The Good
In recent weeks, we’ve had the pleasure to report on some high-profile cybercrime arrests. That trend continues this week as FBI Director Christopher Wray announced another arrest and charges laid against two individuals for deploying REvil ransomware.
Ukrainian Yarolsav Vasinskyi, 22, was arrested in Poland after an international effort spanning law enforcement and private security companies across several countries. Vasinskyi is charged with having been a material participant in multiple REvil-centric attacks, including the devastating attacks on Kaseya. In addition, the Justice Department announced charges against Russian national Yevgeniy Polyanin, 28, and the seizure of $6.1 million in maliciously-obtained funds.
Based on the unsealed court documents, Vasinskyi was directly involved in the attack on Kaseya, which took place in early July 2021. This attack exploited Kaseya’s established infrastructure to distribute REvil ransomware and subsequently cripple a devastating amount of machines.
The attack on Kaseya was a sobering reminder of how relentless these ransomware attackers can be. Many of the affected businesses and individuals will likely still be recovering from the economic damage for years to come. We applaud the continued efforts by law enforcement and the private sector to hunt down and eliminate these criminal threats. Cheers to the good guys, and lets hope this trend continues!
The Bad
A recent Cl0p ransomware campaign struck a sizable blow to the privacy of many. The British company Stor-a-File was the unfortunate target of an attack by Cl0p in September of this year. This is particularly concerning given the business that Stor-a-File is in. They are constantly dealing with sensitive documents and processing them for a variety of customers including those in the medical business. To date, Stor-a-File has refused to pay the attackers, which is an admirable decision. However, as a result, there has been some leakage of data on the Cl0p blog.
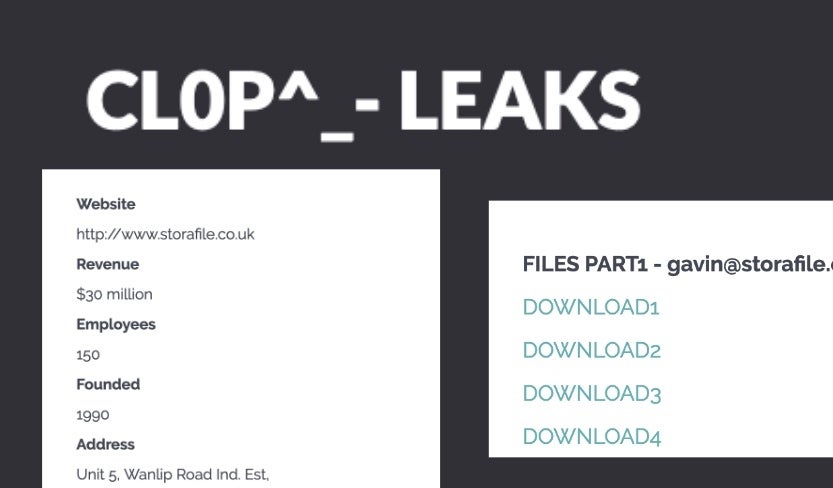
An important aspect to note in this attack is the initial access vector. According to current intelligence, first stage access was obtained via well-known weaknesses in the SolarWinds Serv-U FTP software. This particular vulnerability is a favorite of Cl0p operators. According to a statement from Stor-a-File, “the incident is limited to the small number of records we hold electronically”, and since the incident, the company has patched exposed systems.
Ransomware operators will continue to target vulnerabilities that work, and this incident is a timely reminder that just because a vulnerability drops out of the news cycle, it does not mean it has gone away. Unfortunately, we get new vulnerabilities to worry about every day, which compounds the issue. But at the end of the day, we all have to be extra vigilant and make sure we understand our environment, have adequate and required visibility, and protect those systems which we deem the most ‘critical’.
The Ugly
This week saw disclosure of a critical vulnerability in the Palo Alto GlobalProtect firewall. The flaw, identified as CVE-2021-3064, is a memory corruption vulnerability (stack-based buffer overflow) in the GlobalProtect portal and gateway interfaces.
Upon successful exploitation, a remote attacker may potentially gain access to a root shell, and thus unfettered access to the target systems. Exploitation can be achieved remotely, without the need for any authentication.
The issue affects PAN-OS 8.1 prior to 8.1.17 on both virtual and physical firewalls. Gaining this level of access is extremely attractive to attackers. Beacheading in a network appliance (such as a firewall) allows for a very well detailed view of the adjacent network, along with the necessary access to extend beyond that initial host. Estimates vary as to the number of devices affected; there could be anywhere between 10,000 and 70,000 exposed devices on the public internet.
The flaw was discovered by the Randori Attack Team and subsequently disclosed to Palo Alto, which responded with advisories and patches for the affected systems. We encourage all those who may be exposed, or are seeking more information, to review Palo Alto’s advisory.