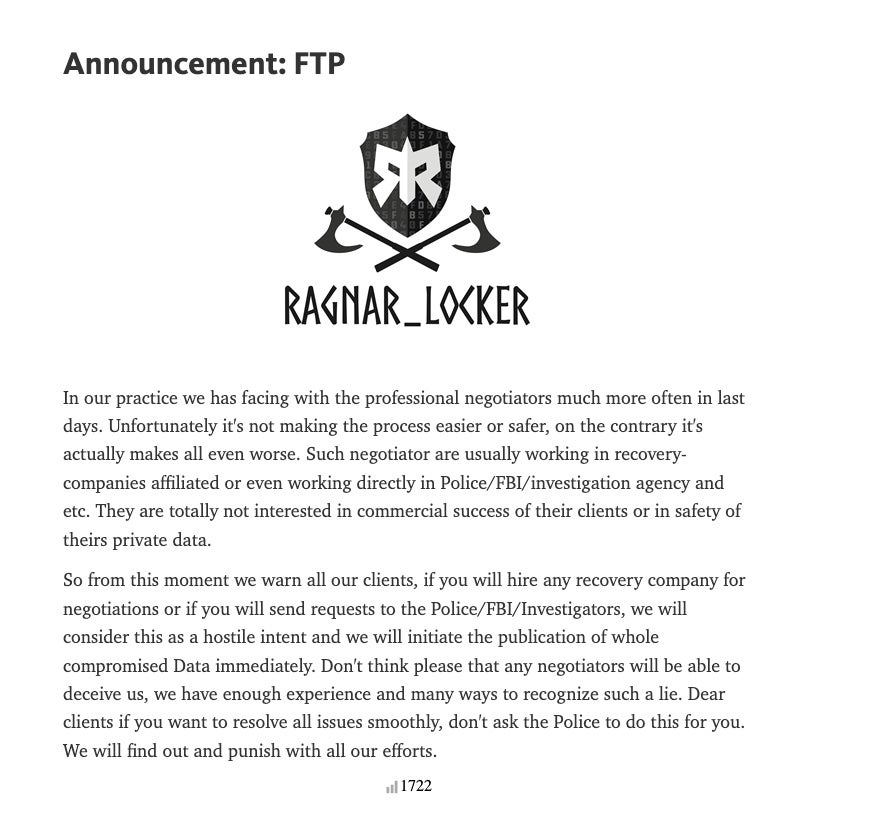
While the attempt to convince victims that negotiators are not acting in good faith should be taken with a large pinch of salt, it remains the case that this new scare tactic piles further pressure on victims to accede to the attacker’s demands. Once they have achieved initial access, ransomware gangs have a growing array of tools and techniques with which to leverage payment from victims, along with plenty of incentive. As the old adage goes, an ounce of prevention is worth a pound of cure.



